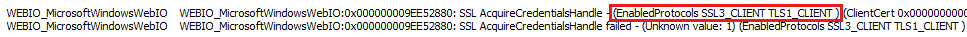Hybrid Configuration wizard doesn't connect to Office 365
Symptoms
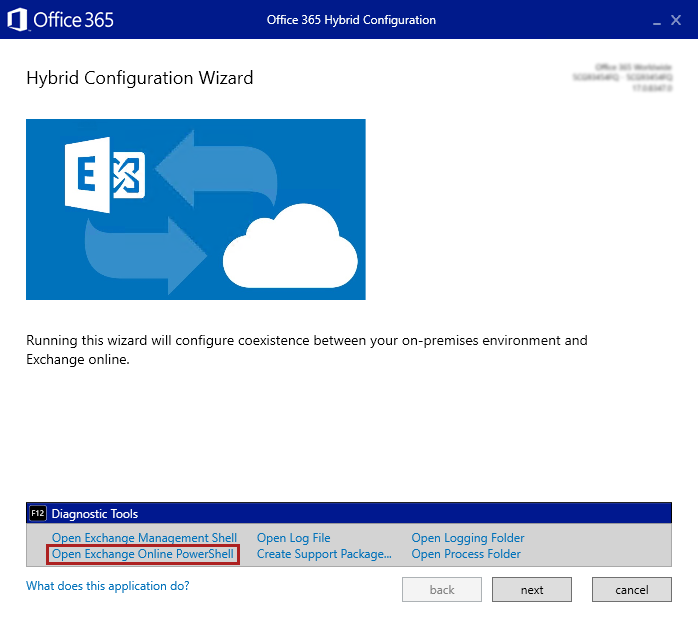
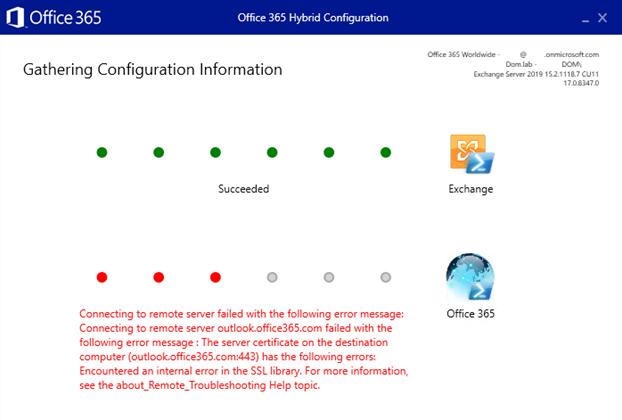
When you run the Hybrid Configuration wizard (HCW) and try to connect to the Office 365 endpoint, you receive the following error message:
Connecting to remote server failed with the following error message: Connecting to remote server outlook.office365.com failed with the following error message: The server certificate on the destination computer (outlook.office365.com:443) has the following errors: Encountered an internal error in the SSL library. For more information, see the about_Remote_Troubleshooting Help topic.
The following screenshot shows the error message in the HCW.
Cause
Office 365 supports only TLS 1.2 connections. Therefore, the Windows system that runs HCW must have TLS 1.2 enabled in the WinHTTP component and at the operating system (OS) level. The following table shows TLS 1.2 support in different Windows systems.
| Windows OS | TLS 1.2 in OS | TLS 1.2 in WinHTTP |
|---|---|---|
| Windows Server 2008 R2, Windows 7 | Disabled by default | Disabled by default |
| Windows Server 2012 | Enabled by default | Disabled by default |
| Windows Server 2012 R2, Windows 8.1, and later | Enabled by default | Enabled by default |
Resolution
For Windows Server 2012 R2, Windows 8.1, and later systems, check whether a custom policy has disabled TLS 1.2 in the WinHTTP component or at the OS level.
For earlier Windows systems, refer to the preceding table to determine whether you have to enable TLS 1.2 at the OS level or only in the WinHTTP component.
To enable TLS 1.2 in the WinHTTP component, follow these steps:
For Windows Server 2012, Windows Server 2008 R2, and Windows 7, make sure that update 3140245 is installed.
Add a registry key to enable TLS 1.2 in the WinHTTP component:
Important
This section, method, or task contains steps that tell you how to modify the registry. However, serious problems might occur if you modify the registry incorrectly. Therefore, make sure that you follow these steps carefully. For protection, back up the registry before you modify it so that you can restore it if a problem occurs. For more information about how to back up and restore the registry, see How to back up and restore the registry in Windows.
Run regedit.
Navigate to
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp.Add a DWORD entry that's named
DefaultSecureProtocols. To enable TLS 1.2, set the DWORD value to0x00000800(hexadecimal) or2048(decimal). Or, to enable TLS 1.2, TLS 1.1, and TLS 1.0, set the DWORD value to0x00000A80(hexadecimal) or2688(decimal).On x64-based computers, also add the
DefaultSecureProtocolsentry (use the same value forDefaultSecureProtocolsas in the previous step) to theWow6432Nodepath:HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp.
To enable TLS 1.2 at the OS level, follow the procedures that are described in Enabling TLS 1.2.
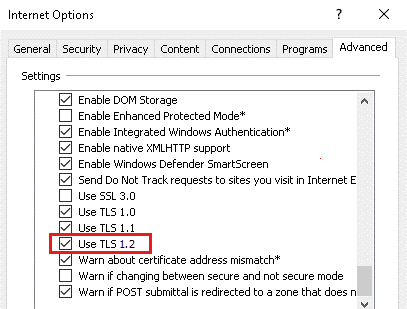
Additionally, run inetcpl.cpl to make sure that TLS 1.2 is enabled on the Advanced tab of Internet Options, as shown in the following screenshot.
More information
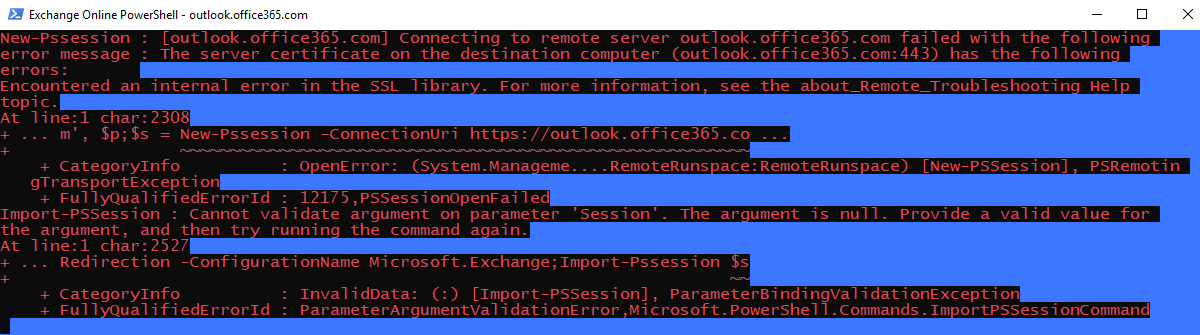
The HCW returns an error message if the New-PSSession cmdlet can't connect to the outlook.office365.com endpoint. The New-PSSession cmdlet uses WinHTTP to make the connection. The error occurs if TLS 1.2 isn't enabled in the WinHTTP component. You can reproduce the error by using the HCW Diagnostic Tools. In HCW, press F12 to open the Diagnostic Tools pane, and then select the Open Exchange Online PowerShell option.
You receive the following error message.
If the WinHTTP component has only TLS 1.0 or TLS 1.1 enabled, New-PSSession won't connect to the Office 365 endpoint or any other endpoint that has only TLS 1.2 enabled. You can use netsh to determine the TLS version that's used by WinHTTP:
Open an elevated Command Prompt window.
Enable WinHTTP logging by running
netsh winhttp set tracing level=verbose format=hex output=file max-trace-file-size=512000 state=enabled.Start a trace session by running
netsh trace start scenario=InternetClient.Open HCW, and try to connect to the Office 365 endpoint.
Stop the trace session by running
netsh trace stop. By default, the trace process saves the trace file to %LOCALAPPDATA%\Temp\NetTraces\NetTrace.etl.Use NetworkMonitor to open the trace file, and then filter on
description.contains("EnabledProtocols")to view the enabled protocols, as follows.