Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
This article walks you through how to review, create, or edit your security policies, and how to navigate advanced settings in Defender for Business.
Default policies
When you're setting up (or maintaining) Defender for Business, an important part of the process includes reviewing your default policies, such as:
Additional policies
In addition to your default security policies, you can add other policies, such as:
- Web content filtering
- Controlled folder access (requires Microsoft Intune)
- Attack surface reduction rules (ASR rules are configured in Intune)
Advanced features and settings
You can view and edit settings for advanced features, such as:
- Turning on (or off) advanced features;
- Specifying which time zone to use in the Microsoft Defender portal; and
- Whether to receive preview features as they become available.
Choose where to manage security policies and devices
Before you begin setting up your security policies, you'll need to choose which portal you want to use. You can choose to use either the Microsoft Defender portal or the Microsoft Intune admin center to onboard devices and create or edit security policies. The following table explains both options.
| Option | Description |
|---|---|
| Microsoft Defender portal | The Microsoft Defender portal (https://security.microsoft.com/) is a one-stop shop for managing your company's devices, security policies, and security settings in Defender for Business. With a simplified configuration process, you can use the Microsoft Defender portal to onboard devices, access your security policies and settings, use the Microsoft Defender Vulnerability Management dashboard, and view and manage incidents in one place. Note that currently, controlled folder access and attack surface reduction rules are set up and configured in the Microsoft Intune admin center. |
| Microsoft Intune admin center | The Microsoft Intune admin center (https://intune.microsoft.com/) lets you manage your workforce's devices and apps, including how they access your company data. You can onboard devices and access your security policies and settings in Intune. You can also use Intune to set up and configure attack surface reduction rules in Defender for Business. Intune is not included in the standalone version of Defender for Business, but it can be added on. If your company has been using Intune, you can choose to continue using it to manage your devices and security policies. To learn more, see Manage device security with endpoint security policies in Microsoft Intune |
If you're using Intune, and you attempt to view or edit security policies in the Microsoft Defender portal by going to Configuration management > Device configuration, you'll be prompted to choose whether to continue using Intune, or switch to using the Microsoft Defender portal instead, as shown in the following screenshot:
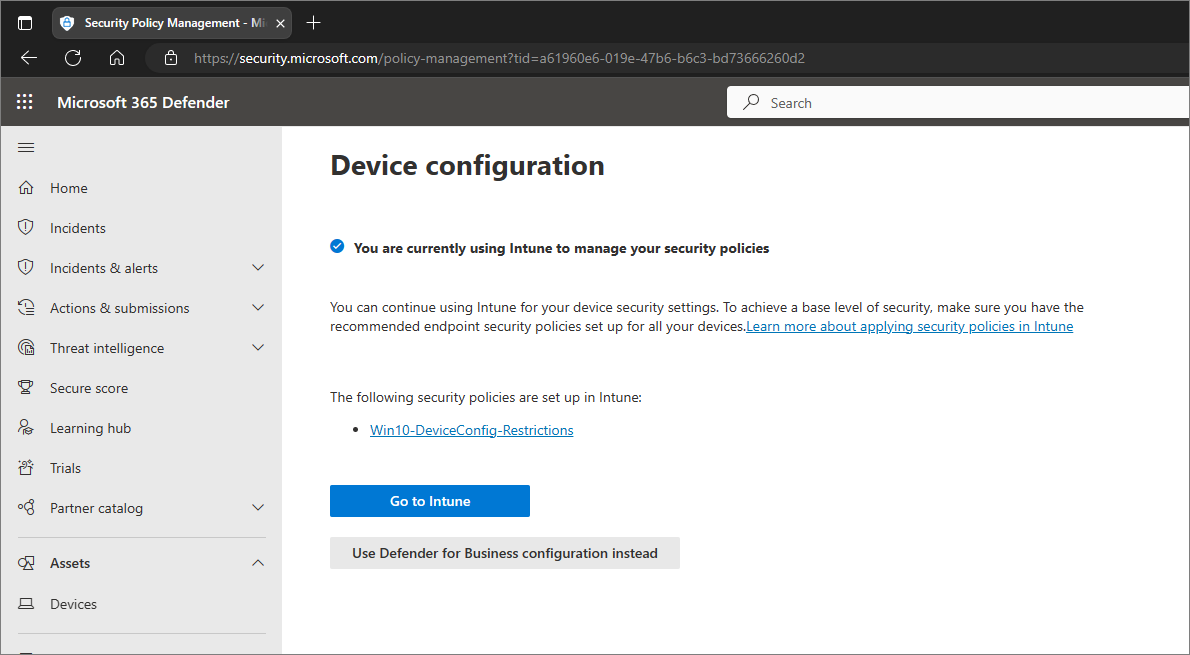
In the preceding image, Use Defender for Business configuration instead refers to using the Microsoft Defender portal, which provides a simplified configuration experience designed for small and medium-sized businesses. If you opt to use the Microsoft Defender portal, you must delete any existing security policies in Intune to avoid policy conflicts. For more details, see I need to resolve a policy conflict.
Note
If you're managing your security policies in the Microsoft Defender portal, you can view those policies in the Intune admin center, where they're listed as Antivirus or Firewall policies. When you view your firewall policies in the Intune admin center, you'll see two policies listed: one policy for firewall protection and another for custom rules.
You can export your list of policies through the Microsoft Intune admin center.
Next steps
- Review or edit your next-generation protection policies to apply antivirus/antimalware protection, and enable network protection.
- Review or edit your firewall policies.
- Set up your web content filtering policy and enable web protection automatically.
- Set up your controlled folder access policy for ransomware protection.
- Enable your attack surface reduction rules.
- Review settings for advanced features and the Microsoft Defender portal.