Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
You can use network security groups to filter and control inbound and outbound network traffic to and from your virtual machines (VMs). You can also use Azure Virtual Network Manager to apply admin security rules to your VMs to control network traffic.
In this article, you learn how to use Network security group test to check if a security rule is blocking traffic to or from your virtual machine by checking what security rules are applied to your VM traffic.
Prerequisites
An Azure account with an active subscription. If you don't have one, create a free account before you begin.
Sign in to the Azure portal with your Azure account.
An Azure virtual machine (VM). If you don't have one, create a Linux VM or a Windows VM.
Test inbound connections
In this section, you test if RDP connections are allowed to your VM from a remote IP address.
In the search box at the top of the portal, enter virtual machines. Select Virtual machines from the search results.
Select the VM that you want to test.
Under Connect, select Connect.
Note
The virtual machine must be in running state.
Under Troubleshoot, select Test network security groups.
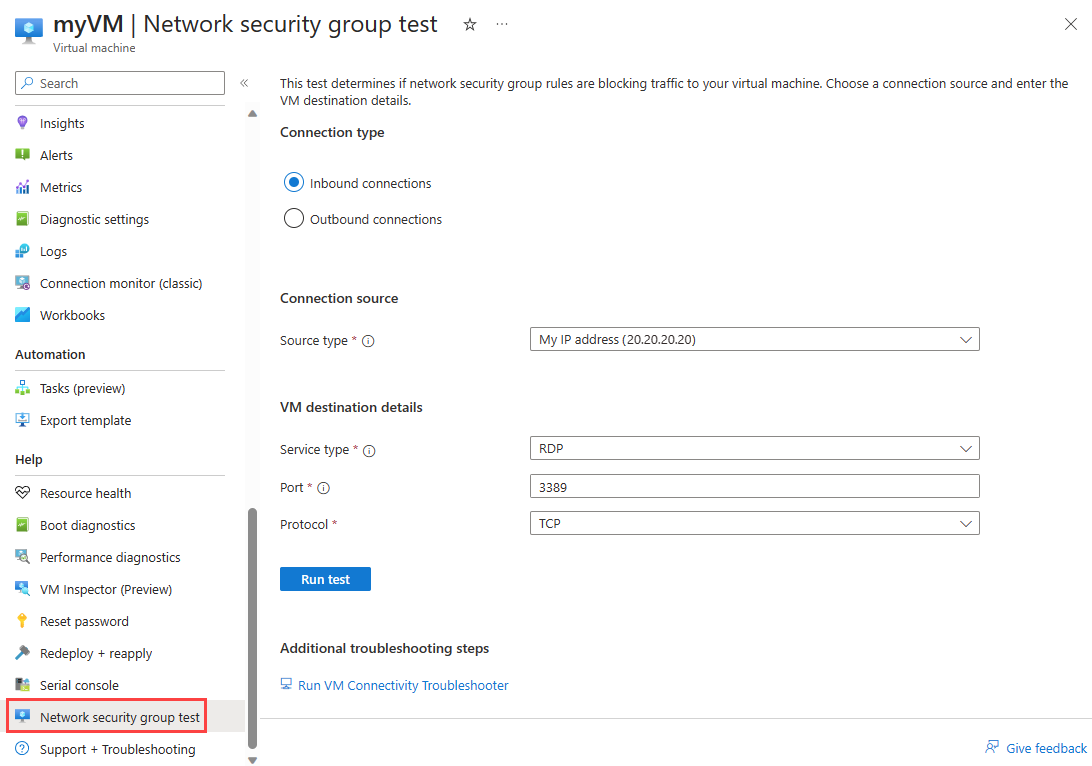
Select Inbound connections. The following options are available for Inbound tests:
Setting Value Source type - My IP address: your public IP address that you're using to access the Azure portal.
- Any IP address: any source IP address.
- Other IP address/CIDR: Source IP address or address prefix.
- Service tag: Source service tag.IP address/CIDR The IP address or address prefix that you want to use as the source.
Note: You see this option if you select Other IP address/CIDR for Source type.Service tag The service tag that you want to use as the source.
Note: You see this option if you select Service tag for Source type.Service type List of predefined services available for the test.
Notes:
- If you select a predefined service, the service port number and protocol are automatically selected.
- If you don't see the port and protocol information that you want, select Custom, and then enter the port number and select the protocol that you want.Port VM port number.
Note: If you select one of the predefined services, the correct port number is automatically selected.
Manually enter the port number when you select Custom for Service type.Protocol Connection protocol. Available options are: Any, TCP, and UDP.
Note: If you select one of the predefined services, the correct protocol used by the service is automatically selected.
Manually select the protocol when you select Custom for Service type.To test if RDP connection is allowed to the VM from a remote IP address, select the following values:
Setting Value Source type Select My IP address. Service type Select RDP. Port Leave the default of 3389. Protocol Leave the default of TCP. Select Run test.
After a few seconds, you see the details of the test:
- If RDP connections are allowed to the VM from the remote IP address, you see Traffic status: Allowed.
- If RDP connections are blocked, you see Traffic status: Denied. In the Summary section, you see the security rules that are blocking the traffic.
To allow the RDP connection to the VM from the remote IP address, add to the network security group a security rule that allows RDP connections from the remote IP address. This security rule must have a higher priority than the one that's blocking the traffic. For more information, see Create, change, or delete a network security group.
Test outbound connections
In this section, you test your VM can have connect to the internet.
In the search box at the top of the portal, enter virtual machines. Select Virtual machines from the search results.
Select the VM you want to test.
Under Connect, select Connect.
Note
The virtual machine must be in running state.
Under Troubleshoot, select Test network security groups.
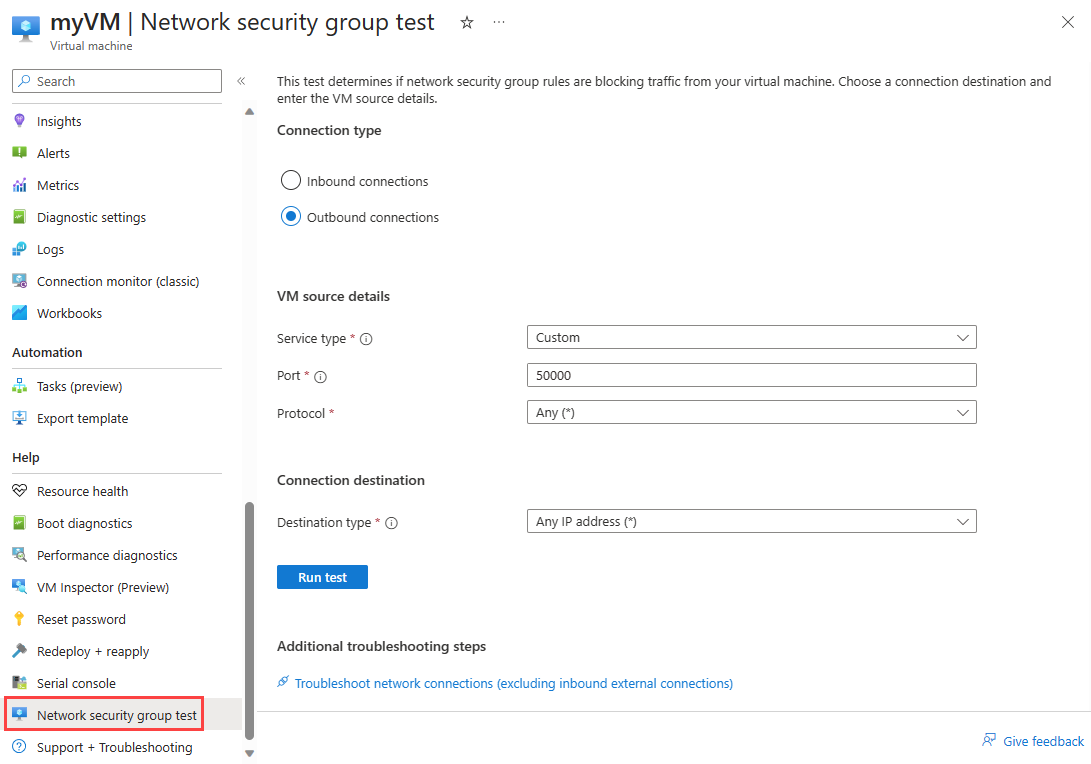
Select Outbound connections. The following options are available for Outbound tests:
Setting Value Service type List of predefined services available for the test.
Notes:
- If you select a predefined service, the service port number and protocol are automatically selected.
- If you don't see the port and protocol information that you want, select Custom, and then enter the port number and select the protocol that you want.Port VM port number.
Note: If you select one of the predefined services, the correct port number is automatically selected.
Manually enter the port number when you select Custom for Service type.Protocol Connection protocol. Available options are: Any, TCP, and UDP.
Note: If you select one of the predefined services, the correct protocol used by the service is automatically selected.
Manually select the protocol when you select Custom for Service type.Destination type - My IP address: your public IP address that you're using to access the Azure portal.
- Any IP address: any source IP address.
- Other IP address/CIDR: Source IP address or address prefix.
- Service tag: Source service tag.IP address/CIDR The IP address or address prefix that you want to use as the destination.
Note: You see this option if you select Other IP address/CIDR for Source type.Service tag The service tag that you want to use as the destination.
Note: You see this option if you select Service tag for Source type.To test if the VM can connect to the internet, select the following values:
Setting Value Service type Select Custom. Port Leave the default of 50000. Protocol Leave the default of Any. Destination type Select Any IP address. Select Run test.
After a few seconds, you see the details of the test:
- If connections to the internet are allowed from the VM, you see Traffic status: Allowed.
- If connections to the internet are blocked, you see Traffic status: Denied. In the Summary section, you see the security rules that are blocking the traffic.
To allow internet connections from the VM, add to the network security group a security rule that allows connections to the internet service tag. This security rule must have a higher priority than the one that's blocking the traffic. For more information, see Create, change, or delete a network security group.
Related content
- To learn how to troubleshoot VM connections, see Troubleshoot connections with Azure Network Watcher.
- To learn more about network security groups, see Network security groups overview.