Configure Verified ID by AU10TIX as your Identity Verification Partner
In this article, we cover the steps needed to integrate Microsoft Entra Verified ID with AU10TIX. AU10TIX is an automated solution for the verification of ID documents + biometrics. AU10TIX supports the verification of documents in over 190 countries/regions reading documents in their regional languages.
To learn more about AU10TIX and its complete set of solutions, visit https://www.au10tix.com/.
Prerequisites
Before you can continue with the steps below you need to meet the following requirements:
- A tenant configured for Microsoft Entra Verified ID service.
- If you don't have an existing tenant, you can create an Azure account for free.
- You need to have completed the onboarding process with Au10tix.
- To create a AU10TIX account, submit the form on this page.
Important
Before you proceed, you must have received the URL from Au10Tix for users to be issued Verified IDs. If you have not yet received it, follow up with Au10Tix before you attempt following the steps documented below.
Scenario description
When onboarding users you can remove the need for error prone manual onboarding steps by using Verified ID with A10TIX account onboarding. Verified IDs can be used to digitally onboard employees, students, citizens, or others to securely access resources and services. For example, rather than an employee needing to go to a central office to activate an employee badge, they can use a Verified ID to verify their identity to activate a badge that is delivered to them remotely. Rather than a citizen receiving a code they must redeem to access governmental services, they can use a Verified ID to prove their identity and gain access. Learn more about account onboarding.
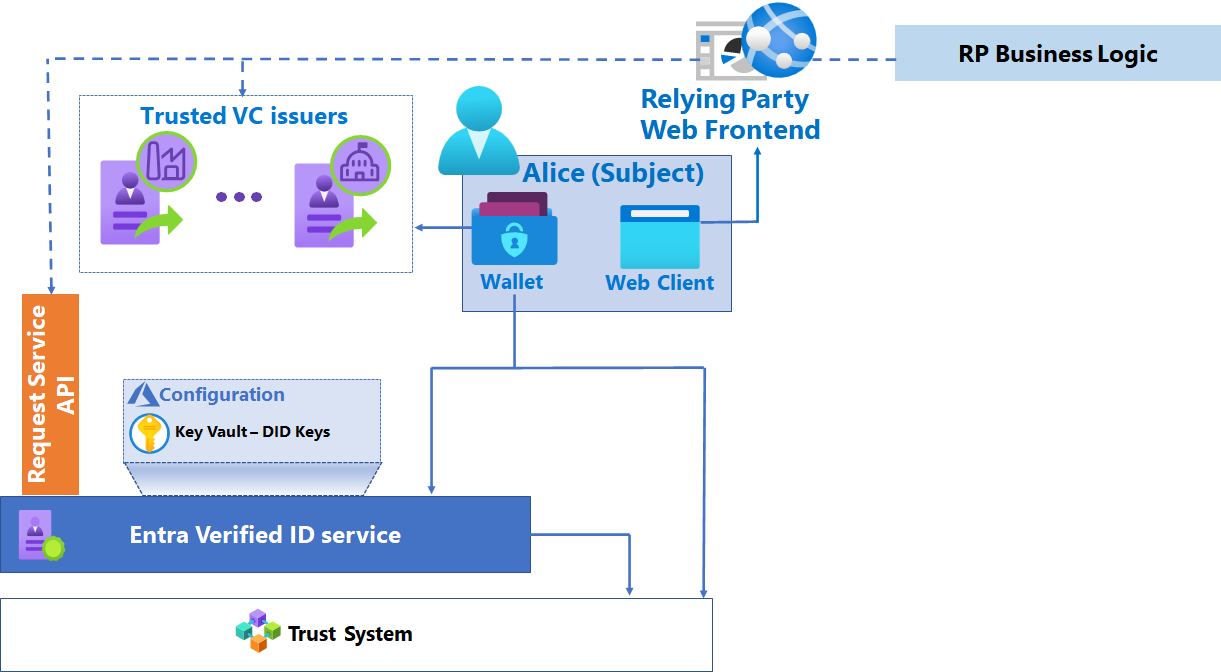
Configure your Application to use AU10TIX Verified ID
For incorporating identity verification into your Apps, using AU10TIX “Government Issued ID -Global” Verified ID follow these steps:
Part 1
As a developer you can share these steps with your tenant administrator to obtain the verification request URL, and body for your application or website to request Verified IDs from your users.
Go to Microsoft Entra admin center -> Verified ID.
Note
Make sure this is the tenant you set up for Verified ID per the pre-requisites.
Go to QuickStart > Verification Request > Start
Choose Select Issuer.
Look for AU10TIX in the Search/select issuers drop-down.
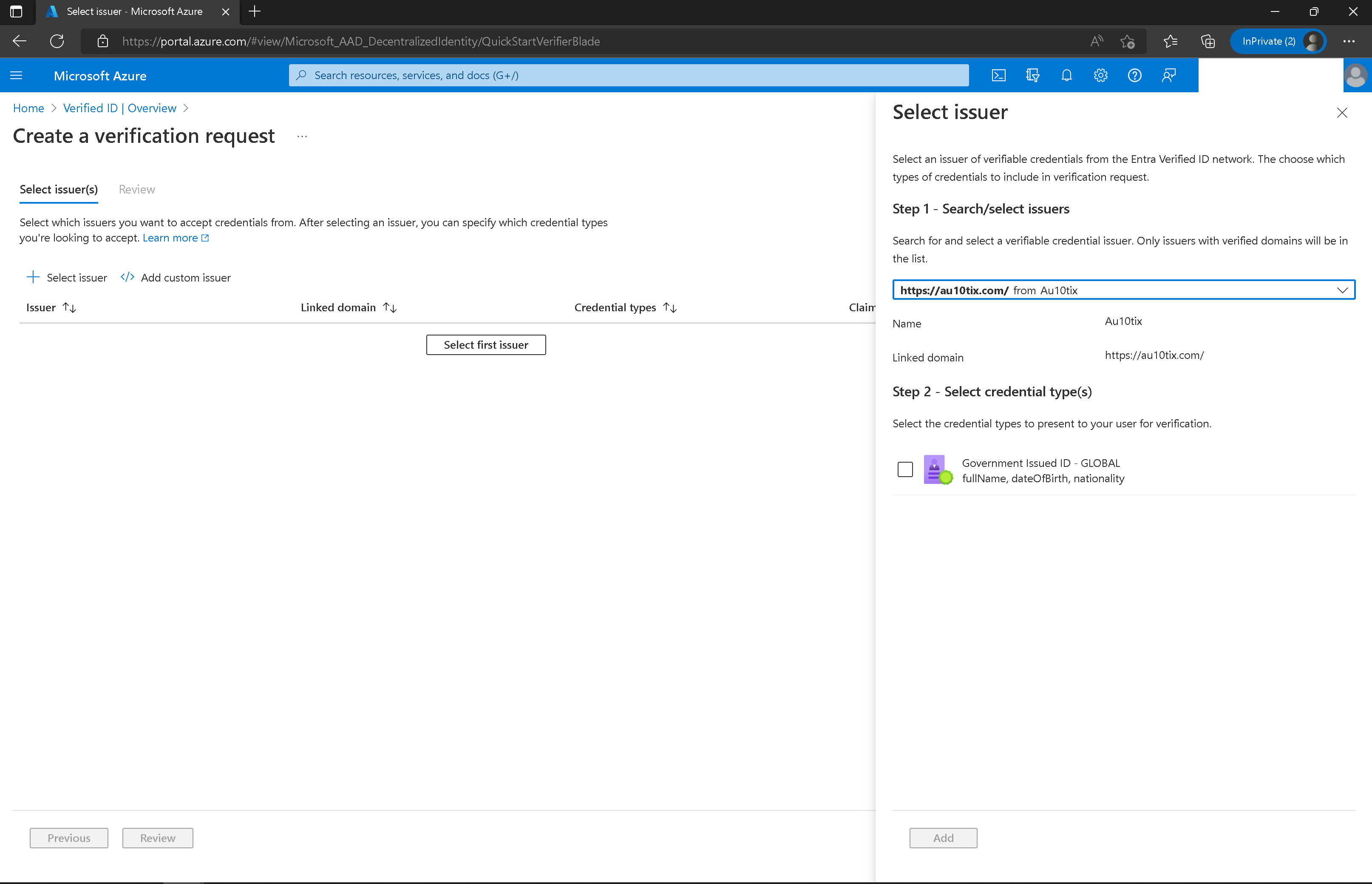
Check the Government Issued ID – Global or other credential type.
Select Add and then select Review.
Download the request body and Copy/paste POST API request URL.
Part 2
As a developer you now have the request URL and body from your tenant admin, follow these steps to update your application or website:
- Add the request URL and body to your application or website to request Verified IDs from your users.
Note
If you are using one of the sample apps, you'll need to replace the contents of the
presentation_request_config.jsonwith the request body obtained in Part 1. The sample code overwrites thetrustedIssuersvalues withIssuerAuthorityvalue fromappsettings.json. Copy thetrustedIssuersvalue from the payload toIssuerAuthorityinappsettings.jsonfile. - Be sure to replace the values for the "url", "state", and "api-key" with your respective values.
- Grant permissions to your app to obtain access token for the Verified ID service request service principal.
Test the user flow
User flow is specific to your application or website. However if you are using one of the sample apps follow the steps outlined as part of the sample app's documentation.
Next steps
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for