What is OSConfig for Linux devices?
IoT/Edge solution builders and operators often need to configure and observe device settings. Common examples include network settings, hostnames, time zones, security benchmarks, firewall rules, ssh users, and so on.
OSConfig for Linux is a compact (≈5MB) device side component which brings these configuration management capabilities directly into your Azure IoT workflows. Compared to alternative practices in the IoT/Edge space, using OSConfig together with Azure IoT or GitOps practices can:
- Reduce the number of device images you need to maintain, by allowing at-scale dynamic configuration at deploy time
- Reduce the frequency of full image updates, by allowing reconfiguration in the field for a specific device or devices at scale
- Eliminate heavy weight data center sever management tools from your IoT/Edge solution, by allowing for configuration management directly from Azure IoT
NOTE: OSConfig is part of Microsoft's suite of security and management capabilities for edge+cloud solutions. The suite covers threat management, workload management, configuration management, and update management. For more information, see: Microsoft security and management suite for Linux devices.
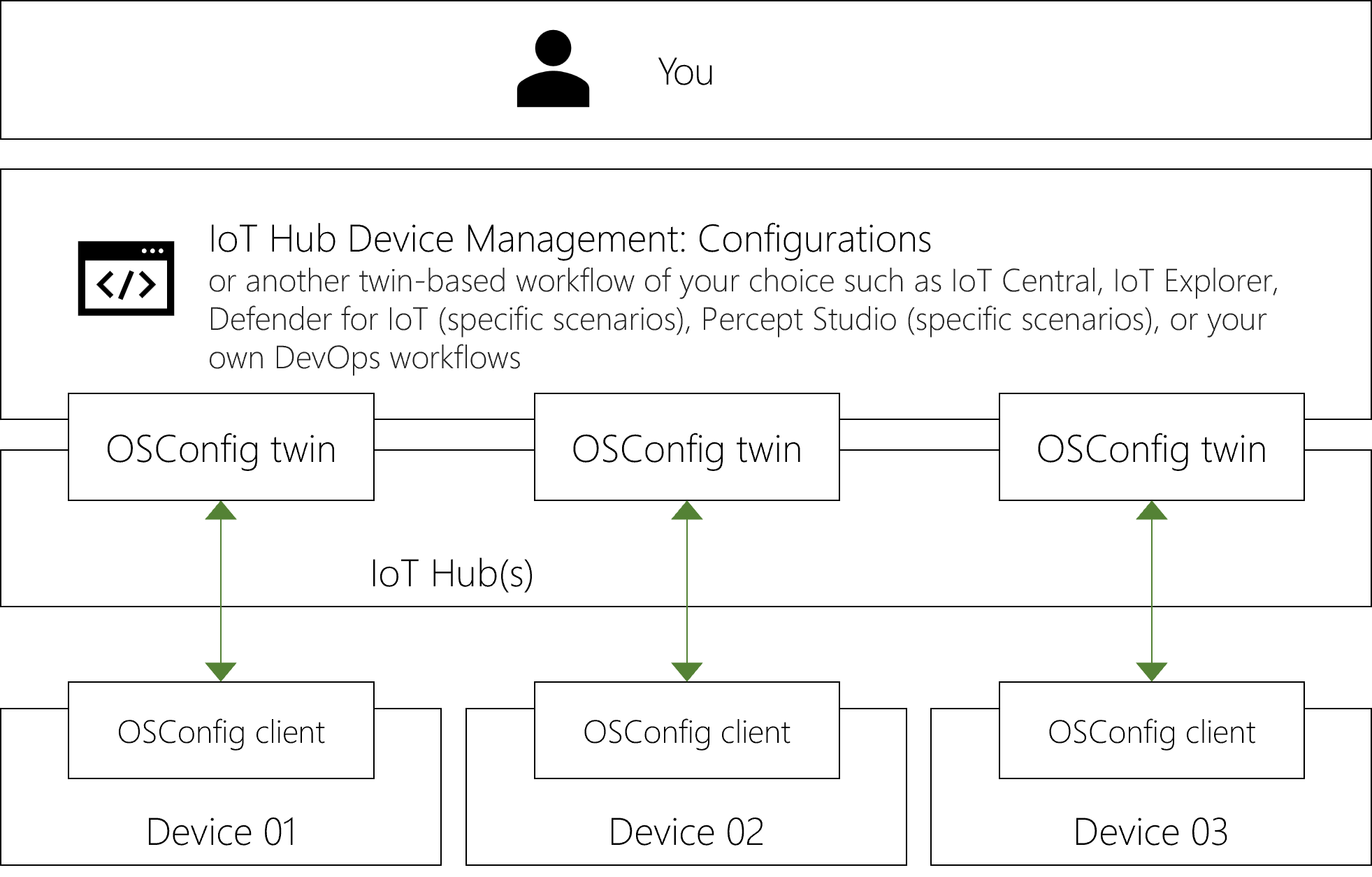
How it works with Azure IoT
The compact and efficient OSConfig agent for Linux runs on each device. It projects the device's configurable and observable properties into your Azure IoT Hub. This enables twin-based workflows (for example: IoT Explorer, Azure IoT Device Management Configurations, and Azure IoT Device Management Queries) to observe and configure the devices.
What can I provision and manage?
OSConfig includes a standard library of built-in capabilities. It also has a plug-in model so you can add or modify functionality for your unique devices.
The following are examples of scenarios you can accomplish using the built-in capabilities.
Network adapter and IP information
For reference information and hands-on examples, see: Working with network adapter status, IP addresses, etc., using OSConfig and Azure IoT.
- Inventory IP addresses for all devices
- Get the IP address of a device for troubleshooting, to connect and IP camera, etc.
- Get the DNS servers used by a device to investigate a name resolution issue
- Audit that all devices are using approved network infrastructure, to catch devices accidentally left connected to test networks, or connecting from an unexpected coffee shop
- Transition devices from static IP to DHCP as part of a deployment process
- Adapt to network infrastructure changes
Package manager configuration
For reference information and hands-on examples, see: Manage the OS package manager using Azure IoT and OSConfig.
- Ensure devices are using your private package repos for approved versions of libraries, etc.
- Dynamically point devices to vendor/partner package repos for specific packages
- Ensure that certain package are installed
- Compare installed packages state across a fleet of devices, and detect drift
Host name
For reference information and hands-on examples, see: Working with host names using Azure IoT and OSConfig.
- Set OS level host names to comply with standards or to ensure data and logs coming from devices can be evaluated in context
- Get OS level host names for inventory and audit
Hosts file
For reference information and hands-on examples, see: Working with /etc/hosts file using Azure IoT and OSConfig.
- Add hosts file entries to enable communication with on-prem infrastructure
- Dynamically provision specific entries based on device role or location
- Audit that devices have the desired entries present
Firewall
For reference information and hands-on examples, see: Manage host firewall with Azure IoT and OSConfig.
- Audit that host-based firewall is enabled across devices
- Audit that the cumulative rule set across devices matches a known-good fingerprint
- Ensure that environment specific rules like “deny all ssh inbound, except from my management subnet” are in place
- Make temporary changes to allow for developer and diagnostic access
- Adapt to changes in security landscape, such as blocking certain traffic based on a newly reported vulnerability
- Adapt to changes in app/workload requirements and network infrastructure, such as enabling access to a new HTTP endpoint
Device information including CPU, OS, TPM, device vendor, and more
For reference information and hands-on examples, see: Report hardware and OS information with Azure IoT and OSConfig.
- Report on OS distros and versions across your fleet
- Target IoT Hub Configurations by reported properties for CPU architecture, OS, etc.
- For heterogenous fleets, discover which devices have TPM capabilities
- For devices with TPM, audit that TPM is active and interfacing with OS as expected
Reboot and Shutdown
For reference information and hands-on examples, see: Reboot or shut down devices with Azure IoT and OSConfig.
- Reboot or shut down misbehaving device
- Coordinate maintenance reboots across many devices
Azure Device Health Service (ADHS) governance
- Set and audit the opt-in level for the ADHS diagnostic data service
Delivery Optimization governance
- Set and audit Delivery Optimization parameters such as Microsoft Connected Cache URLs, throttling, and so on
Custom configuration at scale
For reference information and hands-on examples, see: Custom configuration and reporting with Azure IoT and OSConfig and How to interact with the CommandRunner feature of OSConfig and Azure IoT.
- Run a custom script to configure workloads, OS components, files, etc.
- Configure OS time zones across all devices, for example to ensure that data and logs coming from the device are stamped with organization standard timestamps
- Configure network time source across all devices, to ensure that devices stay in sync with organization standard timekeeping, and don’t use rogue time sources
- Configure package manager settings, such as adding trusted package repositories as sources
- Your imagination is the limit; custom configurations are based on shell commands
Custom reporting at scale, and remote diagnostics
For reference information and hands-on examples, see: Custom configuration and reporting with Azure IoT and OSConfig and How to interact with the CommandRunner feature of OSConfig and Azure IoT.
- Run a custom command to get any information from the devices
- Audit that a certain daemon is running on all devices
- Audit that devices can regularly ping a certain endpoint which is important to your solution
- Your imagination is the limit; custom reporting is based on shell commands
- Verify that a device is alive
- Run diagnostic and developer commands on a device
Next steps
- For immediate hands-on experience with OSConfig, see: Create an OSConfig (with Azure IoT) lab environment in 5 minutes
- For recommended articles based on your context, see: Audiences for OSConfig documentation
- To extend OSConfig with new functionality (or to customize for specific devices), see our GitHub repo at: azure-osconfig