Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Applies to:
- Microsoft Defender for Endpoint Plan 2
- Microsoft Defender XDR
- Microsoft Defender Antivirus
Platforms
- Windows
Want to experience Defender for Endpoint? Sign up for a free trial.
This article describes EDR in block mode, which helps protect devices that are running a non-Microsoft antivirus solution (with Microsoft Defender Antivirus in passive mode).
What is EDR in block mode?
Endpoint detection and response (EDR) in block mode provides added protection from malicious artifacts when Microsoft Defender Antivirus is not the primary antivirus product and is running in passive mode. EDR in block mode is available in Defender for Endpoint Plan 2.
Important
EDR in block mode cannot provide all available protection when Microsoft Defender Antivirus real-time protection is in passive mode. Some capabilities that depend on Microsoft Defender Antivirus to be the active antivirus solution will not work, such as the following examples:
- Real-time protection, including on-access scanning, is not available when Microsoft Defender Antivirus is in passive mode. To learn more about real-time protection policy settings, see Enable and configure Microsoft Defender Antivirus always-on protection.
- Features like network protection and attack surface reduction rules and indicators (file hash, ip address, URL, and certificates) are only available when Microsoft Defender Antivirus is running in active mode. It is expected that your non-Microsoft antivirus solution includes these capabilities.
EDR in block mode works behind the scenes to remediate malicious artifacts that were detected by EDR capabilities. Such artifacts might have been missed by the primary, non-Microsoft antivirus product. EDR in block mode allows Microsoft Defender Antivirus to take actions on post-breach, behavioral EDR detections.
EDR in block mode is integrated with threat & vulnerability management capabilities. Your organization's security team gets a security recommendation to turn EDR in block mode on if it isn't already enabled.
Tip
To get the best protection, make sure to deploy Microsoft Defender for Endpoint baselines.
Watch this video to learn why and how to turn on endpoint detection and response (EDR) in block mode, enable behavioral blocking, and containment at every stage from pre-breach to post-breach.
What happens when something is detected?
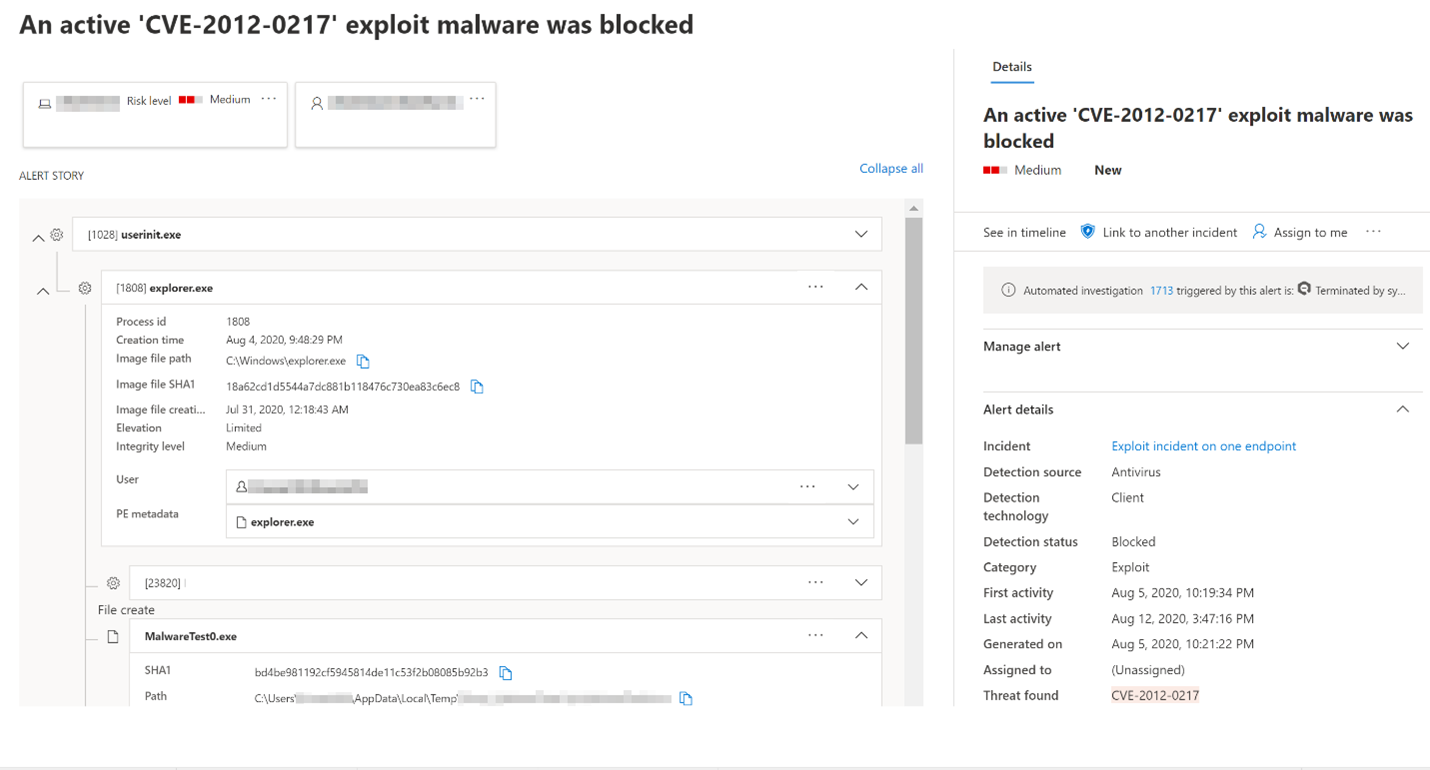
When EDR in block mode is turned on, and a malicious artifact is detected, Defender for Endpoint remediates that artifact. Your security operations team sees the detection status as Blocked or Prevented in the Action center, listed as completed actions. The following image shows an instance of unwanted software that was detected and remediated through EDR in block mode:
Enable EDR in block mode
Important
- Make sure the requirements are met before turning on EDR in block mode.
- Defender for Endpoint Plan 2 licenses are required.
- Beginning with platform version 4.18.2202.X, you can set EDR in block mode to target specific device groups using Intune CSPs. You can continue to set EDR in block mode tenant-wide in the Microsoft Defender portal.
- EDR in block mode is primarily recommended for devices that are running Microsoft Defender Antivirus in passive mode (a non-Microsoft antivirus solution is installed and active on the device).
Microsoft Defender portal
Go to the Microsoft Defender portal (https://security.microsoft.com/) and sign in.
Choose Settings > Endpoints > General > Advanced features.
Scroll down, and then turn on Enable EDR in block mode.
Intune
To create a custom policy in Intune, see Deploy OMA-URIs to target a CSP through Intune, and a comparison to on-premises.
For more information on the Defender CSP used for EDR in block mode, see "Configuration/PassiveRemediation" under Defender CSP.
Group Policy
You can use Group Policy to enable EDR in block mode.
On your Group Policy management computer, open the Group Policy Management Console.
Right-click the Group Policy Object you want to configure, and then select Edit.
In the Group Policy Management Editor go to Computer configuration and then select Administrative templates.
Expand the tree to Windows components > Microsoft Defender Antivirus > Features.
Double-click Enable EDR in block mode and set the option to Enabled.
Select OK.
Requirements for EDR in block mode
The following table lists requirements for EDR in block mode:
| Requirement | Details |
|---|---|
| Permissions | You must have either the Global Administrator or Security Administrator role assigned in Microsoft Entra ID. For more information, see Basic permissions. |
| Operating system | Devices must be running one of the following versions of Windows: - Windows 11 - Windows 10 (all releases) - Windows Server 2019 or later - Windows Server, version 1803 or later - Windows Server 2016 and Windows Server 2012 R2 (with the new unified client solution) |
| Microsoft Defender for Endpoint Plan 2 | Devices must be onboarded to Defender for Endpoint. See the following articles: - Minimum requirements for Microsoft Defender for Endpoint - Onboard devices and configure Microsoft Defender for Endpoint capabilities - Onboard Windows servers to the Defender for Endpoint service - New Windows Server 2012 R2 and 2016 functionality in the modern unified solution (See Is EDR in block mode supported on Windows Server 2016 and Windows Server 2012 R2?) |
| Microsoft Defender Antivirus | Devices must have Microsoft Defender Antivirus installed and running in either active mode or passive mode. Confirm Microsoft Defender Antivirus is in active or passive mode. |
| Cloud-delivered protection | Microsoft Defender Antivirus must be configured such that cloud-delivered protection is enabled. |
| Microsoft Defender Antivirus platform | Devices must be up to date. To confirm, using PowerShell, run the Get-MpComputerStatus cmdlet as an administrator. In the AMProductVersion line, you should see 4.18.2001.10 or above. To learn more, see Manage Microsoft Defender Antivirus updates and apply baselines. |
| Microsoft Defender Antivirus engine | Devices must be up to date. To confirm, using PowerShell, run the Get-MpComputerStatus cmdlet as an administrator. In the AMEngineVersion line, you should see 1.1.16700.2 or above. To learn more, see Manage Microsoft Defender Antivirus updates and apply baselines. |
Important
To get the best protection value, make sure your antivirus solution is configured to receive regular updates and essential features, and that your exclusions are configured. EDR in block mode respects exclusions that are defined for Microsoft Defender Antivirus, but not indicators that are defined for Microsoft Defender for Endpoint.
Microsoft recommends that you use roles with the fewest permissions. This helps improve security for your organization. Global Administrator is a highly privileged role that should be limited to emergency scenarios when you can't use an existing role.
See also
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender for Endpoint Tech Community.