Onboard Windows devices using Group Policy
Important
Some information in this article relates to a prereleased product which may be substantially modified before it's commercially released. Microsoft makes no warranties, expressed or implied, with respect to the information provided here.
Applies to:
- Group Policy
- Microsoft Defender for Endpoint Plan 1
- Microsoft Defender for Endpoint Plan 2
- Microsoft Defender XDR
Want to experience Defender for Endpoint? Sign up for a free trial.
Note
To use Group Policy (GP) updates to deploy the package, you must be on Windows Server 2008 R2 or later.
For Windows Server 2019 and Windows Server 2022, you may need to replace NT AUTHORITY\Well-Known-System-Account with NT AUTHORITY\SYSTEM of the XML file that the Group Policy preference creates.
Note
If you're using the new, unified Microsoft Defender for Endpoint solution for Windows Server 2012 R2 and 2016, please ensure you are using the latest ADMX files in your central store to get access to the correct Microsoft Defender for Endpoint policy options. Please reference How to create and manage the Central Store for Group Policy Administrative Templates in Windows and download the latest files for use with Windows 10.
Check out Identify Defender for Endpoint architecture and deployment method to see the various paths in deploying Defender for Endpoint.
Open the GP configuration package file (
WindowsDefenderATPOnboardingPackage.zip) that you downloaded from the service onboarding wizard. You can also get the package from the Microsoft Defender portal:In the navigation pane, select Settings > Endpoints > Device management > Onboarding.
Select the operating system.
In the Deployment method field, select Group policy.
Click Download package and save the .zip file.
Extract the contents of the .zip file to a shared, read-only location that can be accessed by the device. You should have a folder called OptionalParamsPolicy and the file WindowsDefenderATPOnboardingScript.cmd.
To create a new GPO, open the Group Policy Management Console (GPMC), right-click Group Policy Objects you want to configure and click New. Enter the name of the new GPO in the dialogue box that is displayed and click OK.
Open the Group Policy Management Console (GPMC), right-click the Group Policy Object (GPO) you want to configure and click Edit.
In the Group Policy Management Editor, go to Computer configuration, then Preferences, and then Control panel settings.
Right-click Scheduled tasks, point to New, and then click Immediate Task (At least Windows 7).
In the Task window that opens, go to the General tab. Under Security options click Change User or Group and type SYSTEM and then click Check Names then OK. NT AUTHORITY\SYSTEM appears as the user account the task will run as.
Select Run whether user is logged on or not and check the Run with highest privileges check box.
In the Name field, type an appropriate name for the scheduled task (for example, Defender for Endpoint Deployment).
Go to the Actions tab and select New... Ensure that Start a program is selected in the Action field. Enter the UNC path, using the file server's fully qualified domain name (FQDN), of the shared WindowsDefenderATPOnboardingScript.cmd file.
Select OK and close any open GPMC windows.
To link the GPO to an Organization Unit (OU), right-click and select Link an existing GPO. In the dialogue box that is displayed, select the Group Policy Object that you wish to link. Click OK.
Tip
After onboarding the device, you can choose to run a detection test to verify that the device is properly onboarded to the service. For more information, see Run a detection test on a newly onboarded Defender for Endpoint device.
Additional Defender for Endpoint configuration settings
For each device, you can state whether samples can be collected from the device when a request is made through Microsoft Defender XDR to submit a file for deep analysis.
You can use Group Policy (GP) to configure settings, such as settings for the sample sharing used in the deep analysis feature.
Configure sample collection settings
On your GP management device, copy the following files from the configuration package:
Copy AtpConfiguration.admx into C:\Windows\PolicyDefinitions
Copy AtpConfiguration.adml into C:\Windows\PolicyDefinitions\en-US
If you're using a Central Store for Group Policy Administrative Templates, copy the following files from the configuration package:
Copy AtpConfiguration.admx into \\<forest.root>\SysVol\<forest.root>\Policies\PolicyDefinitions
Copy AtpConfiguration.adml into \\<forest.root>\SysVol\<forest.root>\Policies\PolicyDefinitions\en-US
Open the Group Policy Management Console, right-click the GPO you want to configure and click Edit.
In the Group Policy Management Editor, go to Computer configuration.
Click Policies, then Administrative templates.
Click Windows components and then Windows Defender ATP.
Choose to enable or disable sample sharing from your devices.
Note
If you don't set a value, the default value is to enable sample collection.
Other recommended configuration settings
Update endpoint protection configuration
After configuring the onboarding script, continue editing the same group policy to add endpoint protection configurations. Perform group policy edits from a system running Windows 10 or Server 2019, Windows 11, or Windows Server 2022 to ensure you have all of the required Microsoft Defender Antivirus capabilities. You may need to close and reopen the group policy object to register the Defender ATP configuration settings.
All policies are located under Computer Configuration\Policies\Administrative Templates.
Policy location: \Windows Components\Windows Defender ATP
| Policy | Setting |
|---|---|
| Enable\Disable Sample collection | Enabled - "Enable sample collection on machines" checked |
Policy location: \Windows Components\Microsoft Defender Antivirus
| Policy | Setting |
|---|---|
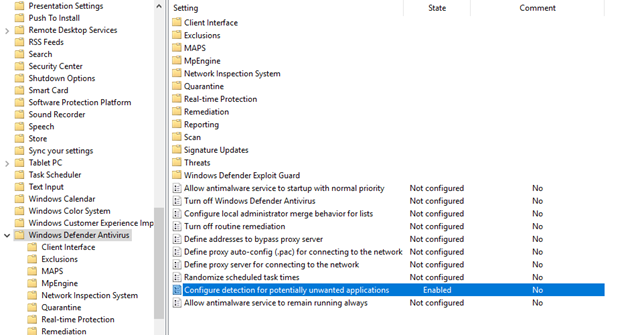
| Configure detection for potentially unwanted applications | Enabled, Block |
Policy location: \Windows Components\Microsoft Defender Antivirus\MAPS
| Policy | Setting |
|---|---|
| Join Microsoft MAPS | Enabled, Advanced MAPS |
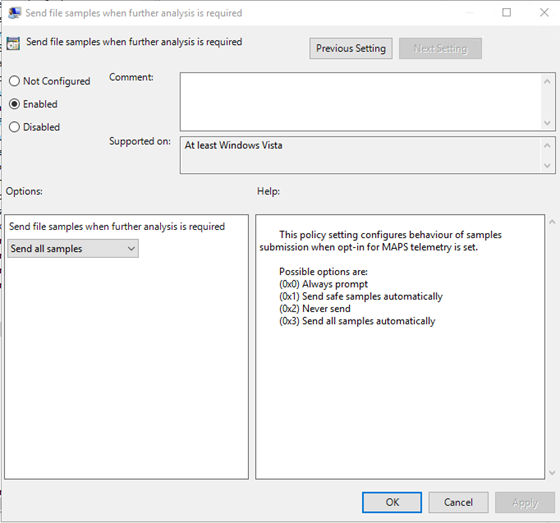
| Send file samples when further analysis is required | Enabled, Send safe samples |
Policy location: \Windows Components\Microsoft Defender Antivirus\Real-time Protection
| Policy | Setting |
|---|---|
| Turn off real-time protection | Disabled |
| Turn on behavior monitoring | Enabled |
| Scan all downloaded files and attachments | Enabled |
| Monitor file and program activity on your computer | Enabled |
Policy location: \Windows Components\Microsoft Defender Antivirus\Scan
These settings configure periodic scans of the endpoint. We recommend performing a weekly quick scan, performance permitting.
| Policy | Setting |
|---|---|
| Check for the latest virus and spyware security intelligence before running a scheduled scan | Enabled |
Policy location: \Windows Components\Microsoft Defender Antivirus\Microsoft Defender Exploit Guard\Attack Surface Reduction
Get the current list of attack surface reduction rules GUIDs from Attack surface reduction rules deployment Step 3: Implement ASR rules. For additional, per rules details, see Attack surface reduction rules reference
Open the Configure Attack Surface Reduction policy.
Select Enabled.
Select the Show button.
Add each GUID in the Value Name field with a Value of 2.
This will set each up for audit only.
| Policy | Location | Setting |
|---|---|---|
| Configure Controlled folder access | \Windows Components\Microsoft Defender Antivirus\Microsoft Defender Exploit Guard\Controlled Folder Access | Enabled, Audit Mode |
Run a detection test to verify onboarding
After onboarding the device, you can choose to run a detection test to verify that a device is properly onboarded to the service. For more information, see Run a detection test on a newly onboarded Microsoft Defender for Endpoint device.
Offboard devices using Group Policy
For security reasons, the package used to Offboard devices will expire 7 days after the date it was downloaded. Expired offboarding packages sent to a device will be rejected. When downloading an offboarding package you'll be notified of the packages expiry date and it will also be included in the package name.
Note
Onboarding and offboarding policies must not be deployed on the same device at the same time, otherwise this will cause unpredictable collisions.
Get the offboarding package from the Microsoft Defender portal:
In the navigation pane, select Settings > Endpoints > Device management > Offboarding.
Select the operating system.
In the Deployment method field, select Group policy.
Click Download package and save the .zip file.
Extract the contents of the .zip file to a shared, read-only location that can be accessed by the device. You should have a file named WindowsDefenderATPOffboardingScript_valid_until_YYYY-MM-DD.cmd.
Open the Group Policy Management Console (GPMC), right-click the Group Policy Object (GPO) you want to configure and click Edit.
In the Group Policy Management Editor, go to Computer configuration, then Preferences, and then Control panel settings.
Right-click Scheduled tasks, point to New, and then click Immediate task.
In the Task window that opens, go to the General tab under Security options and select Change User or Group, enter SYSTEM, then select Check Names and then OK. NT AUTHORITY\SYSTEM appears as the user account that the task will run as.
Select Run whether user is logged on or not and check the Run with highest privileges check-box.
In the Name field, type an appropriate name for the scheduled task (for example, Defender for Endpoint Deployment).
Go to the Actions tab and select New.... Ensure that Start a program is selected in the Action field. Enter the UNC path, using the file server's fully qualified domain name (FQDN), of the shared WindowsDefenderATPOffboardingScript_valid_until_YYYY-MM-DD.cmd file.
Select OK and close any open GPMC windows.
Important
Offboarding causes the device to stop sending sensor data to the portal but data from the device, including reference to any alerts it has had will be retained for up to 6 months.
Monitor device configuration
With Group Policy there isn't an option to monitor deployment of policies on the devices. Monitoring can be done directly on the portal, or by using the different deployment tools.
Monitor devices using the portal
- Go to the Microsoft Defender portal.
- Click Devices inventory.
- Verify that devices are appearing.
Note
It can take several days for devices to start showing on the Devices list. This includes the time it takes for the policies to be distributed to the device, the time it takes before the user logs on, and the time it takes for the endpoint to start reporting.
Setup Defender AV policies
Create a new Group Policy or group these settings in with the other policies. This is dependent upon the customer's environment and how they would like to roll out the service by targeting different organizational units (OUs).
After you choose the GP, or create a new one, edit the GP.
Browse to Computer Configuration > Policies > Administrative Templates > Windows Components > Microsoft Defender Antivirus > Real-time Protection.
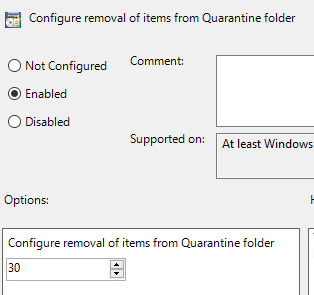
In the Quarantine folder, configure removal of items from Quarantine folder.
In the Scan folder, configure the scan settings.
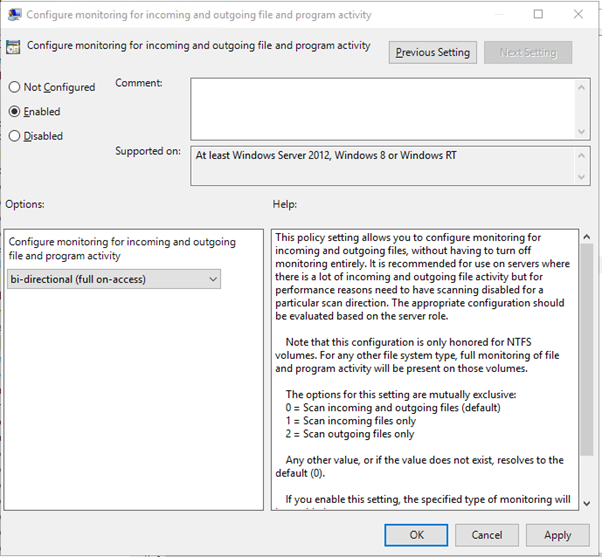
Monitor all files in Real time protection
Browse to Computer Configuration > Policies > Administrative Templates > Windows Components > Microsoft Defender Antivirus > Real-time Protection.
Configure Windows Defender SmartScreen settings
Browse to Computer Configuration > Policies > Administrative Templates > Windows Components > Windows Defender SmartScreen > Explorer.
Browse to Computer Configuration > Policies > Administrative Templates > Windows Components > Windows Defender SmartScreen > Microsoft Edge.
Configure Potentially Unwanted Applications
Browse to Computer Configuration > Policies > Administrative Templates > Windows Components > Microsoft Defender Antivirus.
Configure Cloud Deliver Protection and send samples automatically
Browse to Computer Configuration > Policies > Administrative Templates > Windows Components > Microsoft Defender Antivirus > MAPS.
Note
The Send all samples option will provide the most analysis of binaries/scripts/docs which increases security posture. The Send safe samples option limits the type of binaries/scripts/docs being analyzed, and decreases security posture.
For more information, see Turn on cloud protection in Microsoft Defender Antivirus, and Cloud protection and sample submission in Microsoft Defender Antivirus.
Check for signature update
Browse to Computer Configuration > Policies > Administrative Templates > Windows Components > Microsoft Defender Antivirus > Security Intelligence Updates.
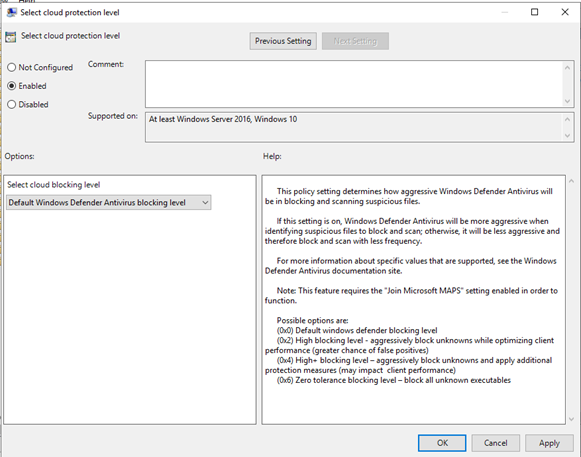
Configure cloud deliver timeout and protection level
Browse to Computer Configuration > Policies > Administrative Templates > Windows Components > Microsoft Defender Antivirus > MpEngine. When you configure cloud protection level policy to Default Microsoft Defender Antivirus blocking policy this will disable the policy. This is what is required to set the protection level to the windows default.
Related topics
- Onboard Windows devices using Microsoft Endpoint Configuration Manager
- Onboard Windows devices using Mobile Device Management tools
- Onboard Windows devices using a local script
- Onboard non-persistent virtual desktop infrastructure (VDI) devices
- Run a detection test on a newly onboarded Microsoft Defender for Endpoint devices
- Troubleshoot Microsoft Defender for Endpoint onboarding issues
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender for Endpoint Tech Community.