Provision read access to Azure SQL Database using Microsoft Purview Data owner policies (preview)
Important
This feature is currently in preview. The Supplemental Terms of Use for Microsoft Azure Previews include additional legal terms that apply to Azure features that are in beta, in preview, or otherwise not yet released into general availability.
Data owner policies are a type of Microsoft Purview access policies. They allow you to manage access to user data in sources that have been registered for Data Policy Enforcement in Microsoft Purview. These policies can be authored directly in the Microsoft Purview governance portal, and after publishing, they get enforced by the data source.
This guide covers how a data owner can delegate authoring policies in Microsoft Purview to enable access to Azure SQL Database. The following actions are currently enabled: Read. Modify isn't supported at this point.
Prerequisites
An Azure account with an active subscription. Create an account for free.
A new or existing Microsoft Purview account. Follow this quickstart guide to create one.
- Create a new Azure SQL Database instance, or use an existing one, in one of the currently available regions for this feature. You can follow this guide to create an Azure SQL Database instance.
Region support
All Microsoft Purview regions are supported.
Enforcement of Microsoft Purview policies is available only in the following regions for Azure SQL Database:
Public cloud:
- East US
- East US2
- South Central US
- West Central US
- West US3
- Canada Central
- Brazil South
- West Europe
- North Europe
- France Central
- UK South
- South Africa North
- Central India
- South East Asia
- East Asia
- Australia East
Sovereign clouds:
- USGov Virginia
- China North 3
Configure the Azure SQL Database instance for policies from Microsoft Purview
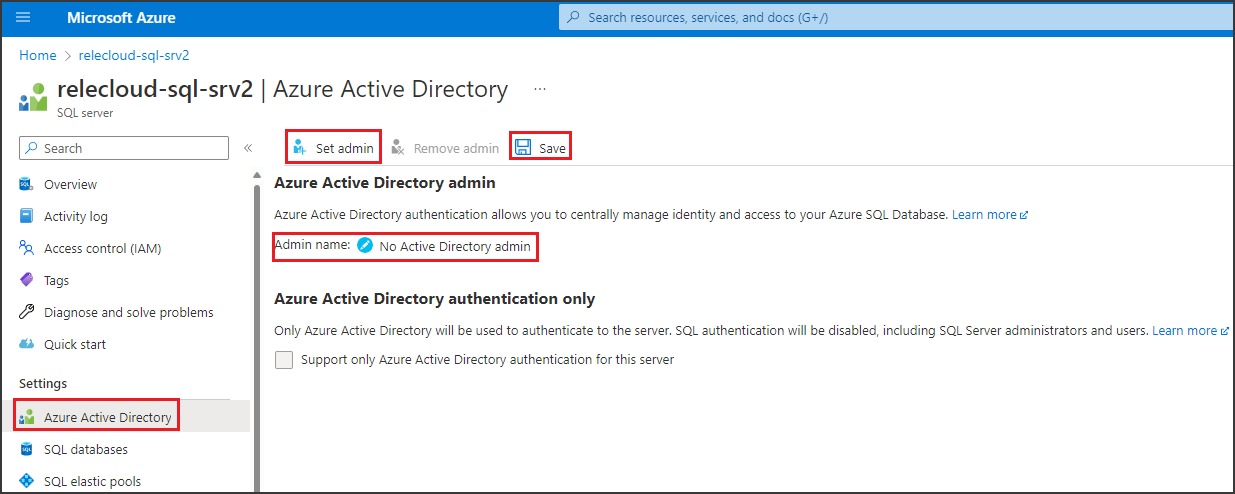
For the logical server associated with Azure SQL Database to honor policies from Microsoft Purview, you need to configure a Microsoft Entra admin. In the Azure portal, go to the logical server that hosts the Azure SQL Database instance. On the side menu, select Microsoft Entra ID. Set an admin name to any Microsoft Entra user or group that you prefer, and then select Save.
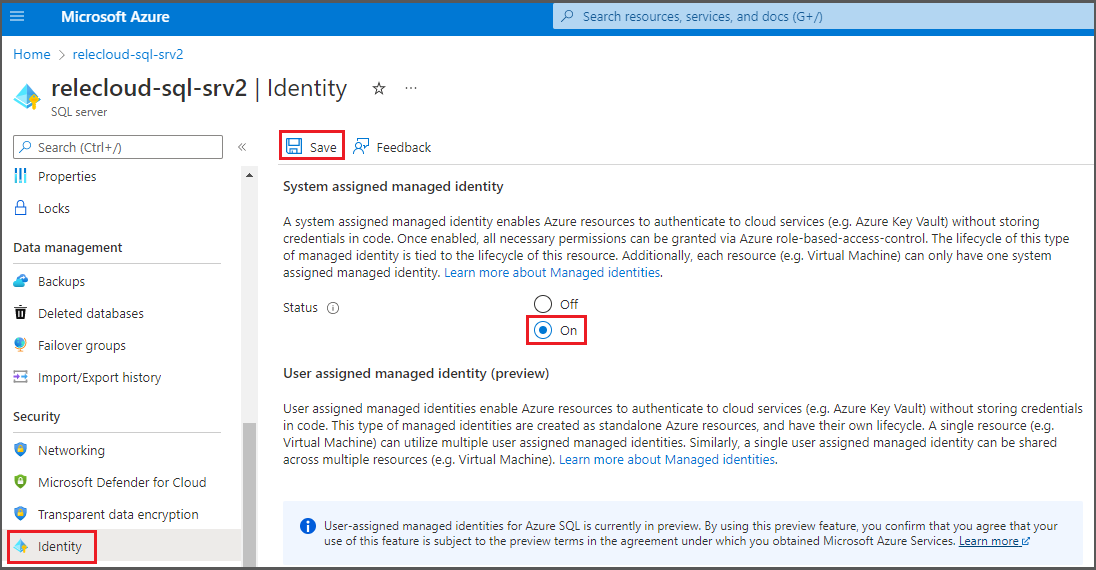
Then, on the side menu, select Identity. Under System assigned managed identity, turn the status to On, and then select Save.
Microsoft Purview configuration
Register the data source in Microsoft Purview
Before a policy can be created in Microsoft Purview for a data resource, you must register that data resource in Microsoft Purview Studio. You will find the instructions related to registering the data resource later in this guide.
Note
Microsoft Purview policies rely on the data resource ARM path. If a data resource is moved to a new resource group or subscription it will need to be de-registered and then registered again in Microsoft Purview.
Configure permissions to enable Data policy enforcement on the data source
Once a resource is registered, but before a policy can be created in Microsoft Purview for that resource, you must configure permissions. A set of permissions are needed to enable the Data policy enforcement. This applies to data sources, resource groups, or subscriptions. To enable Data policy enforcement, you must have both specific Identity and Access Management (IAM) privileges on the resource as well as specific Microsoft Purview privileges:
You must have either one of the following IAM role combinations on the resource's Azure Resource Manager path or any parent of it (that is, using IAM permission inheritance):
- IAM Owner
- Both IAM Contributor and IAM User Access Administrator
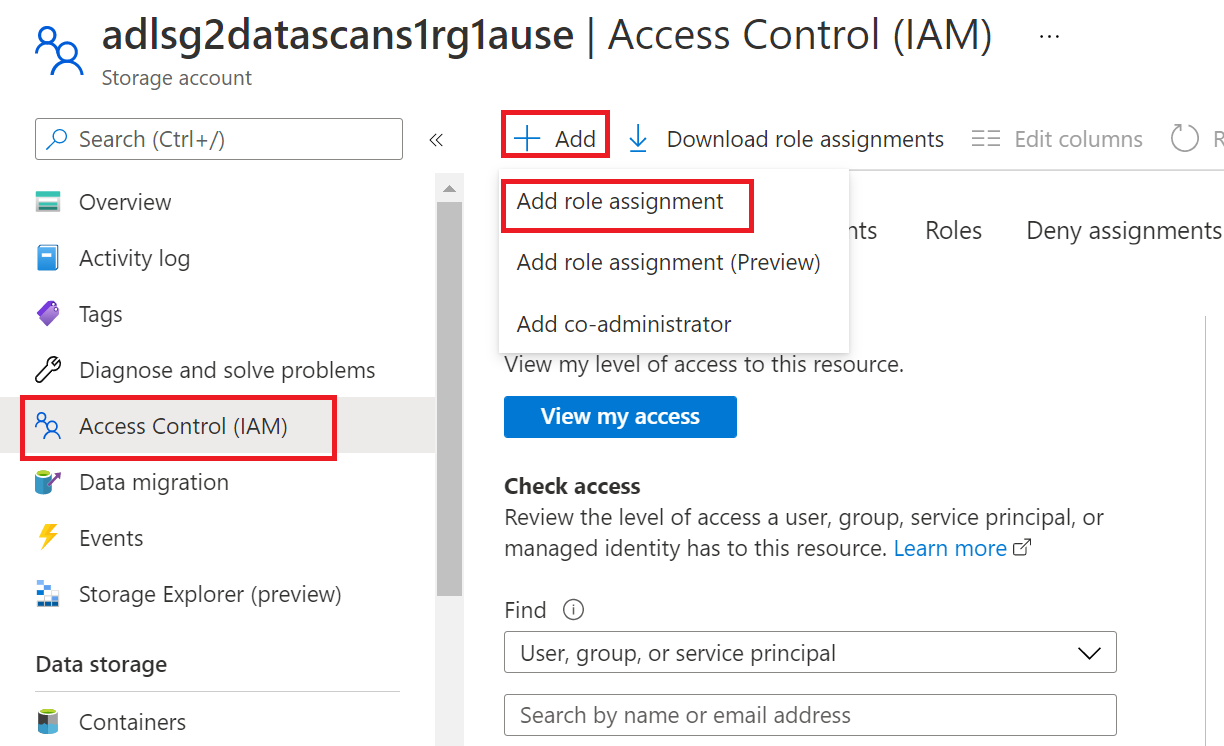
To configure Azure role-based access control (RBAC) permissions, follow this guide. The following screenshot shows how to access the Access Control section in the Azure portal for the data resource to add a role assignment.
Note
The IAM Owner role for a data resource can be inherited from a parent resource group, a subscription, or a subscription management group. Check which Microsoft Entra users, groups, and service principals hold or are inheriting the IAM Owner role for the resource.
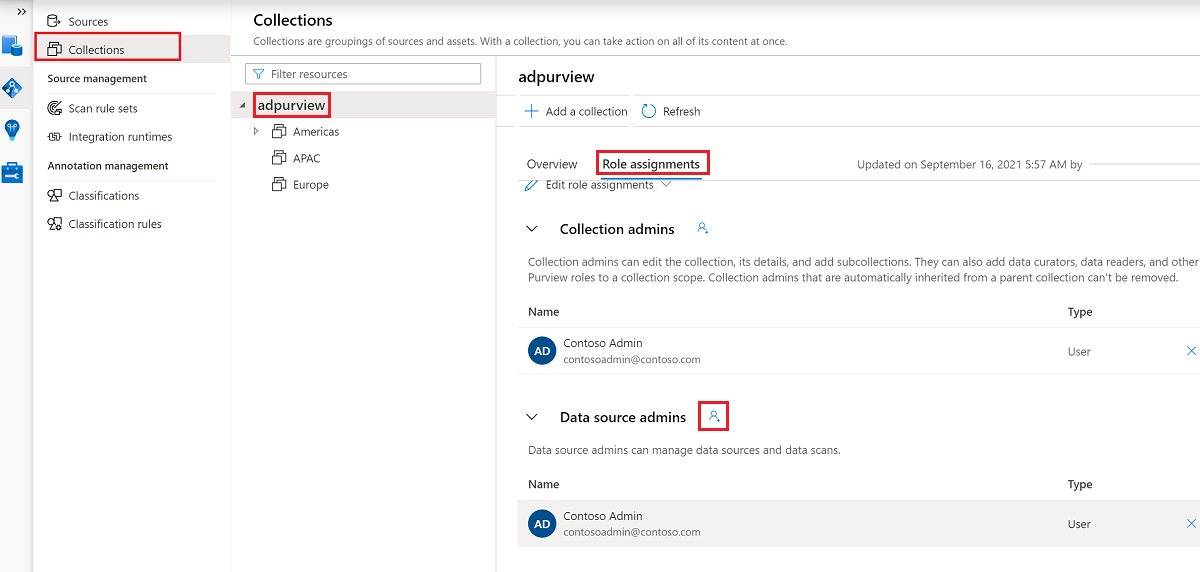
You also need to have the Microsoft Purview Data source admin role for the collection or a parent collection (if inheritance is enabled). For more information, see the guide on managing Microsoft Purview role assignments.
The following screenshot shows how to assign the Data source admin role at the root collection level.
Configure Microsoft Purview permissions to create, update, or delete access policies
To create, update or delete policies, you need to get the Policy author role in Microsoft Purview at root collection level:
- The Policy author role can create, update, and delete DevOps and Data Owner policies.
- The Policy author role can delete self-service access policies.
For more information about managing Microsoft Purview role assignments, see Create and manage collections in the Microsoft Purview Data Map.
Note
Policy author role must be configured at the root collection level.
In addition, to easily search Microsoft Entra users or groups when creating or updating the subject of a policy, you can greatly benefit from getting the Directory Readers permission in Microsoft Entra ID. This is a common permission for users in an Azure tenant. Without the Directory Reader permission, the Policy Author will have to type the complete username or email for all the principals included in the subject of a data policy.
Configure Microsoft Purview permissions for publishing Data Owner policies
Data Owner policies allow for checks and balances if you assign the Microsoft Purview Policy author and Data source admin roles to different people in the organization. Before a Data owner policy takes effect, a second person (Data source admin) must review it and explicitly approve it by publishing it. This does not apply to DevOps or Self-service access policies as publishing is automatic for them when those policies are created or updated.
To publish a Data owner policy you need to get the Data source admin role in Microsoft Purview at root collection level.
For more information about managing Microsoft Purview role assignments, see Create and manage collections in the Microsoft Purview Data Map.
Note
To publish Data owner policies, the Data source admin role must be configured at the root collection level.
Delegate access provisioning responsibility to roles in Microsoft Purview
After a resource has been enabled for Data policy enforcement, any Microsoft Purview user with the Policy author role at the root collection level can provision access to that data source from Microsoft Purview.
Note
Any Microsoft Purview root Collection admin can assign new users to root Policy author roles. Any Collection admin can assign new users to a Data source admin role under the collection. Minimize and carefully vet the users who hold Microsoft Purview Collection admin, Data source admin, or Policy author roles.
If a Microsoft Purview account with published policies is deleted, such policies will stop being enforced within an amount of time that depends on the specific data source. This change can have implications on both security and data access availability. The Contributor and Owner roles in IAM can delete Microsoft Purview accounts. You can check these permissions by going to the Access control (IAM) section for your Microsoft Purview account and selecting Role Assignments. You can also use a lock to prevent the Microsoft Purview account from being deleted through Resource Manager locks.
Register the data sources in Microsoft Purview
The Azure SQL Database data source needs to be registered first with Microsoft Purview before creating access policies. You can follow these guides:
Register and scan Azure SQL Database
After you've registered your resources, you'll need to enable Data Policy Enforcement. Data Policy Enforcement can affect the security of your data, as it delegates to certain Microsoft Purview roles to manage access to the data sources. Go through the secure practices related to Data Policy Enforcement in this guide: How to enable Data Policy Enforcement
Once your data source has the Data policy enforcement toggle Enabled, it will look like this screenshot. This will enable the access policies to be used with the given Azure SQL server and all its contained databases.

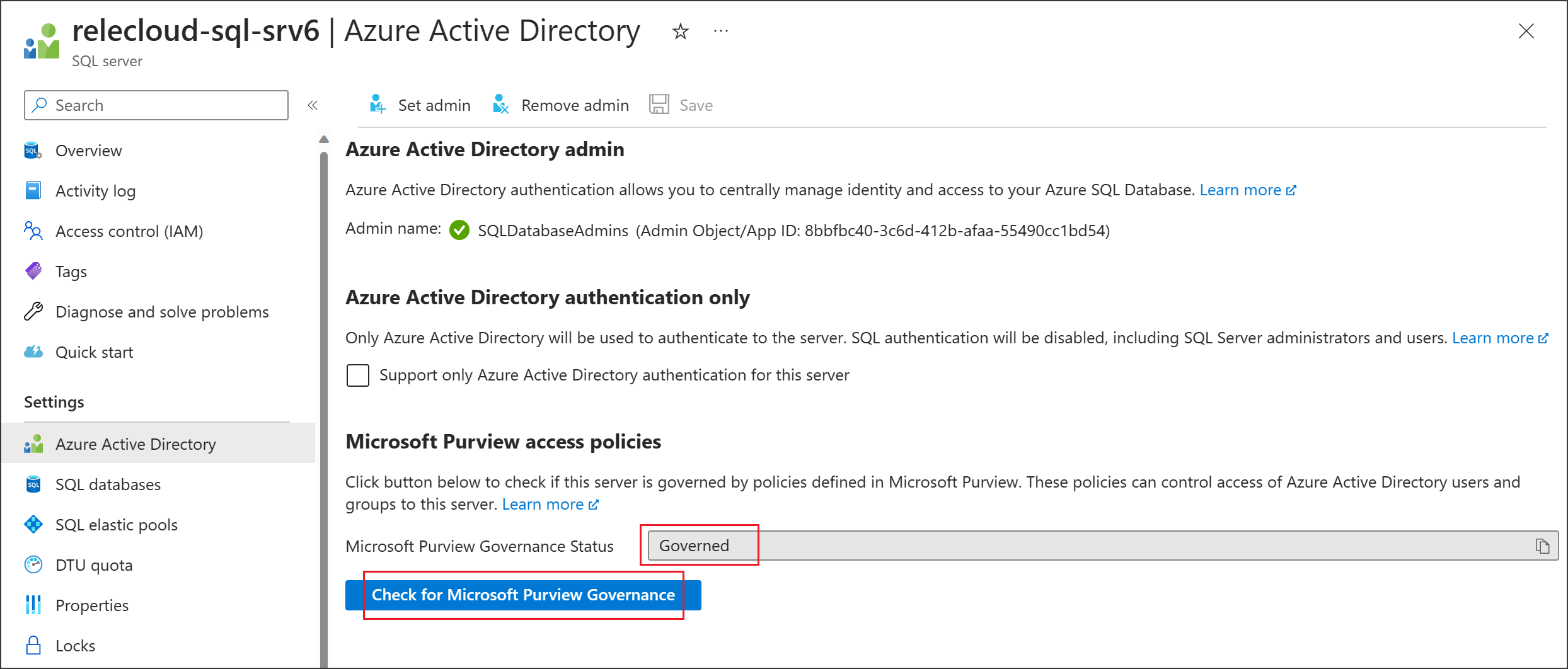
Return to the Azure portal for Azure SQL Database to verify it's now governed by Microsoft Purview:
Sign in to the Azure portal through this link
Select the Azure SQL Server that you want to configure.
Go to Microsoft Entra ID on the left pane.
Scroll down to Microsoft Purview access policies.
Select the button to Check for Microsoft Purview Governance. Wait while the request is processed. It could take a few minutes.
Confirm that the Microsoft Purview Governance Status shows
Governed. Note that it could take a few minutes after you enable Data policy enforcement in Microsoft Purview for the correct status to be reflected.
Note
If you disable Data policy enforcement for this Azure SQL Database data source, it might take up to 24 hours for the Microsoft Purview Governance Status to be updated automatically to Not Governed. This can be accelerated by selecting Check for Microsoft Purview Governance. Before you enable Data policy enforcement for the data source in another Microsoft Purview account, ensure that the Purview Governance Status shows as Not Governed. Then repeat the steps above with the new Microsoft Purview account.
Create and publish a data owner policy
Execute the steps in the Create a new policy and Publish a policy sections of the data-owner policy authoring tutorial. The result will be a data owner policy similar to the example shown.
Example: Read policy. This policy assigns the Microsoft Entra principal 'Robert Murphy' to the SQL Data reader action, in the scope of SQL server relecloud-sql-srv2. This policy has also been published to that server. Note that policies related to this action are supported below server level (for example, database, table).

Important
- Publish is a background operation. It can take up to 5 minutes for the changes to be reflected in this data source.
- Changing a policy does not require a new publish operation. The changes will be picked up with the next pull.
Unpublish a data owner policy
Follow this link for the steps to unpublish a data owner policy in Microsoft Purview.
Update or delete a data owner policy
Follow this link for the steps to update or delete a data owner policy in Microsoft Purview.
Test the policy
After you create the policy, any of the Microsoft Entra users in the Subject should now be able to connect to the data sources in the scope of the policy. To test, use SSMS or any SQL client and try to query. Attempt access to a SQL table you have provided read access to.
If you require more troubleshooting, see the Next steps section in this guide.
Role definition detail
This section contains a reference of how relevant Microsoft Purview data policy roles map to specific actions in SQL data sources.
| Microsoft Purview policy role definition | Data source specific actions |
|---|---|
| Read | Microsoft.Sql/sqlservers/Connect |
| Microsoft.Sql/sqlservers/databases/Connect | |
| Microsoft.Sql/Sqlservers/Databases/Schemas/Tables/Rows | |
| Microsoft.Sql/Sqlservers/Databases/Schemas/Views/Rows | |
Next steps
Check blog, demo, and related how-to guides.
- Doc: Concepts for Microsoft Purview data owner policies
- Doc: Microsoft Purview data owner policies on all data sources in a subscription or a resource group
- Doc: Microsoft Purview data owner policies on an Azure Arc-enabled SQL Server
- Doc: Troubleshoot Microsoft Purview policies for SQL data sources
- Blog: Grant users access to data assets in your enterprise via API
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for