Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Protected view (Protected View) and Application Guard (Application Guard for Office) are mechanisms embedded into Microsoft Office products to help protect users' computers from attacks in files sourced from the Internet. A user's license controls the availability of these tools. When enabled, Office opens files from potentially unsafe locations in Protected View or Application Guard.
As part of the CSPP Plus program, desktop Office clients can open, edit, and save files stored on selected third-party hosts. Like other files originating from the Internet, these files are considered potentially unsafe and, by default, open in a restricted form:
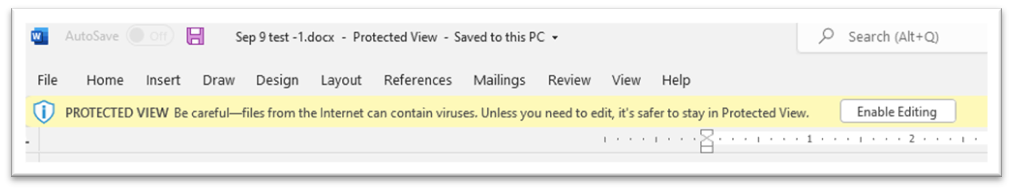
Figure 1 - File opened in Protected View
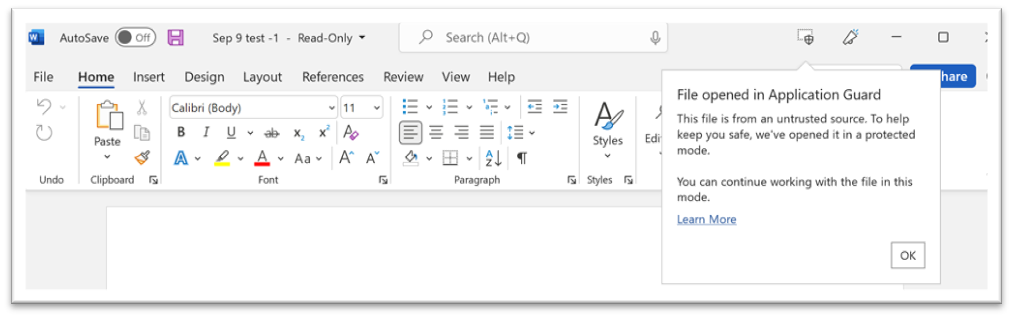
Figure 2 - File opened in Application Guard
It's possible to remove the protection provided by Protected View and Application Guard to enable unrestricted access to files, converting the documents to Trusted Documents.
Note
Organizations can implement policies that prevent removing Protected View and Application Guard protection from a file.
Individual (per file) authorization
Users can trust individual documents to prevent opening them in Protected View and Application Guard:
Warning
Users are advised to only do this if they are confident that the file, and its source, is trustworthy.
For Protected View:
- On the Message Bar, click Enable Editing.
For Application Guard:
- Go to File > Info and select Remove protection.
Manual authorization (per machine)
Users can trust specific Internet locations to prevent Protected View and Application Guard to act on those files based on location.
Warning
Only do this if you're confident that the location is trustworthy.
Add the host internet address as a trusted site:
- Open the Control Panel.
- Open the Internet Options object.
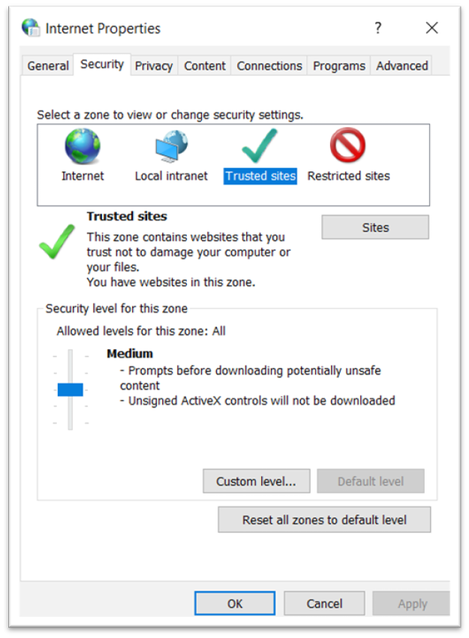
- In the Internet Properties window, click the Security tab.
- Select the Trusted sites entry and click the Sites button.
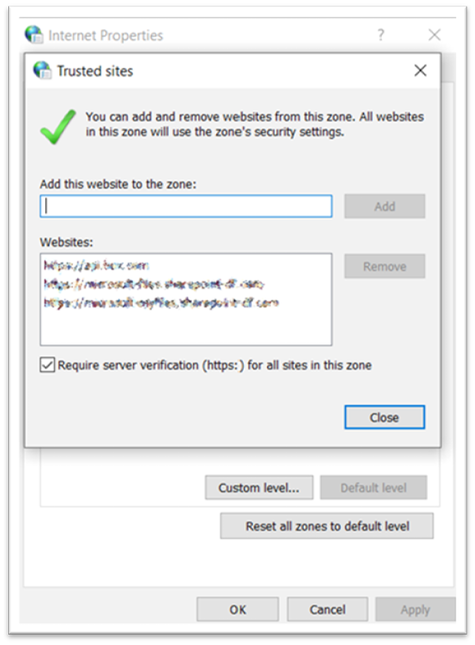
- In the Add this website to the zone field, enter the address for the trusted location starting with https:.
- Click Add.
- Close the windows.
Note
Organizations can implement policies that prevent users from modifying these settings.
Global authorization (GPO)
IT admins can enforce assignments of Internet Sites to Security Zones across organizations using Group Policy Objects (GPO). This includes the classification of a particular hosts as a trusted location.
To enforce mapping hosts to certain zones, IT admins can enable and configure this GPO: Site to Zone Assignment List.
You can find this GPO in the Group Policy Editor under:
Computer Configuration / Administrative Templates / Windows Components / Internet Explorer / Internet Control Panel / Security Page / Site to Zone Assignment List.
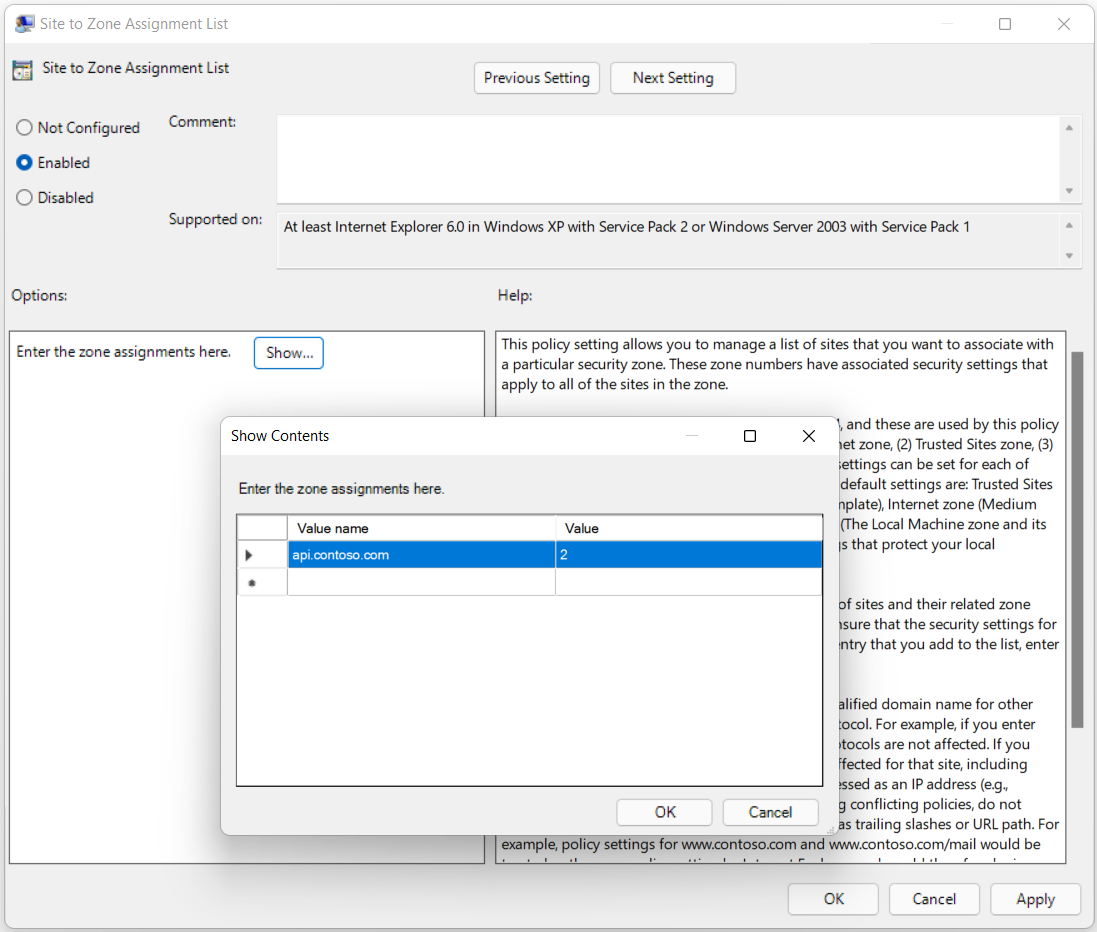
Note
api.contoso.com in the previous screenshot should be replaced by the appropriate domain(s) provided by the CSPP Plus host.
After enabling the GPO, IT Admins can assign websites to each of the security zones according to this map:
- Intranet zone
- Trusted Sites zone
- Internet zone
- Restricted Sites zone
To prevent Protected View and Application Guard to act on files based on location, the host address, starting with https:, should be assigned to Trusted Sites zone (2).
Note
Enabling the Site to Zone Assignment List GPO overwrites all previously configured assignments. It prevents users from modifying the assignments. And sets it to only consider the mappings included in the GPO across all the zones.