Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Use third-party certification authorities (CA) with Intune. Third-party CAs can provision mobile devices with new or renewed certificates by using the Simple Certificate Enrollment Protocol (SCEP), and can support Windows, iOS/iPadOS, Android, and macOS devices.
There are two parts to using this feature: open-source API, and the Intune administrator tasks.
Part 1 - Use an open-source API
Microsoft created an API to integrate with Intune. Through the API you can validate certificates, send success or failure notifications, and use SSL, specifically SSL socket factory, to communicate with Intune.
The API is available on the Intune SCEP API public GitHub repository for you to download, and use in your solutions. Use this API with third-party SCEP servers to run custom challenge validation against Intune before SCEP provisions a certificate to a device.
Integrate with Intune SCEP management solution provides more details on using the API, its methods, and testing the solution you build.
Part 2 - Create the application and profile
Using a Microsoft Entra application, you can delegate rights to Intune to handle SCEP requests coming from devices. The Microsoft Entra application includes application ID and authentication key values that are used within the API solution the developer creates. Administrators then create and deploy SCEP certificates profiles using Intune and can view reports on the deployment status on the devices.
This article provides an overview of this feature from an Administrator-perspective, including creating the Microsoft Entra application.
Overview
The following steps provide an overview of using SCEP for certificates in Intune:
- In Intune, an administrator creates a SCEP certificate profile, and then targets the profile to users or devices.
- The device checks in to Intune.
- Intune creates a unique SCEP challenge. It also adds additional integrity-check information, such as what the expected subject and SAN should be.
- Intune encrypts and signs both the challenge and integrity-check information, and then sends this information to the device with the SCEP request.
- The device generates a certificate signing request (CSR) and public/private key pair on the device based on the SCEP certificate profile that's pushed from Intune.
- The CSR and encrypted/signed challenge are sent to the third-party SCEP server endpoint.
- The SCEP server sends the CSR and the challenge to Intune. Intune then validates the signature, decrypts the payload, and compares the CSR to the integrity-check information.
- Intune sends back a response to the SCEP server, and states whether the challenge validation is successful or not.
- If the challenge is successfully verified, then the SCEP server issues the certificate to the device.
The following diagram shows a detailed flow of third-party SCEP integration with Intune:
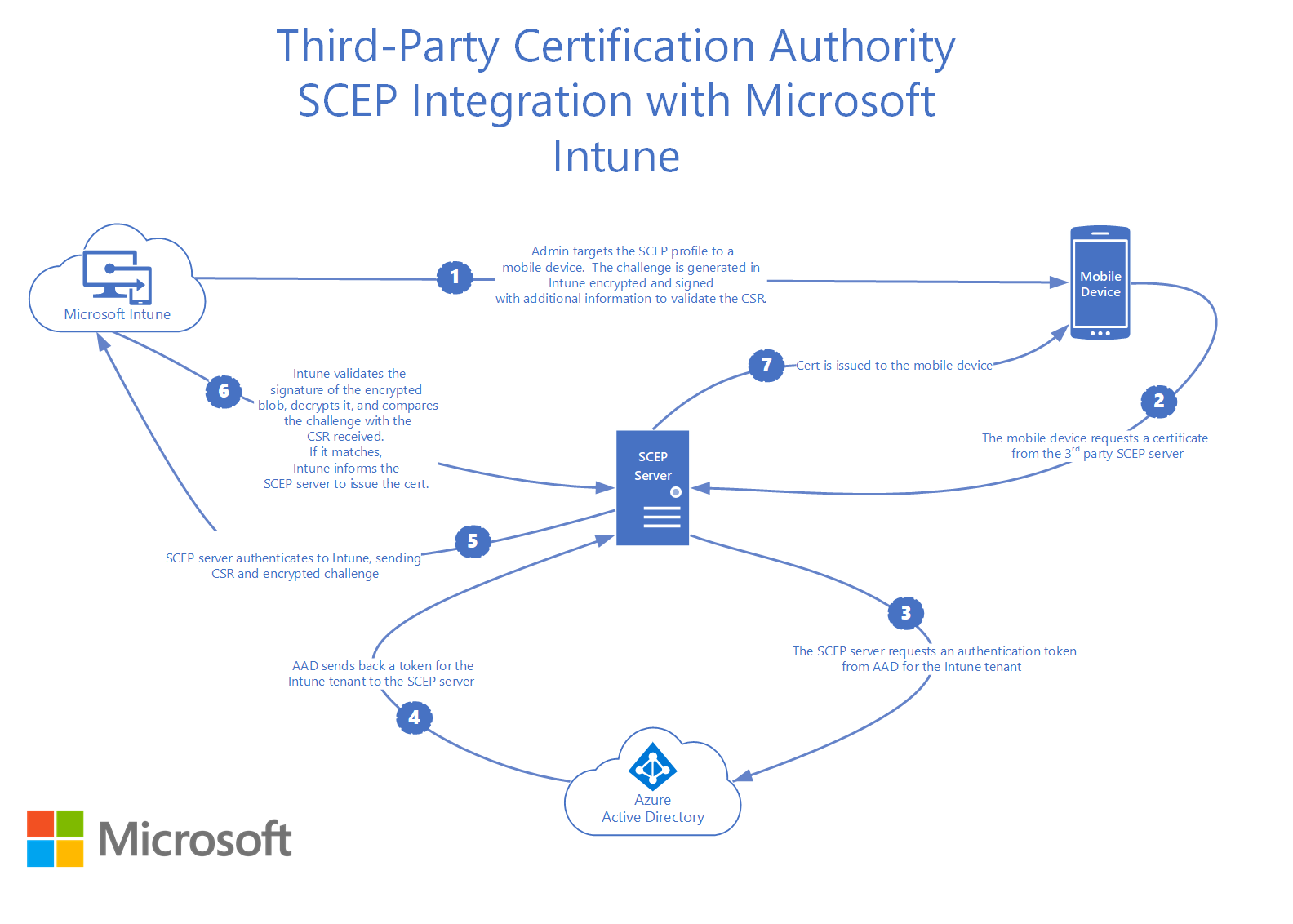
Set up third-party CA integration
Validate third-party certification authority
Before integrating third-party certification authorities with Intune, confirm that the CA you're using supports Intune. Third-party CA partners (in this article) includes a list. You can also check your certification authority's guidance for more information. The CA may include setup instructions specific to their implementation.
Note
To support the following devices, the CA must support the use of an HTTPS URL when you configure you must configure an HTTPS URL when you configure SCEP Server URLs for the SCEP certificate profile:
- Android device administrator
- Android Enterprise device owner
- Android Enterprise corporate-owned work profile
- Android Enterprise personally-owned work profile
Authorize communication between CA and Intune
To allow a third-party SCEP server to run custom challenge validation with Intune, create an app in Microsoft Entra ID. This app gives delegated rights to Intune to validate SCEP requests.
Be sure you have the required permissions to register a Microsoft Entra app. See Required permissions, in the Microsoft Entra documentation.
Create an application in Microsoft Entra ID
In the Azure portal, go to Microsoft Entra ID > App Registrations, and then select New registration.
On the Register an application page, specify the following details:
- In the Name section, enter a meaningful application name.
- For the Supported account types section, select Accounts in any organizational directory.
- For Redirect URI, leave the default of Web, and then specify the sign-on URL for the third-party SCEP server.
Select Register to create the application and to open the Overview page for the new app.
On the app Overview page, copy the Application (client) ID value and record it for later use. You'll need this value later.
In the navigation pane for the app, go to Certificates & secrets under Manage. Select the New client secret button. Enter a value in Description, select any option for Expires, and then and choose Add to generate a value for the client secret.
Important
Before you leave this page, copy the value for the client secret and record it for later use with your third-party CA implementation. This value is not shown again. Be sure to review the guidance for your third-party CA on how they want the Application ID, Authentication Key, and Tenant ID configured.
Record your Tenant ID. The Tenant ID is the domain text after the @ sign in your account. For example, if your account is admin@name.onmicrosoft.com, then your tenant ID is name.onmicrosoft.com.
In the navigation pane for the app, go to API permissions, which are under Manage. You're going to add two separate application permissions:
Select Add a permission:
- On the Request API permissions page, select Intune and then select Application permissions.
- Select the checkbox for scep_challenge_provider (SCEP challenge validation).
- Select Add permissions to save this configuration.
Select Add a permission again.
- On the Request API permissions page, select Microsoft Graph > Application permissions.
- Expand Application and select the checkbox for Application.Read.All (Read all applications).
- Select Add permissions to save this configuration.
Remain on the API permissions page, and select Grant admin consent for <your tenant>, and then select Yes.
The app registration process in Microsoft Entra ID is complete.
Configure and deploy a SCEP certificate profile
As the administrator, create a SCEP certificate profile to target to users or devices. Then, assign the profile.
Removing certificates
After you unenroll or wipe the device, the certificates are removed from the device by Intune and queued for revocations. Revocation on the certificate authority depends on API implementation by each third party.
Third-party certification authority partners
The following third-party certification authorities support Intune:
- AWS Private Certificate Authority
- Cogito Group
- DigiCert
- EasyScep
- EJBCA
- Entrust
- EverTrust
- GlobalSign
- HID Global
- IDnomic
- Keyfactor Command
- KeyTalk
- Keytos
- Nexus Certificate Manager
- SCEPman
- Sectigo
- SecureW2
- Splashtop
- Venafi
If you're a third-party CA interested in integrating your product with Intune, review the API guidance:
Security and privacy information
Some user information in the SCEP profile becomes visible to the third-party certificate authority (CA) receiving the certificate signing request. This happens when you deploy a new or updated SCEP profile that contains the Common name (CN) user attribute, and variables such as UserName, OnPrem_Distinguished_Name, and OnPremisesSamAccountName. During profile deployment, Microsoft Intune replaces these variables with actual values. The targeted devices in turn must reach out to the third-party CA to request a certificate with the actual values.
For a list of supported user variables, see Step 7 under Create a SCEP certificate profile.