Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
This article explains how to exclude specific analytics rules from the Microsoft Defender XDR correlation engine. This feature helps organizations migrating from Microsoft Sentinel maintain predictable incident behavior and ensure compatibility with existing automation workflows.
Overview
Microsoft Defender XDR groups multiple alerts and incidents into unified attack stories. While this capability provides powerful security insights, it can lead to unexpected behavior for organizations migrating from Microsoft Sentinel, where incidents are static and determined solely by analytics rule configurations.
By excluding specific analytics rules from correlation, you can ensure that alerts generated by those rules bypass the correlation engine and group into incidents exactly as they did in Microsoft Sentinel—based only on the grouping configuration of the analytics rule.
For more information about how correlation works in Microsoft Defender XDR, see Alert correlation and incident merging in the Microsoft Defender portal.
Prerequisites
To exclude analytics rules from correlation, you need the following permissions:
Microsoft Sentinel Contributor Users with this Azure role can manage Microsoft Sentinel SIEM workspace data, including alerts and detections.
How exclusion works
When you exclude an analytics rule from correlation:
- Any alert generated by that rule bypasses the correlation engine
- Alerts are grouped into incidents based solely on the analytics rule's grouping configuration
- The behavior matches how incidents were created in Microsoft Sentinel
- The rule operates independently of the correlation logic that normally creates attack stories
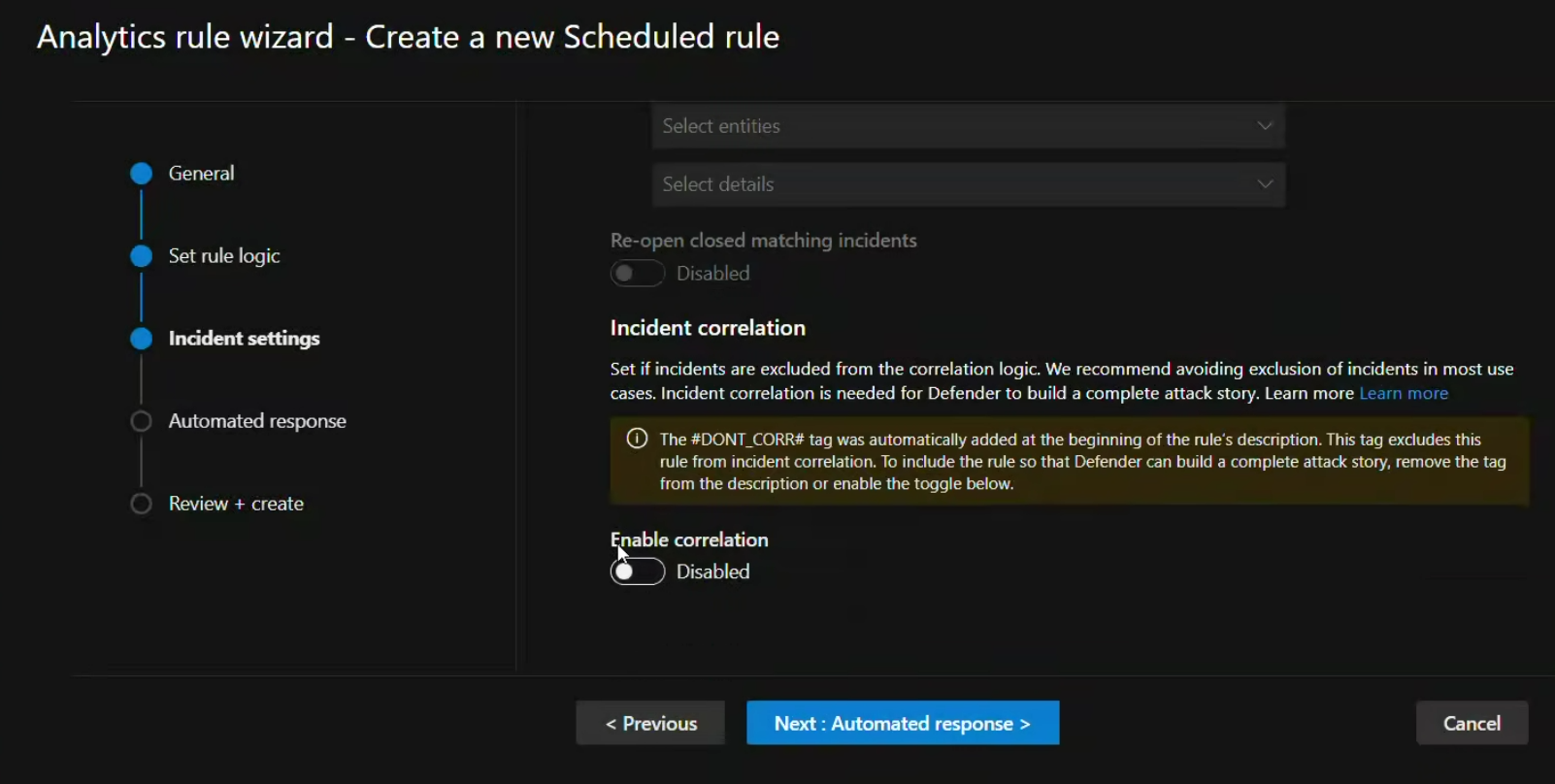
This exclusion is controlled by adding the #DONT_CORR# tag to the beginning of the rule's description.
Exclude a rule from correlation using the UI
You can exclude an analytics rule from correlation using a toggle in the analytics rule wizard.
Go to the Microsoft Defender portal and sign in.
Go to the Analytics rule wizard.
In the General tab of the rule wizard, enter a name and description.
In the Set rule logic tab, configure the rule logic as needed.
In the Incident settings tab, make sure the Enable correlation toggle is set to Disabled.
Set the toggle to On to exclude the rule from correlation.
When you exclude a rule by using the UI toggle, the #DONT_CORR# tag is automatically added to the beginning of the rule's description. The analytics rules view now includes a column for correlation state so you can easily see which rules are excluded as well as filter the list to see rules in a specific state.
Exclude a rule from correlation manually
You can manually add or remove the #DONT_CORR# tag to control the correlation state of an analytics rule.
Add the tag manually
Open the analytics rule in edit mode.
In the rule's Description field, add
#DONT_CORR#at the very beginning of the text.Save the rule.
Control correlation exclusion via API
You can programmatically control the exclusion state of analytics rules by adding or removing the #DONT_CORR# tag through the analytics API.
To modify a rule's correlation state:
Use the Microsoft Defender XDR API to retrieve the rule's current configuration.
Add or remove the
#DONT_CORR#tag at the beginning of the rule's description field.Update the rule using the API.
For more information about using the Microsoft Defender XDR API, see Microsoft Defender XDR APIs overview.
Important considerations
Keep the following points in mind when using correlation exclusion:
The correlation state always matches the tag. If you exclude a rule by using the UI toggle and then manually remove the
#DONT_CORR#tag from the description, the rule's correlation state reverts to Correlation enabled.All analytics rules have correlation enabled by default unless explicitly excluded.
Even when you exclude a rule from correlation, if you define an analytics rule with a dynamic title, the incident title in the Defender portal might be different from the title in Microsoft Sentinel. The Microsoft Sentinel title is the title of the first alert, and in Defender it falls back to the common MITRE tactic of all alerts.
Changing a rule's correlation state doesn't affect alerts that were created before the change. Alerts receive their correlation state when they're created, and this state remains static.
The correlation engine is designed to build complete attack stories and significantly helps SOC analysts understand attacks and respond efficiently. Only exclude rules from correlation when necessary for specific business or operational requirements.
Tag formatting rules:
- Not case sensitive - You can use any combination of uppercase and lowercase letters (for example,
#dont_corr#or#DONT_CORR#). - Spacing is flexible - You can add any number of spaces between the tag and the rest of the description, or no spaces at all.
- Must be at the beginning - The tag must appear at the start of the description field.
For example, the following descriptions are all valid:
- #DONT_CORR# This rule detects suspicious sign in attempts
- #dont_corr# This rule monitors file modifications
- #DONT_CORR#This rule has no space after the tag
- Not case sensitive - You can use any combination of uppercase and lowercase letters (for example,
In specific scenarios, the incident title might differ between the Defender portal and Microsoft Sentinel, even when you turn off incident correlation for the rule:
- When an incident contains alerts with different titles, the Defender portal displays the incident name as the common MITRE ATT&CK technique of all alerts, while Microsoft Sentinel uses the title of the first alert.
- Alerts within the same incident can have different titles when the alert title is configured as a dynamic title and alert grouping to incidents is turned on.
Next steps
- Alert correlation and incident merging in the Microsoft Defender portal
- Create custom detection rules
- Manage custom detections
- Manage incidents in Microsoft Defender
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender XDR Tech Community.