Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Applies to:
- Defender for Endpoint on Mac
- Microsoft Defender for Endpoint Plan 1
- Microsoft Defender for Endpoint Plan 2
Use this article to set up policies for Defender for Endpoint on macOS using Jamf Pro.
Step 1: Get the Microsoft Defender for Endpoint onboarding package
Important
You must have an appropriate role assigned to view, manage, and onboard devices. For more information, see Manage access to Microsoft Defender XDR with Microsoft Entra global roles.
In the Microsoft Defender Portal, navigate to Settings > Endpoints > Onboarding.
Select macOS as the operating system and Mobile Device Management / Microsoft Intune as the deployment method.
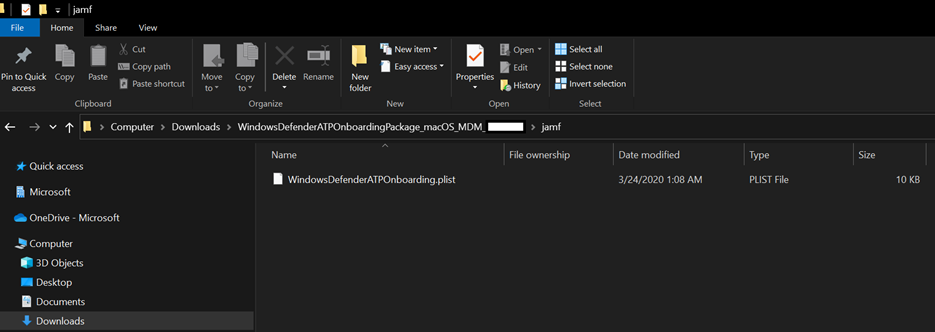
Select Download onboarding package (WindowsDefenderATPOnboardingPackage.zip).
Extract
WindowsDefenderATPOnboardingPackage.zip.Copy the file to your preferred location. For example,
C:\Users\JaneDoe_or_JohnDoe.contoso\Downloads\WindowsDefenderATPOnboardingPackage_macOS_MDM_contoso\Jamf\WindowsDefenderATPOnboarding.plist.
Step 2: Create a configuration profile in Jamf Pro using the onboarding package
Locate the file
WindowsDefenderATPOnboarding.plistfrom the previous section.Sign in to Jamf Pro, navigate to Computers > Configuration Profiles, and select New.
On the General tab, specify the following details:
- Name:
MDE onboarding for macOS - Description:
MDE EDR onboarding for macOS - Category:
None - Distribution Method:
Install Automatically - Level:
Computer Level
- Name:
Navigate to the Application & Custom Settings page, select Upload, and then select Add.
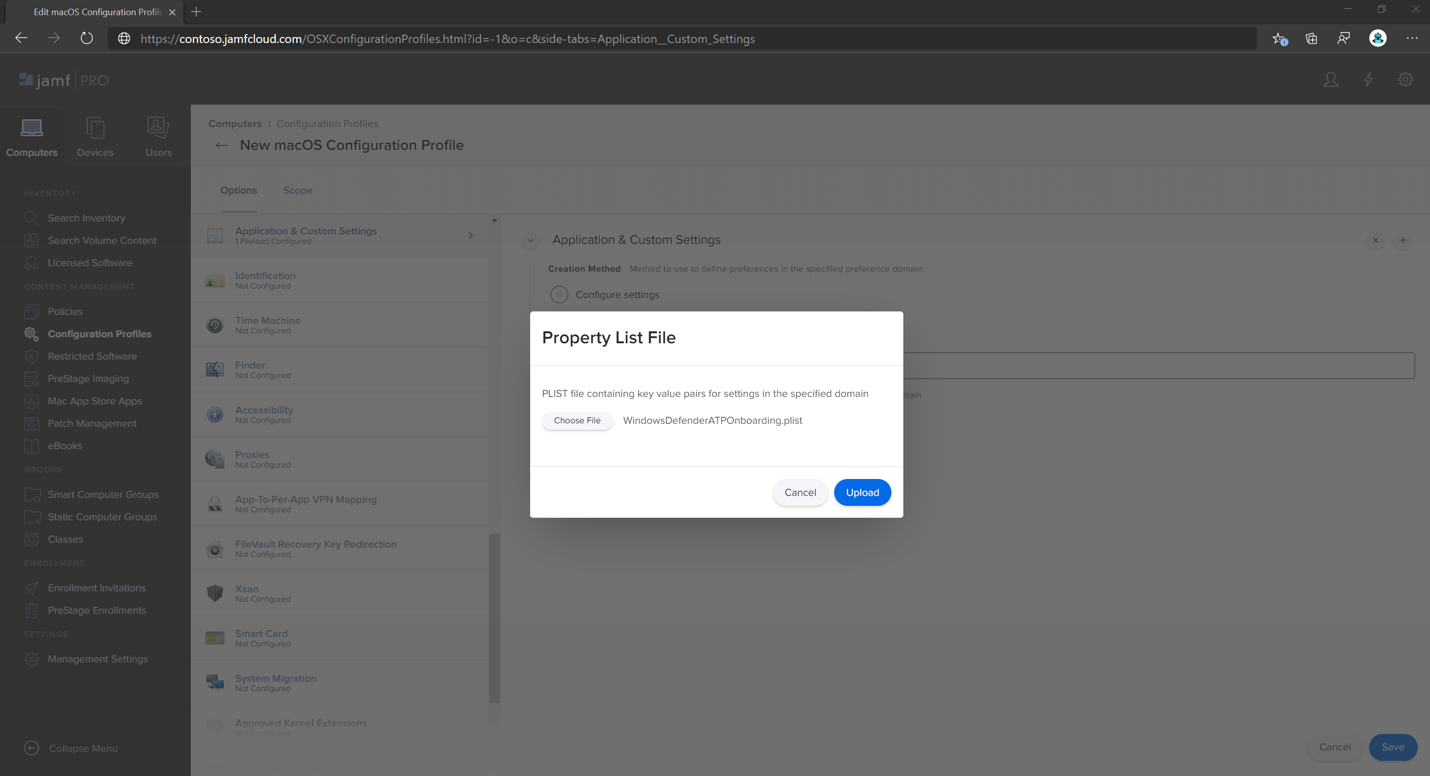
Select Upload File (PLIST file) then in Preference Domain, type
com.microsoft.wdav.atp.Select Open and select the onboarding file.
Select Upload.
Select the Scope tab.
Select the target computers.
Select Save.
Select Done.
Step 3: Configure Microsoft Defender for Endpoint settings
In this step, we go over Preferences so you can configure anti-malware and EDR policies using the Microsoft Defender portal (https://security.microsoft.com) or Jamf.
Important
Microsoft Defender for Endpoint Security Settings Management policies takes precedence over Jamf set (and other third party MDM) policies.
3a. Set policies using Microsoft Defender portal
Follow the guidance in Configure Microsoft Defender for Endpoint in Intune before setting the security policies using Microsoft Defender.
In the Microsoft Defender portal, go to Configuration management > Endpoint security policies > Mac policies > Create new policy.
Under Select Platform, select macOS.
Under Select Template, choose a template and select Create Policy.
Specify a name and description for the policy, and then select Next.
On the Assignments tab, assign the profile to a group where the macOS devices and/or users are located, or All Users and All devices.
For more information about managing security settings, see the following articles:
3b. Set policies using Jamf
You can either use Jamf Pro GUI to edit individual settings of the Microsoft Defender for Endpoint configuration, or use the legacy method by creating a configuration Plist in a text editor, and uploading it to Jamf Pro.
You must use exact com.microsoft.wdav as the Preference Domain. Microsoft Defender for Endpoint uses only this name and com.microsoft.wdav.ext to load its managed settings. (The com.microsoft.wdav.ext version can be used in rare cases when you prefer to use GUI method, but also need to configure a setting that hasn't been added to the schema yet.)
GUI method
Download the
schema.jsonfile from Defender's GitHub repository and save it to a local file:curl -o ~/Documents/schema.json https://raw.githubusercontent.com/microsoft/mdatp-xplat/master/macos/schema/schema.jsonCreate a new configuration profile. Under Computers, go to Configuration Profiles, and then, on the General tab, specify the following details:
- Name:
MDATP MDAV configuration settings - Description:
<blank\> - Category:
None (default) - Level:
Computer Level (default) - Distribution Method:
Install Automatically (default)
- Name:
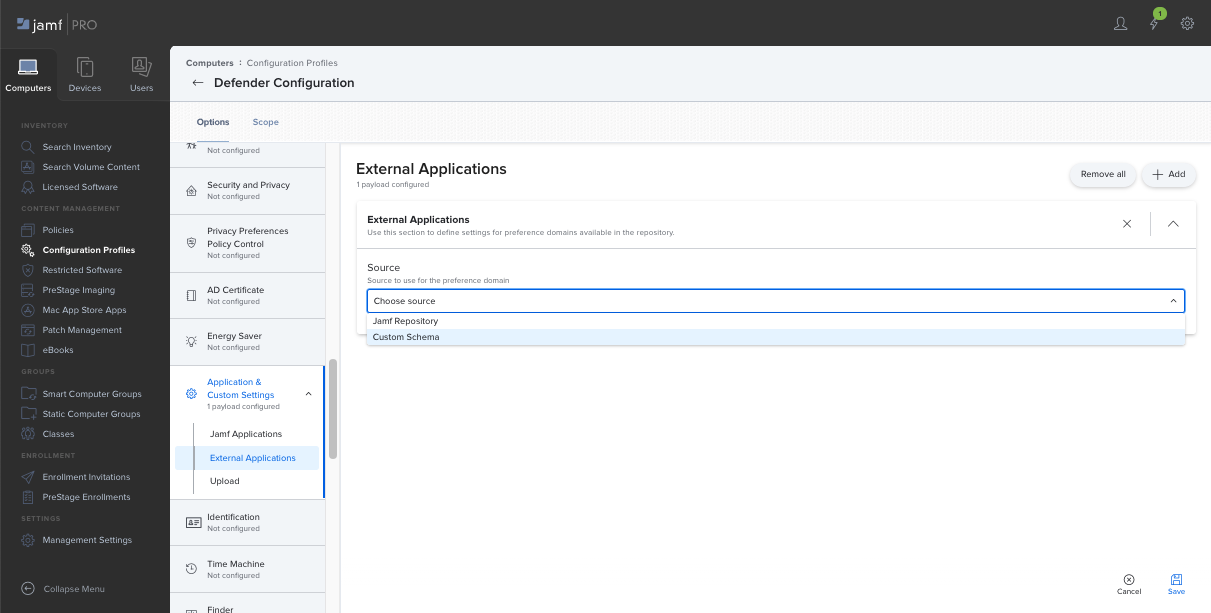
Scroll down to the Application & Custom Settings tab, select External Applications, select Add, and then use Custom Schema as the source for the preference domain.
Type
com.microsoft.wdavfor the Preference Domain, select Add Schema and then upload theschema.jsonfile downloaded on Step 1. Select Save.You can see all supported Microsoft Defender for Endpoint configuration settings under Preference Domain Properties. Select Add/Remove properties to select the settings that you want to be managed, and then select OK to save your changes. (Settings left unselected aren't included into the managed configuration, an end user can configure those settings on their machines.)
Change values of the settings to desired values. You can select More information to get documentation for a particular setting. (You can select Plist preview to inspect what the configuration plist. Select Form editor to return to the visual editor.)
Select the Scope tab.
Select Contoso's Machine Group. Select Add, then select Save.
Select Done. You see the new Configuration profile.
Microsoft Defender for Endpoint adds new settings over time. These new settings are added to the schema, and a new version is published to GitHub. To get updates, download an updated schema and edit your existing configuration profile. On the Application & Custom Settings tab, select Edit schema.
Legacy method
Use the following Microsoft Defender for Endpoint configuration settings:
enableRealTimeProtectionpassiveMode(This setting isn't turned on by default. If you're planning to run non-Microsoft antivirus software on Mac, set it totrue.)exclusionsexcludedPathexcludedFileExtensionexcludedFileNameexclusionsMergePolicyallowedThreats(EICAR is on the sample. If you're going through a proof-of-concept, remove it especially if you're testing EICAR.)disallowedThreatActionspotentially_unwanted_applicationarchive_bombcloudServiceautomaticSampleSubmissiontagshideStatusMenuIcon
For more information, see Property list for Jamf full configuration profile.
<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0"> <dict> <key>antivirusEngine</key> <dict> <key>enableRealTimeProtection</key> <true/> <key>passiveMode</key> <false/> <key>exclusions</key> <array> <dict> <key>$type</key> <string>excludedPath</string> <key>isDirectory</key> <false/> <key>path</key> <string>/var/log/system.log</string> </dict> <dict> <key>$type</key> <string>excludedPath</string> <key>isDirectory</key> <true/> <key>path</key> <string>/home</string> </dict> <dict> <key>$type</key> <string>excludedFileExtension</string> <key>extension</key> <string>pdf</string> </dict> <dict> <key>$type</key> <string>excludedFileName</string> <key>name</key> <string>cat</string> </dict> </array> <key>exclusionsMergePolicy</key> <string>merge</string> <key>allowedThreats</key> <array> <string>EICAR-Test-File (not a virus)</string> </array> <key>disallowedThreatActions</key> <array> <string>allow</string> <string>restore</string> </array> <key>threatTypeSettings</key> <array> <dict> <key>key</key> <string>potentially_unwanted_application</string> <key>value</key> <string>block</string> </dict> <dict> <key>key</key> <string>archive_bomb</string> <key>value</key> <string>audit</string> </dict> </array> <key>threatTypeSettingsMergePolicy</key> <string>merge</string> </dict> <key>cloudService</key> <dict> <key>enabled</key> <true/> <key>diagnosticLevel</key> <string>optional</string> <key>automaticSampleSubmission</key> <true/> </dict> <key>edr</key> <dict> <key>tags</key> <array> <dict> <key>key</key> <string>GROUP</string> <key>value</key> <string>ExampleTag</string> </dict> </array> </dict> <key>userInterface</key> <dict> <key>hideStatusMenuIcon</key> <false/> </dict> </dict> </plist>Save the file as
MDATP_MDAV_configuration_settings.plist.In the Jamf Pro dashboard, open Computers, and their Configuration Profiles. Select New and switch to the General tab.
On the General tab, specify the following details:
- Name:
MDATP MDAV configuration settings - Description:
<blank> - Category:
None (default) - Distribution Method:
Install Automatically (default) - Level:
Computer Level (default)
- Name:
In Application & Custom Settings, select Configure.
Select Upload File (PLIST file).
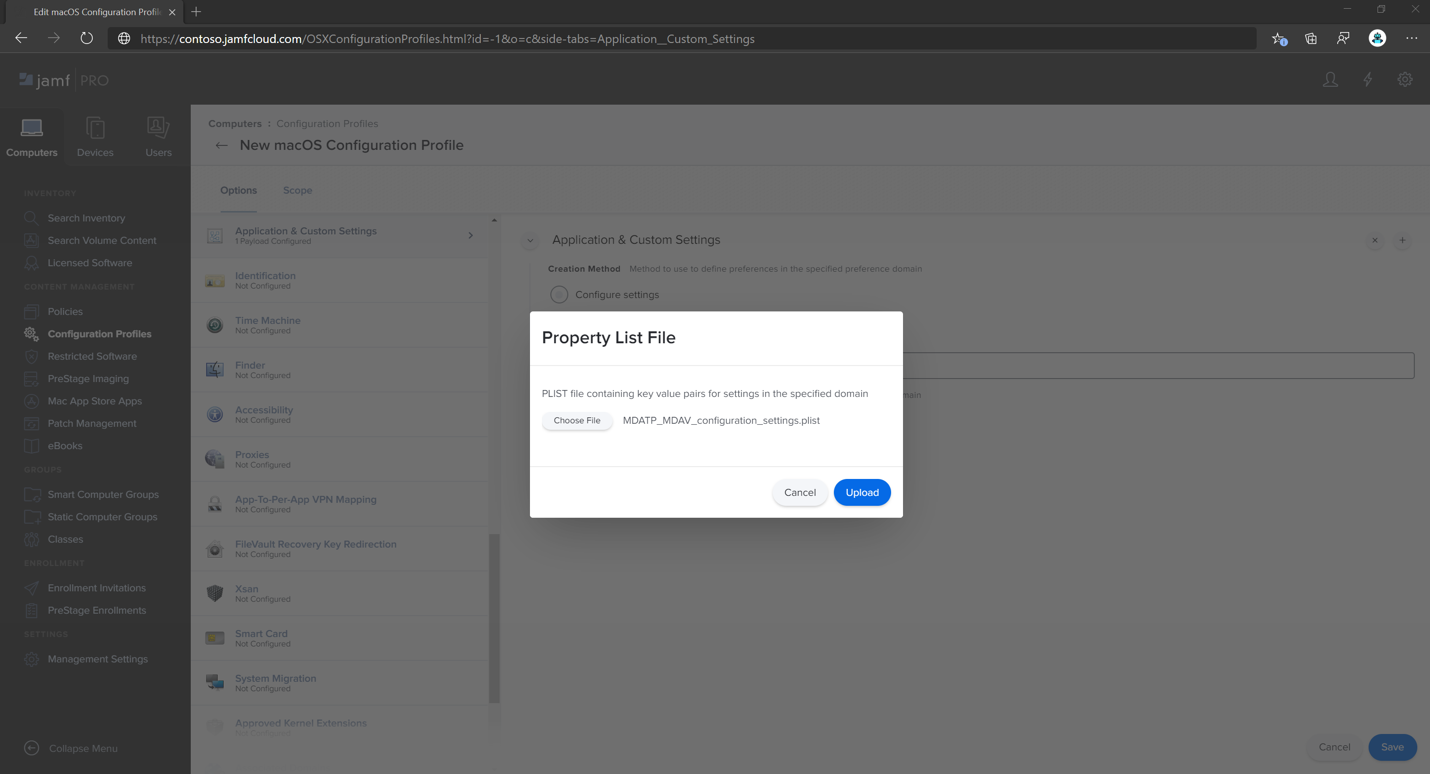
In Preferences Domain, type
com.microsoft.wdav, and then select Upload PLIST File.Select Choose File.
Select the MDATP_MDAV_configuration_settings.plist, and then select Open.
Select Upload.
Select Save.
The file is uploaded.
Select the Scope tab.
Select Contoso's Machine Group. Select Add, then select Save.
Select Done. You see the new Configuration profile.
Step 4: Configure notifications settings
Note
These steps are applicable on macOS 11 (Big Sur) or later. Even though Jamf supports notifications on macOS version 10.15 or later, Defender for Endpoint on macOS requires macOS 11 or later.
In the Jamf Pro dashboard, select Computers, then Configuration Profiles.
Select New, and then, on the General tab, for Options, specify the following details:
On the Notifications tab, select Add, and specify the following values:
- Bundle ID:
com.microsoft.wdav.tray - Critical Alerts: Select Disable
- Notifications: Select Enable
- Banner alert type: Select Include and Temporary (default)
- Notifications on lock screen: Select Hide
- Notifications in Notification Center: Select Display
- Badge app icon: Select Display
- Bundle ID:
On the Notifications tab, select Add one more time, and then scroll down to New Notifications Settings.
- Bundle ID:
com.microsoft.autoupdate.fba
- Bundle ID:
Configure the rest of the settings to the same values mentioned earlier
Now you have two tables with notification configurations, one for Bundle ID: com.microsoft.wdav.tray, and another for Bundle ID: com.microsoft.autoupdate.fba. While you can configure alert settings per your requirements, Bundle IDs must be exactly the same as described before, and Include switch must be On for Notifications.
Select the Scope tab, and then select Add.
Select Contoso's Machine Group. Select Add, and then select Save.
Select Done. You should see the new Configuration profile.
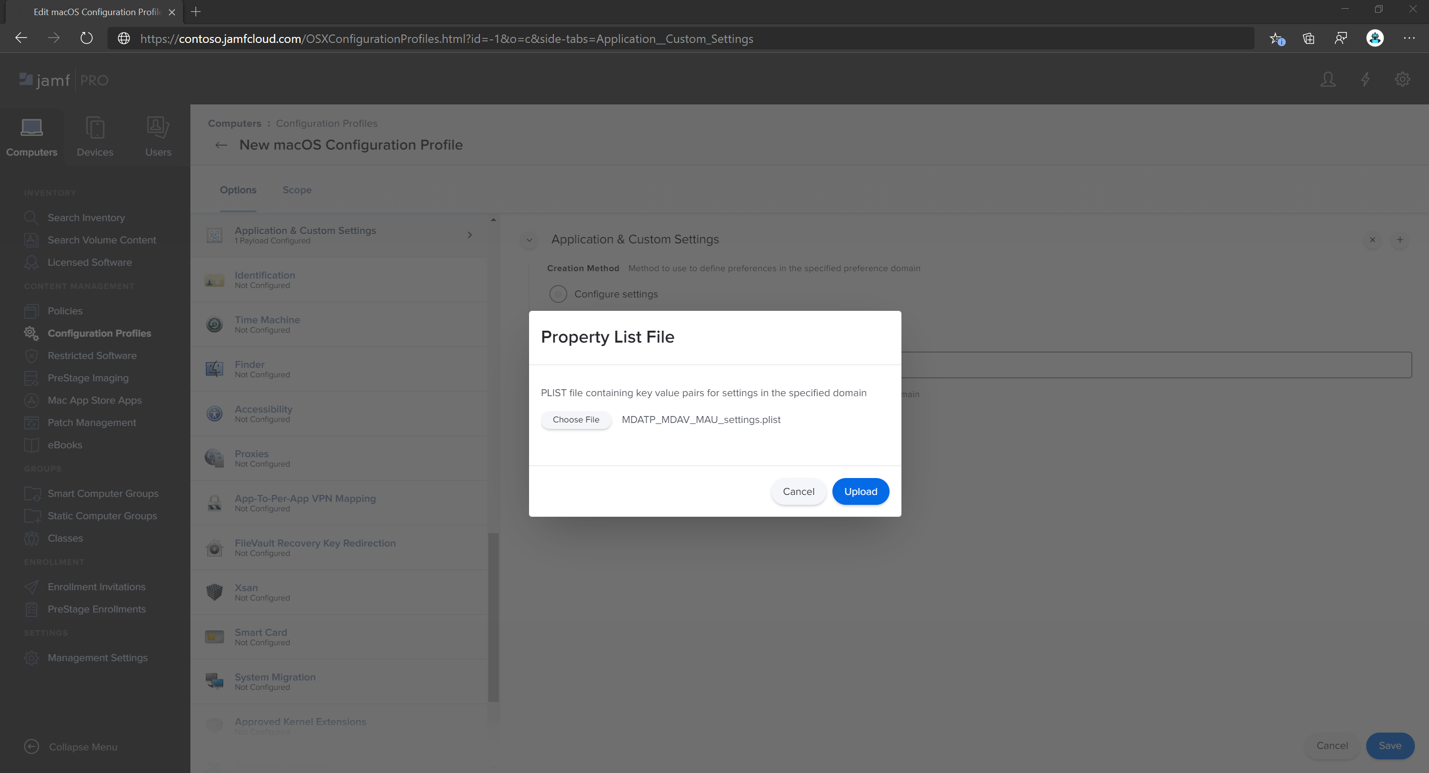
Step 5: Configure Microsoft AutoUpdate (MAU)
Use the following Microsoft Defender for Endpoint configuration settings:
<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0"> <dict> <key>ChannelName</key> <string>Current</string> <key>HowToCheck</key> <string>AutomaticDownload</string> <key>EnableCheckForUpdatesButton</key> <true/> <key>DisableInsiderCheckbox</key> <false/> <key>SendAllTelemetryEnabled</key> <true/> </dict> </plist>Save it as
MDATP_MDAV_MAU_settings.plist.In the Jamf Pro dashboard, select General.
On the General tab, specify the following details:
- Name:
MDATP MDAV MAU settings - Description:
Microsoft AutoUpdate settings for MDATP for macOS - Category:
None (default) - Distribution Method:
Install Automatically (default) - Level:
Computer Level (default)
- Name:
In Application & Custom Settings select Configure.
Select Upload File (PLIST file).
In Preference Domain type
com.microsoft.autoupdate2, and then select Upload PLIST File.Select Choose File.
Select MDATP_MDAV_MAU_settings.plist.
Select Save.
Select the Scope tab.
Select Add.
Select Done.
Step 6: Grant full disk access to Microsoft Defender for Endpoint
In the Jamf Pro dashboard, select Configuration Profiles.
Select + New.
On the General tab, specify the following details:
- Name:
MDATP MDAV - grant Full Disk Access to EDR and AV - Description:
On macOS 11 (Big Sur) or later, the new Privacy Preferences Policy Control - Category:
None - Distribution method:
Install Automatically - Level:
Computer level
- Name:
In Configure Privacy Preferences Policy Control select Configure.
In Privacy Preferences Policy Control, enter the following details:
- Identifier:
com.microsoft.wdav - Identifier Type:
Bundle ID - Code Requirement:
identifier "com.microsoft.wdav" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = UBF8T346G9
- Identifier:
Select + Add.
- Under App or service, select SystemPolicyAllFiles.
- Under access, select Allow.
Select Save (not the one at the bottom right).
Select the
+sign next to App Access to add a new entry.Enter the following details:
- Identifier:
com.microsoft.wdav.epsext - Identifier Type:
Bundle ID - Code Requirement:
identifier "com.microsoft.wdav.epsext" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = UBF8T346G9
- Identifier:
Select + Add.
- Under App or service, select SystemPolicyAllFiles.
- Under access, select Allow.
- Select Save (not the one at the bottom right).
- Select the Scope tab.
- Select + Add.
- Select Computer Groups, and under Group Name, select Contoso's MachineGroup.
Alternatively, you can download fulldisk.mobileconfig and upload it to Jamf Configuration Profiles as described in Deploying Custom Configuration Profiles using Jamf Pro|Method 2: Upload a Configuration Profile to Jamf Pro.
Note
Full Disk Access granted through Apple MDM Configuration Profile isn't reflected in System Settings => Privacy & Security => Full Disk Access.
Step 7: Approve System extensions for Microsoft Defender for Endpoint
In the Configuration Profiles, select + New.
On the General tab, specify the following details:
- Name:
MDATP MDAV System Extensions - Description:
MDATP system extensions - Category:
None - Distribution Method:
Install Automatically - Level:
Computer Level
- Name:
In System Extensions select Configure.
In System Extensions, enter the following details:
- Display Name:
Microsoft Corp. System Extensions - System Extension Types:
Allowed System Extensions - Team Identifier:
UBF8T346G9 - Allowed System Extensions:
com.microsoft.wdav.epsextcom.microsoft.wdav.netext
- Display Name:
Select the Scope tab.
Select + Add.
Select Computer Groups > under Group Name > select Contoso's Machine Group.
Select + Add.
Select Save.
Select Done.
Step 8: Configure Network Extension
As part of the Endpoint Detection and Response capabilities, Microsoft Defender for Endpoint on macOS inspects socket traffic and reports this information to the Microsoft Defender portal.
Note
These steps are applicable on macOS 11 (Big Sur) or later. Even though Jamf supports notifications on macOS version 10.15 or later, Defender for Endpoint on macOS requires macOS 11 or later.
In the Jamf Pro dashboard, select Computers, then Configuration Profiles.
Select New, and enter the following details for Options:
On the General tab, specify the following values:
- Name:
Microsoft Defender Network Extension - Description:
macOS 11 (Big Sur) or later - Category:
None *(default)* - Distribution Method:
Install Automatically *(default)* - Level:
Computer Level *(default)*
- Name:
On the Content Filter tab, specify the following values:
- Filter Name:
Microsoft Defender Content Filter - Identifier:
com.microsoft.wdav - Leave Service Address, Organization, User Name, Password, Certificate blank (Include isn't* selected)
- Filter Order:
Inspector - Socket Filter:
com.microsoft.wdav.netext - Socket Filter Designated Requirement:
identifier "com.microsoft.wdav.netext" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = UBF8T346G9 - Leave Network Filter fields blank (Include isn't* selected)
Note that Identifier, **Socket Filter, and Socket Filter Designated Requirement exact values as specified earlier.
- Filter Name:
Select the Scope tab.
Select + Add. Select Computer Groups, and then under Group Name, select Contoso's Machine Group. Then select + Add.
Select Save.
Select Done.
Alternatively, you can download netfilter.mobileconfig and upload it to Jamf Configuration Profiles as described in Deploying Custom Configuration Profiles using Jamf Pro|
Step 9: Configure Background Services
Caution
macOS 13 (Ventura) contains new privacy enhancements. Beginning with this version, by default, applications can't run in background without explicit consent. Microsoft Defender for Endpoint must run its daemon process in background.
This configuration profile grants Background Service permissions to Microsoft Defender for Endpoint. If you previously configured Microsoft Defender for Endpoint through Jamf, we recommend you update the deployment with this configuration profile.
Download background_services.mobileconfig from our GitHub repository.
Upload downloaded mobileconfig to Jamf Configuration Profiles as described in Deploying Custom Configuration Profiles using Jamf Pro|Method 2: Upload a Configuration Profile to Jamf Pro.
Step 10: Grant Bluetooth Permissions
Caution
macOS 14 (Sonoma) contains new privacy enhancements. Beginning with this version, by default, applications can't access Bluetooth without explicit consent. Microsoft Defender for Endpoint uses it if you configure Bluetooth policies for Device Control.
Download bluetooth.mobileconfig from GitHub repository.
Warning
Current version of Jamf Pro doesn't support this kind of payload yet. If you upload this mobileconfig as-is, Jamf Pro removes unsupported payload, and it fails to apply to client machines. You need to sign downloaded mobileconfig first, after that Jamf Pro considers it "sealed" and won't tamper with it. See instructions below:
You need to have at least one signing certificate installed into your KeyChain, even a self-signed certificate works. You can inspect what you have with:
> /usr/bin/security find-identity -p codesigning -v 1) 70E46A47F552EA8D58521DAC1E7F5144BA3012BC "DevCert" 2) 67FC43F3FAB77662BB7688C114585BAA37CA8175 "Mac Developer: John Doe (1234XX234)" 3) E142DFD879E5EB60FA249FB5B24CEAE3B370394A "Apple Development: Jane Doe 7XX7778888)" 4) 21DE31645BBF1D9F5C46E82E87A6968111E41C75 "Apple Development: me@example.com (8745XX123)" 4 valid identities found
Choose any of them, and provide the quoted text as the -N parameter:
/usr/bin/security cms -S -N "DevCert" -i bluetooth.mobileconfig -o bluetooth-signed.mobileconfig
Now you can upload the generated bluetooth-signed. Mobileconfig to Jamf Pro as described in Deploying Custom Configuration Profiles using Jamf Pro|Method 2: Upload a Configuration Profile to Jamf Pro.
Note
Bluetooth granted through Apple MDM Configuration Profile isn't reflected in System Settings => Privacy & Security => Bluetooth.
Step 11: Schedule scans with Microsoft Defender for Endpoint on macOS
Follow the instructions in Schedule scans with Microsoft Defender for Endpoint on macOS.
Step 12: Deploy Microsoft Defender for Endpoint on macOS
Note
In the steps that follow, the name of the .pkg file and the Display Name values are examples. In these examples, 200329 represents the date on which the
package and policy were created (in yymmdd format), and v100.86.92 represents the version of the Microsoft Defender application that is being deployed.
These values should be updated to conform with the naming convention you use in your environment for Packages and Policies.
Navigate to where you saved
wdav.pkg.Rename it to
wdav_MDM_Contoso_200329.pkg.Open the Jamf Pro dashboard.
Select your computer and select the gear icon at the top, and then select Computer Management.
In Packages, select + New.
On the General tab, in New Package, specify the following details:
- Display Name: Leave it blank for now. Because it's reset when you choose your pkg.
- Category:
None (default) - Filename:
Choose File
Open the file and point it to
wdav.pkgorwdav_MDM_Contoso_200329.pkg.Select Open. Set the Display Name to Microsoft Defender Advanced Threat Protection and Microsoft Defender Antivirus.
- Manifest File isn't required. Microsoft Defender for Endpoint works without Manifest File.
- Options tab: Keep default values.
- Limitations tab: Keep default values.
Select Save. The package is uploaded to Jamf Pro.
It can take a few minutes for the package to be available for deployment.
Navigate to the Policies page.
Select + New to create a new policy.
In General, for the Display name, use
MDATP Onboarding Contoso 200329 v100.86.92 or later.Select Recurring Check-in.
Select Save. Then select Packages, and then selectConfigure.
Select the Add button next to Microsoft Defender Advanced Threat Protection and Microsoft Defender Antivirus.
Select Save.
Create a smart group for machines with Microsoft Defender profiles.
For a better user experience, configuration profiles to enrolled machines must be installed before Microsoft Defender's package. In most cases JamF Pro pushes configuration profiles immediately, and those policies are executed after some time (that is, during check-in). However, in some cases, configuration profiles deployment can be deployed with a significant delay (that is, if a user's machine is locked).
Jamf Pro provides a way to ensure the correct order. You can create a smart group for machines that already received Microsoft Defender's configuration profile, and install Microsoft Defender's package only to those machines (and as soon as they receive this profile).
Follow these steps:
Create a smart group. In a new browser window, open Smart Computers Groups.
Select New, and give your group a name.
On the Criteria tab, select Add, and then select Show Advanced Criteria.
Select Profile Name as a criterion, and use the name of a previously created configuration profile as the value:
Select Save.
Go back to the window where you configure a package policy.
Select the Scope tab.
Select the target computers.
Under Scope, select Add.
Switch to the Computer Groups tab. Find the smart group you created, and then select Add.
- If you want users to install Defender for Endpoint voluntarily (or on demand), select Self-Service.
- Select Done.
Configuration profile scope
Jamf requires you to define a set of machines for a configuration profile. You need to make sure that all machines receiving Defender's package, also receive all configuration profiles listed above.
Warning
Jamf supports Smart Computer Groups that allow deploying, such as configuration profiles or policies to all machines matching certain criteria evaluated dynamically. It's a powerful concept that is widely used for configuration profiles distribution.
However, keep in mind that these criteria shouldn't include presence of Defender on a machine. While using this criterion might sound logical, it creates problems that are difficult to diagnose.
Defender relies on all these profiles at the moment of its installation.
Making configuration profiles depending on Defender's presence effectively delays deployment of configuration profiles, and results in an initially unhealthy product and/or prompts for manual approval of certain application permissions, that are otherwise auto approved by profiles. Deploying a policy with Microsoft Defender's package after deploying configuration profiles ensures the end user's best experience, because all required configurations will be applied before the package installs.
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender for Endpoint Tech Community.