Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Important
Support for Windows 11 SE will end in October 2026
Microsoft will not release a feature update after Windows 11 SE, version 24H2. Support for Windows 11 SE—including software updates, technical assistance, and security fixes—will end in October 2026. While your device will continue to work, we recommend transitioning to a device that supports another edition of Windows 11 to ensure continued support and security.
This article describes important aspects to consider before deploying apps with managed installer.
Existing apps deployed in Intune
If you have Windows 11 SE devices that already have apps deployed through Intune, the apps won't get retroactively tagged with the managed installer mark. You may need to redeploy the apps through Intune to get them properly tagged with managed installer and allowed to run.
Enrollment Status Page
The Enrollment Status Page (ESP) is compatible with Windows 11 SE. However, due to the Windows 11 SE base policy, devices can be blocked from completing enrollment if:
- You have the ESP configured to block device use until required apps are installed, and
- You deploy an app that is blocked by the Windows 11 SE base policy, not installable via a managed installer (without more policies), and not allowed by any supplemental policies or AppLocker policies
If you choose to block device use on the installation of apps, you must ensure that apps are also not blocked from installation.
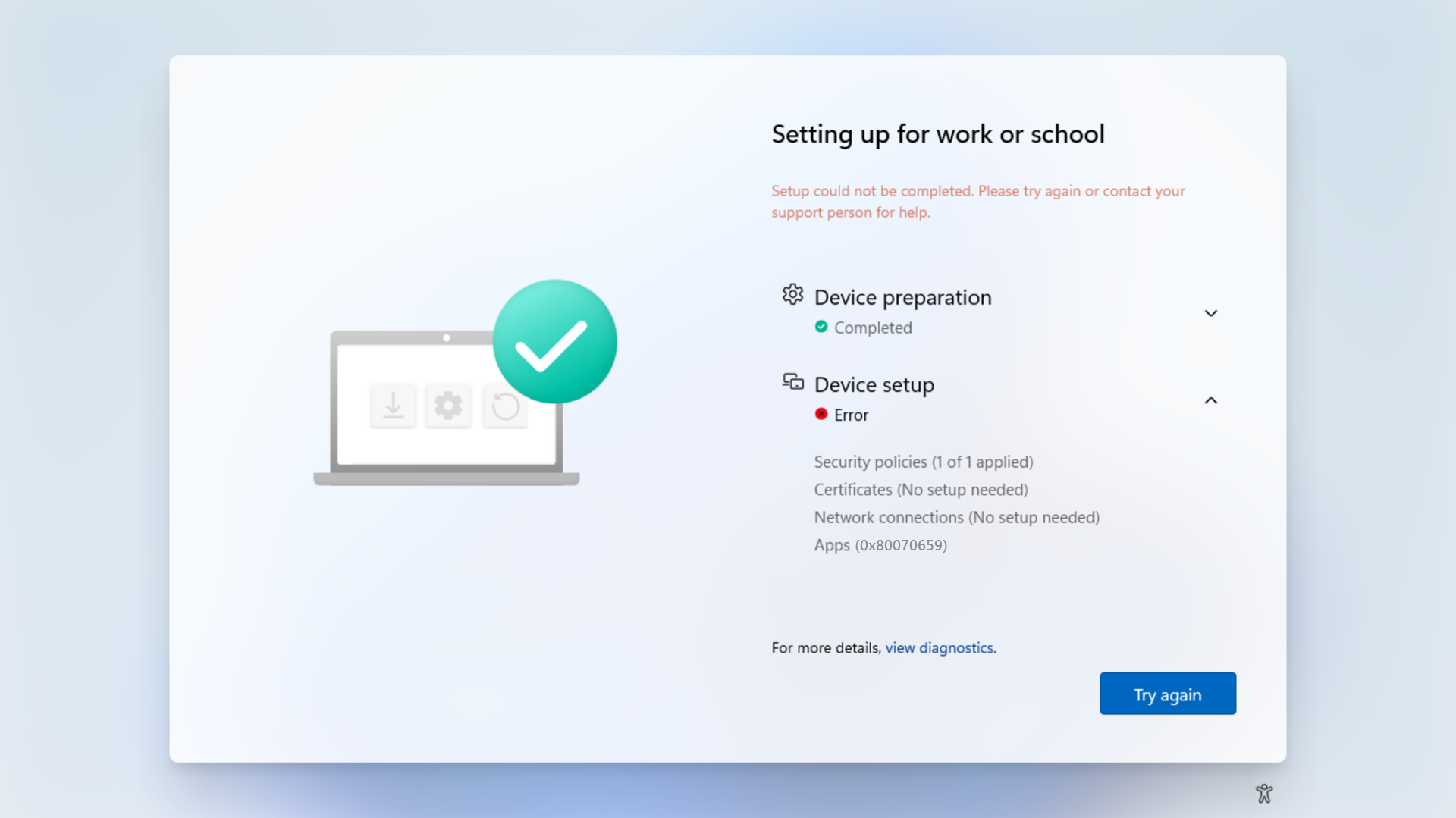
ESP errors mitigation
To ensure that you don't run into installation or enrollment blocks, you can pick one of the following options, in accordance with your internal policies:
- Ensure that all apps are unblocked from installation. Apps must be compatible with the Windows 11 SE managed installer flow, and if they aren't compatible out-of-box, have the corresponding supplemental policy to allow them
- Don't deploy apps that you haven't validated
- Set your Enrollment Status Page configuration to not block device use based on required apps
To learn more about the ESP, see Set up the Enrollment Status Page.
Potential impact to events collected by Log Analytics integrations
Log Analytics is a cloud service that can be used to collect data from AppLocker policy events. Windows 11 SE devices enrolled in an Intune Education tenant will automatically receive an AppLocker policy. The result is an increase in events generated by the AppLocker policy.
If your organization is using Log Analytics, it's recommended to review your Log Analytics setup to:
- Ensure there's an appropriate data collection cap in place to avoid unexpected billing costs
- Turn off the collection of non-error AppLocker events in Log Analytics, except for MSI and Script logs
For more information, see Use Event Viewer with AppLocker