Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Provide single sign-on (SSO) to on-premises applications secured with Security Assertion Markup Language (SAML) authentication. Provide remote access to SAML based SSO applications through application proxy. With SAML single sign-on, Microsoft Entra authenticates to the application using the user's Microsoft Entra account. Microsoft Entra ID communicates the sign-on information to the application through a connection protocol. You can also map users to specific application roles based on rules you define in your SAML claims. By enabling application proxy in addition to SAML SSO, your users have external access to the application and a seamless SSO experience.
The applications must be able to consume SAML tokens issued by Microsoft Entra ID. This configuration doesn't apply to applications using an on-premises identity provider. For these scenarios, we recommend reviewing Resources for migrating applications to Microsoft Entra ID.
SAML SSO with application proxy also works with the SAML token encryption feature. For more info, see Configure Microsoft Entra SAML token encryption.
The protocol diagrams describe the single sign-on sequence for both a service provider-initiated (SP-initiated) flow and an identity provider-initiated (IdP-initiated) flow. Application proxy works with SAML SSO by caching the SAML request and response to and from the on-premises application.
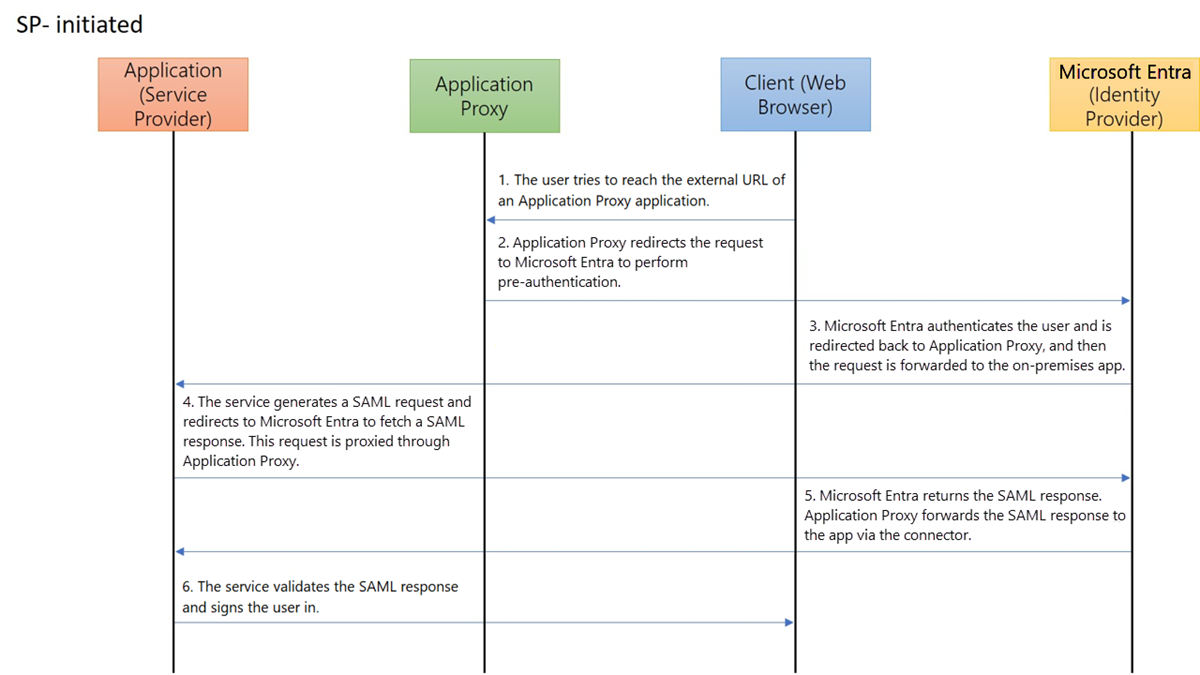
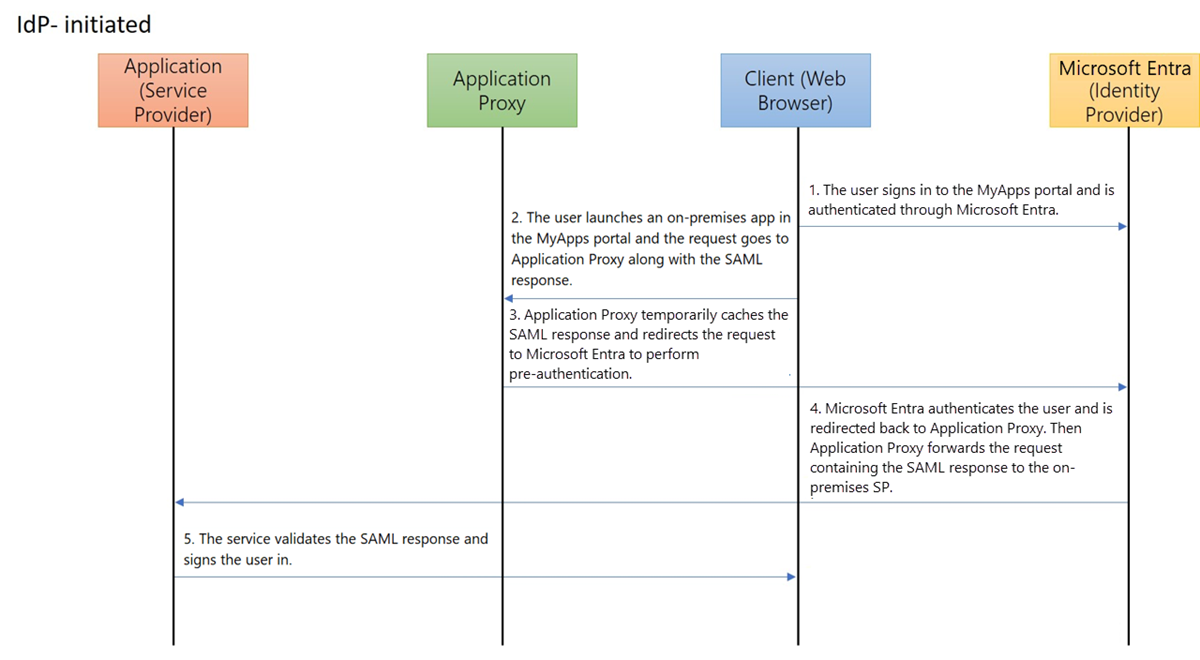
Create an application and set up SAML SSO
In the Microsoft Entra admin center, select Microsoft Entra ID > Enterprise applications and select New application.
Enter the display name for your new application. Select Integrate any other application you don't find in the gallery, then select Create.
On the app's Overview page, select Single sign-on.
Select SAML as the single sign-on method.
First set up SAML SSO to work while on the corporate network, see the basic SAML configuration section of Configure SAML-based single sign-on to configure SAML-based authentication for the application.
Add at least one user to the application and make sure the test account has access to the application. While connected to the corporate network, use the test account to see if you have single sign-on to the application.
Note
After you set up application proxy, you'll come back and update the SAML Reply URL.
Publish the on-premises application with application proxy
Before you provide SSO for on-premises applications, enable application proxy and install a connector. Learn more about how to prepare your on-premises environment, install and register a connector, and test the connector. Once you have the connector set up, follow these steps to publish your new application with application proxy.
With the application still open in the Microsoft Entra admin center, select application proxy. Provide the Internal URL for the application. If you're using a custom domain, you also need to upload the Transport Layer Security (TLS) certificate for your application.
Note
As a best practice, use custom domains whenever possible for an optimized user experience. Learn more about Working with custom domains in Microsoft Entra application proxy.
Select Microsoft Entra ID as the Pre Authentication method for your application.
Copy the External URL for the application. You need this URL to complete the SAML configuration.
Using the test account, try to open the application with the External URL to validate that application proxy is set up correctly. If there are issues, see Troubleshoot application proxy problems and error messages.
Update the SAML configuration
With the application still open in the Microsoft Entra admin center, select Single sign-on.
In the Set up Single Sign-On with SAML page, go to the Basic SAML Configuration heading, and select its Edit icon (a pencil). Make sure the External URL you configured in application proxy is populated in the Identifier, Reply URL, and Logout URL fields. These URLs are required for application proxy to work correctly.
Edit the Reply URL configured earlier so that its domain reachable on the internet via application proxy. For example, if your External URL is
https://contosotravel-f128.msappproxy.netand the original Reply URL washttps://contosotravel.com/acs, you need to update the original Reply URL tohttps://contosotravel-f128.msappproxy.net/acs.Select the checkbox next to the updated Reply URL to mark it as the default.
After marking the required Reply URL as default, you can also delete the previously configured Reply URL that used the internal URL.
For an SP-initiated flow, make sure the back-end application specifies the correct Reply URL or Assertion Consumer Service URL for receiving the authentication token.
Note
If the back-end application expects the Reply URL to be the Internal URL, you need to either use custom domains to have matching internal and external URLs or install the My Apps secure sign-in extension on users' devices. This extension will automatically redirect to the appropriate application proxy Service. To install the extension, see My Apps secure sign-in extension.
Test your app
Your app is up and running. To test the app:
- Open a browser and navigate to the External URL that you created when you published the app.
- Sign in with the test account that you assigned to the app. You should be able to load the application and have SSO into the application.