Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Trusted Signing uses Azure role-based access control (RBAC) to control access to verify identities and certificate profiles. The following roles are essential for enabling workflows:
| Role Name | Purpose | Notes |
|---|---|---|
| Trusted Signing Identity Verifier | Required to manage identity validation requests | Can only be used in the Azure portal—not supported via Azure CLI |
| Trusted Signing Certificate Profile Signer | Required to successfully sign using Azure Trusted Signing | Necessary for signing operations; works with both Azure CLI and portal |
In this tutorial, you'll review the supported roles for Trusted Signing and learn how to assign them to your Trusted Signing resources using the Azure portal.
Supported roles for Trusted Signing
The following table lists the roles that Trusted Signing supports, including what each role can access within the service’s resources:
| Role | Manage and view account | Manage certificate profiles | Sign by using a certificate profile | View signing history | Manage role assignment | Manage identity validation |
|---|---|---|---|---|---|---|
| Trusted Signing Identity Verifier | x | |||||
| Trusted Signing Certificate Profile Signer | x | x | ||||
| Owner | x | x | x | |||
| Contributor | x | x | ||||
| Reader | x | |||||
| User Access Admin | x |
The Trusted Signing Identity Verifier role is required to manage identity validation requests, which you can do only in the Azure portal, and not by using the Azure CLI. The Trusted Signing Certificate Profile Signer role is required to successfully sign by using Trusted Signing.
Assign roles
In the Azure portal, go to your Trusted Signing account. On the resource menu, select Access Control (IAM).
Select the Roles tab and search for Trusted Signing. The following figure shows the two custom roles.
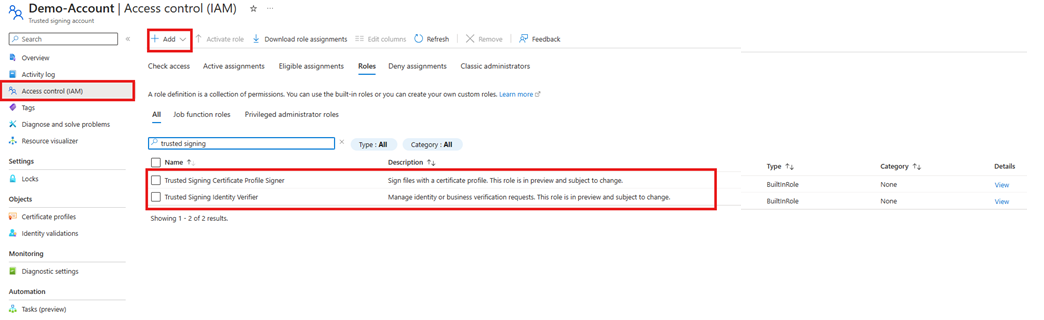
To assign these roles, select Add, and then select Add role assignment. Follow the guidance in Assign roles in Azure to assign the relevant roles to your identities.
To create a Trusted Signing account and certificate profile, you must be assigned at least the Contributor role.
For more granular access control on the certificate profile level, you can use the Azure CLI to assign roles. You can use the following commands to assign the Trusted Signing Certificate Profile Signer role to users and service principals to sign files:
az role assignment create --assignee <objectId of user/service principle> --role "Trusted Signing Certificate Profile Signer" --scope "/subscriptions/<subscriptionId>/resourceGroups/<resource-group-name>/providers/Microsoft.CodeSigning/codeSigningAccounts/<trustedsigning-account-name>/certificateProfiles/<profileName>"