Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Properly configured inbound connectors are a trusted source of incoming mail to Microsoft 365 or Office 365. But in complex routing scenarios where email for your Microsoft 365 or Office 365 domain is routed somewhere else first, the source of the inbound connector is typically not the true indicator of where the message came from. Complex routing scenarios include:
- Third-party cloud filtering services
- Managed filtering appliances
- Hybrid environments (for example, with on-premises Exchange)
Mail routing in complex scenarios looks like this:
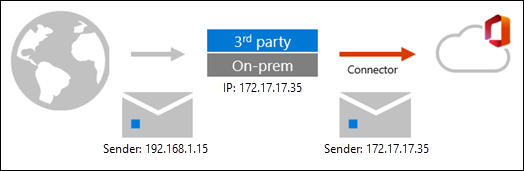
As you can see, the message adopts the source IP of the service, appliance, or on-premises Exchange organization that sits in front of Microsoft 365. The message arrives in Microsoft 365 with a different source IP address. This behavior isn't a limitation of Microsoft 365; it's simply how SMTP works.
In these scenarios, you can still get the most out of Exchange Online Protection (EOP) and Microsoft Defender for Office 365 by using Enhanced Filtering for Connectors (also known as skip listing).
After you enable Enhanced Filtering for Connectors, mail routing in complex routing scenarios looks like this:
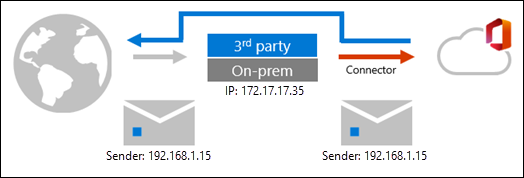
As you can see, Enhanced Filtering for connectors allows IP address and sender information to be preserved.
In these routing scenarios, an ARC seal is typically used to maintain the source information and message integrity using DKIM. However, DKIM frequently fails because many services that modify the message don't support ARC. To help in these situations, Enhanced Filtering for Connectors not only preserves the IP address from the previous hop but also intelligently recovers from DKIM signature failures. This behavior helps the messages pass authentication through the spoof intelligence filters.
Enhanced Filtering for Connectors has the following benefits:
- Improved accuracy for the Microsoft filtering stack and machine learning models, which include:
- Reduced false positives in DMARC from content modification and lack of an ARC seal.
- Heuristic clustering
- Anti-spoofing
- Anti-phishing
- Better post-breach capabilities in Automated investigation and response (AIR)
- Able to use explicit email authentication (SPF, DKIM, and DMARC) to verify the reputation of the sending domain for impersonation and spoof detection. For more information about explicit and implicit email authentication, see Email authentication in Microsoft 365.
For more information, see the What happens when you enable Enhanced Filtering for Connectors? section later in this article.
Use the procedures in this article to enable Enhanced Filtering for Connectors on individual connectors. For more information about connectors in Exchange Online, see Configure mail flow using connectors.
Note
- Enhanced Filtering for Connectors is intended for scenarios where the MX record for the domain doesn't point to Microsoft 365. For example:
- Hybrid environments where internet mail is routed through the on-premises Exchange environment before being delivered to Microsoft 365. Mail sent to on-premises recipients isn't scanned by Microsoft 365.
- Internet mail is routed through a non-Microsoft service or device before delivery to Microsoft 365 recipients as described in MX record points to third-party spam filtering.
- Enhanced Filtering for Connectors isn't intended for non-Microsoft services or devices that scan mail after Microsoft 365. Once Microsoft 365 scans a message, be careful not to break the chain of trust by routing mail through any non-Exchange server that isn't part of your cloud or on-premises organization. When the message eventually arrives at the destination mailbox, the headers from the first scanning verdict might no longer be accurate.
- In non-linear inbound routing scenarios in Centralized Mail Transport, adding on-premises hybrid servers to Enhanced Filtering for Connectors isn't supported. This configuration can cause Microsoft 365 to scan mail that returns from the on-premises environment, which adds a compauth header value to messages, and might result in the message being identified as spam. In linear inbound routing scenarios in Centralized Mail Transport, adding on-premises hybrid servers to Enhanced Filtering for Connectors is supported.
- Examples of non-linear inbound routing (adding on-premises hybrid servers to Enhanced Filtering for Connectors isn't supported):
- Internet > Microsoft 365 > On-premises > Microsoft 365
- Internet > non-Microsoft service > Microsoft 365 > On-premises > Microsoft 365
- Examples of linear inbound routing (adding on-premises hybrid servers to Enhanced Filtering for Connectors is supported):
- Internet > On-premises > Microsoft 365
- Internet > non-Microsoft service > On-premises > Microsoft 365
- Examples of non-linear inbound routing (adding on-premises hybrid servers to Enhanced Filtering for Connectors isn't supported):
Configure Enhanced Filtering for Connectors
Note
Currently, IPv6 addresses are supported only in PowerShell. To use PowerShell to configure Enhanced Filtering for Connectors, see the Use Exchange Online PowerShell or Exchange Online Protection PowerShell to configure Enhanced Filtering for Connectors on an inbound connector section later in this article.
What do you need to know before you begin?
Include all of the trusted IP addresses that are associated with the on-premises hosts or the third-party filters that send email into your Microsoft 365 or Office 365 organization, including any intermediate hops with public IP addresses. To get these IP addresses, consult the documentation or support that's provided with the service.
If you have mail flow rules (also known as transport rules) that set the SCL to -1 for messages that flow through this connector, you must disable those mail flow rules after you enable Enhanced Filtering for Connectors.
To open the Microsoft Defender portal, go to https://security.microsoft.com. To go directly to the Enhanced Filtering for Connectors page, use https://security.microsoft.com/skiplisting.
To connect to Exchange Online PowerShell, see Connect to Exchange Online PowerShell. To connect to Exchange Online Protection PowerShell, see Connect to Exchange Online Protection PowerShell.
To configure Enhanced Filtering for Connectors, you need to be a member of one of the following role groups:
- Organization Management or Security Administrator in the Microsoft Defender portal.
- Organization Management in Exchange Online.
Use the Microsoft Defender portal to configure Enhanced Filtering for Connectors on an inbound connector
In the Microsoft Defender portal, go to Email & Collaboration > Policies & Rules > Threat policies page > Rules section > Enhanced filtering.
On the Enhanced Filtering for Connectors page, select the inbound connector that you want to configure by clicking on the name.
In the connector details flyout that appears, configure the following settings:
IP addresses to skip: Choose one of the following values:
Disable Enhanced Filtering for Connectors: Turn off Enhanced Filtering for Connectors on the connector.
Automatically detect and skip the last IP address: We recommend this value if you have to skip only the last message source.
Skip these IP addresses that are associated with the connector: Select this value to configure a list of IP addresses to skip.
Important
- Entering the IP addresses of Microsoft 365 or Office 365 is not supported. Do not use this feature to compensate for issues introduced by unsupported email routing paths. Use caution and limit the IP ranges to only the email systems that will handle your own organization's messages prior to Microsoft 365 or Office 365.
- Entering any loopback address (127.0.0.0/8) or private IP address defined by RFC 1918 (10.0.0.0/8, 172.16.0.0/12, and 192.168.0.0/16) is not supported. Enhanced Filtering automatically detects and skips loopback addresses and private IP addresses. If the previous hop is an email server that's behind a network address translation (NAT) device that assigns private IP addresses, we recommend that you configure NAT to assign a public IP address to the email server.
- Currently, IPv6 addresses are supported only in PowerShell.
If you selected Automatically detect and skip the last IP address or Skip these IP addresses that are associated with the connector, the Apply to these users section appears:
Apply to entire organization: We recommend this value after you test the feature on a few recipients first.
Apply to a small set of users: Select this value to configure a list of recipient email addresses that Enhanced Filtering for Connectors applies to. We recommend this value as an initial test of the feature.
Note
- This value is only effective on the actual email addresses that you specify. For example, if a user has five email addresses associated with their mailbox (also known as proxy addresses), you need to specify all five of their email addresses here. Otherwise, messages that are sent to the four other email addresses will go through normal filtering.
- In hybrid environments where inbound mail flows through on-premises Exchange, you must specify the targetAddress of the MailUser object. For example,
michelle@contoso.mail.onmicrosoft.com. - This value is only effective on messages where all recipients are specified here. If a message contains any recipients that aren't specified here, normal filtering is applied to all recipients of the message.
Apply to entire organization: We recommend this value after you test the feature on a few recipients first.
When you're finished, select Save.
Use Exchange Online PowerShell or Exchange Online Protection PowerShell to configure Enhanced Filtering for Connectors on an inbound connector
To configure Enhanced Filtering for Connectors on an inbound connector, use the following syntax:
Set-InboundConnector -Identity <ConnectorIdentity> [-EFSkipLastIP <$true | $false>] [-EFSkipIPs <IPAddresses>] [-EFUsers "emailaddress1","emailaddress2",..."emailaddressN"]
EFSkipLastIP: Valid values are:
$true: Only the last message source is skipped.$false: Skip the IP addresses specified by the EFSkipIPs parameter. If no IP addresses are specified there, Enhanced Filtering for Connectors is disabled on the inbound connector. The default value is$false.
EFSkipIPs: The specific IPv4 or IPv6 addresses to skip when the EFSkipLastIP parameter value is
$false. Valid values are:- A single IP address: For example,
192.168.1.1. - An IP address range: For example,
192.168.1.0-192.168.1.31. - Classless Inter-Domain Routing (CIDR) IP: For example,
192.168.1.0/25.
See the Skip these IP addresses that are associated with the connector description in the previous section for limitations on IP addresses.
- A single IP address: For example,
EFUsers: The comma-separated email address of recipient email addresses that you want to apply Enhanced Filtering for Connectors to. See the Apply to a small set of users description in the previous section for limitations on individual recipients. The default value is blank (
$null), which means Enhanced Filtering for Connectors is applied to all recipients.
This example configures the inbound connector named From Anti-Spam Service with the following settings:
- Enhanced Filtering for Connectors is enabled on the connector, and the IP address of the last message source is skipped.
- Enhanced Filtering for Connectors only applies to the recipient email addresses
michelle@contoso.com,laura@contoso.com, andjulia@contoso.com.
Set-InboundConnector -Identity "From Anti-Spam Service" -EFSkipLastIP $true -EFUsers "michelle@contoso.com","laura@contoso.com","julia@contoso.com"
To disable Enhanced Filtering for Connectors, use the value $false for the EFSkipLastIP parameter.
For detailed syntax and parameter information, see Set-InboundConnector.
What happens when you enable Enhanced Filtering for Connectors?
The following table describes what connections look like before and after you enable Enhanced Filtering for Connectors:
| Feature | Before Enhanced Filtering is enabled | After Enhanced Filtering is enabled |
|---|---|---|
| Email domain authentication | Implicit using anti-spoof protection technology. | Explicit, based on the source domain's SPF, DKIM, and DMARC records in DNS. |
| X-MS-Exchange-ExternalOriginalInternetSender | Not available | This header is stamped if skip listing was successful, enabled on the connector, and recipient match happens. The value of this field contains information about the true source address. |
| X-MS-Exchange-SkipListedInternetSender | Not available | This header is stamped if skip listing was enabled on the connector, irrespective of recipient matches. The value of this field contains information about the true source address. This header is used primarily for reporting purposes and to help understand WhatIf scenarios. |
You can view the improvements in filtering and reporting by using the Threat protection status report in the Microsoft Defender portal. For more information, see Threat protection status report.
See also
Mail flow best practices for Exchange Online, Microsoft 365, and Office 365 (overview)