Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Monitoring the traffic for Global Secure Access is an important activity for ensuring your tenant is configured correctly and that your users are getting the best experience possible. The Global Secure Access traffic logs (preview) provide insight into who is accessing what resources, where they're accessing them from, and what action took place.
This article describes how to use the traffic logs for Global Secure Access.
Prerequisites
- A Global Secure Access Administrator role in Microsoft Entra ID.
- A Global Secure Access Log Reader role in Microsoft Entra ID.
- The product requires licensing. For details, see the licensing section of What is Global Secure Access. If needed, you can purchase licenses or get trial licenses.
How the traffic logs work
The Global Secure Access logs provide details of your network traffic. To better understand those details and how you can analyze those details to monitor your environment, it's helpful to look at the three levels of the logs and their relationship to each other.
A user accessing a website represents one session, and within that session there may be multiple connections, and within that connection there may be multiple transactions.
- Session: A session is identified by the first URL a user accesses. That session could then open many connections, for example a news site that contains multiple ads from several different sites.
- Connection: A connection includes the source and destination IP, source and destination port, and fully qualified domain name (FQDN). The connection components comprise the 5 tuple.
- Transaction: A transaction is a unique request and response pair.
Within each log instance, you can see the connection ID and transaction ID in the details. By using the filters, you can look at all connections and transactions for a single session.
How to view the traffic logs
- Sign in to the Microsoft Entra admin center as at least a Reports Reader.
- Global Secure Access > Monitor > Traffic logs.
The top of the page displays a summary of all transactions as well as a breakdown for each type of traffic. Select the Microsoft 365 or Private access buttons to filter the logs to each traffic type.
Note
At this time, Session ID information is not available in the log details.
View the log details
Select any log from the list to view the details. These details provide valuable information that can be used to filter the logs for specific details or to troubleshoot a scenario. The details can be added as a column and used to filter the logs.

Filter and column options
The traffic logs can provide many details, so to start only some columns are visible. Enable and disable the columns based on the analysis or troubleshooting tasks you're performing, as the logs could be difficult to view with too many columns selected. The column and filter options align with each item in the Activity details.
Select Columns from the top of the page to change the columns that are displayed.
To filter the traffic logs to a specific detail, select the Add filter button and then enter the detail you want to filter by.
For example if you want to look at all the logs from a specific connection:
Select the log detail and copy the
connectionIdfrom the Activity details.Select Add filter and choose Connection ID.
In the field that appears, paste the
connectionIdand select Apply.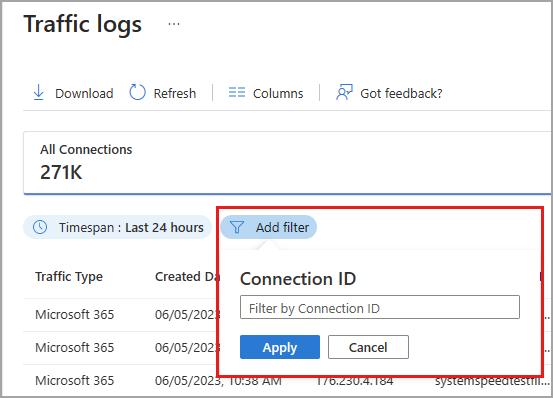
Connection logs
Connection logs provide a summary of all associated transactions, including the total transaction count and blocked transactions, allowing for quick identification of any blocked activity.
A connection represents multiple transactions occurring in the last 24 hours and sharing the same flow correlation ID. While the transaction logs provide detailed information about individual transactions, connection logs offer a higher-level overview by aggregating multiple transactions. Connections are logged in real time with Active/Closed status, providing admins with near real-time traffic visibility.
We are currently previewing a new tab in the Traffic logs blade for you to view Connections:

Transactions associated with each Connection are viewed by selecting the Transactions tab.
Troubleshooting scenarios
The following details may be helpful for troubleshooting and analysis:
- If you're interested in the size of the traffic being sent and received, enable the Sent Bytes and Received Bytes columns. Select the column header to sort the logs by the size of the logs.
- If you are reviewing the network activity for a risky user, you can filter the results by user principal name and then review the sites they're accessing.
- To look for traffic to the types of websites that you want to block or allow, enable the Web category column.
The log details provide valuable information about your network traffic. Not all details are defined in the list below, but the following details are useful for troubleshooting and analysis:
- Transaction ID: Unique identifier representing the request/response pair.
- Connection ID: Unique identifier representing the connection that initiated the log.
- Device category: Device type where the transaction initiated from. Either client or remote network.
- Action: The action taken on the network session. Either Allowed or Denied.
Configure diagnostic settings to export logs
You can export the Global Secure Access traffic logs (preview) to an endpoint for further analysis and alerting. This integration is configured in Microsoft Entra diagnostic settings.
Sign in to the Microsoft Entra admin center as at least a Security Administrator.
Browse to Entra ID > Monitoring & health > Diagnostic settings.
Select Add Diagnostic setting.
Give your diagnostic setting a name.
Select
NetworkAccessTrafficLogs.Select the Destination details for where you'd like to send the logs. Choose any or all of the following destinations. Additional fields appear, depending on your selection.
- Send to Log Analytics workspace: Select the appropriate details from the menus that appear.
- Archive to a storage account: Provide the number of days you'd like to retain the data in the Retention days boxes that appear next to the log categories. Select the appropriate details from the menus that appear.
- Stream to an event hub: Select the appropriate details from the menus that appear.
- Send to partner solution: Select the appropriate details from the menus that appear.