Events
Nov 18, 6 AM - Nov 22, 12 PM
Protect your org with AI-powered solutions built across platforms and cloud environments at Microsoft Ignite.
Register nowThis browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
The goal of a cloud risk assessment is to ensure that the system and data that exists in or is considered for migration to the cloud don't introduce any new or unidentified risk into the organization. The focus is to ensure confidentiality, integrity, availability, and privacy of information processing and to keep identified risks below the accepted internal risk threshold.
In a shared responsibility model, the Cloud Service Provider (CSP) is responsible for managing security and compliance of the cloud as the provider. The customer remains responsible for managing and configuring security and compliance in the cloud in accordance with their needs and risk tolerance.
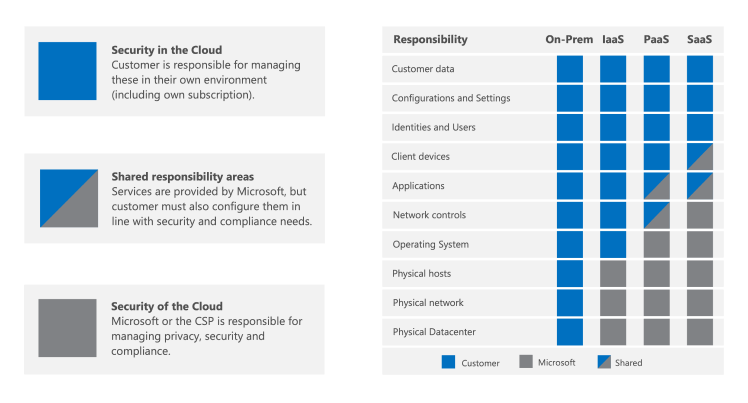
In this guide, best practices are shared on how to efficiently evaluate vendor risks and how to use the resources and tools Microsoft makes available.
Cloud deployments can be categorized as Infrastructure as a Service (IaaS), Platform as a Service (PaaS), or Software as a Service (SaaS). Depending upon the applicable cloud service model, the level of responsibility over the security controls for the solution shift between the CSP and the customer. In a traditional on-premises model, the customer is responsible for the whole stack. When moving to the cloud, all physical security responsibilities transfer to the CSP. Depending on the cloud service model for your organization, additional responsibilities shift over to the CSP. However, in most cloud service models, your organization remains responsible for the devices used to access the cloud, network connectivity, your accounts and identities, and your data. Microsoft invests heavily in creating services that allow customers to stay in control of their data across the entire lifecycle.
Microsoft Cloud operates at a hyperscale, relying on a combination of DevSecOps and automation to standardize operating models. Microsoft operating model changes the way risk is approached compared to traditional on-premises operating models, leading to the implementation of different and sometimes unfamiliar controls to manage risks. When conducting your cloud risk assessment, keep in mind that Microsoft's goal is to ensure all risks are addressed, but not necessarily to implement the same controls your organization does. Microsoft may address the same risks with a different set of controls and that should be reflected in the cloud risk assessment. Additionally, some risks in a traditional on-prem design are of lower severity in a cloud environment, and vice versa. Designing and implementing strong preventive controls can reduce much of the work required by the detective and corrective controls. An example of this is Microsoft's implementation of Zero Standing Access (ZSA).
Microsoft recommends that customers map their internal risk and controls framework to an independent framework that addresses cloud risks in a standardized way. If your existing internal risk assessment models don't address the specific challenges that come with cloud computing, you'll benefit from these broadly adopted and standardized frameworks. Your internal control framework may already be a conglomeration of multiple standardized frameworks, having these controls mapped to their corresponding frameworks will help during your assessment.
A secondary benefit is that Microsoft provides mappings against these frameworks in documentation and tools that will accelerate your risk assessments. Examples of these frameworks include the ISO 27001 Information security standard, CIS Benchmark, and NIST SP 800-53. Microsoft offers the most comprehensive set of compliance offerings of any CSP. For more information, see Microsoft compliance offerings.
Use Microsoft Purview Compliance Manager to create your own assessments that evaluate compliance with the industry and regional regulations that apply to your organization. Assessments are built upon the framework of assessment templates, which contain the necessary controls, improvement actions, and where applicable, Microsoft actions for completing the assessment. For Microsoft actions, detailed implementation plans and recent audit results are provided. This way, time can be saved on fact finding, mapping, and researching how specific controls are implemented by Microsoft. For more information, see the Microsoft Purview Compliance Manager article.
While the customer is responsible for managing and configuring security and compliance in the cloud, the CSP is responsible for managing security and compliance of the cloud. One way to validate that the CSP is effectively addressing their responsibilities and upholding their promises is to review their external audit reports such as ISO and SOC. Microsoft makes external audit reports available to authenticated audiences on the Service Trust Portal (STP).
In addition to external audit reports, Microsoft highly encourages customers to take advantage of the following resources to help understand how Microsoft operates in depth:
On-demand learning path: Microsoft Learn offers hundreds of learning paths and modules on different topics. Amongst them, take Learn how Microsoft safeguards customer data to understand Microsoft's fundamental security and privacy practices.
Service Assurance on Microsoft Compliance: Articles on Microsoft's practices are categorized into 14 domains for easier review. Each domain includes an overview that address common risk scenarios for with each area. Audit tables are provided containing links to the most recent reports stored on the STP, related sections, and the date the audit report was conducted for Microsoft online services. If available, links to artifacts demonstrating control implementation, such as third-party vulnerability assessments and business continuity plan verification reports are provided. Like audit reports, these artifacts are hosted on STP and require authentication to access.
| Domain | Description |
|---|---|
| Architecture | The design of Microsoft online services and the security principles that act as its foundation. |
| Audit logging and monitoring | How Microsoft captures, processes, stores, protects, and analyzes logs to detect unauthorized activity and monitor performance. make security and performance monitoring possible. |
| Datacenter security | How Microsoft securely operates the datacenters that provide the means to operate Microsoft online services worldwide. |
| Encryption and key management | The cryptographic protection of customer communications and the data stored and processed in the cloud. |
| Governance, risk, and compliance | How Microsoft enforces the security policies it creates and manages risk to meet customer promises and compliance requirements. |
| Identity and access management | The protection of Microsoft online services and customer data from unauthorized or malicious access. |
| Security incident management | The processes Microsoft uses to prepare for, detect, respond, and communicate all security incidents. |
| Network security | How Microsoft protects its network boundaries from external attacks and manages its internal network to limit their propagation. |
| Personnel management | The screening processes, training, and secure management of personnel throughout their time at Microsoft. |
| Privacy and data management | How Microsoft handles and protects customer data to preserve their data rights. |
| Resiliency and continuity | Process and technologies used to maintain service availability and ensure business continuity and recovery. |
| Security development and operation | How Microsoft ensures that its services are designed, run, and managed securely throughout their lifecycle. |
| Supplier management | How Microsoft screens and manages third-party companies that assist with Microsoft online services. |
| Threat and vulnerability management | The processes Microsoft uses to scan for, detect, and address vulnerabilities and malware. |
Microsoft makes a concerted effort to publish information, such as the articles on this site, to help customers understand how we keep their data safe and satisfy their compliance requirements. However, it can be difficult to stayed informed on the global regulatory landscape, navigate complicated compliance and risk scenarios, and reach an acceptable level of assurance. To overcome these challenges, Microsoft launched the Compliance Program for Microsoft Cloud (CPMC). The CPMC is a fee-based premium program offering personalized regulatory and industry specific compliance support, education, and networking opportunities. For more information on CPMC specific offerings, check out the CPMC website.
Events
Nov 18, 6 AM - Nov 22, 12 PM
Protect your org with AI-powered solutions built across platforms and cloud environments at Microsoft Ignite.
Register nowTraining
Module
Prepare for cloud security by using the Microsoft Cloud Adoption Framework for Azure - Training
Security is a core consideration for all customers, in every environment. But moving to the cloud is a significant change that requires a shift in your security mindset and approach. The Cloud Adoption Framework provides guidance for this security journey by providing clarity for the processes, best practices, models, and experiences.
Certification
Microsoft Certified: Information Protection and Compliance Administrator Associate - Certifications
Demonstrate the fundamentals of data security, lifecycle management, information security, and compliance to protect a Microsoft 365 deployment.