Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
File policies are a great tool for finding threats to your information protection policies. For instance, create file policies that find places where users stored sensitive information, credit card numbers, and third-party ICAP files in your cloud.
In this tutorial, you'll learn how to use Microsoft Defender for Cloud Apps to detect unwanted files stored in your cloud that leave you vulnerable, and take immediate action to stop them in their tracks and lock down the files that pose a threat by using Admin quarantine to protect your files in the cloud, remediate problems, and prevent future leaks from occurring.
Understand how quarantine works
Note
- For a list of apps that support admin quarantine, see the list of governance actions.
- Files labeled by Defender for Cloud Apps can't be quarantined.
- Defender for Cloud Apps admin quarantine actions is limited to 100 actions per day.
- Sharepoint sites that are renamed either directly or as part of domain rename can't be used as a folder location for admin quarantine.
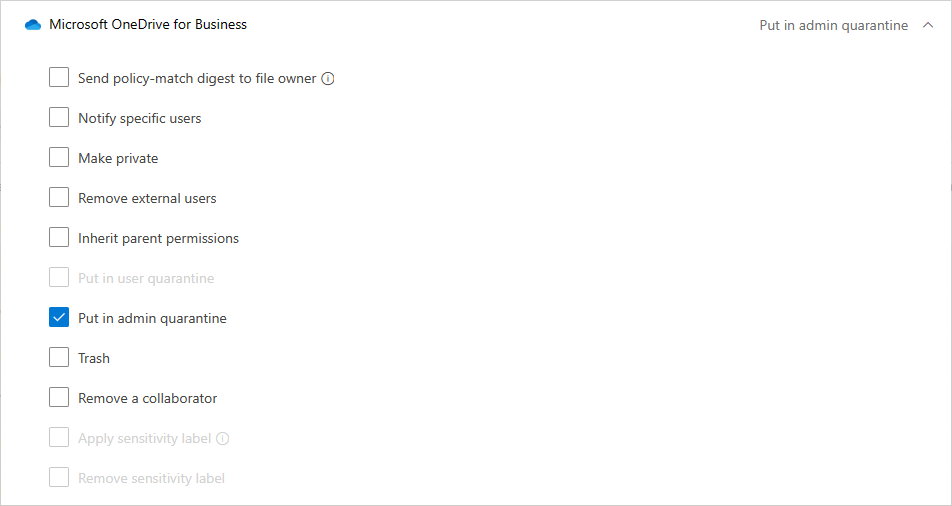
When a file matches a policy, the Admin quarantine option is available for the file.
Set an automated quarantine action in the policy.
When Admin quarantine is applied, the following things occur behind the scenes:
The original file is moved to the admin quarantine folder you set.
The original file is deleted.
A tombstone file is uploaded to the original file location.
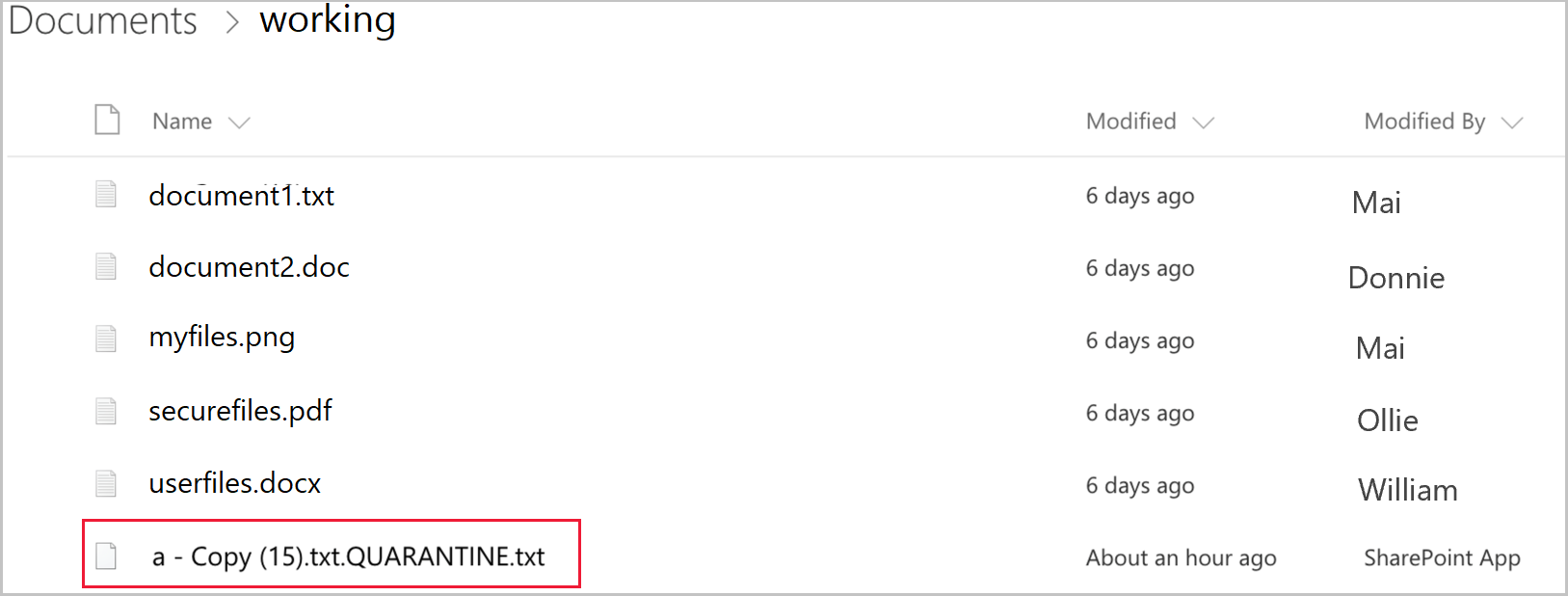
The user can only access the tombstone file. In the file, they can read the custom guidelines provided by IT and the correlation ID to give IT to release the file.
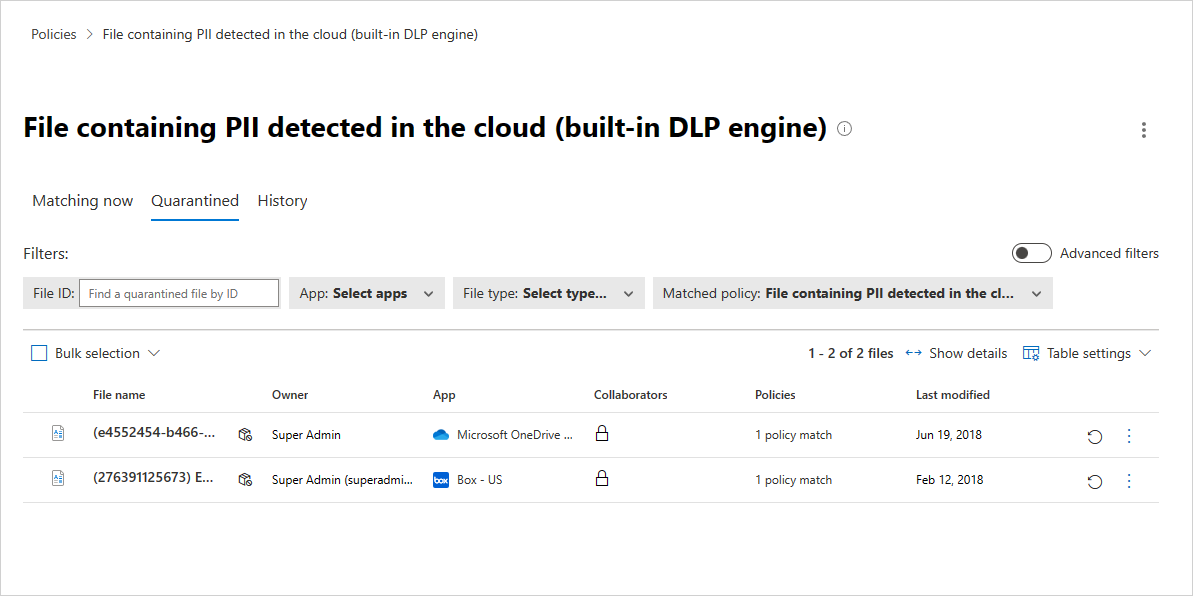
When you receive the alert that a file has been quarantined, go to Policies -> Policy Management. Then select the Information Protection tab. In the row with your file policy, choose the three dots at the end of the line, and select View all matches. This brings you the report of matches, where you can see the matching and quarantined files:
After a file is quarantined, use the following process to remediate the threat situation:
Inspect the file in the quarantined folder on SharePoint online.
You can also look at the audit logs to deep dive into the file properties.
If you find the file is against corporate policy, run the organization's Incident Response (IR) process.
If you find that the file is harmless, you can restore the file from quarantine. At that point the original file is released, and copied back to the original location. The tombstone is deleted, and the user can access the file.
Validate that the policy runs smoothly. Then, you can use the automatic governance actions in the policy to prevent further leaks and automatically apply an Admin quarantine when the policy is matched.
Note
When you restore a file:
- Original shares aren't restored, default folder inheritance applied.
- The restored file contains only the most recent version.
- The quarantine folder site access management is the customer's responsibility.
Set up admin quarantine
Set file policies that detect breaches. Examples of these types of policies include:
- A metadata only policy such as a sensitivity label in SharePoint Online
- A native data loss prevention (DLP) policy such as a policy that searches for credit card numbers
- An ICAP third-party policy such as a policy that looks for Vontu
Set a quarantine location:
For Microsoft 365 SharePoint or OneDrive for Business, you can't put files in admin quarantine as part of a policy until you set it up:
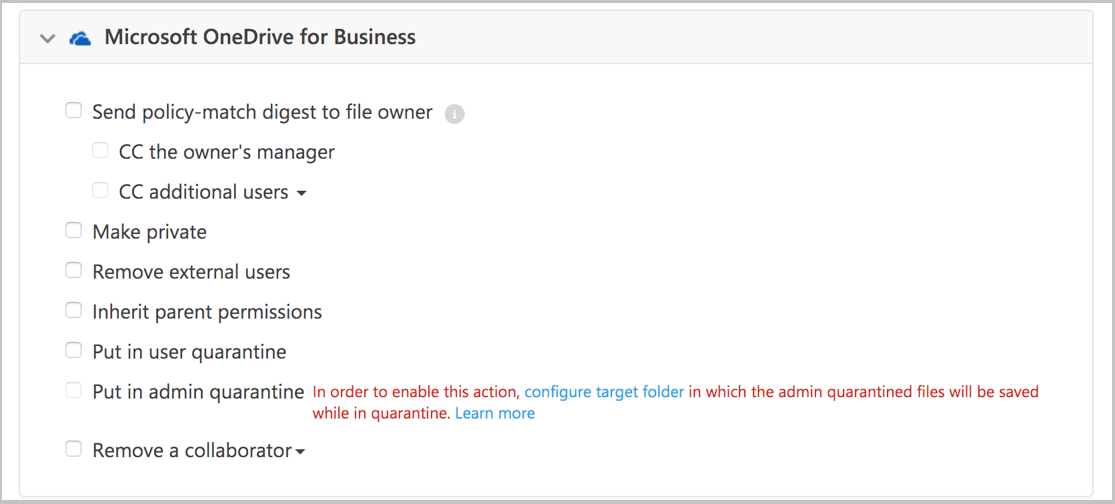
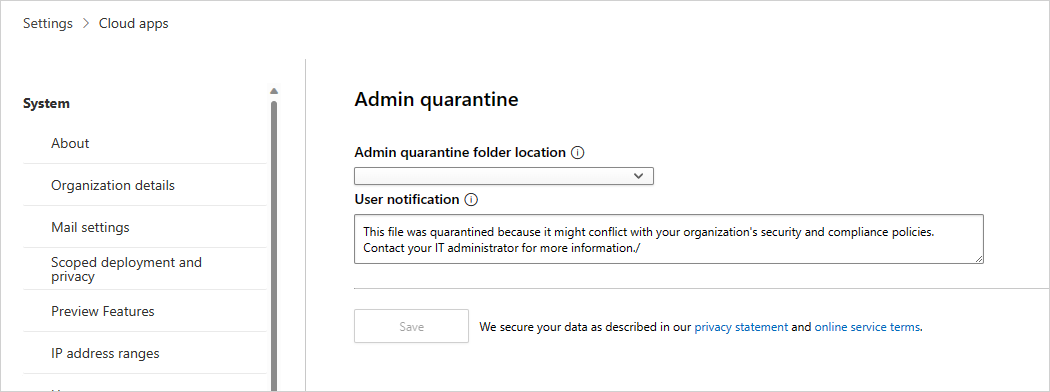
To set admin quarantine settings, in the Microsoft Defender Portal, select Settings. Then choose Cloud Apps. Under Information Protection, choose Admin quarantine. Provide a site for the quarantine folder location and a user notification that your user will receive when their file is quarantined.
Note
Defender for Cloud Apps creates a quarantine folder on the selected site.
For Box, the quarantine folder location and user message can't be customized. The folder location is the drive of the admin who connected Box to Defender for Cloud Apps and the user message is: This file was quarantined to your administrator's drive because it might violate your company's security and compliance policies. Contact your IT administrator for help.
Next steps
If you run into any problems, we're here to help. To get assistance or support for your product issue, please open a support ticket.