List Azure deny assignments
Similar to a role assignment, a deny assignment attaches a set of deny actions to a user, group, or service principal at a particular scope for the purpose of denying access. Deny assignments block users from performing specific Azure resource actions even if a role assignment grants them access.
This article describes how to list deny assignments.
Important
You can't directly create your own deny assignments. Deny assignments are created and managed by Azure.
How deny assignments are created
Deny assignments are created and managed by Azure to protect resources. You can't directly create your own deny assignments. However, you can specify deny settings when creating a deployment stack, which creates a deny assignment that is owned by the deployment stack resources. Deployment stacks is currently in preview. For more information, see Protect managed resources against deletion.
Compare role assignments and deny assignments
Deny assignments follow a similar pattern as role assignments, but also have some differences.
| Capability | Role assignment | Deny assignment |
|---|---|---|
| Grant access | ✅ | |
| Deny access | ✅ | |
| Can be directly created | ✅ | |
| Apply at a scope | ✅ | ✅ |
| Exclude principals | ✅ | |
| Prevent inheritance to child scopes | ✅ | |
| Apply to classic subscription administrator assignments | ✅ |
Deny assignment properties
A deny assignment has the following properties:
| Property | Required | Type | Description |
|---|---|---|---|
DenyAssignmentName |
Yes | String | The display name of the deny assignment. Names must be unique for a given scope. |
Description |
No | String | The description of the deny assignment. |
Permissions.Actions |
At least one Actions or one DataActions | String[] | An array of strings that specify the control plane actions to which the deny assignment blocks access. |
Permissions.NotActions |
No | String[] | An array of strings that specify the control plane action to exclude from the deny assignment. |
Permissions.DataActions |
At least one Actions or one DataActions | String[] | An array of strings that specify the data plane actions to which the deny assignment blocks access. |
Permissions.NotDataActions |
No | String[] | An array of strings that specify the data plane actions to exclude from the deny assignment. |
Scope |
No | String | A string that specifies the scope that the deny assignment applies to. |
DoNotApplyToChildScopes |
No | Boolean | Specifies whether the deny assignment applies to child scopes. Default value is false. |
Principals[i].Id |
Yes | String[] | An array of Microsoft Entra principal object IDs (user, group, service principal, or managed identity) to which the deny assignment applies. Set to an empty GUID 00000000-0000-0000-0000-000000000000 to represent all principals. |
Principals[i].Type |
No | String[] | An array of object types represented by Principals[i].Id. Set to SystemDefined to represent all principals. |
ExcludePrincipals[i].Id |
No | String[] | An array of Microsoft Entra principal object IDs (user, group, service principal, or managed identity) to which the deny assignment does not apply. |
ExcludePrincipals[i].Type |
No | String[] | An array of object types represented by ExcludePrincipals[i].Id. |
IsSystemProtected |
No | Boolean | Specifies whether this deny assignment was created by Azure and cannot be edited or deleted. Currently, all deny assignments are system protected. |
The All Principals principal
To support deny assignments, a system-defined principal named All Principals has been introduced. This principal represents all users, groups, service principals, and managed identities in a Microsoft Entra directory. If the principal ID is a zero GUID 00000000-0000-0000-0000-000000000000 and the principal type is SystemDefined, the principal represents all principals. In Azure PowerShell output, All Principals looks like the following:
Principals : {
DisplayName: All Principals
ObjectType: SystemDefined
ObjectId: 00000000-0000-0000-0000-000000000000
}
All Principals can be combined with ExcludePrincipals to deny all principals except some users. All Principals has the following constraints:
- Can be used only in
Principalsand cannot be used inExcludePrincipals. Principals[i].Typemust be set toSystemDefined.
List deny assignments
Follow these steps to list deny assignments.
Important
You can't directly create your own deny assignments. Deny assignments are created and managed by Azure. For more information, see Protect managed resources against deletion.
Prerequisites
To get information about a deny assignment, you must have:
Microsoft.Authorization/denyAssignments/readpermission, which is included in most Azure built-in roles.
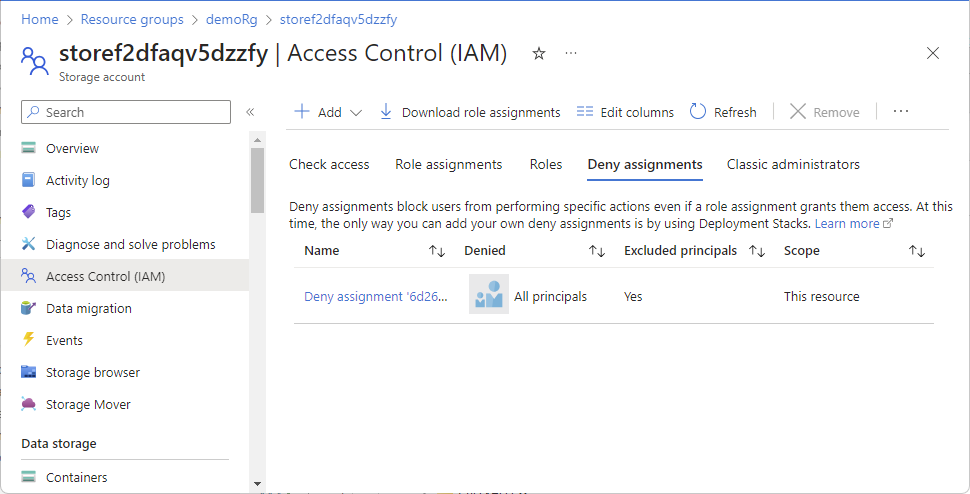
List deny assignments in the Azure portal
Follow these steps to list deny assignments at the subscription or management group scope.
In the Azure portal, open the selected scope, such as resource group or subscription.
Select Access control (IAM).
Select the Deny assignments tab (or select the View button on the View deny assignments tile).
If there are any deny assignments at this scope or inherited to this scope, they'll be listed.
To display additional columns, select Edit Columns.
Column Description Name Name of the deny assignment. Principal type User, group, system-defined group, or service principal. Denied Name of the security principal that is included in the deny assignment. Id Unique identifier for the deny assignment. Excluded principals Whether there are security principals that are excluded from the deny assignment. Does not apply to children Whether the deny assignment is inherited to subscopes. System protected Whether the deny assignment is managed by Azure. Currently, always Yes. Scope Management group, subscription, resource group, or resource. Add a checkmark to any of the enabled items and then select OK to display the selected columns.
List details about a deny assignment
Follow these steps to list additional details about a deny assignment.
Open the Deny assignments pane as described in the previous section.
Select the deny assignment name to open the Users page.
The Users page includes the following two sections.
Deny setting Description Deny assignment applies to Security principals that the deny assignment applies to. Deny assignment excludes Security principals that are excluded from the deny assignment. System-Defined Principal represents all users, groups, service principals, and managed identities in an Azure AD directory.
To see a list of the permissions that are denied, select Denied Permissions.
Action type Description Actions Denied control plane actions. NotActions Control plane actions excluded from denied control plane actions. DataActions Denied data plane actions. NotDataActions Data plane actions excluded from denied data plane actions. For the example shown in the previous screenshot, the following are the effective permissions:
- All storage actions on the data plane are denied except for compute actions.
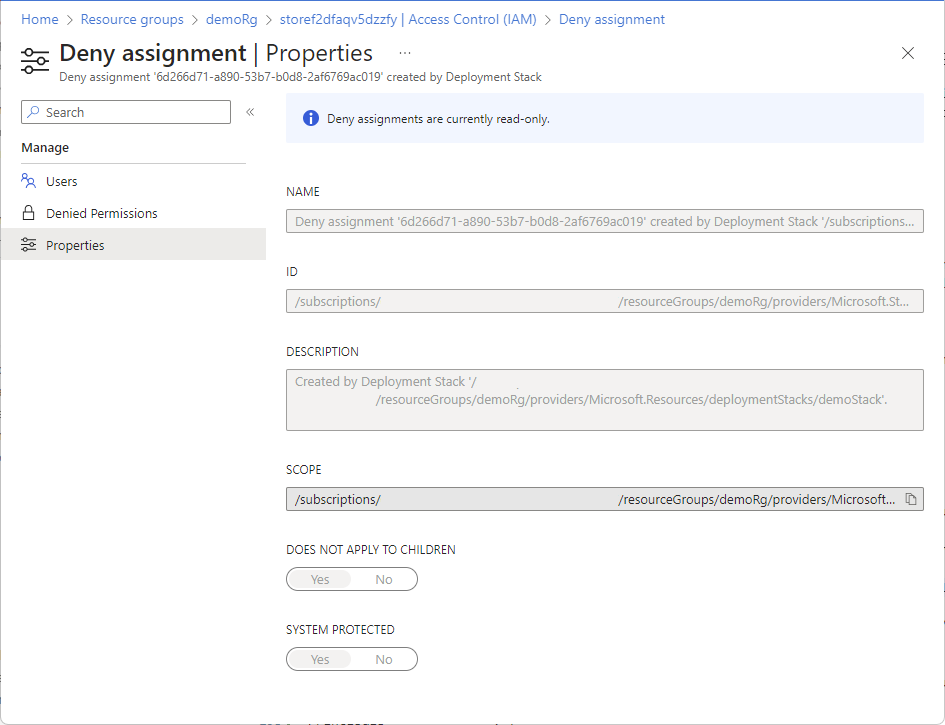
To see the properties for a deny assignment, select Properties.
On the Properties page, you can see the deny assignment name, ID, description, and scope. The Does not apply to children switch indicates whether the deny assignment is inherited to subscopes. The System protected switch indicates whether this deny assignment is managed by Azure. Currently, this is Yes in all cases.
Next steps
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for