Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Microsoft's Containers Secure Supply Chain (CSSC) framework is a seamless, agile ecosystem of tools and processes built to integrate and execute security controls throughout the lifecycle of containers. The container secure supply chain strategy is built considering all the security needs of the container applications. The goal is to prevent the use of vulnerable container images and create container infrastructure with a standard security portfolio.
The CSSC framework is built using the following steps:
- Identify the supply chain stages for containerized applications
- Outline the risks and the required security controls in each stage
- Describe the security objectives and goals in each stage
- Identify security tools, processes, and best practices in each stage
- Maintain security posture with metadata, logging, and reporting in each stage
Stages in supply chains for containers
A supply chain for containers is built in stages to align with the lifecycle of containers. Each stage in the pipeline identifies with distinct goals, security risks, and processes. Microsoft identifies the following five stages in the supply chain for containers.
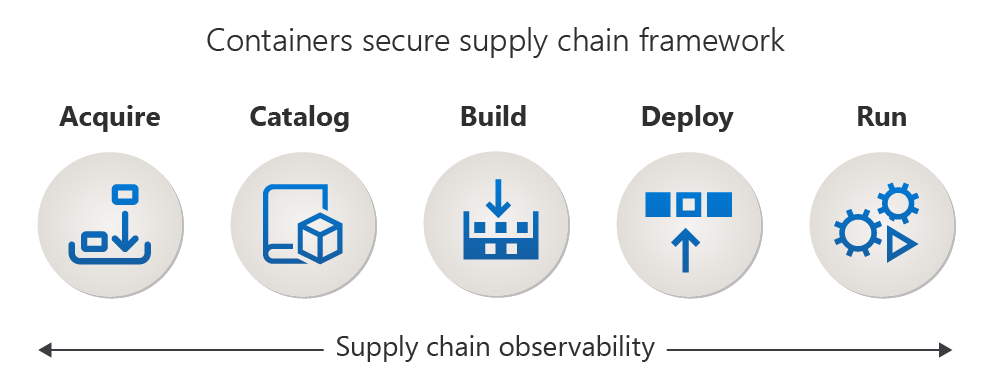
| Stage | Details |
|---|---|
| Acquire | Acquire container images from external sources or third-party vendors. |
| Catalog | Offer approved container images for internal consumption including builds and deployments. |
| Build | Produce compliant service and application images and deployment artifacts. |
| Deploy | Securely deploy containerized services and applications to the hosting environments. |
| Run | Run containers created from compliant, latest, and secure container images executing the business logic for an application. |
Implementing security processes across all five stages of the supply chain requires consistent practice of Observability and Monitoring. Constantly evolving security practices update container images, discover vulnerabilities, trigger changes in internal process, business requirements, and further requires monitoring to add transparency in each stage.
Common supply chain threats
When we talk about CSSC, we're talking about a continuous software transaction between software vendors, external sources, developers, service, and operations providers, distributing channels, and most importantly our customer base. Our goal is to achieve a secure transaction of container software and deliver an effective container infrastructure to our customers. Any small compromise, vulnerability, or attack can cause an immediate inherent adversity, severe loss to our trusted partners, customers, and Microsoft's reputation. It's crucial to address these security compromises and possible threats throughout the supply chain to ensure the security and integrity of containerized applications.
Microsoft identifies and delves deeper into the security compromises and possible threats throughout the supply chain:
Untrusted Sources
Using container images from untrusted sources can introduce significant security risks. These untrusted sources may have container images that contain malware, vulnerabilities, or backdoor.
Microsoft addresses these security compromises with following practices:
- Validating the authenticity and integrity of container images before incorporating them into its supply chain to mitigate these risks.
- Use container images from trusted sources. Employ image scanning and verification tools to help ensure images come from reputable repositories and haven't been tampered with.
Compromised Registries
Registries that aren't properly secured can host compromised or outdated container images. It's crucial to regularly audit and secure the registries to prevent the distribution of insecure container images. This includes ensuring that images comply with licensing requirements and enterprise best practices.
Microsoft addresses these security compromises with following practices:
- Regularly audit and secure container images registries.
- Employ access controls, authentication controls, and image scanning to detect and prevent the use of insecure or outdated images.
Compromised Dependencies
Injecting malicious code into base images or using malicious libraries can jeopardize the security of container applications.
Microsoft addresses these security compromises with following practices:
- Implement strict controls on the dependencies used in your container images.
- Regularly update base images and libraries to patch known vulnerabilities.
- Utilize container image scanning to identify and remediate any malicious or vulnerable dependencies.
Compromised Build Environments
Insecure build environments can lead to the inclusion of vulnerable, outdated, or noncompliant container images.
Microsoft addresses these security compromises with following practices:
- Secure your build environments by using trusted and regularly updated tools and containers.
- Implement a process to remove outdated or vulnerable container images to ensure the latest versions are used during the build process.
Unverified Deployment
Deploying untrusted or malicious container images can expose organizations to various security breaches. Access controls and a robust verification process should be in place to ensure that only authorized and verified container images are deployed.
Microsoft addresses these security compromises with following practices:
- Enforce strict access controls and image verification processes during deployment.
- Utilize role-based access control (RBAC) to limit who can deploy container images.
- Ensure only trusted and thoroughly tested images are deployed in production.
Lack of Observability
Monitoring and observability are crucial for detecting security issues. Enterprises must invest in tools and processes that provide visibility into the entire supply chain, enabling real-time tracking of container images and the detection of security attacks.
Microsoft addresses these security compromises with following practices:
- Implement monitoring and observability solutions in your containerized environment.
- Use logging, tracing, and monitoring tools to keep track of container image changes, security events, and anomalies in the supply chain.
- Set up alerts and notifications for suspicious activities.
In addition to these measures, it's essential to establish clear security policies and practices, educate your team on security best practices, and conduct regular security assessments and audits of your container supply chain. Continuously stay updated with security threats and vulnerabilities relevant to containers and adapt your security measures accordingly. Container security is an ongoing process that requires vigilance and proactive risk management.
Next Steps
For more information about each stage of the CSSC Framework, see: