Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
In today's stringent regulatory environment, it's important for organizations to monitor and analyze how users interact with security products. Organizations may need to keep track of actions, transactions, and configuration settings on a platform to ensure that they're meeting compliance regulations and regulatory standards.
Security Copilot today provides access to audit logs through Microsoft Purview Unified Audit Log (UAL), Microsoft Purview Data Security Posture Management (DSPM) for AI, and the Office Management API to help you satisfy compliance and regulatory requirements. The UAL from Purview gives you visibility into information such as administrator events and activity metadata, whereas DSPM for AI provides insights into prompt/response pairs.
- Admin events - Privileged actions such as changes to tenant-level settings or administrative changes (for example, data sharing, agent, agent trigger, plugin and promptbook configurations).
- Activity metadata - Logs of user interactions within the Security Copilot platform (for example, a user asked a prompt at a specific time with information on the activity type).
- Prompt Response Pairs - Activity in Security Copilot can contain a prompt to a skill, which produces a response pair. The pair and its content are a core functionality of the platform and a critical point of inspection for audit purposes.
Note
Customer content such as that contained within the prompt and response pair is currently only included through Microsoft Purview DSPM for AI. For more information, please see Microsoft Purview for DSPM.
By keeping track of these interactions, you can potentially identify risks, ensure stable operation of important workflows, and protect production data.
Enable Security Copilot for Purview Audit and DSPM Solutions
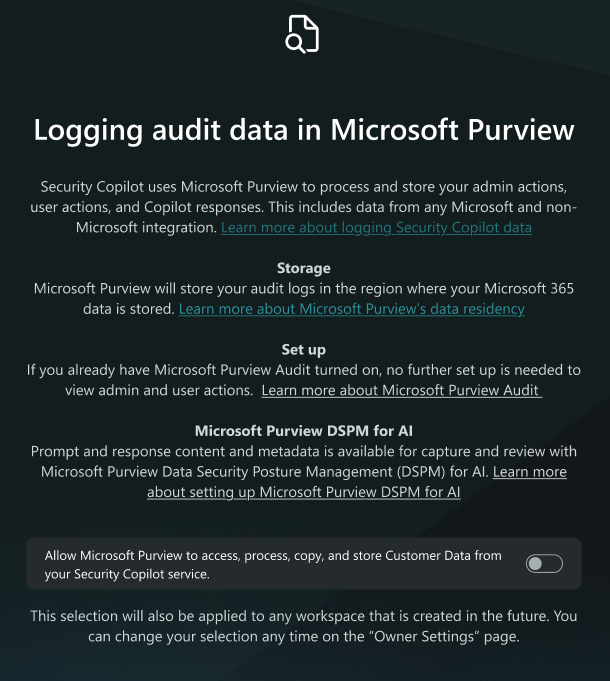
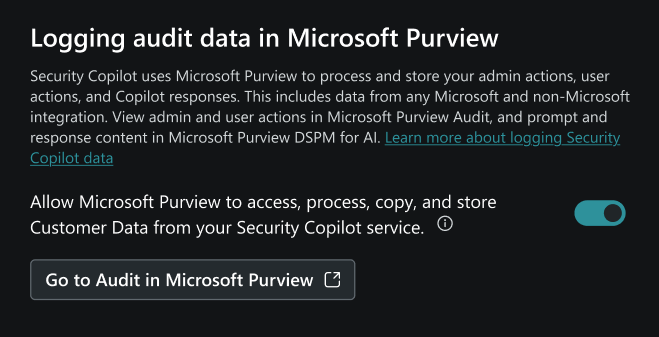
To enable Purview DSPM for AI and UAL solutions for Security Copilot, the capability must be enabled within Security Copilot and configured within the respective Purview solutions. There are two options to enable the capabilities within Security Copilot. Initially, during the first run experience, a Security Administrator may opt into allowing Microsoft Purview to access, process, copy and store administrator actions, user actions, and Copilot responses. For more information on getting started with Security Copilot see Get started with Security Copilot.
Additionally, a Security Administrator can also access this option through the Owner settings page. For more information on role types, see Understand authentication.
Use the following steps to update the audit log settings:
Sign in to Security Copilot (https://securitycopilot.microsoft.com).
Select the home menu icon.
Navigate to the Owner > Owner settings > Logging audit data in Microsoft Purview.
Important
Microsoft Purview will store your Customer Data in the region where your Microsoft 365 data is stored. For more information, see, Privacy and data security. The default retention period for audit logs is 180 days but can be extended using audit log retention policies. For more information, see Manage audit log retention policies.
You can turn the toggle on or off.
Access Security Copilot audit logs via Unified Audit Log in Microsoft Purview
Before you begin
This section gives an overview of the prerequisites to access the audit log.
You'll need to:
- Verify that you have opted to allow Microsoft Purview access inside Security Copilot. For more information, see Enable the audit log capability.
- Verify that the audit log feature is active within Microsoft Purview. For more information, see Before you search the audit log.
Note
You'll require proper permissions to access the audit log in Microsoft Purview. For more information, see Permissions in the Microsoft Purview portal. These access rights might be different from those in Security Copilot.
Options to access the Unified Audit Log in Microsoft Purview
You can take the following actions to access the audit log in Microsoft Purview:
- Search the audit log - Article that provides instructions on how to access and search through the audit log event data to gain insight and further investigate user activities.
- Search through the audit log activities - Article that describes the activities that are captured in the audit log.
- Activities Operation Name References for Security Copilot - A listing of activity operation names for Security Copilot management, agent management, and AI interactions such as prompts.
- Search the audit log using a PowerShell script - Article that provides instructions on how you can run a PowerShell script to search the audit log to help you investigate security incidents and compliance issues.
- Monitor user activities and system events with Security Copilot and Microsoft Sentinel - Blog that provides insight on how to leverage sending Security Copilot audit logs to your cloud native SIEM to gain deeper insights into usage and take proactive measures to mitigate risks.
Access prompt response pair content in Microsoft Purview DSPM for AI
Before you begin
This section gives an overview of the prerequisites to access prompt response pair content via Purview DSPM for AI.
You'll need to:
- Verify that you have opted to allow Microsoft Purview access inside Security Copilot. For more information, see Enable the audit log capability.
- Verify that necessary setup steps are complete, see Learn | DSPM for AI Setup.
- Validate that any administrator requiring policy creation or the ability to view content captured in prompts and responses meets the minimum permission levels. The role and permission configurations are detailed on Learn | DSPM for AI
- Confirm that DSPM policies for Copilot content capture have been configured, see DSPM for AI Default Policies on Learn.
Once the prerequisties are met different ways to enact information protection, and viewing the content within prompt and response pairs are posbible.
- Review the capbilites of the Purview DSPM for AI solution Microsoft Purview data security and compliance protections for generative AI apps
- Protect the information accessed by different Copilot experiences Information protection considerations for Copilot
- View and search content within the Activity explorer events for Purview DSPM for AI Activity explorer events