Configure customer-managed keys for Azure Load Testing with Azure Key Vault
Azure Load Testing automatically encrypts all data stored in your load testing resource with keys that Microsoft provides (service-managed keys). Optionally, you can add a second layer of security by also providing your own (customer-managed) keys. Customer-managed keys offer greater flexibility for controlling access and using key-rotation policies.
The keys you provide are stored securely using Azure Key Vault. You can create a separate key for each Azure load testing resource you enable with customer-managed keys.
When you use customer-managed encryption keys, you need to specify a user-assigned managed identity to retrieve the keys from Azure Key Vault.
Azure Load Testing uses the customer-managed key to encrypt the following data in the load testing resource:
- Test script and configuration files
- Secrets
- Environment variables
Note
Azure Load Testing does not encrypt metrics data for a test run with your customer-managed key, including the JMeter metrics sampler names that you specify in the JMeter script. Microsoft has access to this metrics data.
Prerequisites
An Azure account with an active subscription. If you don't have an Azure subscription, create a free account before you begin.
An existing user-assigned managed identity. For more information about creating a user-assigned managed identity, see Manage user-assigned managed identities.
Limitations
Customer-managed keys are only available for new Azure load testing resources. You should configure the key during resource creation.
Once customer-managed key encryption is enabled on a resource, it can't be disabled.
Azure Load Testing can't automatically rotate the customer-managed key to use the latest version of the encryption key. You should update the key URI in the resource after the key is rotated in the Azure Key Vault.
Configure your Azure key vault
To use customer-managed encryption keys with Azure Load Testing, you need to store the key in Azure Key Vault. You can use an existing key vault or create a new one. The load testing resource and key vault may be in different regions or subscriptions in the same tenant.
Make sure to configure the following key vault settings when you use customer-managed encryption keys.
Configure key vault networking settings
If you restricted access to your Azure key vault by a firewall or virtual networking, you need to grant access to Azure Load Testing for retrieving your customer-managed keys. Follow these steps to grant access to trusted Azure services.
Configure soft delete and purge protection
You have to set the Soft Delete and Purge Protection properties on your key vault to use customer-managed keys with Azure Load Testing. Soft delete is enabled by default when you create a new key vault and can't be disabled. You can enable purge protection at any time. Learn more about soft delete and purge protection in Azure Key Vault.
Follow these steps to verify if soft delete is enabled and enable it on a key vault. Soft delete is abled by default when you create a new key vault.
You can enable purge protection when you create a new key vault by selecting the Enable purge protection settings.
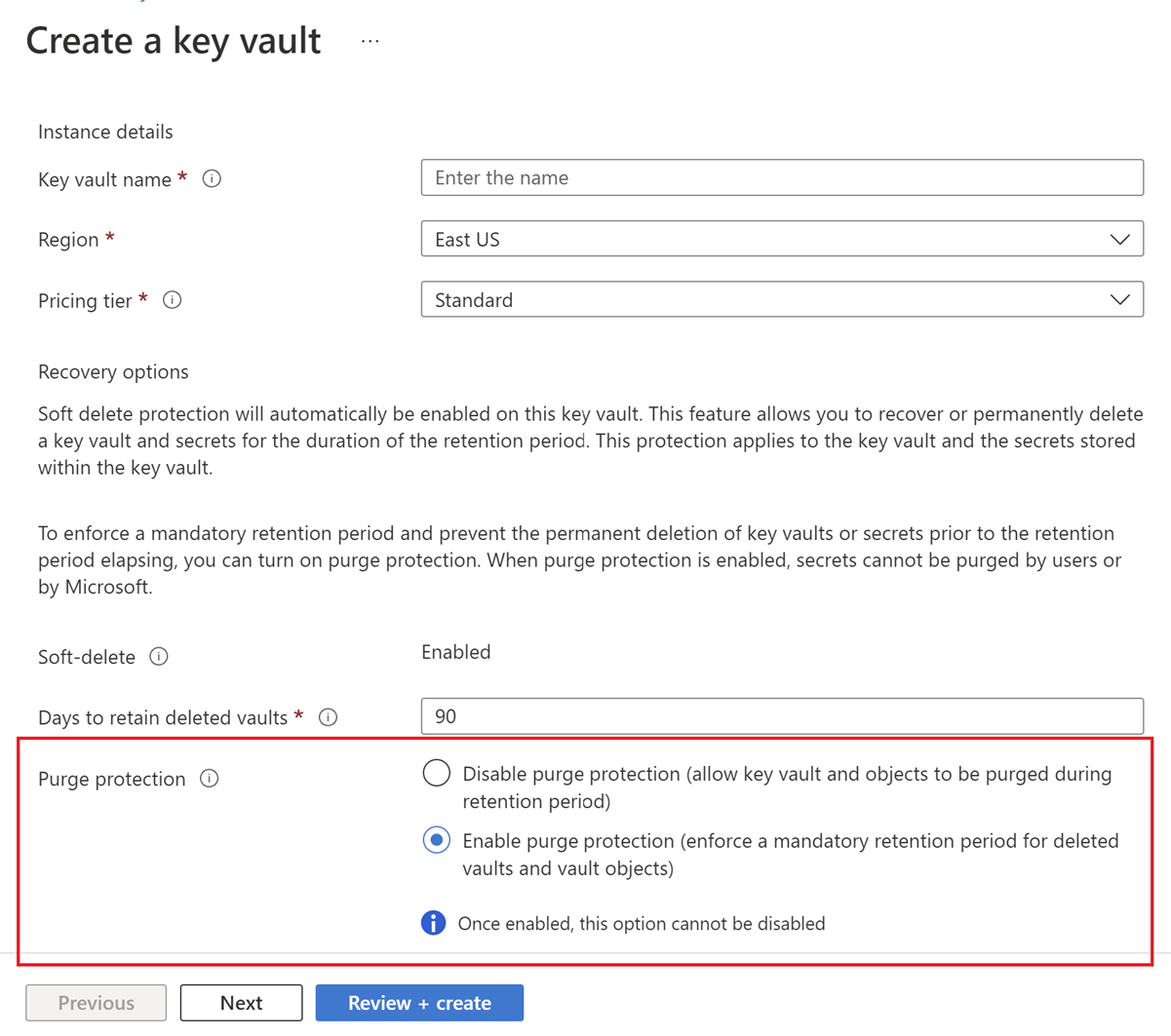
To enable purge protection on an existing key vault, follow these steps:
- Navigate to your key vault in the Azure portal.
- Under Settings, choose Properties.
- In the Purge protection section, choose Enable purge protection.
Add a customer-managed key to Azure Key Vault
Next, add a key to the key vault. Azure Load Testing encryption supports RSA keys. For more information about supported key types in Azure Key Vault, see About keys.
To learn how to add a key with the Azure portal, see Set and retrieve a key from Azure Key Vault using the Azure portal.
Add an access policy to your key vault
When you use customer-managed encryption keys, you have to specify a user-assigned managed identity. The user-assigned managed identity for accessing the customer-managed keys in Azure Key Vault must have appropriate permissions to access the key vault.
In the Azure portal, go to the Azure key vault instance that you plan to use to host your encryption keys.
Select Access Policies from the left menu.
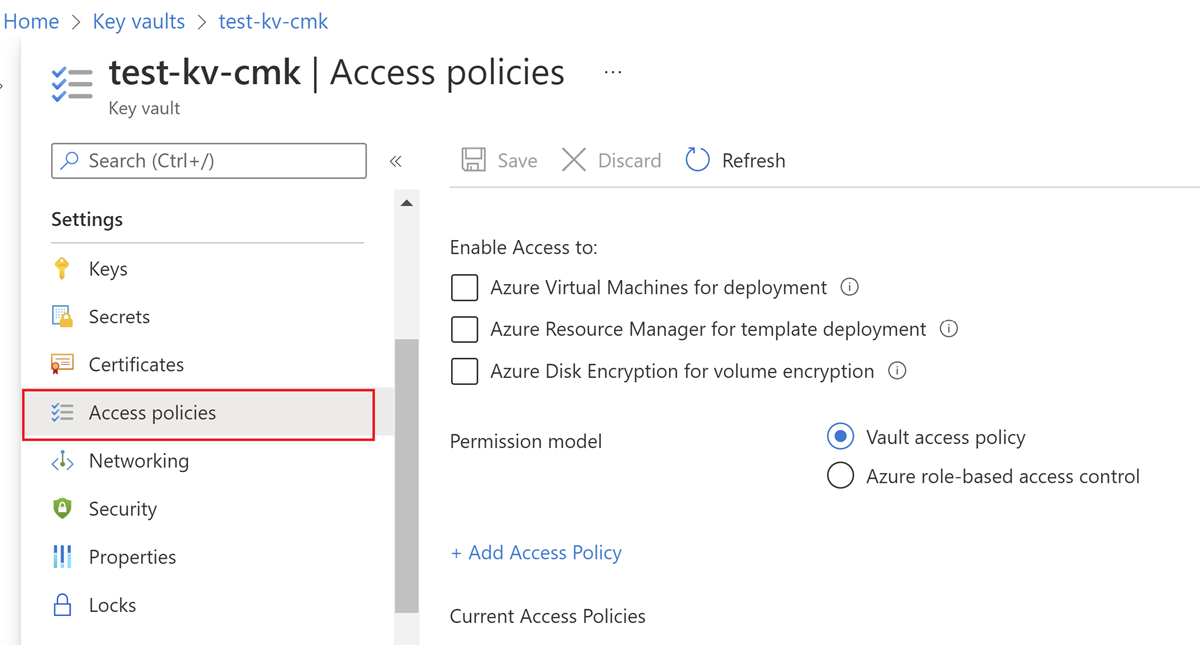
Select + Add Access Policy.
In the Key permissions drop-down menu, select Get, Unwrap Key, and Wrap Key permissions.
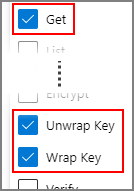
In Select principal, select None selected.
Search for the user-assigned managed identity you created earlier, and select it from the list.
Choose Select at the bottom.
Select Add to add the new access policy.
Select Save on the key vault instance to save all changes.
Use customer-managed keys with Azure Load Testing
You can only configure customer-managed encryption keys when you create a new Azure load testing resource. When you specify the encryption key details, you also have to select a user-assigned managed identity to retrieve the key from Azure Key Vault.
To configure customer-managed keys for a new load testing resource, follow these steps:
Follow these steps to create an Azure load testing resource in the Azure portal and fill out the fields on the Basics tab.
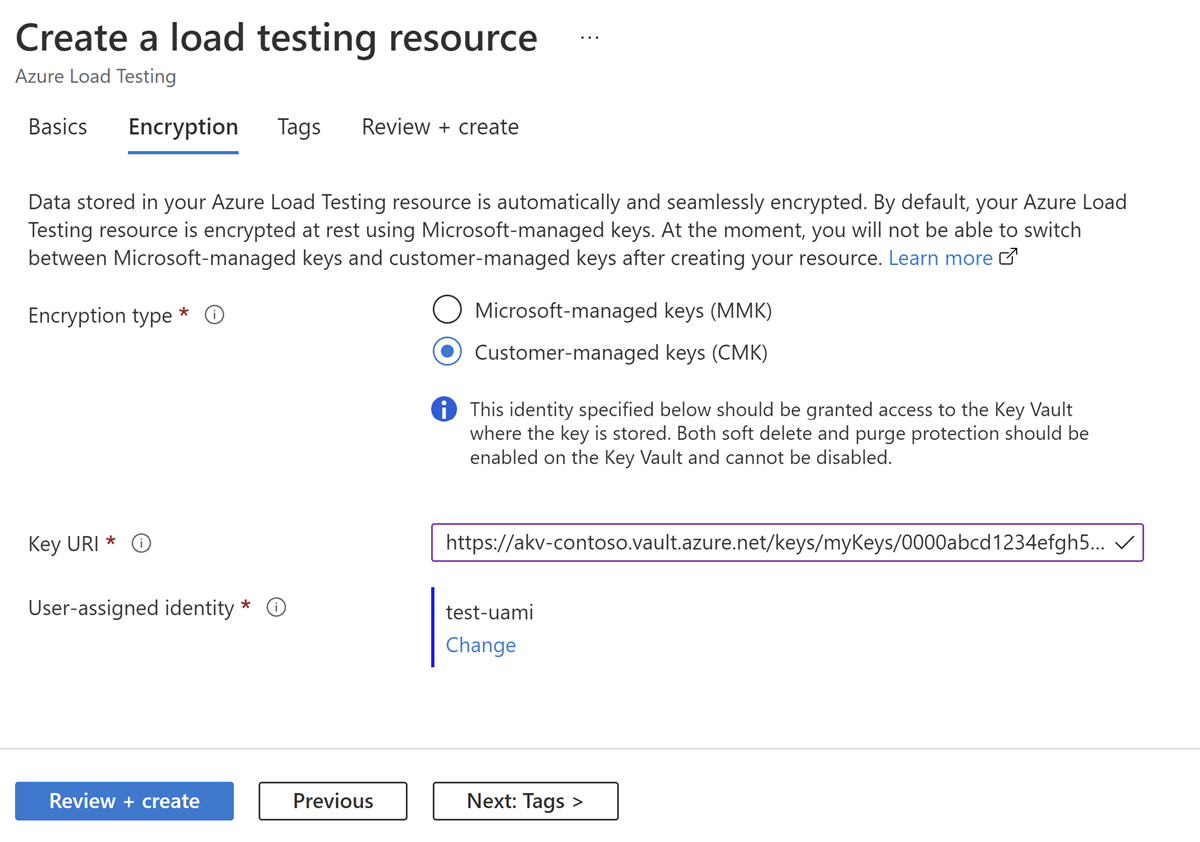
Go to the Encryption tab, and then select Customer-managed keys (CMK) for the Encryption type field.
In the Key URI field, paste the URI/key identifier of the Azure Key Vault key including the key version.
For the User-assigned identity field, select an existing user-assigned managed identity.
Select Review + create to validate and create the new resource.
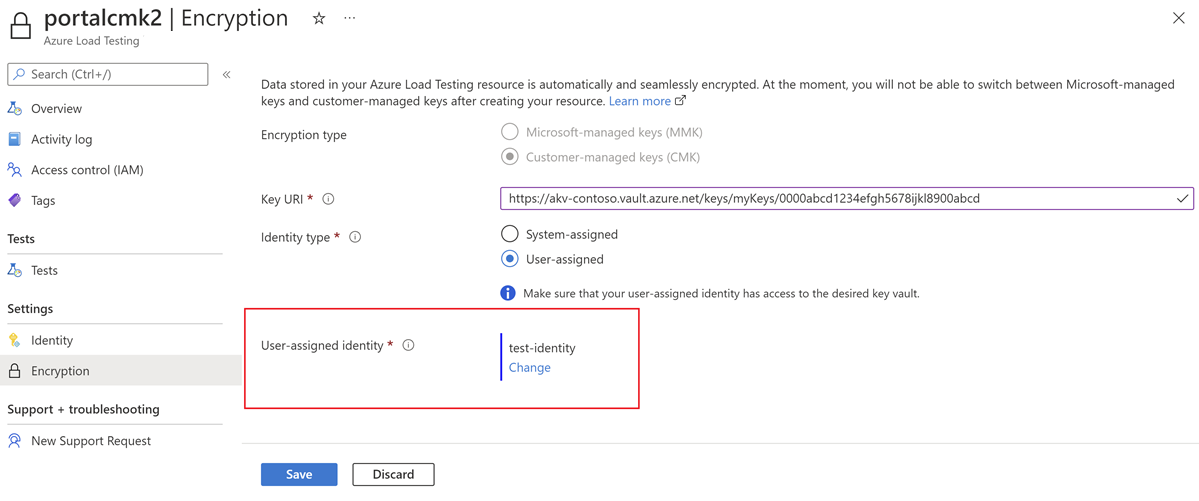
Change the managed identity for retrieving the encryption key
You can change the managed identity for customer-managed keys for an existing load testing resource at any time.
In the Azure portal, go to your Azure load testing resource.
On the Settings page, select Encryption.
The Encryption type shows the encryption type that was used for creating the load testing resource.
If the encryption type is Customer-managed keys, select the type of identity to use to authenticate to the key vault. The options include System-assigned (the default) or User-assigned.
To learn more about each type of managed identity, see Managed identity types.
- If you select System-assigned, the system-assigned managed identity needs to be enabled on the resource and granted access to the AKV before changing the identity for customer-managed keys.
- If you select User-assigned, you must select an existing user-assigned identity that has permissions to access the key vault. To learn how to create a user-assigned identity, see Use managed identities for Azure Load Testing Preview.
Save your changes.
Important
Make sure that the selected managed identity has access to the Azure Key Vault.
Update the customer-managed encryption key
You can change the key that you're using for Azure Load Testing encryption at any time. To change the key with the Azure portal, follow these steps:
In the Azure portal, go to your Azure load testing resource.
On the Settings page, select Encryption. The Encryption type shows the encryption selected for the resource while creation.
If the selected encryption type is Customer-managed keys, you can edit the Key URI field with the new key URI.
Save your changes.
Rotate encryption keys
You can rotate a customer-managed key in Azure Key Vault according to your compliance policies. To rotate a key:
- In Azure Key Vault, update the key version or create a new key.
- Update the customer-managed encryption key for your load testing resource.
Frequently asked questions
Is there an extra charge to enable customer-managed keys?
No, there's no charge to enable this feature.
Are customer-managed keys supported for existing Azure load testing resources?
This feature is currently only available for new Azure load testing resources.
How can I tell if customer-managed keys are enabled on my Azure load testing resource?
- In the Azure portal, go to your Azure load testing resource.
- Go to the Encryption item in the left navigation bar.
- You can verify the Encryption type on your resource.
How do I revoke an encryption key?
You can revoke a key by disabling the latest version of the key in Azure Key Vault. Alternatively, to revoke all keys from a key vault instance, you can delete the access policy granted to the managed identity of the load testing resource.
When you revoke the encryption key you may be able to run tests for about 10 minutes, after which the only available operation is resource deletion. It's recommended to rotate the key instead of revoking it to manage resource security and retain your data.
Related content
- Learn how to Monitor server-side application metrics.
- Learn how to Parameterize a load test with secrets and environment variables.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for