Security baselines assessment
Applies to:
- Microsoft Defender Vulnerability Management
- Microsoft Defender XDR
- Microsoft Defender for Servers Plan 2
Note
To use this feature you'll require Microsoft Defender Vulnerability Management Standalone or if you're already a Microsoft Defender for Endpoint Plan 2 customer, the Defender Vulnerability Management add-on.
Instead of running never-ending compliance scans, security baselines assessment helps you to continuously and effortlessly monitor your organization's security baselines compliance and identify changes in real time.
A security baseline profile is a customized profile that you can create to assess and monitor endpoints in your organization against industry security benchmarks. When you create a security baseline profile, you're creating a template that consists of multiple device configuration settings and a base benchmark to compare against.
Security baselines provide support for Center for Internet Security (CIS) benchmarks for Windows 10, Windows 11, and Windows Server 2008 R2 and above, as well as Security Technical Implementation Guides (STIG) benchmarks for Windows 10 and Windows Server 2019.
Note
The benchmarks currently only support Group Policy Object (GPO) configurations and not Microsoft Configuration Manager (Intune).
Tip
Did you know you can try all the features in Microsoft Defender Vulnerability Management for free? Find out how to sign up for a free trial.
Get started with security baselines assessment
Go to Vulnerability management > Baselines assessment in the Microsoft Defender portal.
Select the Profiles tab at the top, then select the Create profile button.
Enter a name and description for your security baselines profile and select Next.
On the Baseline profile scope page set the profile settings such as software, base benchmark (CIS or STIG), and the compliance level and select Next.
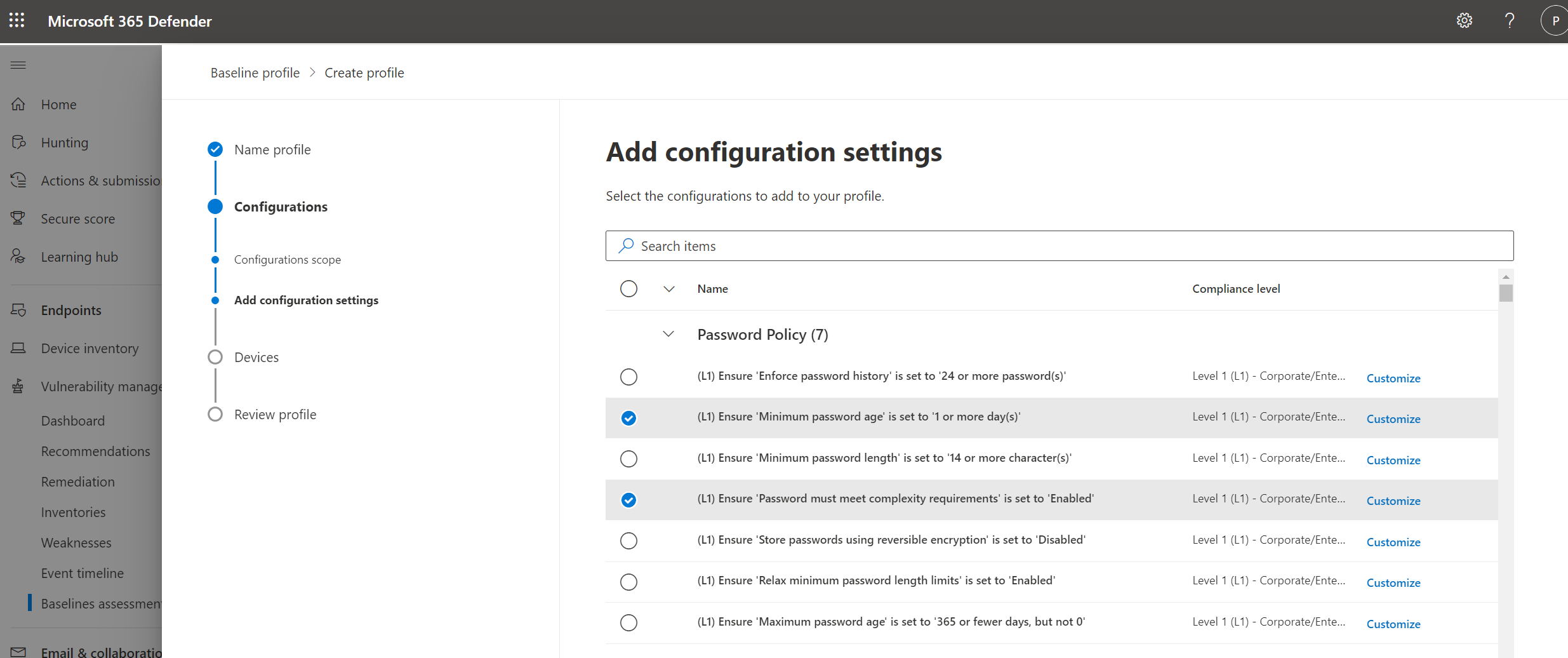
Select the configurations you want to include in the profile.
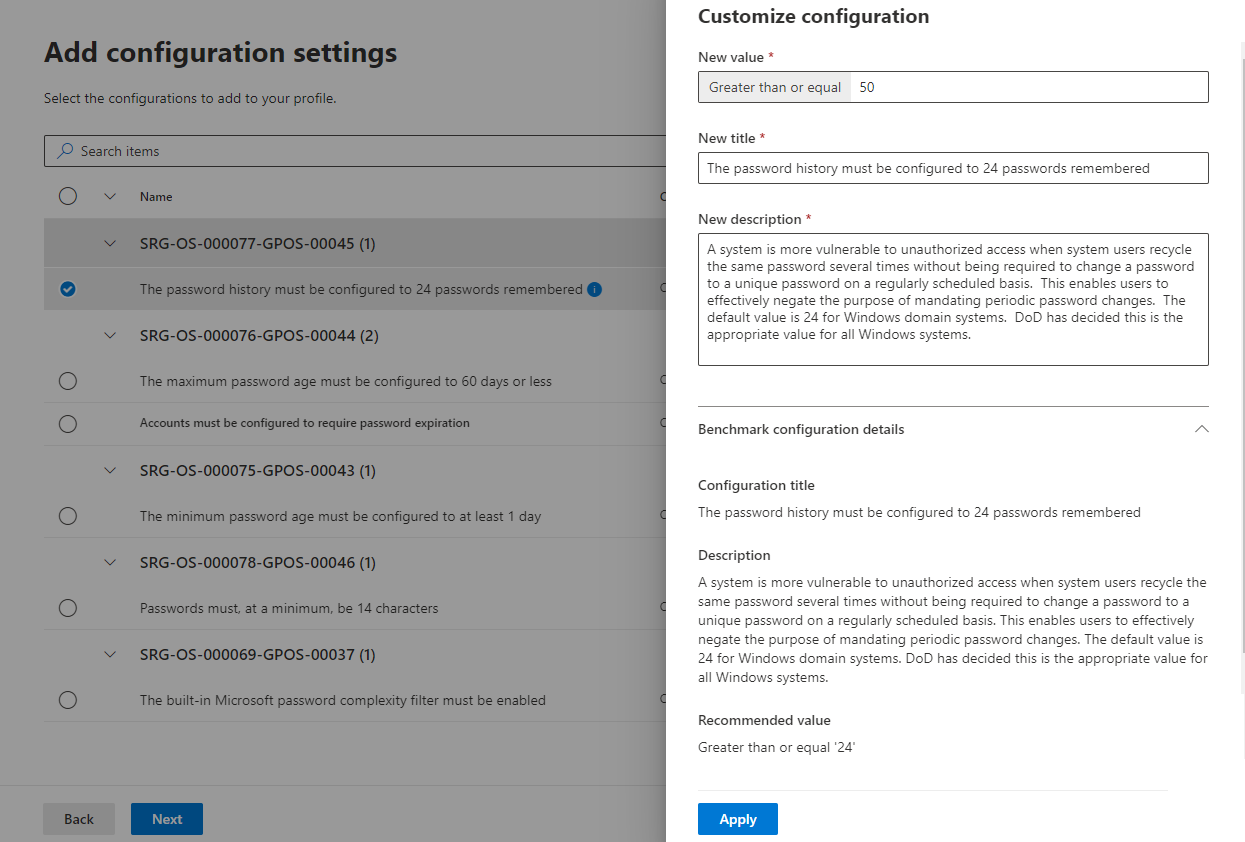
Select Customize if you want to change the threshold configuration value for your organization.
Select Next to choose the device groups and device tags you want to include in the baseline profile. The profile will be automatically applied to devices added to these groups in the future.
Select Next to review the profile.
Select Submit to create your profile.
On the final page, select View profile page to see the assessment results.
Note
You can create multiple profiles for the same operating system with various customizations.
When you customize a configuration an icon will appear beside it to indicate that it has been customized and is no longer using the recommended value. Select the reset button to revert to the recommended value.
Useful icons to be aware of:
 - This configuration has been customized before. When creating a new profile if you select Customize, you'll see the available variations you can choose from.
- This configuration has been customized before. When creating a new profile if you select Customize, you'll see the available variations you can choose from.
 - This configuration has been customized and is not using the default value.
- This configuration has been customized and is not using the default value.
Security baselines assessment overview
On the security baselines assessment overview page you can view device compliance, profile compliance, top failing devices and top misconfigured devices.
Review security baseline profile assessment results
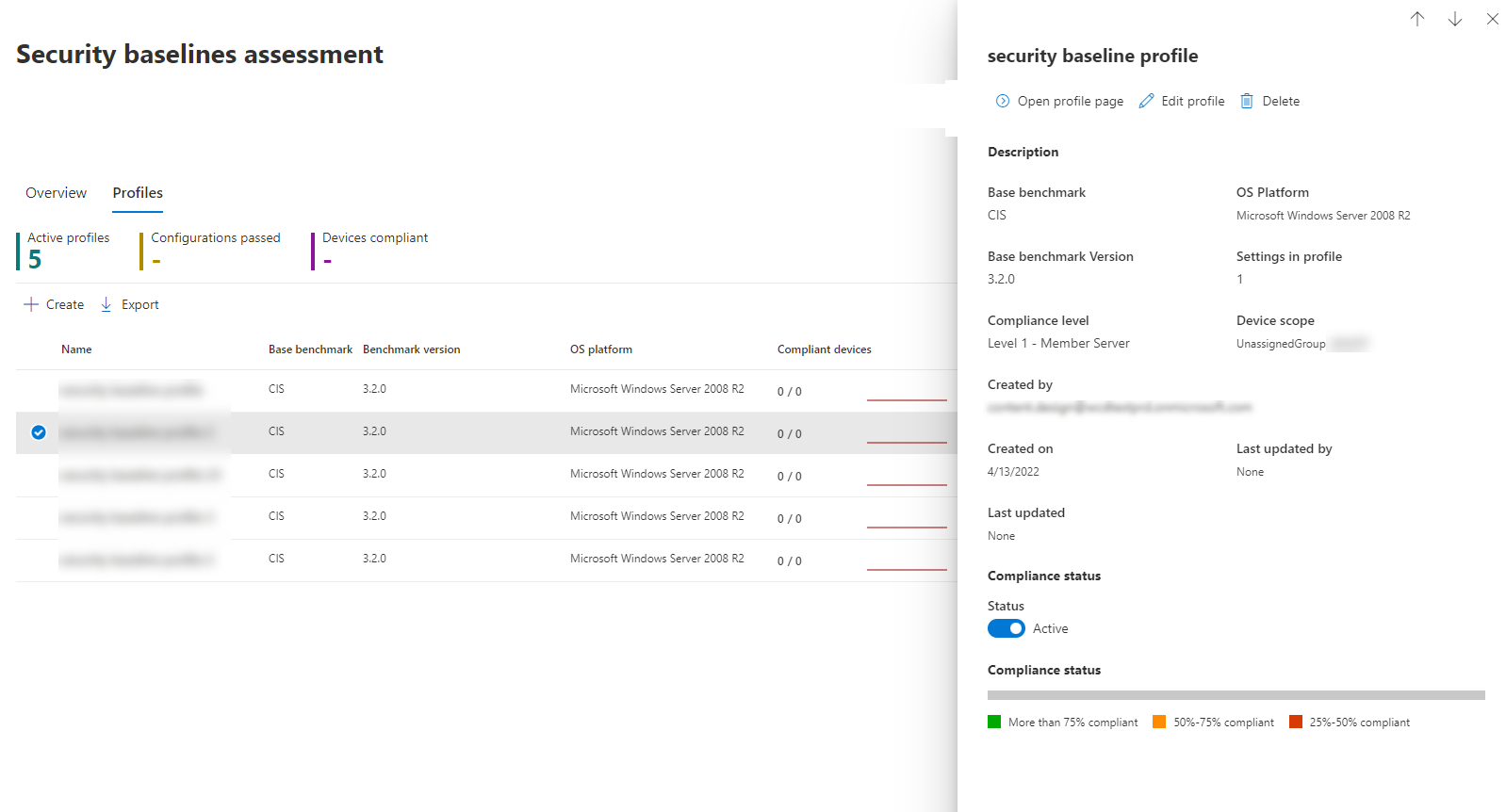
In the Profiles page, select any of your profiles to open a flyout with additional information.
Select Open profile page. The profile page contains two tabs Configurations and Devices.
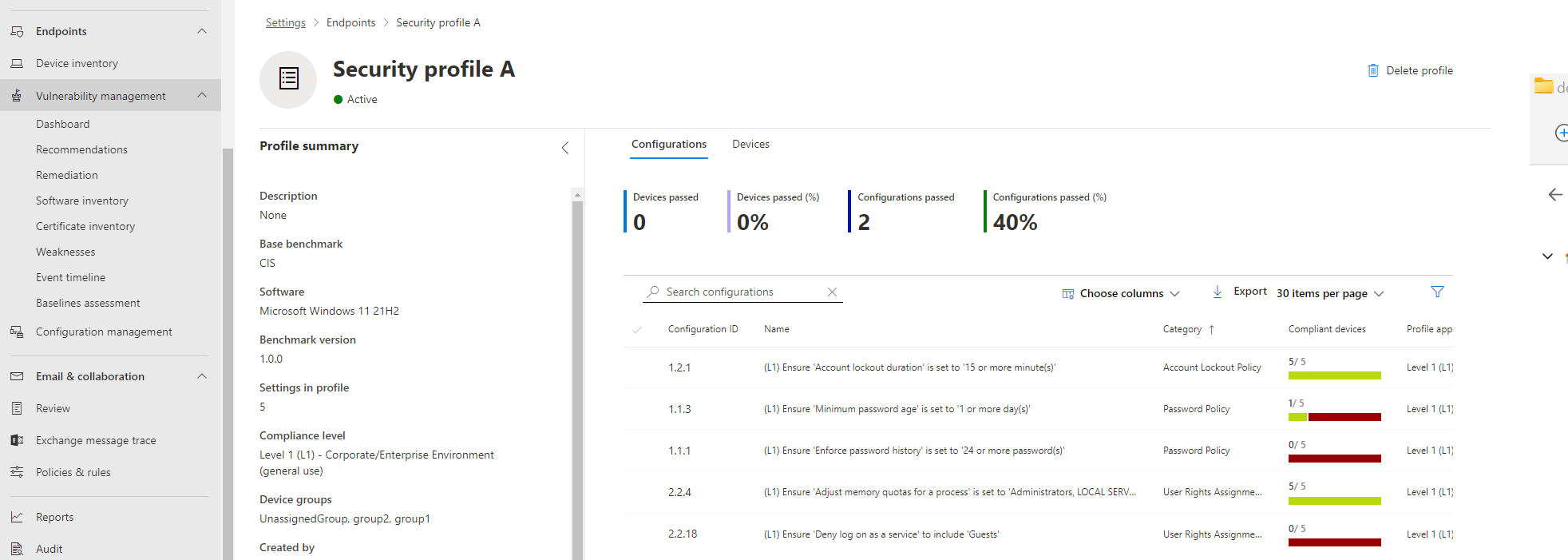
View by configuration
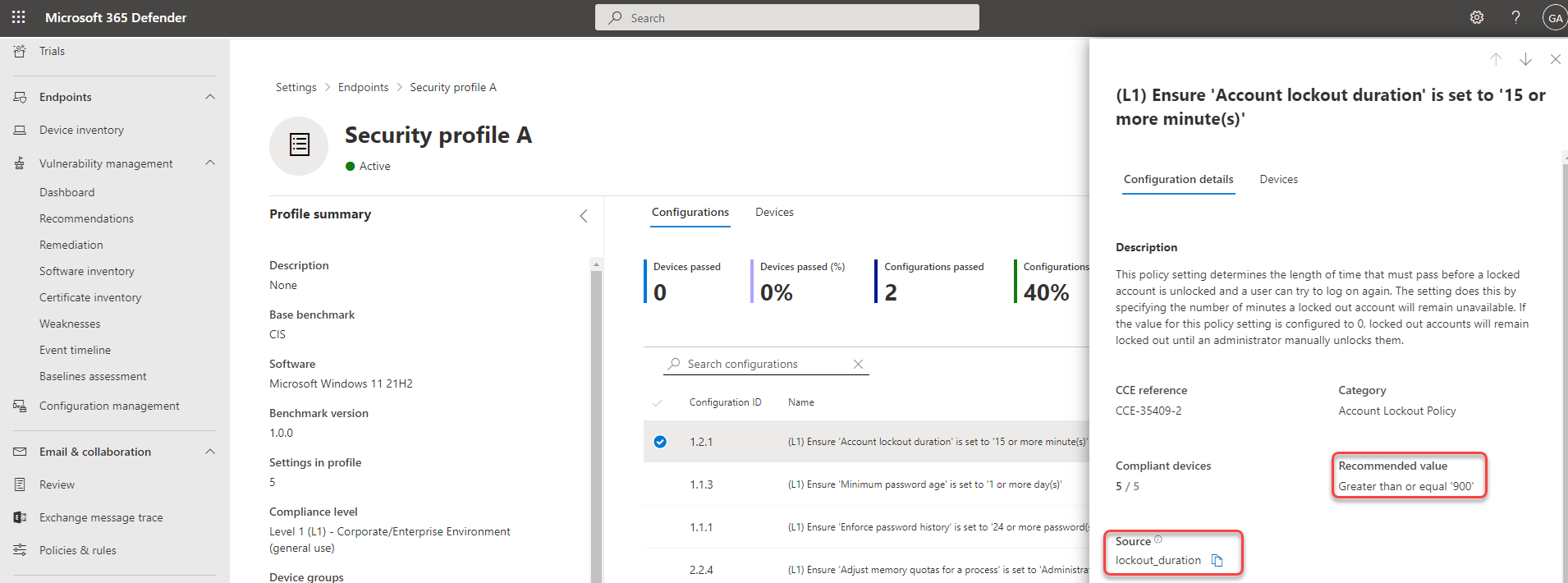
In the Configurations tab, you can review the list of configurations and assess their reported compliance state.
By selecting a configuration in the list, you'll see a flyout with details for the policy setting, including the recommended value (the expected value range for a device to be considered compliant) and the source used to determine the current device settings.
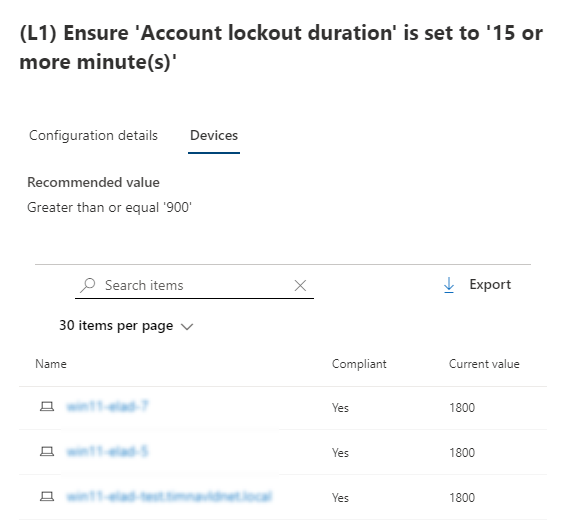
The Devices tab shows a list of all applicable devices and their compliance state against this specific configuration. For each device, you can use the current value detected to see why it's compliant or non compliant.
View by device
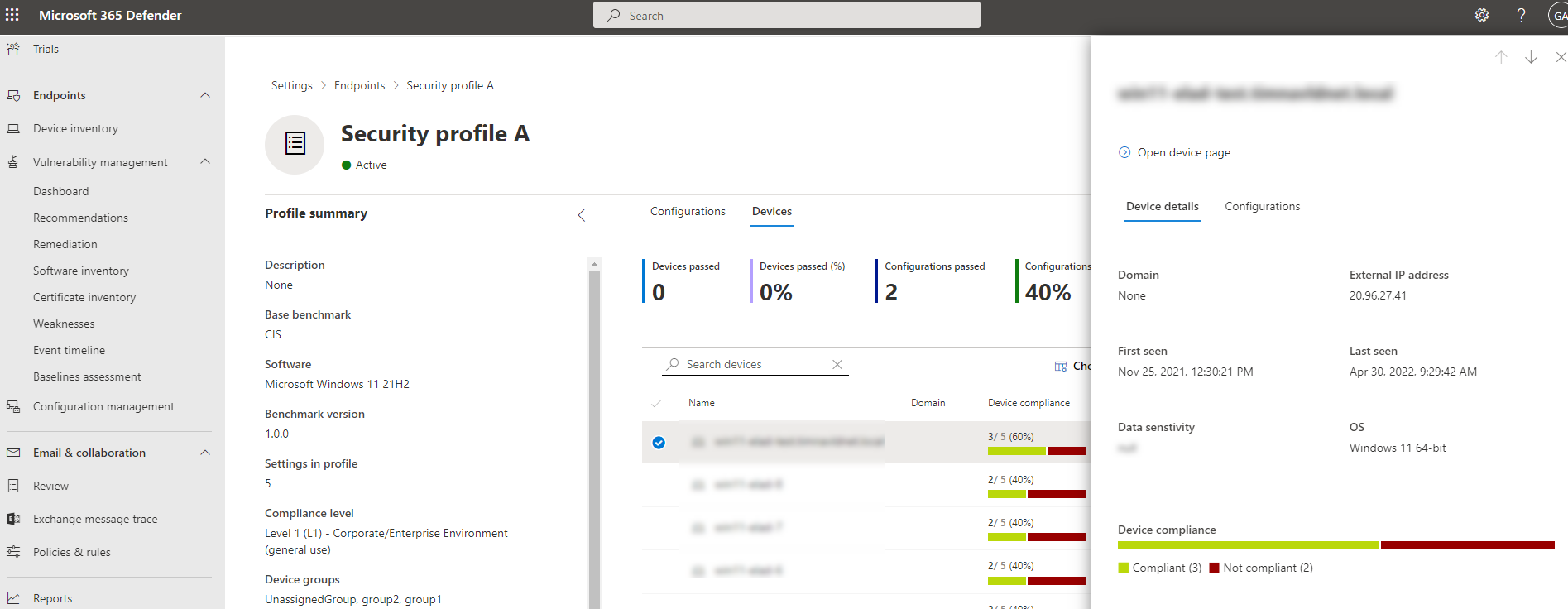
In the main Devices tab, you can review the list of devices and assess their reported compliance state.
By selecting a device in the list, you'll see a flyout with additional details.
Select the Configuration tab to view the compliance of this specific device against all the profile configurations.
At the top of the device side panel, select Open device page to go to the device page in the device inventory. The device page displays the Baseline compliance tab that provides granular visibility into the compliance of the device.
By selecting a configuration in the list, you'll see a flyout with compliance details for the policy setting on this device.
Create and manage exceptions
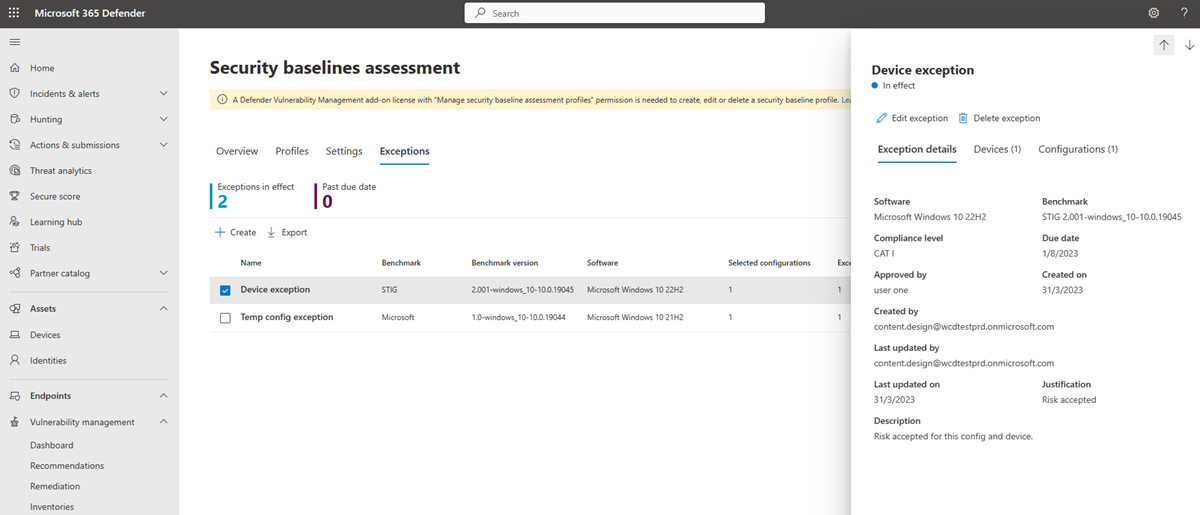
You may have cases where you don't want to assess specific configurations on certain devices. For example, a device could be under third party control or it could have an alternate mitigation already in place. In these situations, you can add exceptions to exclude the assessment of specific configurations on a device.
Devices included in exceptions won't be assessed for the specified configurations in the baseline profiles. This means it won't affect an organization's metrics and score, and it can help provide organizations with a clearer view of their compliance.
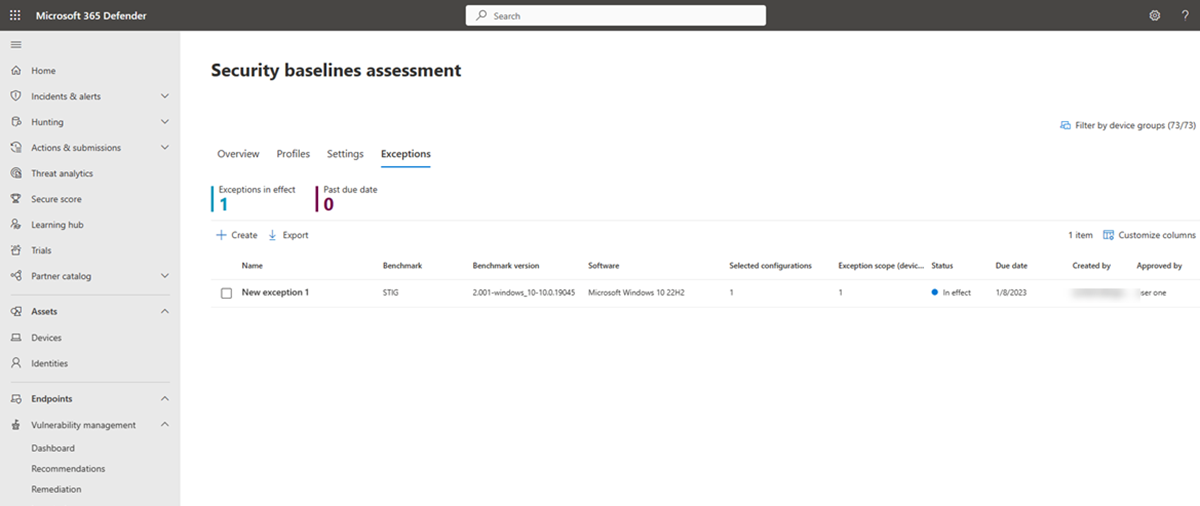
To view exceptions:
- Go to Vulnerability management > Baselines assessment in the Microsoft Defender portal.
- Select the Exceptions tab at the top
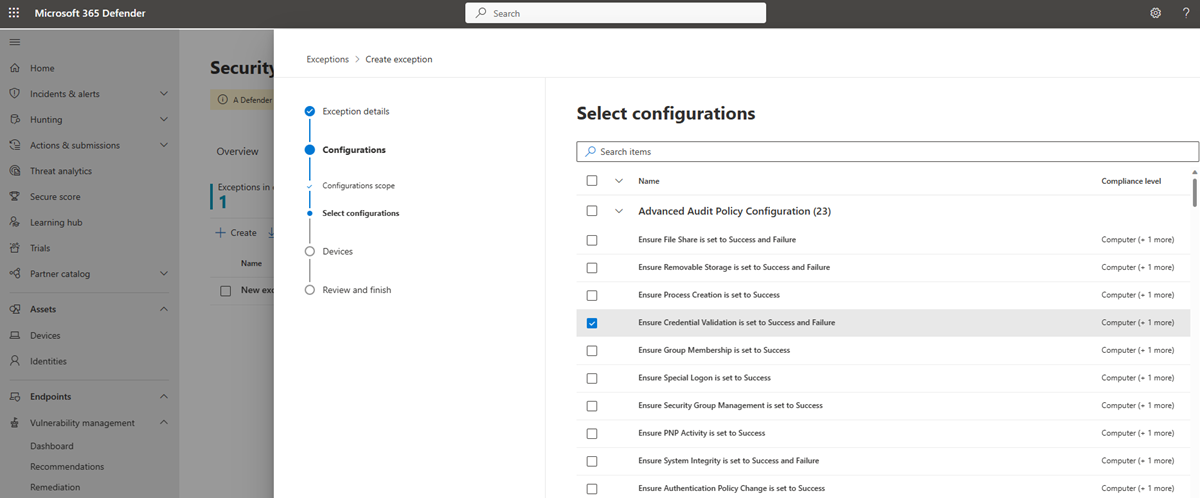
To add a new exception:
On the Exceptions tab select the Create button.
Fill in the requested details, including the justification reason, and duration.
Select Next.
On the Configuration scope page choose the software, base benchmark, and the compliance level and select Next.
Select the configurations you want to add to the exception.
Select Next to choose the devices you want to include in the exception. The exception will be automatically applied to devices.
Select Next to review the exception.
Select Submit to create your exception.
On the final page, select View all exceptions to return to the exceptions page.
In the Exceptions page, select any of your exceptions to open a flyout pane where you can see the status, edit or delete your exception:
Use advanced hunting
You can run advanced hunting queries on the following tables to gain visibility on security baselines in your organization:
- DeviceBaselineComplianceProfiles: provides details on created profiles.
- DeviceBaselineComplianceAssessment: device compliance related information.
- DeviceBaselineComplianceAssessmentKB: general settings for CIS and STIG benchmarks (not related to any device).
Related articles
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for