Effective security rules overview
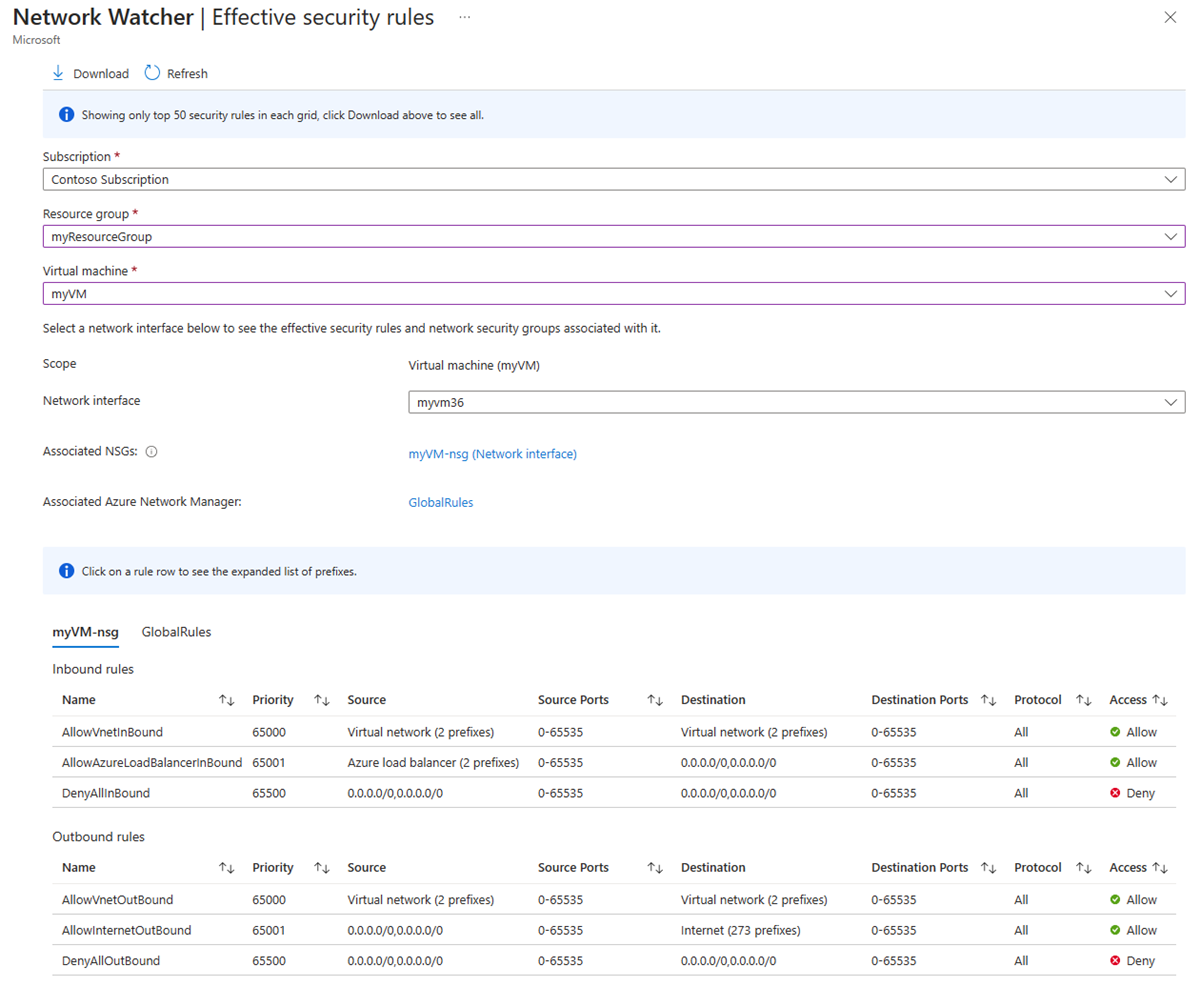
Effective security rules view is a feature in Azure Network Watcher that you can use to view the aggregated inbound and outbound rules applied to a network interface. It provides visibility into security and admin rules applied to a network interface. You can use this feature to troubleshoot connectivity issues and to audit security and compliance of your Azure network resources.
You can define a prescriptive set of security rules as a model for security governance in your organization. Then, you can implement a periodic compliance audit in a programmatic way by comparing the prescriptive rules with the effective rules for each of the virtual machines in your network.
The effective security rules applied to a network interface are an aggregation of the rules that exist in the network security group associated to a network interface and the subnet the network interface is in. For more information, see Network security groups and How network security groups filter network traffic. Additionally, the effective security rules include the admin rules that are applied to the virtual network using the Azure Virtual Network Manager. For more information, see Azure Virtual Network Manager.
Effective security rules in the Azure portal
In Azure portal, rules are displayed for each network interface and grouped by inbound vs outbound. A download button is available to easily download all the security rules into a CSV file.
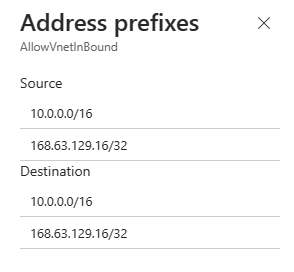
You can select a rule to see associated source and destination prefixes.
Next step
To learn how to use effective security rules, continue to:
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for