Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Note
The Vulnerability Management section in the Microsoft Defender portal is now located under Exposure management. With this change, you can now consume and manage security exposure data and vulnerability data in a unified location, to enhance your existing Vulnerability Management features. Learn more.
These changes are relevant for Preview customers (Microsoft Defender XDR + Microsoft Defender for Identity preview option).
Important
Some information in this article relates to a prereleased product which may be substantially modified before it's commercially released. Microsoft makes no warranties, expressed or implied, with respect to the information provided here.
Microsoft Defender Vulnerability Management provides exceptions to help you control what type of data is relevant to your organization and to selectively exclude certain data from your remediation efforts.
This article describes how to create, view, and manage exceptions.
To learn more about exceptions, see Exceptions in Microsoft Defender Vulnerability Management.
Tip
Did you know you can try all the features in Microsoft Defender Vulnerability Management for free? Find out how to sign up for a free trial.
Types of exceptions
Microsoft Defender Vulnerability Management supports two types of exceptions. A security recommendation exception excludes an entire recommendation, while a Common Vulnerabilities and Exposures (CVE) exception excludes a specific CVE.
For more information, see Types of exceptions.
Tip
This article provides instructions relevant to both types of exceptions. Each section specifies the difference between CVE exceptions and security recommendation exceptions where applicable.
Prerequisites
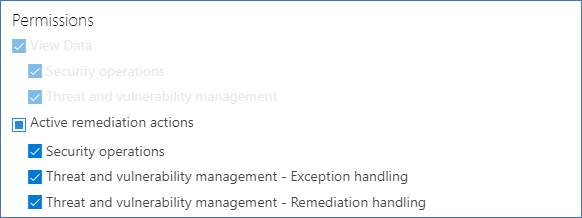
Check if you have the exceptions handling permission. Learn more about RBAC roles.
Exceptions are effective only for the specified duration and scope. Ensure you document the rationale and monitor for any changes in your environment.
Note
Exceptions are currently only supported in the Microsoft Defender portal, and not via public API.
Create an exception
Select the recommendation or CVE to exclude
In the Microsoft Defender portal, do one of the following:
- If you're a Microsoft Defender XDR + Microsoft Defender for Identity preview customer, select Exposure management > Recommendations, and select Vulnerabilities on the left.
- If you're an existing customer, select Endpoints > Vulnerability management > Recommendations.
By default, the page shows all recommendations filtered to all device groups. To view recommendations for a specific device group:
If you're a Microsoft Defender XDR + Microsoft Defender for Identity preview customer, select Scope filter on the top right, and select the device group you want to view from the Device Groups section.

If you're an existing customer, select Filter by device groups on the top right, and select the device group you want to view.
Select a security recommendation you would like to create an exception for. In the recommendation details page, on the bottom right, select Exception options.
Fill in exception details and apply the exception (recommendation and CVE exceptions)
Fill in the exception justification and the exception duration.
Select the exception scope: Apply the exception globally or to specific device groups.
Select Confirm and apply. A confirmation message appears.
It can take up to one hour for the change to take effect on the exposed assets count and the organization's exposure score. During this period, the recommendation or CVE may still appear in reports and dashboards until the update is fully processed.
When the exception takes effect:
- For CVE exceptions, the CVE no longer appears in the inventory lists for the selected scope. For recommendation exceptions, the recommendation isn't active until the end of the exception duration. The recommendation state changes to Full exception or Partial exception (by device group).
- Threat analytics and alerts related to the excluded recommendation or CVE are suppressed.
- The recommendation details or CVE details page indicates that the recommendation or CVE has an exception.
- The organization's exposure score and secure score may be updated to reflect the exception. For more information, see View impact after exceptions are applied and Exposed devices and impact after exceptions.
Note
Exception durations can't be extended. If you need the exception to continue after it expires, create a new exception with the required duration and scope.
After you cancel an exception, you can immediately create a new exception with the same scope or different settings.
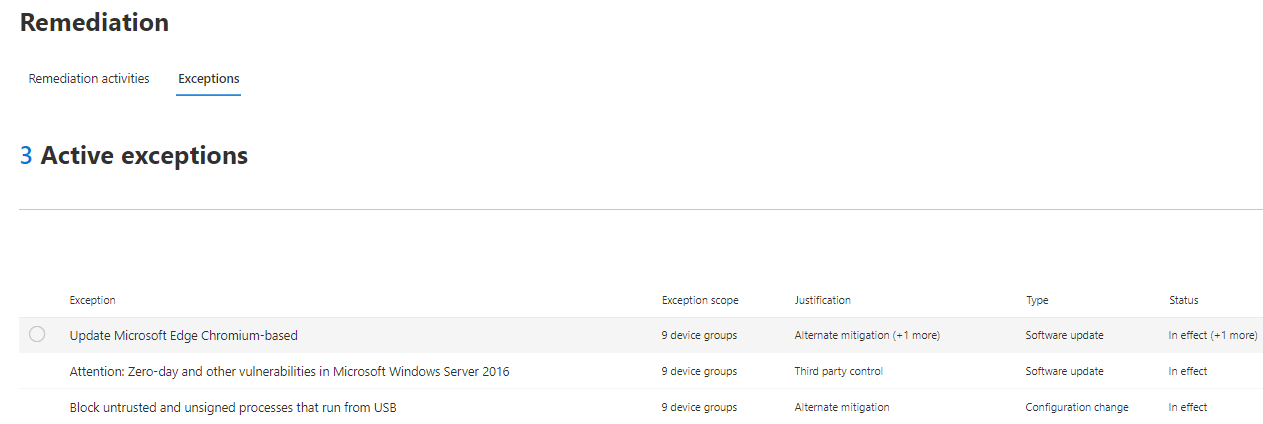
View all exceptions (recommendation and CVE exceptions)
Navigate to the Exceptions tab in the Remediation page. You can filter by justification, type, and status.
Select an exception to open a flyout with more details. Exceptions per devices group will have a list of every device group the exception covers, which you can export. You can also view the related recommendation or cancel the exception.
Cancel an exception (recommendation and CVE exceptions)
To cancel an exception:
Navigate to the Exceptions tab in the Remediation page, and do one of the following.
To cancel a single exception, in the exception details page, under the exception name, select Cancel exception.
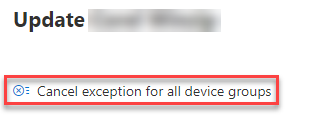
To cancel the exception for all device groups or for a global exception, select Cancel exception for all device groups. You can only cancel exceptions for device groups you have permissions for.
To cancel the exception for a specific device group, select the device group, and in the device group page, select Cancel exception.
View impact after exceptions are applied (recommendation exceptions only)
In the Recommendations page, select Customize columns and select Exposed devices (after exceptions) and Impact (after exceptions).
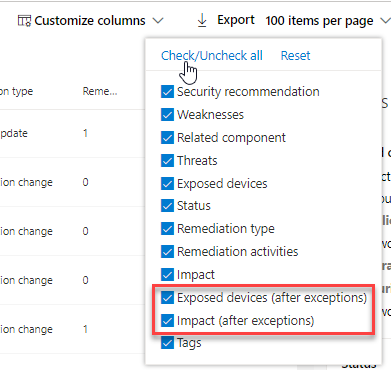
The exposed devices (after exceptions) column shows the remaining devices that are still exposed to vulnerabilities after exceptions are applied.
For more information, see Exposed devices and impact after exceptions.


