Phase 3: Configure Microsoft Entra Permissions Management monitoring and alerting
This section of the Microsoft Entra Permissions Management operations reference guide describes the checks and actions you should take to implement an effective alerting and reporting strategy.
Implement a reporting system for key stakeholders
Recommended owner: Information Security Architecture
Identify key stakeholders who consume reports
Microsoft Entra Permissions Management generates system reports for visibility and insights into cloud environments. To help define who consumes reports in your organization, note the following recommended audiences:
| Report | Recommended audience |
|---|---|
| Access Key Entitlements and Usage | Information Security Operations, target authorization system technical owners |
| User Entitlements and Usage | IAM, Security Assurance and Audit, target authorization system technical owners |
| Group Entitlements and Usage | IAM, Security Assurance and Audit, target authorization system technical owners |
| Identity Permissions | IAM, Security Assurance and Audit, target authorization system technical owners |
| Permissions Analytics | IAM, Security Assurance and Audit, target authorization system technical owners |
| Role/Policy Details | IAM, Security Assurance and Audit, target authorization system technical owners |
| PCI History | Information Security Operations, Cloud Infrastructure, Security Assurance and Audit |
| All Permissions for Identity | IAM, Security Assurance and Audit, Incident Response, target authorization system technical owners |
For detailed descriptions, see system reports in the Reports Dashboard
Schedule reports for key stakeholders
For the key stakeholders who consume reports, set up a regular delivery cadence: hourly, daily, weekly, biweekly, or monthly. Learn to create, view, and share a custom report.
Define custom audit queries to meet organizational requirements
Use custom audit queries to obtain activity log information the product ingests, review access, and conduct compliance reviews. In addition, use them for forensics. For example, during a security incident, use audit queries to find an attacker’s entry point and trace their path.
Use Permissions Management to create and save custom audit queries that others view in your organization. We recommend you build audit queries that align with the information your organization regularly reviews. Use the following diagrams to get started.
Note
The following diagrams are query examples. The exact structure depends on your query. When creating custom audit queries, select the authorization system type and the authorization system(s) and folder(s) you want to query.
Review access to critical resources
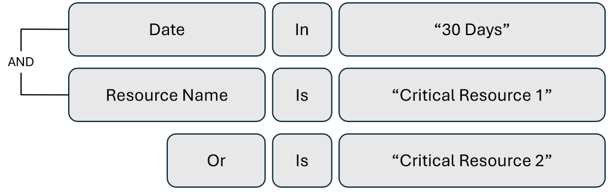
Review administrator and privileged account activity
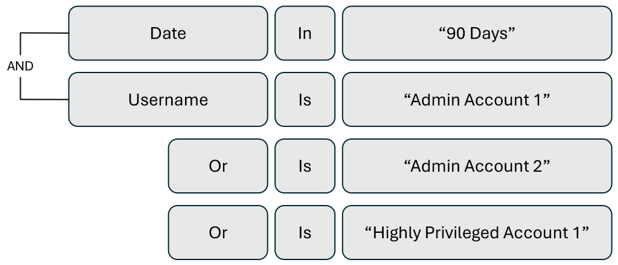
Review high-risk permissions usage

Review authorization failures

Review access key usage
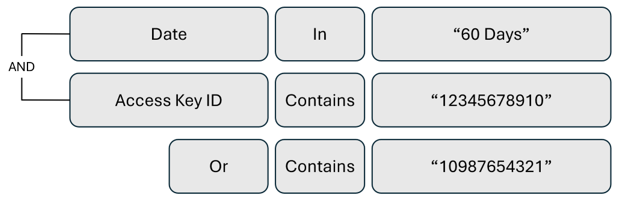
Review Permissions Management remediation activity
Note
To query Microsoft Entra Permissions Management logs, for the authorization system type, select Platform.
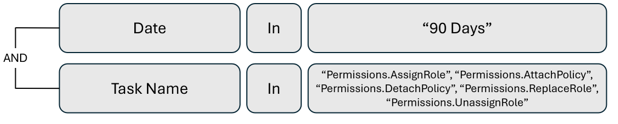
For more information on how to create, view, save, and use custom queries:
- Create a custom query
- Filter and query user activity
- Use queries to see how users access information
Configure alerts for Security Operations investigations
You can configure alerts to continuously monitor your environment. Get notifications for overprivileged accounts, anomalous permissions usage, potential threats, and service disruptions.
Determine the alerts that serve your environment and who receives them. This action provides better visibility into your environment, and enables a more proactive approach to managing identities and their access to resources.
To learn about alert types and usage scenarios, see the Microsoft Entra Permissions Management alerts guide.
Develop alert response strategies and playbooks
Develop manual or automated response strategies and playbooks for your configured alerts.
- Determine who acts on the alert, likely the alert recipient
- Create and provide clear remediation steps
For example, review the following response strategy and playbook for an Inactive User alert.
Example manual response strategy
Remediation: When an Inactive User alert triggers, the alert recipient assigns the user read-only status, and applies the ck_exclude_from_reports tags to the user.
In the manual response, use Microsoft Entra Permissions Management remediation tools and clarify that recipients of the Inactive User alerts perform remediation. The recipients use Permissions Management to assign read-only status to the user. This action revokes the user’s permissions and assigns them read only status with the click of a button.
A recipient applies the ck_exclude_from_reports tags to the user. This tag removes the user from the Permissions Analytics Report, so it’s not called out as an inactive user.
Example automated response strategy
Remediation: When an Inactive User alert triggers, the user is deleted by Microsoft Power Automate, a tool to create flows for cloud, desktop, and business processes.
Use Power Automate for automated responses to Inactive User alerts. For instance, create a flow that deletes inactive users after an email from Permissions Management indicates inactivity.
Next steps
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for