Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Managed identities for Azure resources provide Azure services with an automatically managed identity in Microsoft Entra ID. You can use this identity to authenticate to any service that supports Microsoft Entra authentication without having credentials in your code.
In this article, you'll learn how to view the service principal of a managed identity.
Note
Service principals are enterprise applications.
Prerequisites
- If you're unfamiliar with managed identities for Azure resources, see What are managed identities for Azure resources?.
- If you don't already have an Azure account, sign up for a free account before continuing.
- Enable system assigned identity on a virtual machine or application.
View the service principal for a managed identity using the Azure portal
Sign in to the Microsoft Entra admin center.
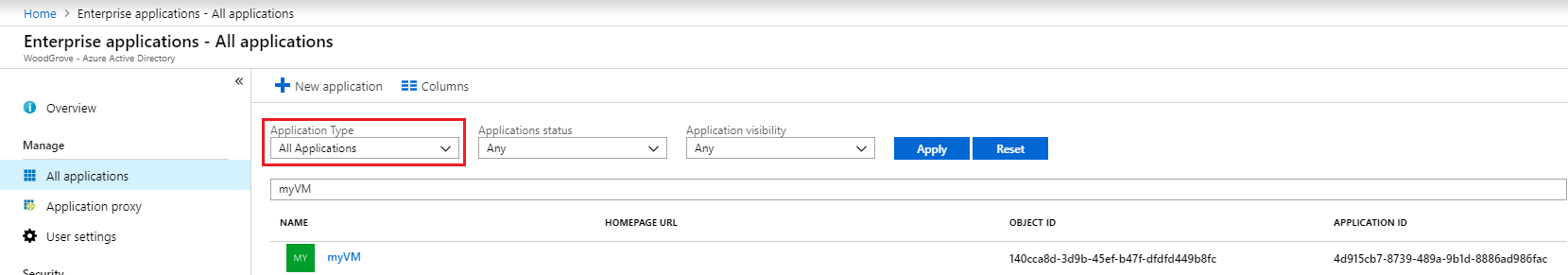
Browse to Entra ID > Enterprise apps.
In the Manage section select All applications.
Set a filter for "Application type == Managed Identities" and select Apply.
(Optional) In the search filter box, enter the name of the Azure resource that has system managed identities enabled or the name of the user assigned managed identity.
Next steps
For more information about managed identities, see Managed identities for Azure resources.
View the service principal of a managed identity using Azure CLI
Use the Bash environment in Azure Cloud Shell. For more information, see Get started with Azure Cloud Shell.
If you prefer to run CLI reference commands locally, install the Azure CLI. If you're running on Windows or macOS, consider running Azure CLI in a Docker container. For more information, see How to run the Azure CLI in a Docker container.
If you're using a local installation, sign in to the Azure CLI by using the az login command. To finish the authentication process, follow the steps displayed in your terminal. For other sign-in options, see Authenticate to Azure using Azure CLI.
When you're prompted, install the Azure CLI extension on first use. For more information about extensions, see Use and manage extensions with the Azure CLI.
Run az version to find the version and dependent libraries that are installed. To upgrade to the latest version, run az upgrade.
The following command demonstrates how to view the service principal of a virtual machine (VM) or application with managed identity enabled. Replace <Azure resource name> with your own values.
az ad sp list --display-name <Azure resource name>
Next steps
For more information on managing Microsoft Entra service principals, see Azure CLI ad sp.
View the service principal for a managed identity using PowerShell
To run the scripts for this example, you have two options:
- Use the Azure Cloud Shell, which you can open using the Try It button on the top right corner of code blocks.
- Run scripts locally by installing the latest version of Azure PowerShell, then sign in to Azure using
Connect-AzAccount.
The following command demonstrates how to view the service principal of a virtual machine (VM) or application with system assigned identity enabled. Replace <Azure resource name> with your own values.
Get-AzADServicePrincipal -DisplayName <Azure resource name>
Next steps
For more information on viewing Microsoft Entra service principals using PowerShell, see Get-AzADServicePrincipal.