Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
This Microsoft Purview Information Protection Guide has been prepared by Microsoft for use by Australian Government and other interested organizations. Its intent is to assist Australian Government organizations to improve their data security posture while meeting information classification and protection requirements. Guidance provided in this guide is intended to align as closely as possible with requirements set out in the Protected Security Policy Framework (PSPF) and Information Security Manual (ISM). Guidance provided in this guide will also align with and support configurations recommended via ASD's Blueprint for Secure Cloud.
This guide is aimed at Australian Government Chief Data Officers (CDO), Chief Technology Officers (CTO), Chief Security Officers (CSO), Chief Information Security Officers(CISO), risk or compliance officers, information privacy or other information management roles.
Microsoft Purview maturity model for Australian Government has been created to help organizations understand where their Microsoft Purview initiative should start and what they need to do to increase their data security maturity and level of compliance.
This guide is written for a typical Government organization, with examples written applicable to this effect. However, every Government organization needs to tailor the guidance to meet their unique requirements.
The section of the guide titled Australian Government requirement to capability mapping includes a listing of PSPF requirements, along with an explanation of how Microsoft Purview capabilities can be configured to align with each requirement, and a link to the corresponding guide sections. Relevant Information Security Manual (ISM) and Australian Government Recordkeeping Metadata Standard (AGRkMS) requirements are also discussed.
Architectural Overview
This guide makes use of three key capabilities to meet government information protection and classification requirements, namely:
- Sensitivity labeling
- Data Loss Prevention (DLP)
- Sensitivity auto-labeling
The following diagram provides a conceptual overview of the interaction between these three Microsoft 365 capabilities along with examples of use.

Sensitivity labeling
Microsoft Purview Information Protection includes a capability called sensitivity labeling. Sensitivity labeling allows for users to apply labels to items such as files and email. These labels can be aligned with data security controls to protect the enclosed information. Sensitivity labeling can also be extended to other services such as SharePoint sites, Teams, and meetings.
Sensitivity labels, when aligned with an organization's classification requirements, such as those defined in Protective Security Policy Framework (PSPF), allow us to treat labels as classifications. They provide us with visual markings via the user interface and other marking options. For example:

Data security controls that can be applied via sensitivity labels, include:
- The ability to encrypt items, preventing access by unauthorized users.
- The ability to provide label recommendations to users upon detection of sensitive information.
- The control of external user access to labeled locations.
- The control of Teams meeting security settings for meetings that have certain labels applied.
Labeling client experience
As discussed in Microsoft Office client support, users typically interact with labeled items via a Microsoft 365 Apps Office client, web based client, or a mobile device equivalent. These clients allow users to apply labels to items:

If a user forgets to apply a label to an item, the client prompts the user to apply a label before saving the item or, if an email, before sending it.
While a user is working on an item, if a label is yet to be applied and information is detected that aligns with a security classification, then a label recommendation can be provided to the user. If sensitive content is then detected that aligns with a higher classification than the one currently applied, a recommendation can be provided to the user that they increase the item's sensitivity.
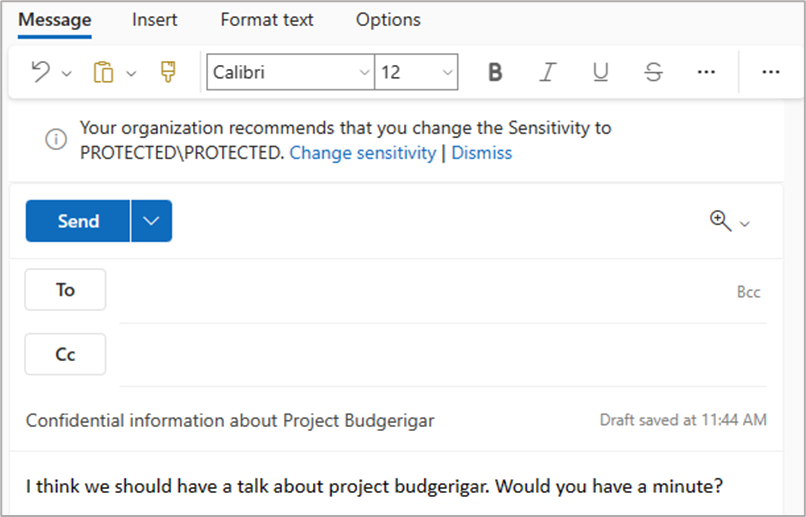
Such recommendations help to ensure label accuracy. Label accuracy is important as many controls governing the flow of information are based on item sensitivity.
Applicability to Copilot for Microsoft 365
Microsoft 365 Copilot inherits Microsoft 365's multiple forms of protection against compromise and unauthorized access. The permission model within Microsoft 365 helps to ensure that information can't be intentionally leaked between users and groups.
Important
Microsoft Purview configuration isn't a prerequisite for Copilot for Microsoft 365. However, deployment of Microsoft Purview configurations strengthens your overall information security posture in your organization's entire environment, including Copilot.
The information risk mitigations that Microsoft Purview provides is complementary to Copilot for Microsoft 365. The most straightforward example of this is through label inheritance. If Copilot is used to generate an item based on a source item, for example, to generate a summary of a source Word document, then any sensitivity labels that were applied to the source item are inherited by the generated item. This helps to ensure protections applied to information are maintained as the information changes form.

When evaluating potential security concerns that could eventuate as a result of Copilot for Microsoft 365 enablement, risks can be grouped into three categories:
- Data Leak out of AI tool: Content generated by Copilot could contain sensitive information.
- Data Oversharing: Users might distribute Copilot generated items that contain sensitive information.
- Data Leak into AI tool: Users might inadvertently leak sensitive data into Copilot.
The following capabilities, which are discussed in this guide, are able to help mitigate data leak out of Copilot and data oversharing risks:
- Identifying information identifies whether generated content or content being shared contains sensitive or security classified information. Controls protect the information automatically apply.
- Client-based auto-labeling identifies when a generated item contains sensitive information and provide a label recommendation to the user. The label is subject to any label-based controls.
- Label groups and sites configuration applies security controls, including restrictions on sharing and external user access, to locations. If a Copilot generated item is moved to a location, which isn't deemed as safe for the label applied to the item, alerting triggers to allow for cleanup.
- DLP rules protecting classified information, when paired with mandatory labeling configuration, applies to all Office documents and emails. Due to label inheritance, Copilot generated content inherits the labels applied to their source information, which means that they'll also be within the scope of relevant label-based DLP policies.
- DLP rules protecting sensitive information ensures that, regardless of the label that has been applied to an item, the correct security controls still apply. This ensures that in event that Copilot might have utilized sensitive information in a generated item, the information is protected from oversharing.
- Sensitivity label encryption prevents oversharing by ensuring that only authorized users can access security classified items. Additionally, encryption permissions lock Copilot out of highly sensitive items, reducing risk of information being included in generated content.
For more Copilot for Microsoft 365 specific information on these controls, see Information protection considerations for Copilot.
Regarding risks concerned with data leak into AI tools, sensitivity label encryption is relevant to this. Other controls aren't Microsoft Purview specific and aren't addressed as part of this guide. However, the following links provide relevant information:
- Restricted SharePoint search (RSS) allows organizations to limit Copilot for Microsoft 365 to only accessing an approved list of up to 100 sites. Implementation of this capability can help to reduce the risk of Copilot indexing information that organizations aren't prepared for it to have access to. This feature is to enable Copilot while the previous list of Microsoft Purview controls are implemented and any existing oversharing due to inappropriate permissions is addressed. Once potential for information risk is mitigated, RSS is then disabled to allow users full benefit of Copilot's capabilities.
- Data access governance reports, included in SharePoint Premium, can be used to discover sites that contain potentially overshared or sensitive content so that they can be addressed.
- Site lifecycle management, included in SharePoint Premium, can be used to automatically detect and act on inactive sites. Removing inactive sites helps to ensure that the information Copilot has access to is current and relevant.
Contact us
If you'd like to reach out to the creators of this guide to discuss the guidance provided then feel free to do so via AUGovMPIPGuide@microsoft.com.