Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
This article describes how Microsoft Edge supports Conditional Access for managed devices and how you can access Conditional Access protected resources with unmanaged devices.
Introduction
When it comes to managing and protecting your cloud resources, identity and access are both important. In a hybrid computing world, users can access your organization's resources using various devices and apps from anywhere at anytime. Just focusing on who can access a resource isn't good enough. You also need to factor in how a resource is accessed.
Conditional Access gives you a balance between security and productivity. For more information, see Plan a Conditional Access deployment, a detailed guide to help plan and deploy Conditional Access in Microsoft Entra ID (formerly known as Azure Active Directory). (For more information about this name change, see New name for Microsoft Entra ID.)
Microsoft Edge natively supports access to Conditional Access protected resources on both managed and unmanaged devices.
Note
We have exempted Edge Auth from enforcing specific device-based Conditional Access controls during the authentication bootstrap process. Specifically, the following controls are currently exempted: RequireApprovedApp, RequireCompliantApp, and RequireCompliantDevice. However, RequireDomainJoinedDevice is not exempted and will be enforced.
Accessing Conditional Access protected URLs with Microsoft Edge on managed devices
Microsoft Edge natively supports Microsoft Entra (formerly known as Azure Active Directory) Conditional Access. There's no need to install a separate extension, Edge's native support provides stable and high quality access. When you're signed into an Edge profile with enterprise Microsoft Entra ID (formerly known as Azure Active Directory) credentials, Microsoft Edge allows seamless access to enterprise cloud resources protected using Conditional Access. This support is available across all platforms, including all supported versions of Windows and macOS.
The respective Microsoft Entra (formerly known as Azure Active Directory) account needs to be connected to Windows, so a Primary Refresh Token is sent along with the request for evaluation in the Conditional Access policy. To add a work or school account to Windows, follow these steps to Add or remove accounts on your PC. Note that there are limits to the number of work or school accounts connected to Windows, which is documented in this device management FAQ.
Accessing Conditional Access protected URLs with Microsoft Edge on BYOD using Intune MAM
Mobile Application Management (MAM) for unenrolled devices is commonly used for personal or bring your own devices (BYOD). MAM is an option for users who don't enroll their personal devices, but still need access to their organization's email, Teams meetings, and more. For more specific information about MAM, see What is Microsoft Intune app management? and the MAM FAQ. For more information about conditional access on Windows devices, see Require an app protection policy on Windows devices.
Access issues
On a compliant device, the identity accessing the resource should match the identity on the profile. If it doesn't or the device is unmanaged, access is blocked and you'll see a message like the one in the following screenshot. In this example, balas@contos.com is the sign-in account needed to access the resource.
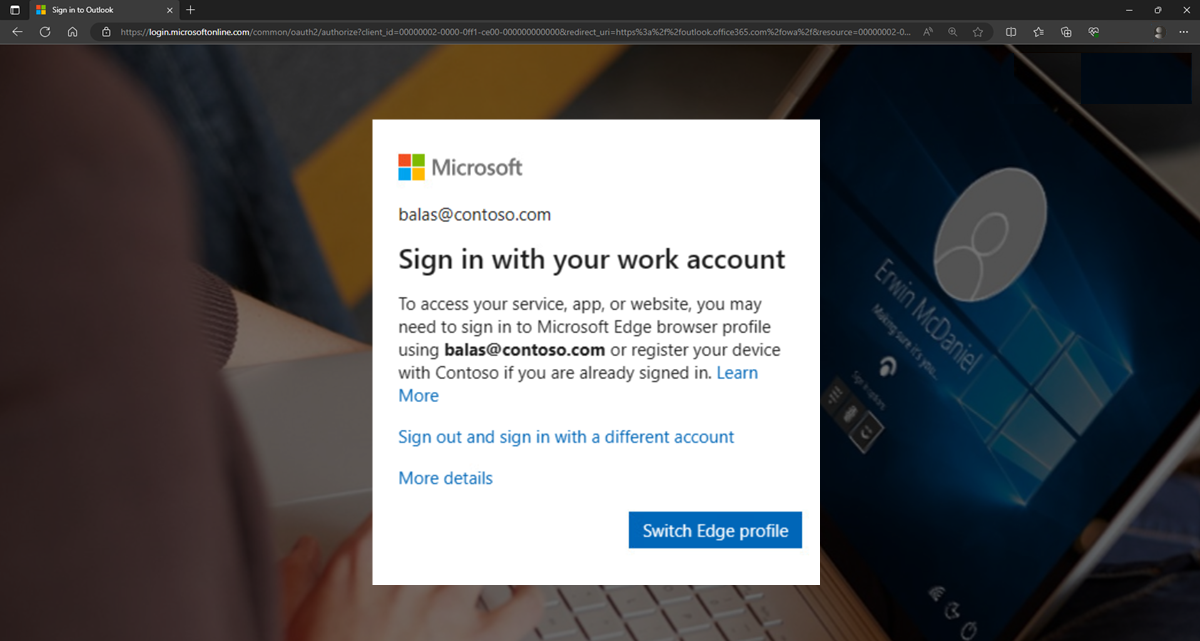
Fixing access issues with Microsoft Edge on managed devices
If access is blocked, you have to switch to the required profile or create a profile with a matching identity. Select Switch Edge profile and Microsoft Edge will guide you through the sign-in process. For more information, see Require an app protection policy on Windows devices (preview).
You can also work with profile settings by selecting the account picture in the browser and using the dropdown menu for the following tasks:
- Manage your profiles - Click the gear icon (Manage profile settings) to open Edge Settings.
- Pick an existing profile - Select the profile name.
- Create a personal profile - Select Set up a new personal profile.
- Create a new work profile - Select Other profiles and then select Set up a new work profile. The "Other profiles" option also lets you Browse as guest or Browse in Kids Mode.
Troubleshoot Conditional Access policies provides more information about fixing a Conditional Access issue.
Fixing access issues with unenrolled devices using Intune MAM
Access issues, such as an expired enrollment, and their resolution are in Troubleshooting.