Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
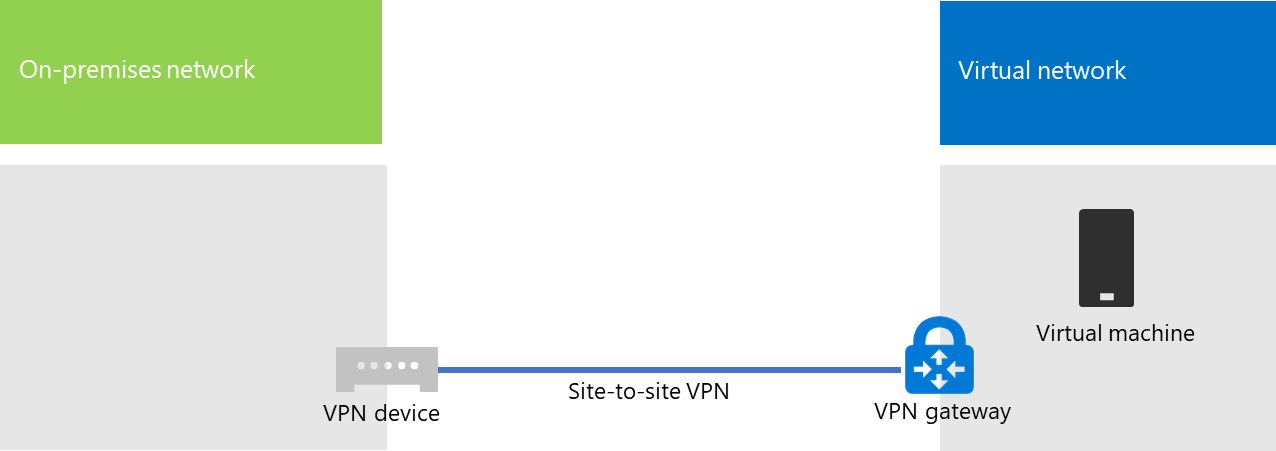
A cross-premises Azure virtual network is connected to your on-premises network, extending your network to include subnets and virtual machines hosted in Azure infrastructure services. This connection lets computers on your on-premises network to directly access virtual machines in Azure and vice versa.
For example, a directory synchronization server running on an Azure virtual machine needs to query your on-premises domain controllers for changes to accounts and synchronize those changes with your Microsoft 365 subscription.
To set up a cross-premises Azure virtual network using a site-to-site virtual private network (VPN) connection, see VPN Gateway documentation.
Here is your resulting configuration.
Next step
Deploy Microsoft 365 Directory Synchronization in Microsoft Azure