Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Learn how to configure ArcGIS Pro to access geospatial datasets from the Microsoft Planetary Computer Pro GeoCatalog by using OAuth 2.0-delegated authentication with Microsoft Entra ID.
This process requires that you:
- Register two applications in Microsoft Entra ID (a web API and a desktop client).
- Configure delegated permissions with the
user_impersonationscope. - Connect ArcGIS Pro to Azure Blob Storage and SpatioTemporal Asset Catalog (STAC)-compliant datasets in the Microsoft Planetary Computer Pro environment.
Learn how to securely browse and access data hosted in Microsoft Planetary Computer Pro directly in ArcGIS Pro by using Microsoft Entra ID user impersonation.
Prerequisites
- Access to a Microsoft Entra ID tenant
- Azure subscription with permissions to manage app registrations
- ArcGIS Pro installed on your machine
Tip
Before you begin, review background information in Register an application in Microsoft Entra ID.
Register a web API application for ArcGIS Pro
Open the Azure portal and search for Entra. Select Microsoft Entra ID.
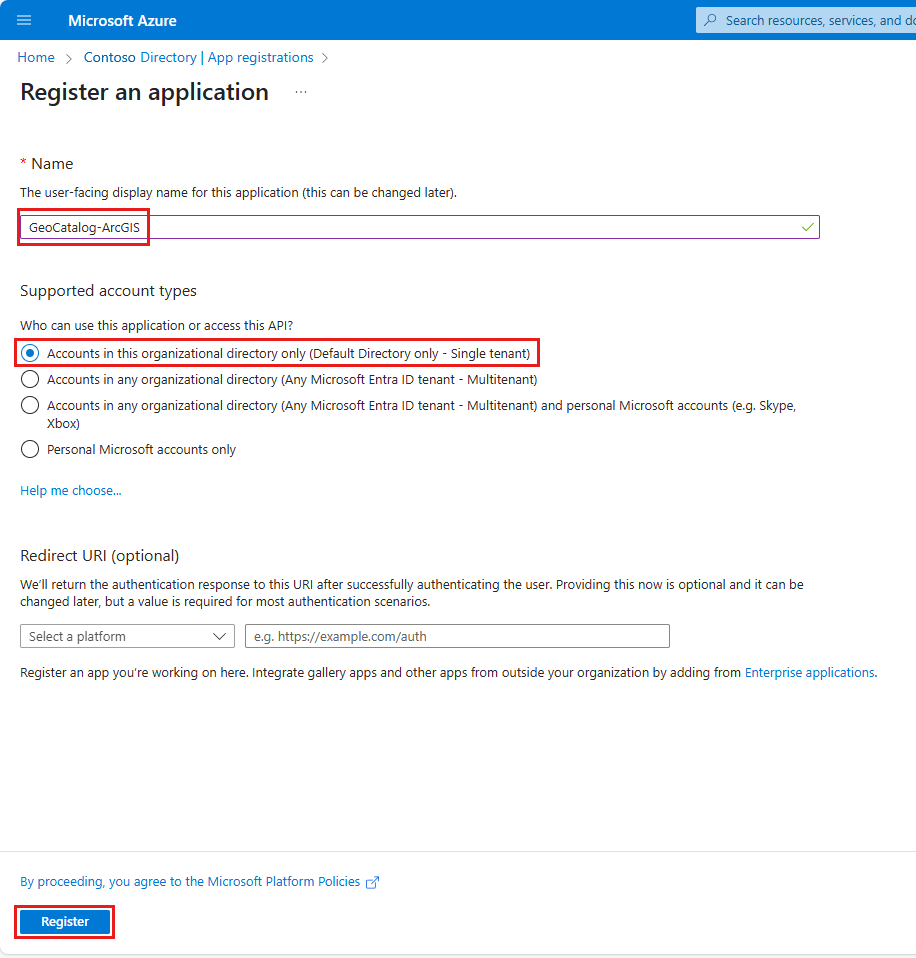
Go to App registrations > New registration.
Register the Web API app. Here are some name suggestions:
- ArcGISPro-GeoCatalog-WebAPI
- ArcGIS Pro
Under Supported account types, select Accounts in any organizational directory (Any Microsoft Entra ID tenant - Multitenant).
In your new app (named ArcGIS Pro in our example), go to Authentication > Add a platform > Web.
In Configure Web > Redirect URI, add
<https://localhost>. Select Configure.Return to Authentication > Add a platform, and then select Mobile and desktop applications.
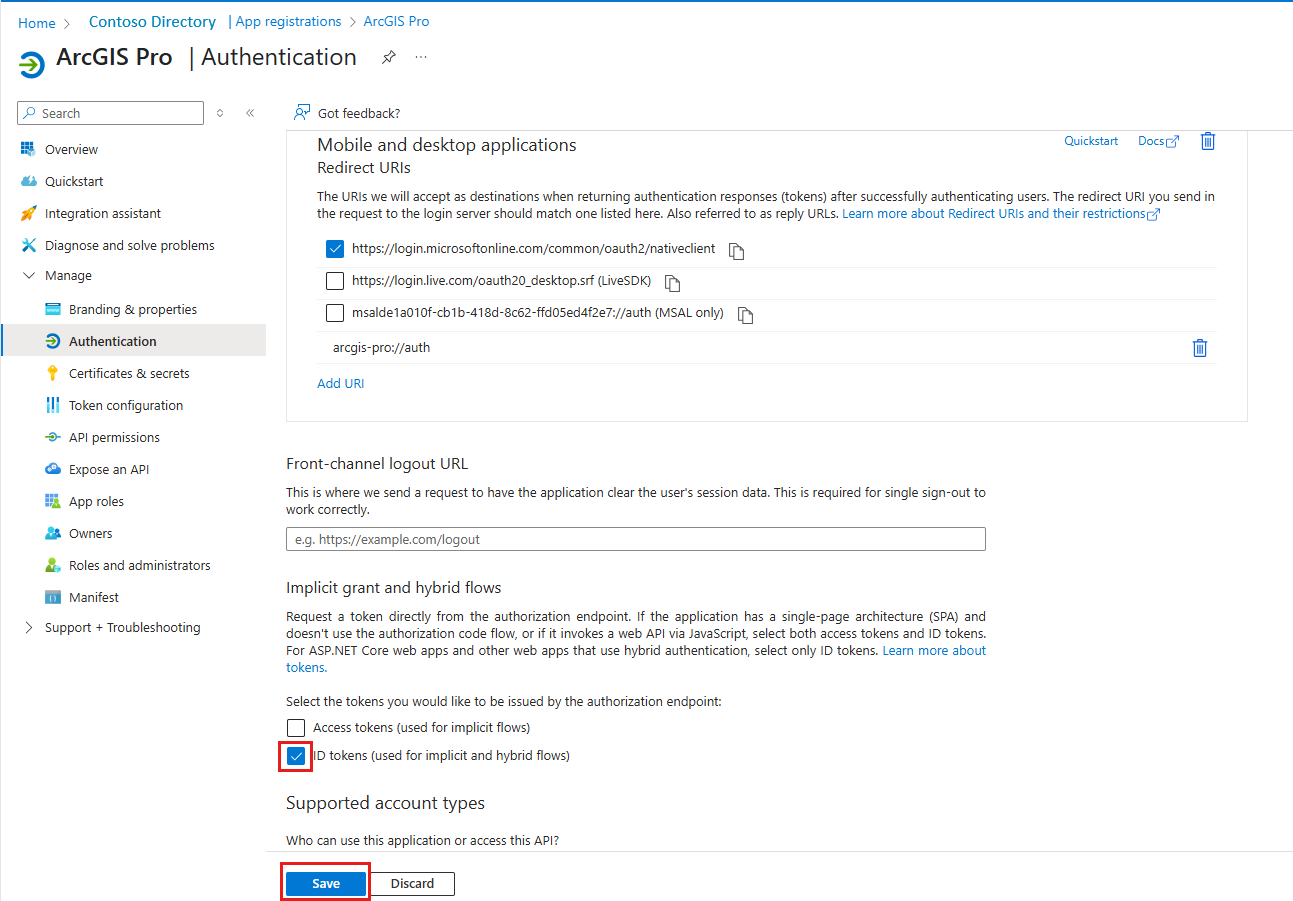
In Configure Web > Redirect URI, add
arcgis-pro://auth. Select Configure.Under Implicit grant and hybrid flows, select the checkbox for ID tokens (used for implicit and hybrid flows). Select Save.
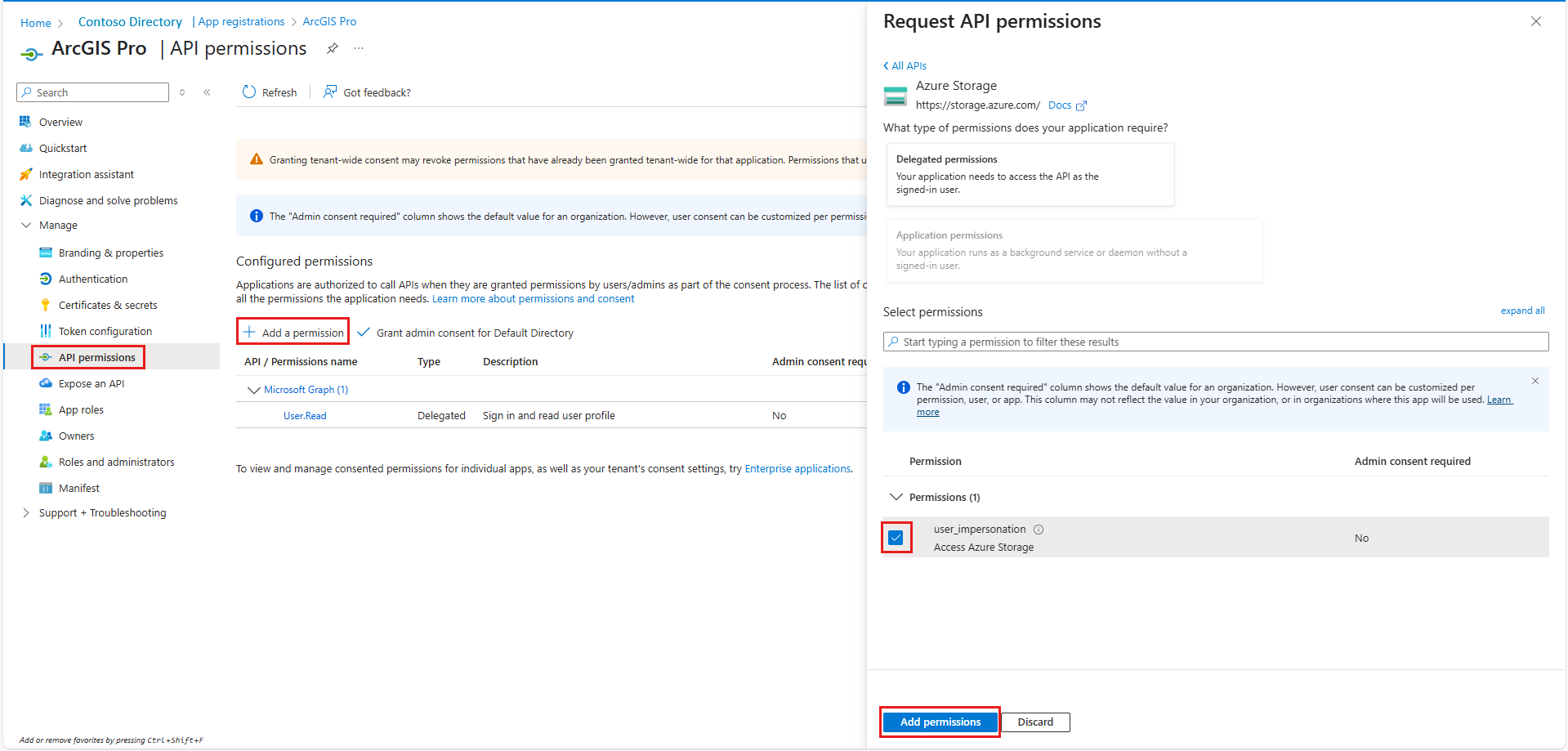
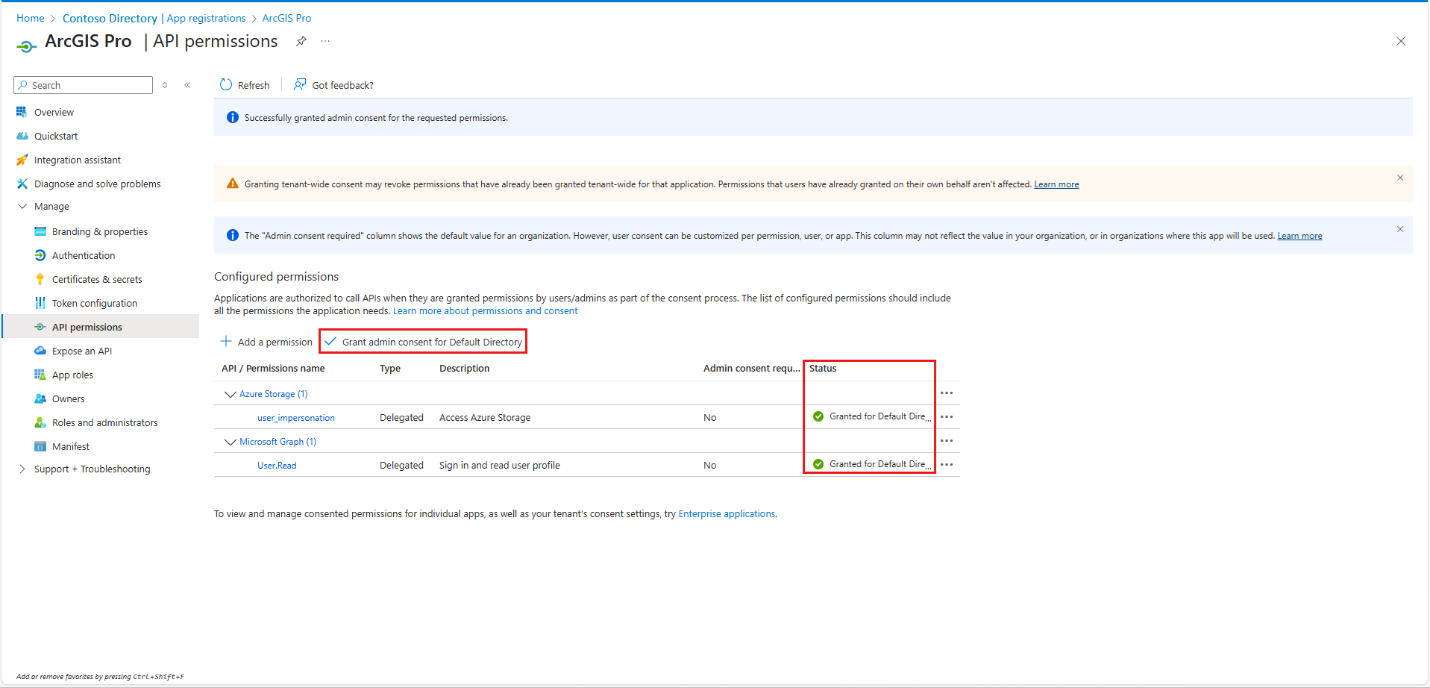
Select API Permissions on the left menu. Add and grant admin consent for:
- Azure Storage > user_impersonation
- Microsoft Graph > User.Read (default)
After you add permissions, select Grant admin consent for Default Directory.
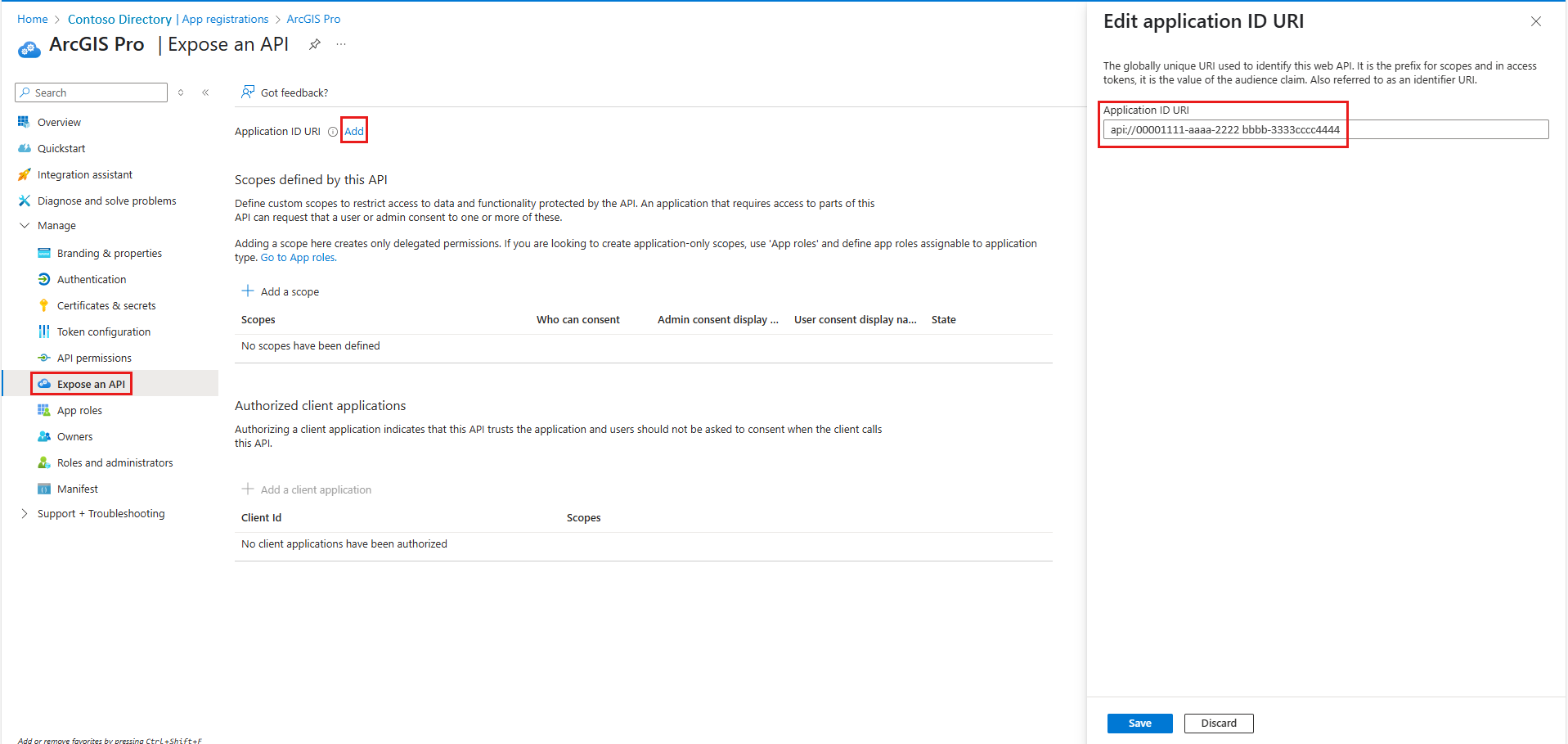
On the left menu, select Expose an API > Add. Under Edit application ID URI add your app's URI in Application ID URI.
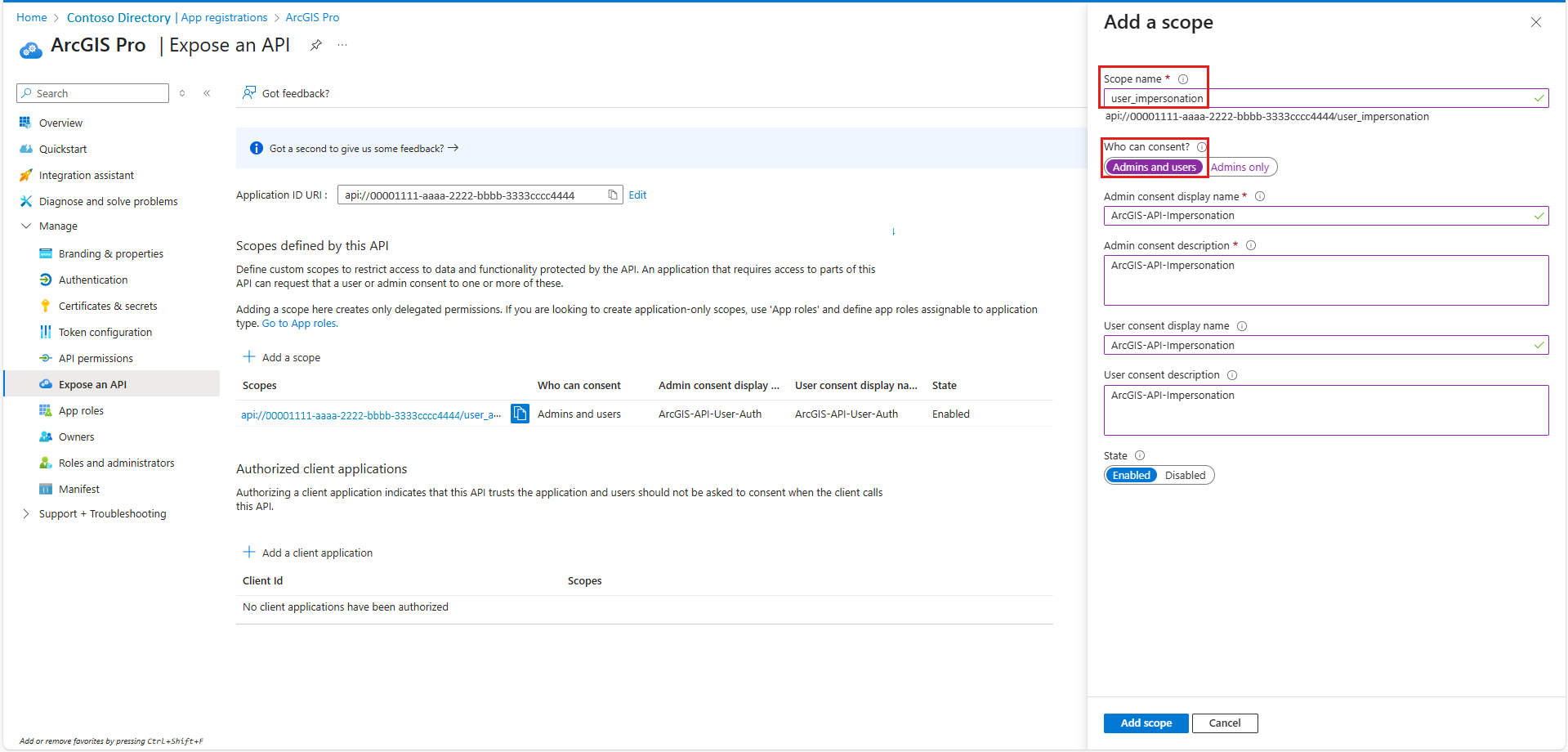
Select Add a scope and add the following information:
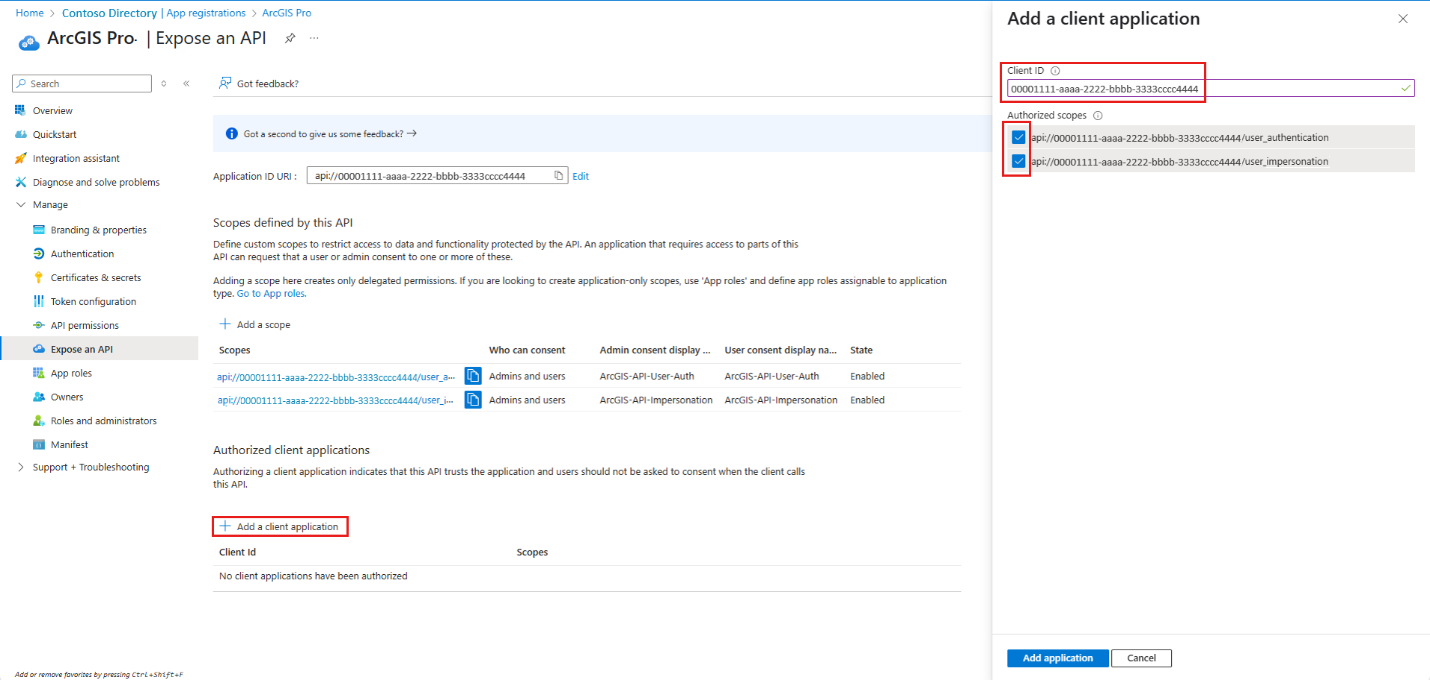
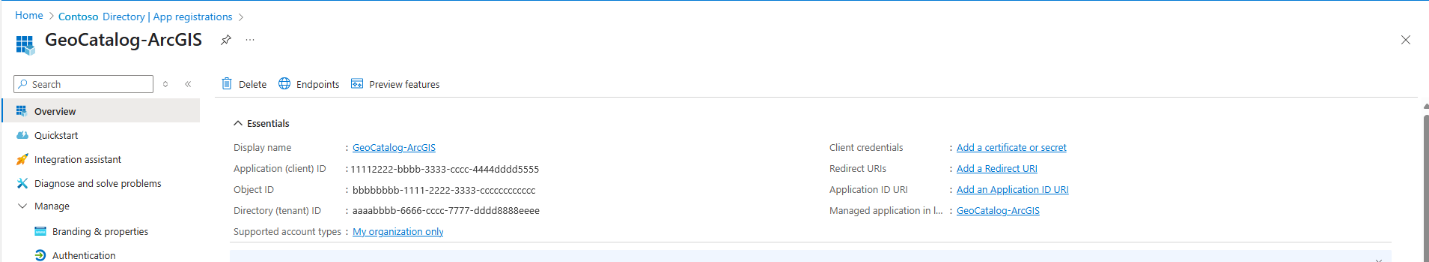
Select Add a client application. Choose and take note of the client ID. You need the client ID to set up an authentication connection in ArcGIS Pro.
Register a desktop client application for ArcGIS Pro
After you register your first application, register a second (with a distinct name). The second app represents ArcGIS Pro Desktop and configures its API permissions. Ensure that the new app can access the web API that you exposed with the first application.
Create a second app registration for the ArcGIS Pro desktop client with one of these suggested names: ArcGISPro-GeoCatalog-DesktopClient or GeoCatalog-ArcGIS. Set the account type by selecting Single tenant.
Configure the desktop client app. In this example, we use the name GeoCatalog-ArcGIS. Repeat the steps from the first app registration:
- For Add a platform, select Web.
- For Redirect URI, add
<https://localhost>. - For Add a platform, select Mobile and desktop applications.
- For Redirect URI, add
arcgis-pro://auth. - Under Implicit grant and hybrid flows, select ID tokens (used for implicit and hybrid flows). Select Save.
Add access to the web API app:
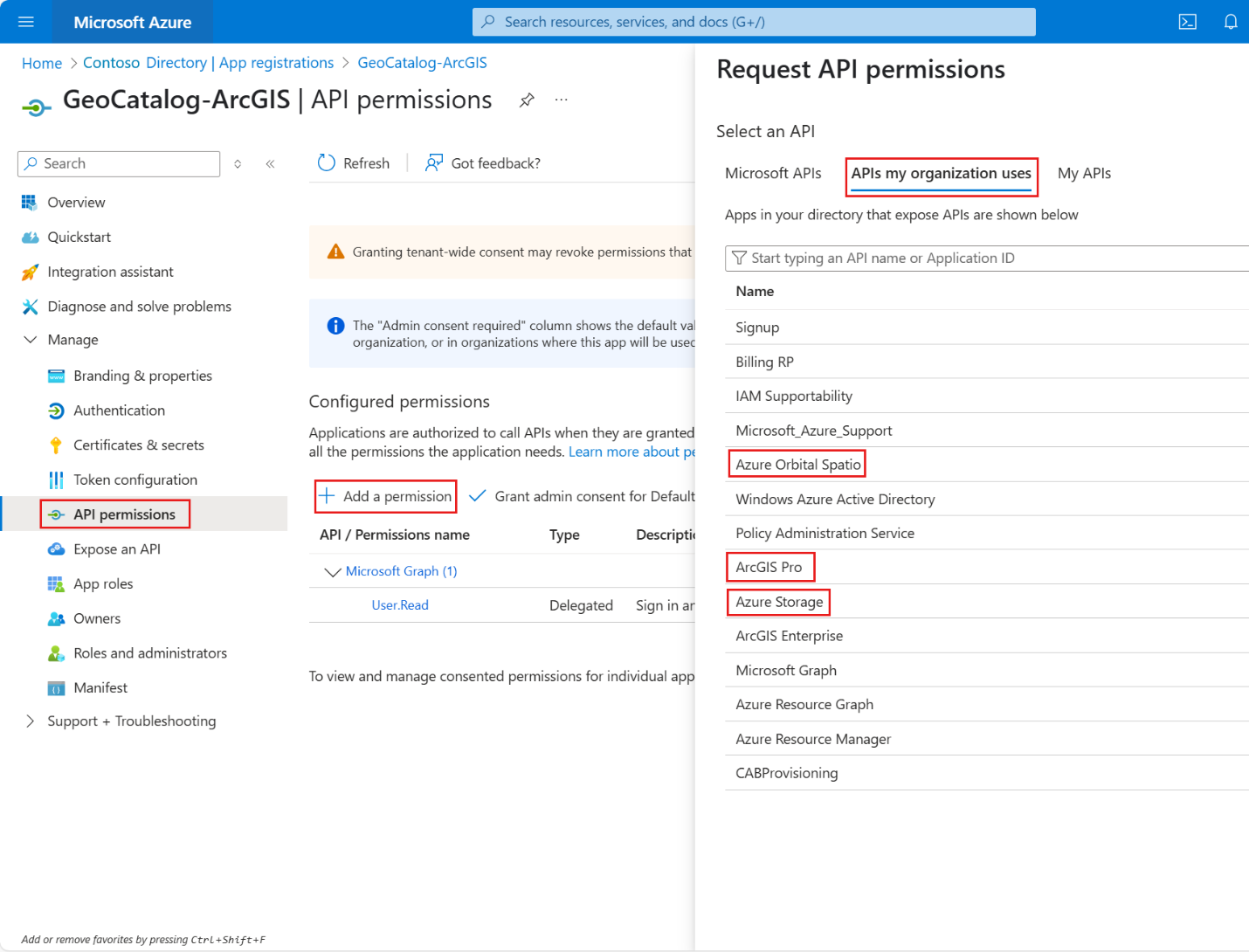
On the API permissions tab, select Add a permission.
Go to the APIs my organization uses tab and search for the Web API app that you created previously (for example, ArcGIS Pro).
Select the app name to open the Request API Permissions screen.
Select both user_authentication and user_impersonation, the delegated permissions that you defined in the first app.
Select Add permissions.
Add the following delegated permissions:
- Azure Storage > user_impersonation
- Azure Orbital Spatio > user_impersonation
- Microsoft Graph > User.Read (enabled by default)
- Add permissions
- Grant admin consent
Configure ArcGIS Pro (desktop) for Microsoft Planetary Computer Pro GeoCatalog access
This section outlines how to configure authentication and data access in the ArcGIS Pro desktop application. You use OAuth 2.0 integration with Microsoft Entra ID and access the Microsoft Planetary Computer Pro GeoCatalog. This section includes steps to add an authentication connection and create storage and STAC data connections.
Add an authentication connection
Go to the ArcGIS Pro settings page in one of the following ways:
- From an open project, select the Project tab on the ribbon.
- From the start page, select the Settings tab.
On the left menu, select Options.
Go to Options > Application > Authentication.
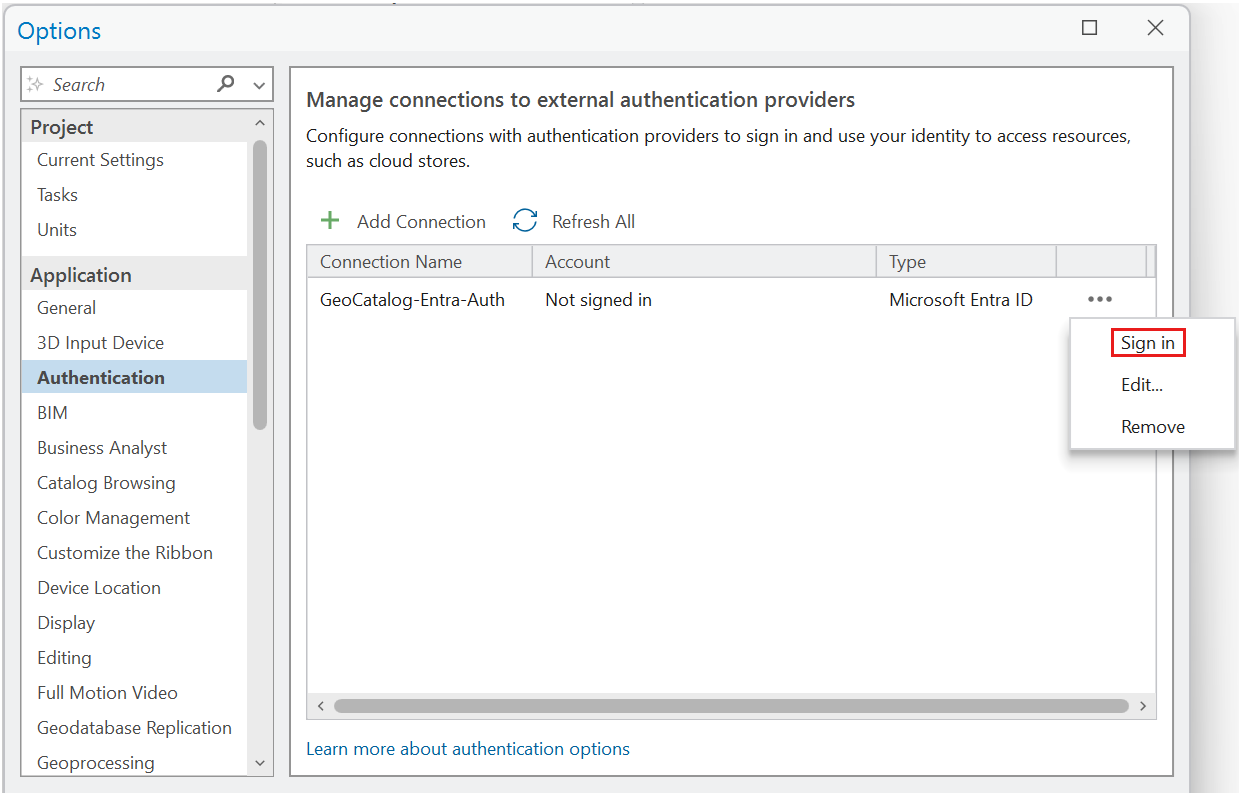
Select Add Connection.
Enter a value in the Connection Name field.
For Type, select Microsoft Entra ID.
Enter values in the Entra Domain and Client ID fields.
- You can find your Microsoft Entra ID domain (also known as your primary domain) from Microsoft Entra ID in the Azure portal.
- For Client ID, enter the client ID you set in the Add a client application step.
Add the following values in the Scopes fields:
https://storage.azure.com/.defaulthttps://geocatalog.spatio.azure.com/.default
Select OK.
Sign in through the Authentication dialog and complete the prompts.
Tip
For more information, see the documentation: Connect to authentication providers from ArcGIS Pro.
Prepare and record GeoCatalog information
GeoCatalog URI, collection name, and token API endpoint
Create a Microsoft Planetary Computer Pro GeoCatalog in your Azure subscription (for example, arcgisprogeocatalog), and locate it in the appropriate resource group.
Select the GeoCatalog that you created.
Copy the value of its GeoCatalog URI. For example,
https://arcgisprogeocatalog.<unique-identity>.<cloud-region>.geocatalog.spatio.azure.com.Paste the link for your GeoCatalog URI in the browser and select the Collections button.
Record the value in Collection Name. For example,
sentinel-2-l2a-tutorial-1000.Construct the token API endpoint by using this pattern:
<GeoCatalog URI>/sas/token/<Collection Name>?api-version=2025-04-30-preview. For example:https://arcgisprogeocatalog.<unique-identity>.<cloud-region>.geocatalog.spatio.azure.com/sas/token/sentinel-2-l2a-tutorial-1000?api-version=2025-04-30-preview.
Find and record the storage location
Each collection within the Microsoft Planetary Computer Pro GeoCatalog stores geospatial data and STAC Item assets in a dedicated storage account and Azure blob container. In the following steps, you find and record the storage account and container names for a specific collection.
Note
An Azure Storage account and blob container are discoverable only after STAC Items or other assets are added to a collection.
There are two easy ways to discover the storage account and blob container for a collection: by using a thumbnail or by using a STAC Item with assets.
Discover the storage account by using a collection thumbnail
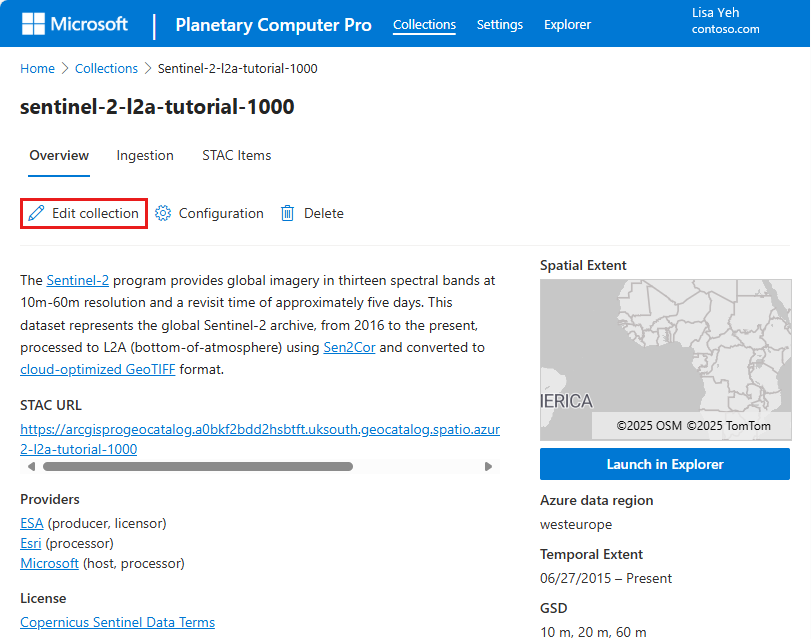
From a specific Collections page, select the value for Collection Name.
Select the Edit collection button.
In the resulting JSON display, locate the key
title:assets:thumbnail:hrefand copy the corresponding value. For example:https://<unique-storage>.blob.core.windows.net/sentinel-2-l2a-tutorial-1000-<unique-id>/collection-assets/thumbnail/lulc.pngRecord the values under Account Name and Container Name. For example:
- (Storage) Account Name:
<unique-storage> - Container Name:
sentinel-2-l2a-tutorial-1000-<unique-id>
- (Storage) Account Name:
Discover the storage account by using a STAC Item
From a specific Collections page, select STAC Items.
Select the checkbox next to one of the listed STAC Items.
Scroll to the bottom of the STAC Item right panel and select the link to retrieve the STAC Item JSON.
Find the object called
assetswithin the STAC Item JSON specification. Select one of the asset types within this object and find thehrefkey."assets": { "image": { "href": "https://<unique-storage>.blob.core.windows.net/naip-sample-datasets-<unique-id>/12f/va_m_3807708_sw_18_060_20231113_20240103/image.tif", } }Record the value for Account Name and Container Name. For example:
- (Storage) Account Name:
<unique-storage> - Container Name:
naip-sample-datasets-<unique-id>
- (Storage) Account Name:
Set up a connection to Azure Blob Storage
In ArcGIS Pro, open the Create Cloud Storage Connection File geoprocessing tool to create a new ACS connection file. You can access this tool in the main ribbon on the Analysis tab. Select Tools, and then search for the tool by typing its name.
Specify a value for the Connection File Location for the ACS file.
Provide a name for Connection File. For example, geocatalog_connection.acs.
Select Service Provider > Azure.
For Authentication, select the name of the auth profile that you used earlier.
For Access Key ID (Account Name), use the Account Name value that you recorded earlier:
<unique-storage>.For Bucket (Container) Name use the Container Name value that you recorded earlier:
sentinel-2-l2a-tutorial-1000-<unique-id>.Don't specify a value for Folder.
Add the provider option ARC_TOKEN_SERVICE_API and set the value to the token API endpoint that you constructed earlier. For example:
https://arcgisprogeocatalog.<unique-identity>.<cloud-region>.geocatalog.spatio.azure.com/sas/token/sentinel-2-l2a-tutorial-1000?api-version=2025-04-30-previewAdd the provider option ARC_TOKEN_OPTION_NAME and set the value to AZURE_STORAGE_SAS_TOKEN.
Create a STAC connection to Microsoft Planetary Computer Pro
Tip
Refer to the ArcGIS Pro documentation Create a STAC connection.
Provide a name in STAC Connection. For example, GeoCatalog_Connection.
For Connection, use the form
<GeoCatalog URI>/stac. For example:https://arcgisprogeocatalog.<unique-identity>.<cloud-storage>.geocatalog.spatio.azure.com/stacReference the authentication settings that you created in the previous step.
Add values for Custom Parameters:
- Name:
api-version - Value:
2025-04-30-preview
- Name:
Add the ACS connection file that you created in the previous step to the Cloud Storage Connections list. Select OK.
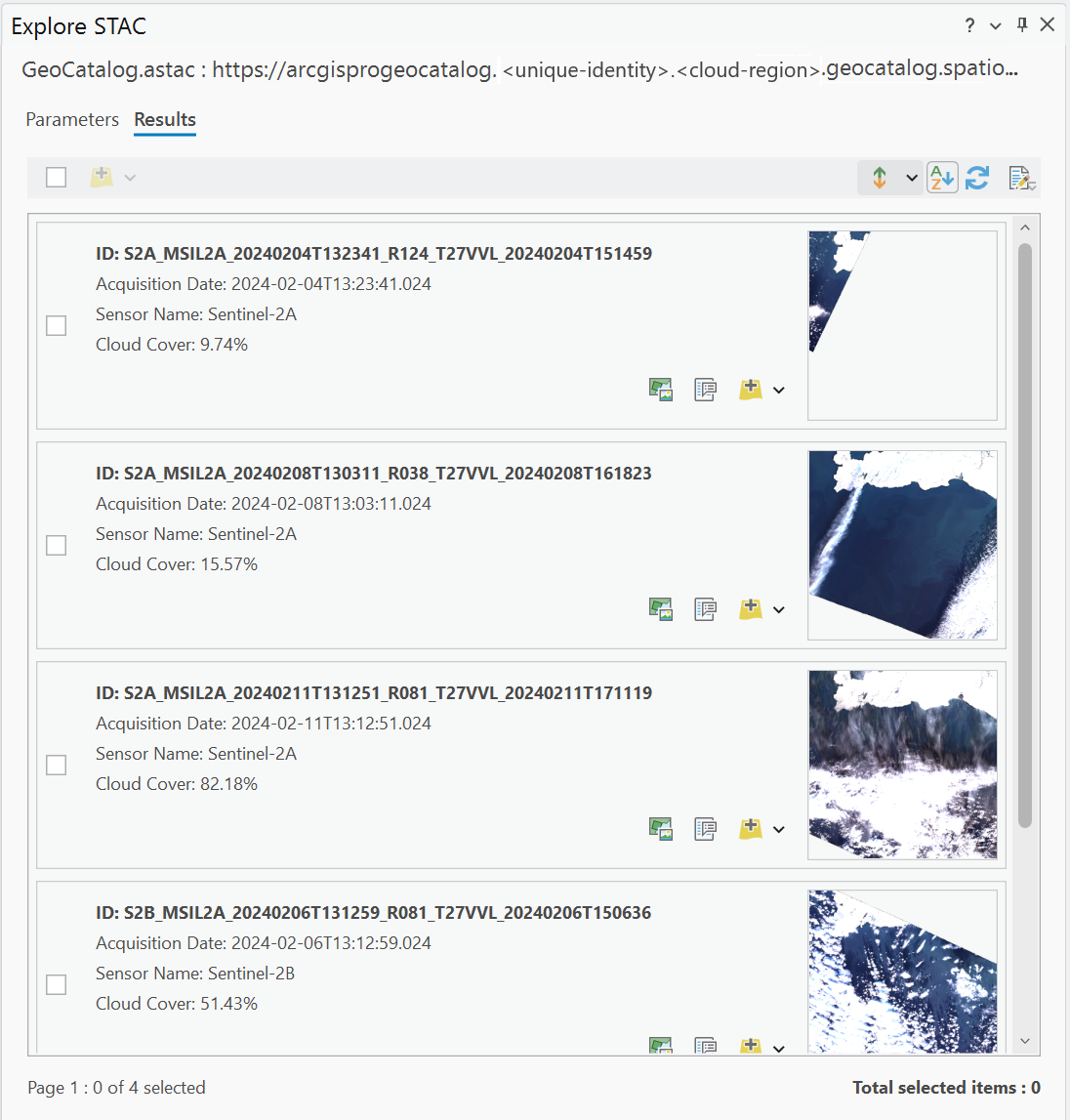
Explore the STAC connection.
Tip
Learn more about the ArcGIS Explore STAC pane.
Search, fetch extensive STAC metadata, and view and browse images.
Add selected images to the Map or Scene functions.