Authenticate to Azure resources from .NET apps hosted on-premises
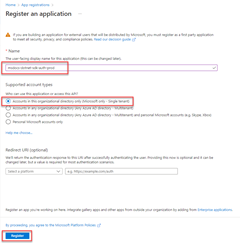
Apps hosted outside of Azure (for example, on-premises or at a third-party data center) should use an application service principal to authenticate to Azure when accessing Azure resources. Application service principal objects are created using the app registration process in Azure. When an application service principal is created, a client ID and client secret will be generated for your app. The client ID, client secret, and your tenant ID are then stored in environment variables so they can be used by the Azure Identity library to authenticate your app to Azure at runtime.
A different app registration should be created for each environment the app is hosted in. This allows environment specific resource permissions to be configured for each service principal and make sure an app deployed to one environment doesn't talk to Azure resources that are part of another environment.
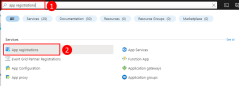
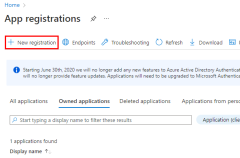
1 - Register the application in Azure
An app can be registered with Azure using either the Azure portal or the Azure CLI.
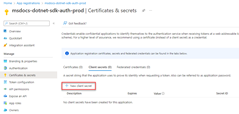
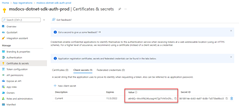
Sign in to the Azure portal and follow these steps.
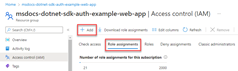
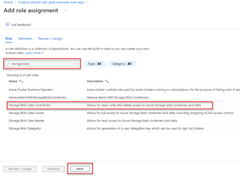
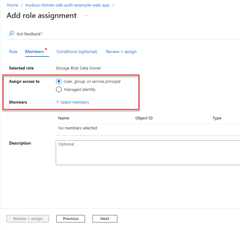
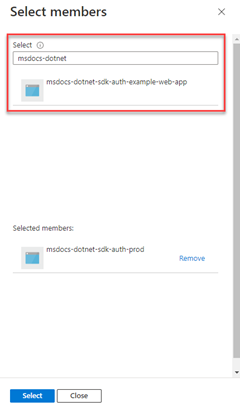
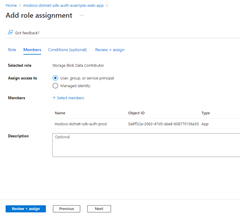
2 - Assign roles to the application service principal
Next, you need to determine what roles (permissions) your app needs on what resources and assign those roles to your app. Roles can be assigned a role at a resource, resource group, or subscription scope. This example shows how to assign roles for the service principal at the resource group scope, since most apps group all their Azure resources into a single resource group.
3 - Configure environment variables for application
The DefaultAzureCredential object will look for service principal credentials in a set of environment variables at runtime. There are multiple ways to configure environment variables when working with .NET depending on your tooling and environment.
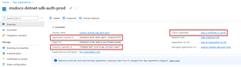
Regardless of which approach you choose, configure the following environment variables when working with a service principal:
AZURE_CLIENT_ID→ The app ID value.AZURE_TENANT_ID→ The tenant ID value.AZURE_CLIENT_SECRET→ The password/credential generated for the app.
If your app is hosted in IIS, it's recommended that you set environment variables per app pool to isolate settings between apps.
appcmd.exe set config -section:system.applicationHost/applicationPools /+"[name='Contoso'].environmentVariables.[name='ASPNETCORE_ENVIRONMENT',value='Production']" /commit:apphost
appcmd.exe set config -section:system.applicationHost/applicationPools /+"[name='Contoso'].environmentVariables.[name='AZURE_CLIENT_ID',value='00000000-0000-0000-0000-000000000000']" /commit:apphost
appcmd.exe set config -section:system.applicationHost/applicationPools /+"[name='Contoso'].environmentVariables.[name='AZURE_TENANT_ID',value='11111111-1111-1111-1111-111111111111']" /commit:apphost
appcmd.exe set config -section:system.applicationHost/applicationPools /+"[name='Contoso'].environmentVariables.[name='AZURE_CLIENT_SECRET',value='=abcdefghijklmnopqrstuvwxyz']" /commit:apphost
You can also configure these settings directly using the applicationPools element inside of the applicationHost.config file:
<applicationPools>
<add name="CorePool" managedRuntimeVersion="v4.0" managedPipelineMode="Classic">
<environmentVariables>
<add name="ASPNETCORE_ENVIRONMENT" value="Development" />
<add name="AZURE_CLIENT_ID" value="00000000-0000-0000-0000-000000000000" />
<add name="AZURE_TENANT_ID" value="11111111-1111-1111-1111-111111111111" />
<add name="AZURE_CLIENT_SECRET" value="=abcdefghijklmnopqrstuvwxyz" />
</environmentVariables>
</add>
</applicationPools>
4 - Implement DefaultAzureCredential in your application
DefaultAzureCredential is an opinionated, ordered sequence of mechanisms for authenticating to Microsoft Entra ID. Each authentication mechanism is a class derived from the TokenCredential class and is known as a credential. At runtime, DefaultAzureCredential attempts to authenticate using the first credential. If that credential fails to acquire an access token, the next credential in the sequence is attempted, and so on, until an access token is successfully obtained. In this way, your app can use different credentials in different environments without writing environment-specific code.
To use DefaultAzureCredential, add the Azure.Identity and optionally the Microsoft.Extensions.Azure packages to your application:
In a terminal of your choice, navigate to the application project directory and run the following commands:
dotnet add package Azure.Identity
dotnet add package Microsoft.Extensions.Azure
Azure services are accessed using specialized client classes from the various Azure SDK client libraries. These classes and your own custom services should be registered so they can be accessed via dependency injection throughout your app. In Program.cs, complete the following steps to register a client class and DefaultAzureCredential:
- Include the
Azure.IdentityandMicrosoft.Extensions.Azurenamespaces viausingdirectives. - Register the Azure service client using the corresponding
Add-prefixed extension method. - Pass an instance of
DefaultAzureCredentialto theUseCredentialmethod.
For example:
using Microsoft.Extensions.Azure;
using Azure.Identity;
builder.Services.AddAzureClients(clientBuilder =>
{
clientBuilder.AddBlobServiceClient(
new Uri("https://<account-name>.blob.core.windows.net"));
clientBuilder.UseCredential(new DefaultAzureCredential());
});
An alternative to UseCredential is to instantiate DefaultAzureCredential directly:
using Azure.Identity;
builder.Services.AddSingleton<BlobServiceClient>(_ =>
new BlobServiceClient(
new Uri("https://<account-name>.blob.core.windows.net"),
new DefaultAzureCredential()));
When the preceding code runs on your local development workstation, it looks in the environment variables for an application service principal or at locally installed developer tools, such as Visual Studio, for a set of developer credentials. Either approach can be used to authenticate the app to Azure resources during local development.
When deployed to Azure, this same code can also authenticate your app to other Azure resources. DefaultAzureCredential can retrieve environment settings and managed identity configurations to authenticate to other services automatically.