Manage Disk Encryption policy for Windows devices with Intune
Use Intune to configure BitLocker encryption on devices that run Windows 10 or later, and Personal Data Encryption (PDE) on devices that run Windows 11 Version 22H2 or later.
Tip
Some settings for BitLocker require the device have a supported TPM.
To configure encryption on your managed devices, use one of the following policy types:
Endpoint security > Windows encryption policy. Choose from the following profiles:
BitLocker - A focused group of settings that are dedicated to configuring BitLocker. For more information, see the BitLocker CSP.
Personal Data Encryption - Personal Data Encryption (PDE) differs from BitLocker in that it encrypts files instead of whole volumes and disks. PDE occurs in addition to other encryption methods like BitLocker. Unlike BitLocker that releases data encryption keys at boot, PDE doesn't release data encryption keys until a user signs in using Windows Hello for Business. For more information, see the PDE CSP.
Device configuration profile for endpoint protection for BitLocker. BitLocker settings are one of the available settings categories for Windows 10/11 endpoint protection.
View the BitLocker settings that are available for BitLocker in endpoint protection profiles from device configuration policy.
Tip
Intune provides a built-in encryption report that presents details about the encryption status of devices, across all your managed devices. After Intune encrypts a Windows device with BitLocker, you can view and manage BitLocker recovery keys when you view the encryption report.
You can also access important information for BitLocker from your devices, as found in Microsoft Entra ID.
Important
Before enabling BitLocker, understand and plan for recovery options that meet your organizations needs. For more information, start with BitLocker recovery overview in the Windows security documentation.
Role-based access controls to manage BitLocker
To manage BitLocker in Intune, an account must be assigned an Intune role-based access control (RBAC) role that includes the Remote tasks permission with the Rotate BitLockerKeys (preview) right set to Yes.
You can add this permission and right to your own custom RBAC roles or use one of the following built-in RBAC roles that include this right:
- Help Desk Operator
- Endpoint Security Administrator
Create and deploy policy
Use one of the following procedures to create the policy type you prefer.
Create an endpoint security policy for Windows
Sign in to the Microsoft Intune admin center.
Select Endpoint security > Disk encryption > Create Policy.
Set the following options:
- Platform: Windows
- Profile: Choose either BitLocker or Personal Data Encryption

On the Configuration settings page, configure settings for BitLocker to meet your business needs.
Select Next.
On the Scope (Tags) page, choose Select scope tags to open the Select tags pane to assign scope tags to the profile.
Select Next to continue.
On the Assignments page, select the groups that receive this profile. For more information on assigning profiles, see Assign user and device profiles.
Select Next.
On the Review + create page, when you're done, choose Create. The new profile is displayed in the list when you select the policy type for the profile you created.
Create a device configuration profile for Windows encryption
Tip
The following procedure configures BitLocker through a device configuration template for Endpoint protection. To configure Personal Data Encryption, use the device configuration settings catalog and the PDE category.
Sign in to the Microsoft Intune admin center.
Select Devices > Manage devices > Configuration > On the Policies tab, select Create.
Set the following options:
- Platform: Windows 10 and later
- Profile type: Select Templates > Endpoint protection, and then select Create.
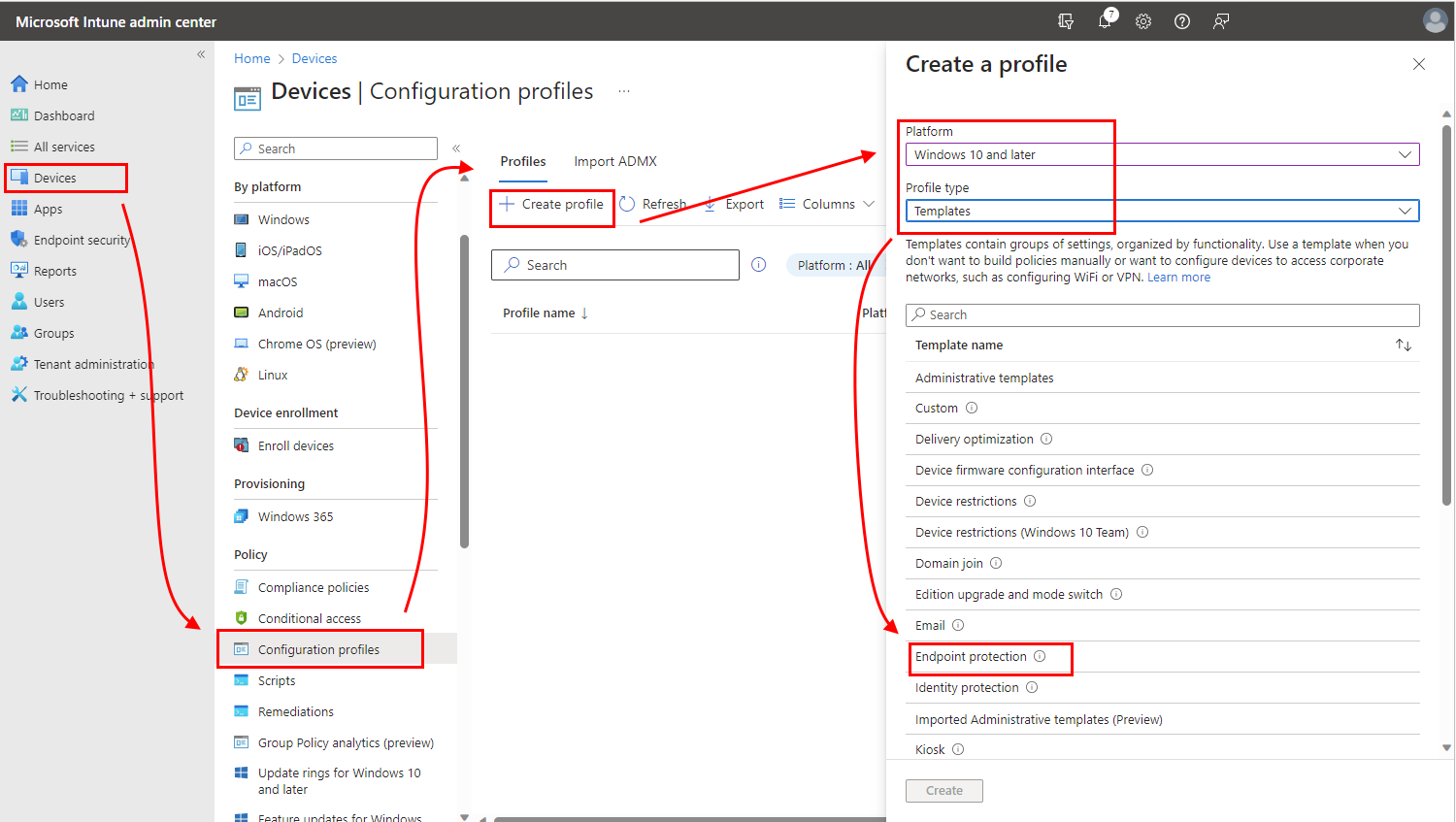
On the Configuration settings page, expand Windows Encryption.

Configure settings for BitLocker to meet your business needs.
If you want to enable BitLocker silently, see Silently enable BitLocker on devices, in this article for extra prerequisites and the specific setting configurations you must use.
Select Next to continue.
Complete configuration of other settings, and then save the profile.
Manage BitLocker
The following subjects can help you manage specific tasks through BitLocker policy, and manage recovery keys:
- Silently enable BitLocker on devices
- Full disk vs Used Space only encryption
- View details for recovery keys
- View recovery keys for tenant-attached devices
- Rotate BitLocker recovery keys
- End user self service recovery key experiences
To view information about devices that receive BitLocker policy, see Monitor disk encryption.
Silently enable BitLocker on devices
You can configure a policy for BitLocker to automatically and silently encrypt a device without presenting any UI to the end user, even when that user isn't a local Administrator on the device.
To be successful, devices must meet the following device prerequisites, receive the applicable settings to silently enable BitLocker, and must not have settings that require use of a TPM startup PIN or key. Use of a startup PIN or key is incompatible with silent encryption as it requires user interaction.
Device Prerequisites
A device must meet the following conditions to be eligible for silently enabling BitLocker:
- If end users sign in to the devices as Administrators, the device must run Windows 10 version 1803 or later, or Windows 11.
- If end users sign in to the devices as Standard Users, the device must run Windows 10 version 1809 or later, or Windows 11.
- The device must be Microsoft Entra joined or Microsoft Entra hybrid joined.
- Device must contain at least TPM (Trusted Platform Module) 1.2.
- The BIOS mode must be set to Native UEFI only.
Required settings to silently enable BitLocker
Depending on the type of policy that you use to silently enable BitLocker, configure the following settings. Both methods manage BitLocker through Windows encryption CSPs on Windows devices.
Endpoint security Disk encryption policy - Configure the following settings in the BitLocker profile:
- Require Device Encryption = Enabled
- Allow Warning For Other Disk Encryption = Disabled
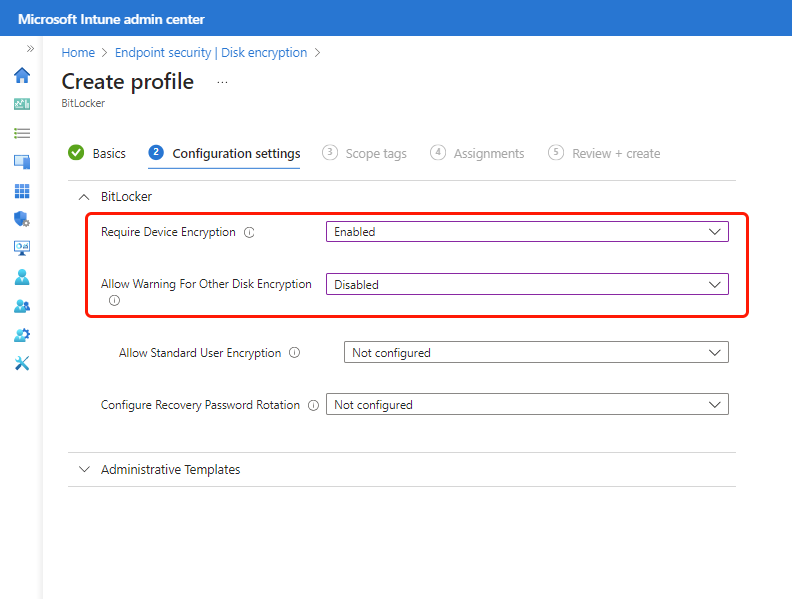
In addition to the two required settings, consider use of Configure Recovery Password Rotation.
Device configuration Endpoint protection policy - Configure the following settings in the Endpoint protection template or a custom settings profile:
- Warning for other disk encryption = Block.
- Allow standard users to enable encryption during Microsoft Entra join = Allow
- User creation of recovery key = Allow or Do not allow 256-bit recovery key
- User creation of recovery password = Allow or Require 48-digit recovery password
TPM startup PIN or key
A device must not be set to require a startup PIN or startup key.
When a TPM startup PIN or startup key is required on a device, BitLocker can't silently enable on the device, and instead requires interaction from the end user. Settings to configure the TPM startup PIN or key are available in both the endpoint protection template and the BitLocker policy. By default, these policies don't configure these settings.
Following are the relevant settings for each profile type:
Endpoint security disk encryption policy - TPM settings are only visible after you expand the Administrative Templates category and then in the Windows Components > BitLocker Drive Encryption > Operating System Drives section set Require additional authentication at startup to Enabled. When configured, the following TPM settings are then available:
Configure TPM startup key and PIN - Configure this as Do not allow startup key and PIN with TPM
Configure TPM startup PIN - Configure this as Do not allow startup PIN with TPM
Configure TPM startup - Configure this as Allow TPM or Require TPM
Configure TPM startup key - Configure this as Do not allow startup key with TPM
Device configuration policy - In the endpoint protection template you'l find the following settings in the Windows Encryption category:
- Compatible TPM startup - Configure this as Allow TPM or Require TPM
- Compatible TPM startup PIN - Configure this as Do not allow startup PIN with TPM
- Compatible TPM startup key - Configure this as Do not allow startup Key with TPM
- Compatible TPM startup key and PIN - Configure this as Do not allow startup Key and PIN with TPM
Warning
While neither the endpoint security or device configuration policies configure the TPM settings by default, some versions of the security baseline for Microsoft Defender for Endpoint will configure both Compatible TPM startup PIN and Compatible TPM startup key by default. These configurations might block silent enablement of BitLocker.
If you deploy this baseline to devices on which you want to silently enable BitLocker, review your baseline configurations for possible conflicts. To remove conflicts, either reconfigure the settings in the baselines to remove the conflict, or remove applicable devices from receiving the baseline instances that configure TPM settings that block silent enablement of BitLocker.
Full disk vs Used Space only encryption
Three settings determine whether an OS drive is encrypted by encrypting the used space only, or by full disk encryption:
- Whether the hardware of the device is modern standby capable
- Whether silent enablement has been configured for BitLocker
- ('Warning for other disk encryption' = Block or 'Hide prompt about third-party encryption' = Yes)
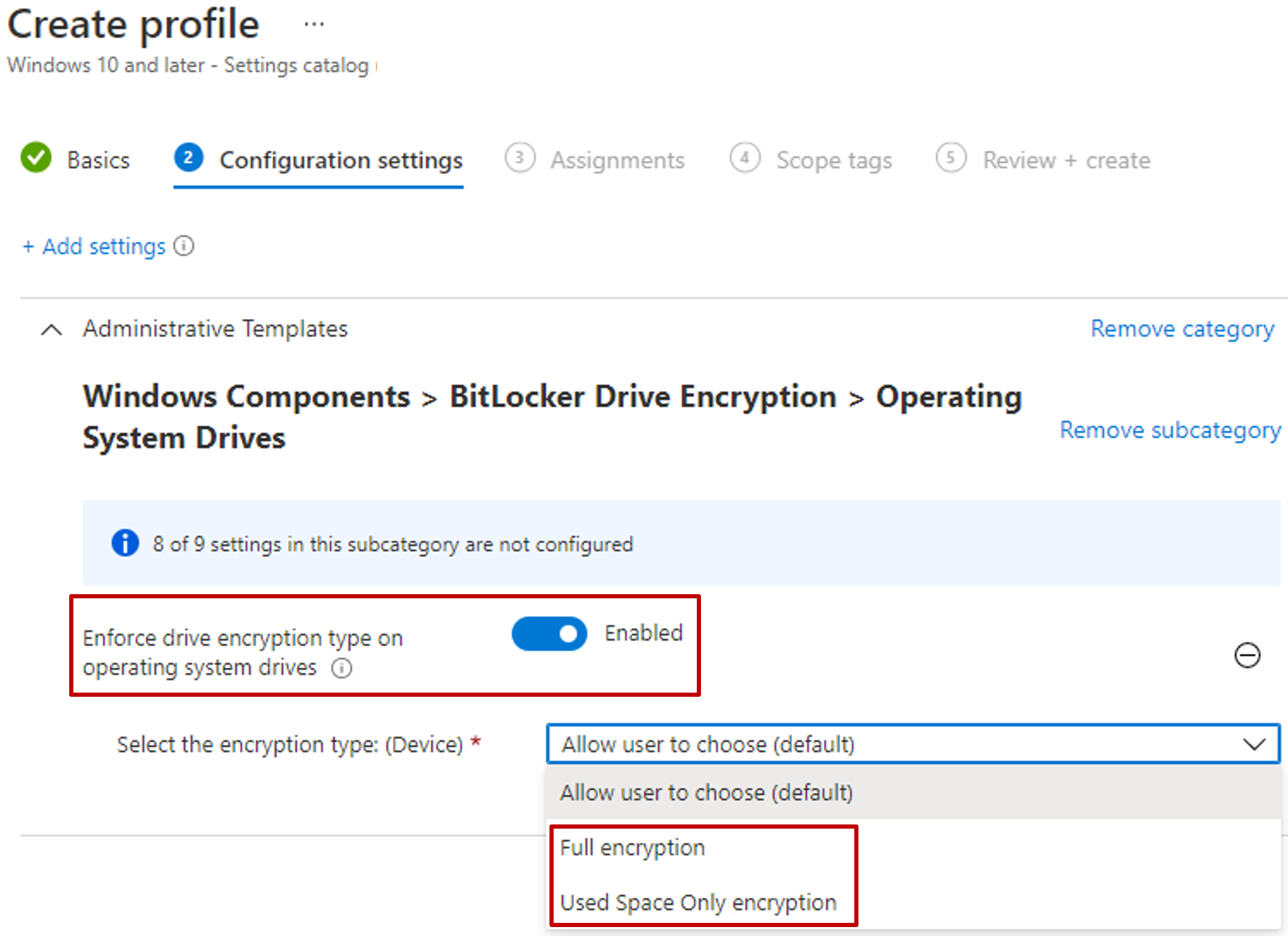
- Configuration of the SystemDrivesEncryptionType
- (Enforce drive encryption type on operating system drives)
Assuming that SystemDrivesEncryptionType isn't configured, the following behavior is expected. When silent enablement is configured on a modern standby device, the OS drive is encrypted using the used space only encryption. When silent enablement is configured on a device that isn't capable of modern standby, the OS drive is encrypted using full disk encryption. The result is the same whether you're using an Endpoint Security disk encryption policy for BitLocker or a Device Configuration profile for endpoint protection for BitLocker. If a different end state is required, the encryption type can be controlled by configuring the SystemDrivesEncryptionType using settings catalog.
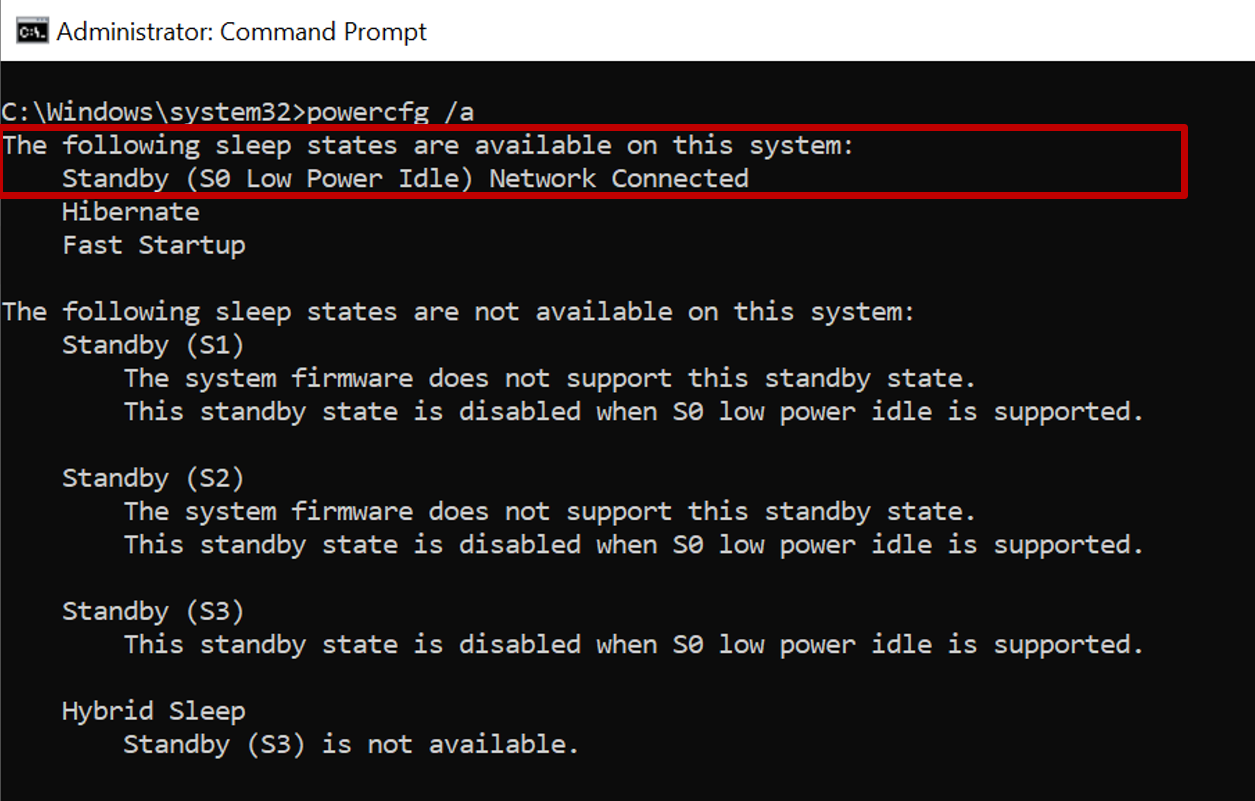
To verify whether the hardware is modern standby capable, run the following command from a command prompt:
powercfg /a
If the device supports modern standby, it shows that Standby (S0 Low Power Idle) Network Connected is available
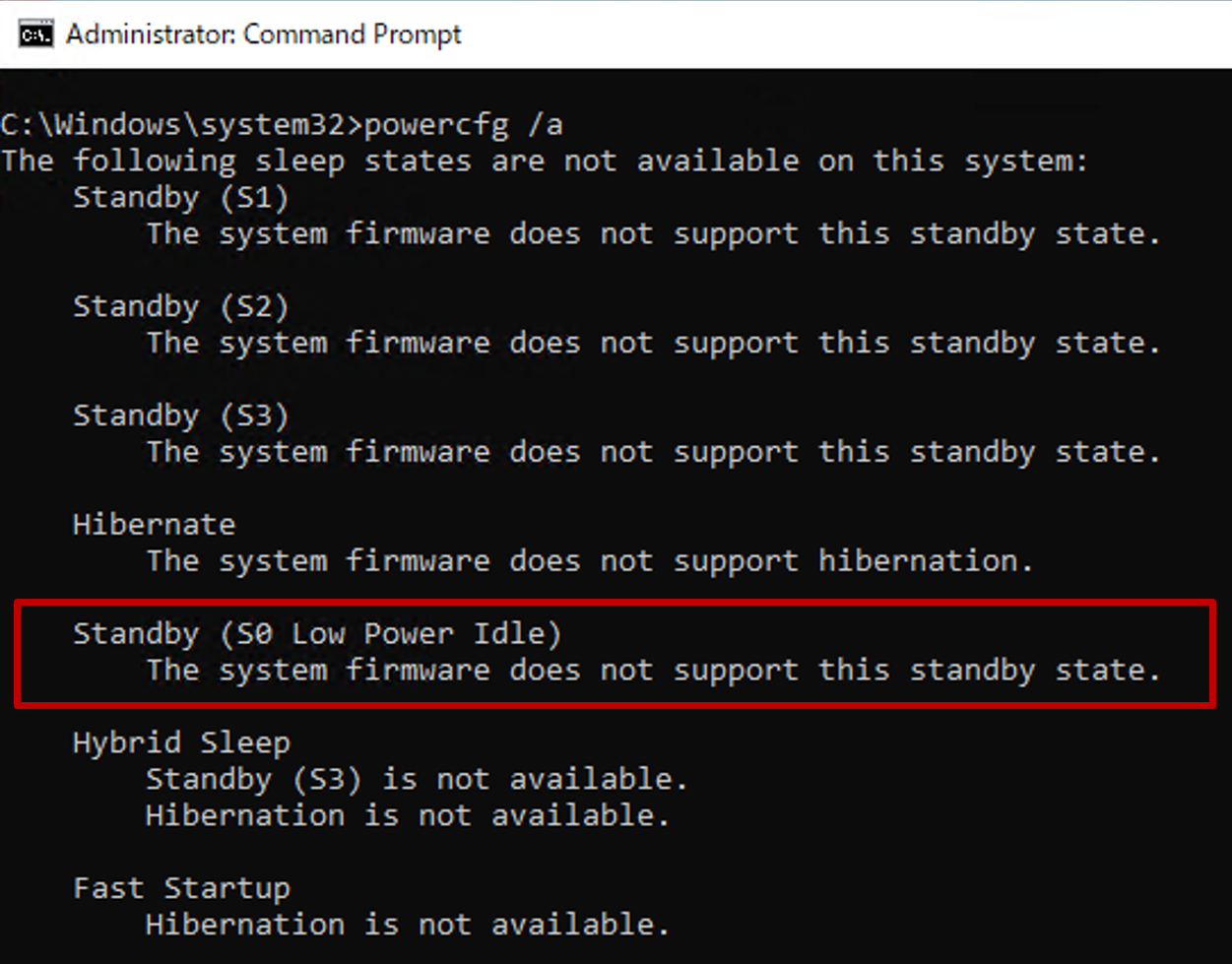
If the device doesn't support modern standby, such as a virtual machine, it shows that Standby (S0 Low Power Idle) Network Connected isn't supported
To verify the encryption type, run the following command from an elevated (admin) command prompt:
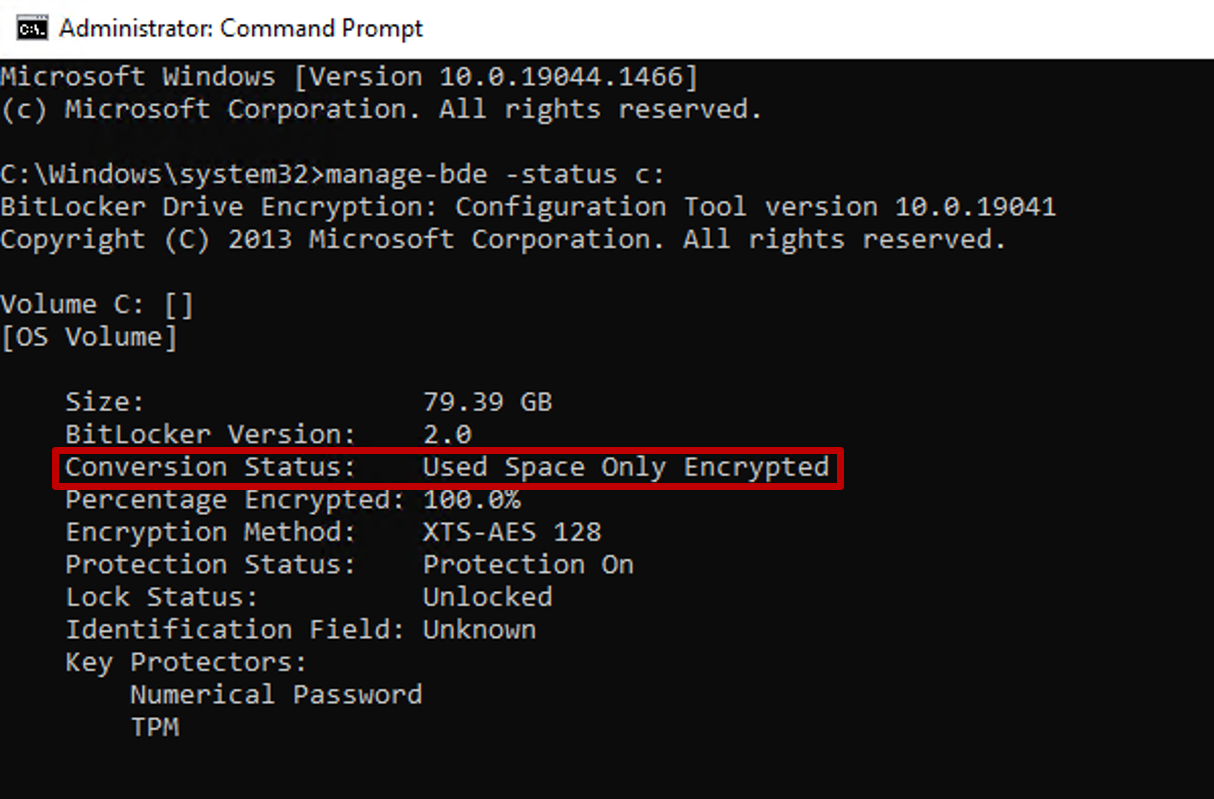
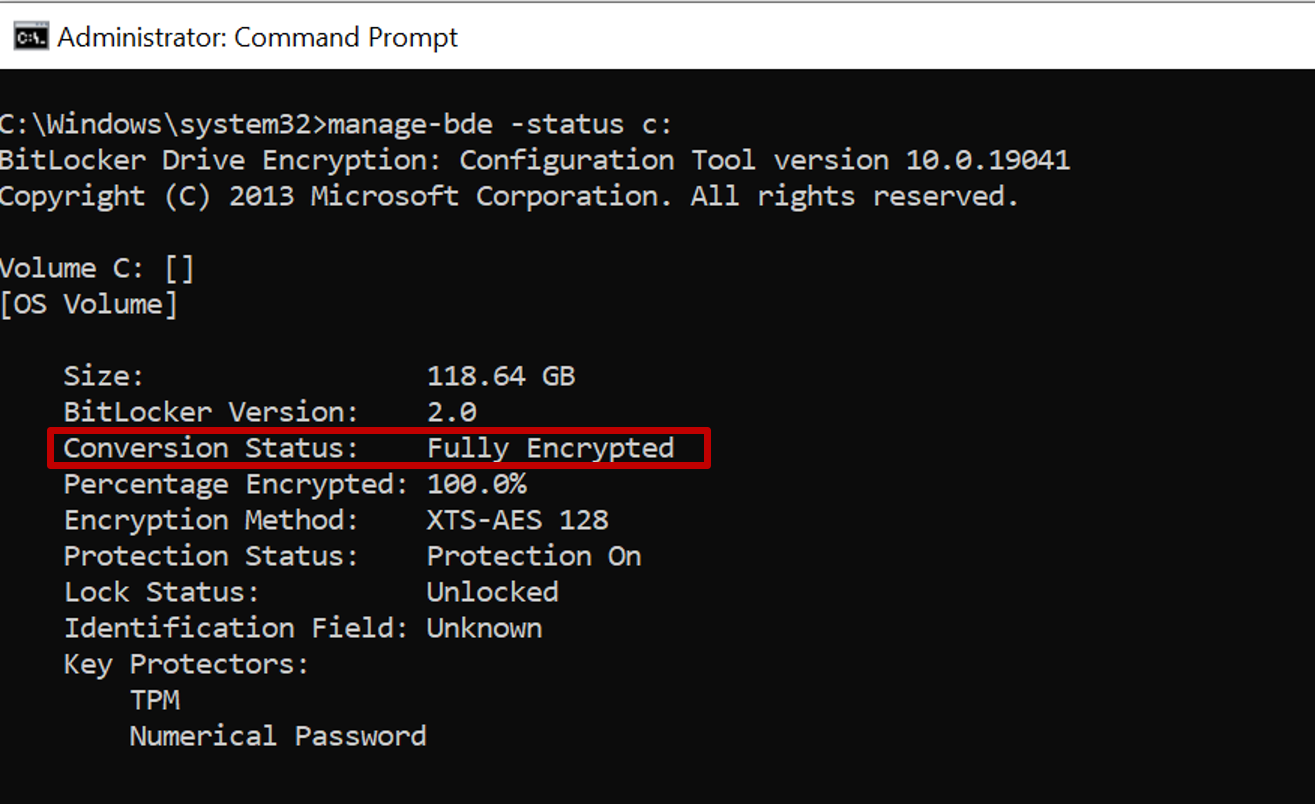
manage-bde -status c:
The 'Conversion Status' field reflects the encryption type as either Used Space Only encrypted or Fully Encrypted.
To change the disk encryption type between full disk encryption and used space only encryption, use the'Enforce drive encryption type on operating system drives' setting within settings catalog.
View details for recovery keys
Intune provides access to the Microsoft Entra node for BitLocker so you can view BitLocker Key IDs and recovery keys for your Windows 10/11 devices, from within the Microsoft Intune admin center. Support to view recovery keys can also extend to your tenant-attached devices.
To be accessible, the device must have its keys escrowed to Microsoft Entra.
Sign in to the Microsoft Intune admin center.
Select Devices > All devices.
Select a device from the list, and then under Monitor, select Recovery keys.
Hit Show Recovery Key. Selecting this option generates an audit log entry under 'KeyManagement' activity.
When keys are available in Microsoft Entra, the following information is available:
- BitLocker Key ID
- BitLocker Recovery Key
- Drive Type
When keys aren't in Microsoft Entra, Intune displays No BitLocker key found for this device.
Note
Currently, Microsoft Entra ID supports a maximum of 200 BitLocker recovery keys per device. If you reach this limit, silent encryption will fail due to the failing backup of recovery keys before starting encryption on the device.
Information for BitLocker is obtained using the BitLocker configuration service provider (CSP). BitLocker CSP is supported on Windows 10 version 1703 and later, Windows 10 Pro version 1809 and later, and Windows 11.
IT admins need to have a specific permission within Microsoft Entra ID to be able to see device BitLocker recovery keys: microsoft.directory/bitlockerKeys/key/read. There are some roles within Microsoft Entra ID that come with this permission, including Cloud Device Administrator, Helpdesk Administrator, etc. For more information on which Microsoft Entra roles have which permissions, see Microsoft Entra built-in roles.
All BitLocker recovery key accesses are audited. For more information on Audit Log entries, see Azure portal audit logs.
Note
If you delete the Intune object for a Microsoft Entra joined device protected by BitLocker, the deletion triggers an Intune device sync and removes the key protectors for the operating system volume. Removing the key protector leaves BitLocker in a suspended state on that volume. This is necessary because BitLocker recovery information for Microsoft Entra joined devices is attached to the Microsoft Entra computer object and deleting it may leave you unable to recover from a BitLocker recovery event.
View recovery keys for tenant-attached devices
When you use the tenant attach scenario, Microsoft Intune can display recovery key data for tenant attached devices.
To support the display of recovery keys for tenant attached devices, your Configuration Manager sites must run version 2107 or later. For sites that run 2107, you must install an update rollup to support Microsoft Entra joined devices: See KB11121541.
To view the recovery keys, your Intune account must have the Intune RBAC permissions to view BitLocker keys, and must be associated with an on-premises user that has the related permissions for Configuration Manager of Collection Role, with Read Permission > Read BitLocker Recovery Key Permission. For more information, see Configure role-based administration for Configuration Manager.
Rotate BitLocker recovery keys
You can use an Intune device action to remotely rotate the BitLocker recovery key of a device that runs Windows 10 version 1909 or later, and Windows 11.
Prerequisites
Devices must meet the following prerequisites to support rotation of the BitLocker recovery key:
Devices must run Windows 10 version 1909 or later, or Windows 11
Microsoft Entra joined and Microsoft Entra hybrid joined devices must have support for key rotation enabled via BitLocker policy configuration:
- Client-driven recovery password rotation to Enable rotation on Microsoft Entra joined devices or Enable rotation on Microsoft Entra ID and Microsoft Entra joined hybrid joined devices
- Save BitLocker recovery information to Microsoft Entra ID to Enabled
- Store recovery information in Microsoft Entra ID before enabling BitLocker to Required
For information about BitLocker deployments and requirements, see the BitLocker deployment comparison chart.
To rotate the BitLocker recovery key
Sign in to the Microsoft Intune admin center.
Select Devices > All devices.
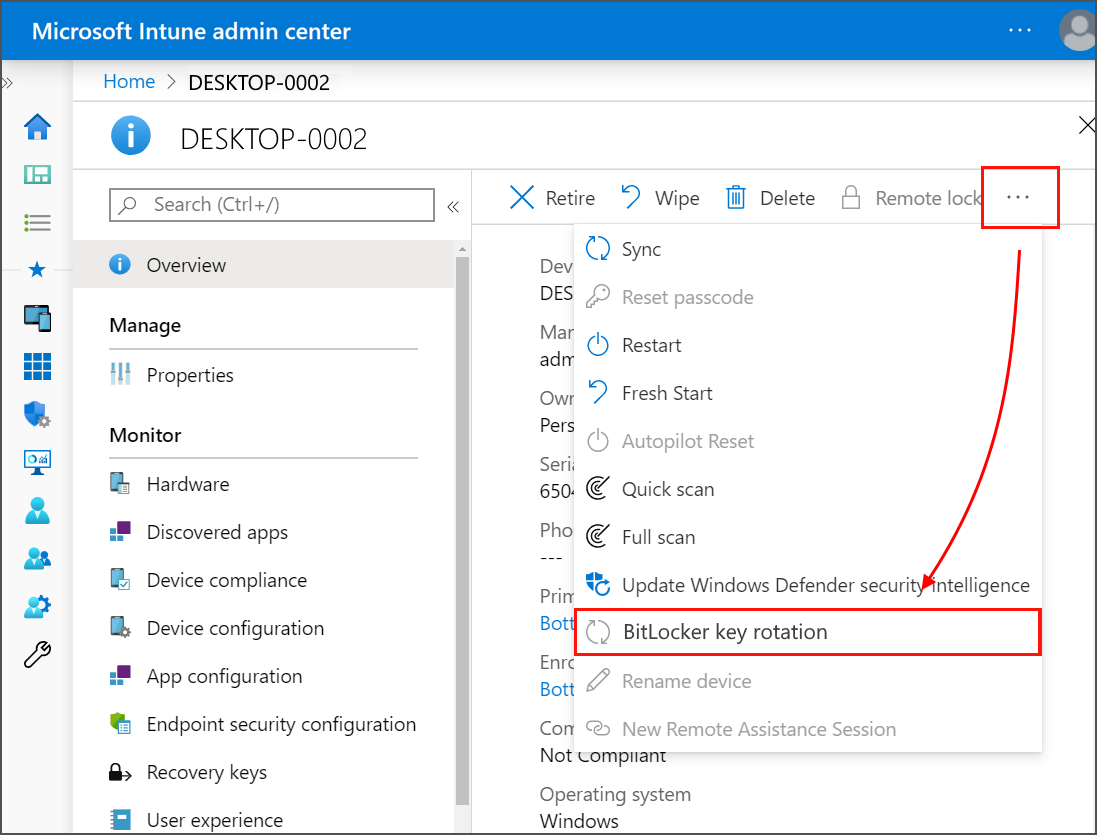
In the list of devices that you manage, select a device, and then select the BitLocker key rotation remote action. If this option should be available but isn't visible, select the ellipsis (...) and then BitLocker key rotation.
On the Overview page of the device, select the BitLocker key rotation. If you don't see this option, select the ellipsis (…) to show all options, and then select the BitLocker key rotation device remote action.
Self service recovery keys
To help end users get their recovery keys without calling the company helpdesk, Intune enables self service scenarios for the end user through the Company Portal app.
While Intune helps configure policy to define the escrow of BitLocker recovery keys, these keys are stored within Entra ID. These are the capabilities within Entra ID that are helpful to use with self-service BitLocker recovery key access for end users.
Tenant-wide toggle to prevent recovery key access for non-admin users: This setting determines if users can use self-service to recover their BitLocker keys. The default value is 'No' which allows all users to recover their BitLocker keys. 'Yes' restricts non-admin users from being able to see the BitLocker keys for their own devices if there are any. Learn more about this control in Entra ID.
Auditing for recovery key access: Audit Logs within the Entra ID portal show the history of activities within the tenant. Any user recovery key accesses made through the Company Portal website will be logged in Audit Logs under the Key Management category as a “Read BitLocker key” activity type. The user’s User Principal Name and other info such as key ID is also logged. Learn more about audit logs in Entra ID.
Entra Conditional Access policy requiring a compliant device to access BitLocker Recovery Key: With Conditional Access policy (CA), you can restrict the access to certain corporate resources if a device isn't compliant with the “Require compliant device” setting. If this is set up within your organization, and a device fails to meet the Compliance requirements configured in the Intune Compliance policy, that device can't be used to access the BitLocker Recovery Key as it is considered a corporate resource which is access controlled by CA.
Next steps
- Manage FileVault policy
- Monitor disk encryption
- Troubleshooting BitLocker policy
- Known issues for Enforcing BitLocker policies with Intune
- BitLocker management for enterprises, in the Windows security documentation
- Personal Data Encryption overview
- Self service scenarios for the end user through the Company Portal app