Strengthen your security posture - Assess and protect
Welcome to Phase 2 of Strengthen your security posture: Assess and protect.
Central to understanding your security posture is having a comprehensive inventory of all your assets. This article describes capabilities you can use to get an accurate view of the assets in your network and ways to help you protect them.
| Capability | Description | Get started |
|---|---|---|
| Assess your devices | Use the device inventory page in Microsoft Defender for Endpoint to get a comprehensive view of the devices discovered in your organization. Explore the information available like the risk level, platform information, and the onboarding status of a device. Use the filters available to customize your view. | Device inventory |
| Assign device value | Every device can potentially pose a risk to your organization but the impact of some devices being compromised compared to others can vary. You might have devices that belong to people who have access to sensitive, proprietary, or high priority information, this means the impact could be high if these devices are compromised. In contrast, devices that are only used for internet access with no data could be classified as having a lower risk. Identifying and assigning value to your devices can help identify how vulnerable your organization is to cybersecurity threats. How assets affect your vulnerability is reflected in your exposure score in the Microsoft Defender portal. Devices assigned as "high value" receive more weight meaning your score will be higher. |
Assign device value |
| Onboard newly discovered devices | Devices that have been discovered, but aren't yet onboarded and secured by Microsoft Defender for Endpoint, appear in the device inventory Computers and Mobile tab. To start onboarding these devices, see Onboard newly discovered devices. |
About onboarding status |
Onboard newly discovered devices
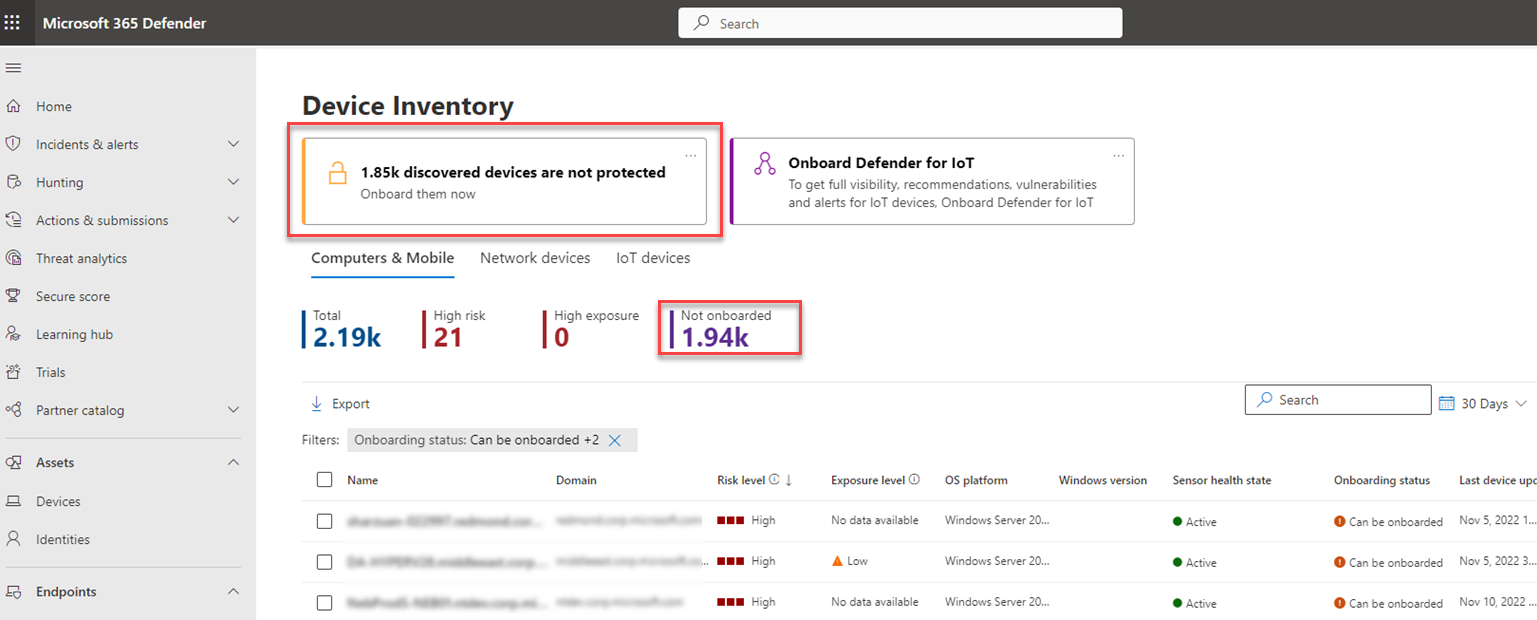
The device inventory provides a clear view into newly discovered devices in your network that aren't yet protected. At the top of each device inventory tab, you can see the total number of devices that aren't onboarded:
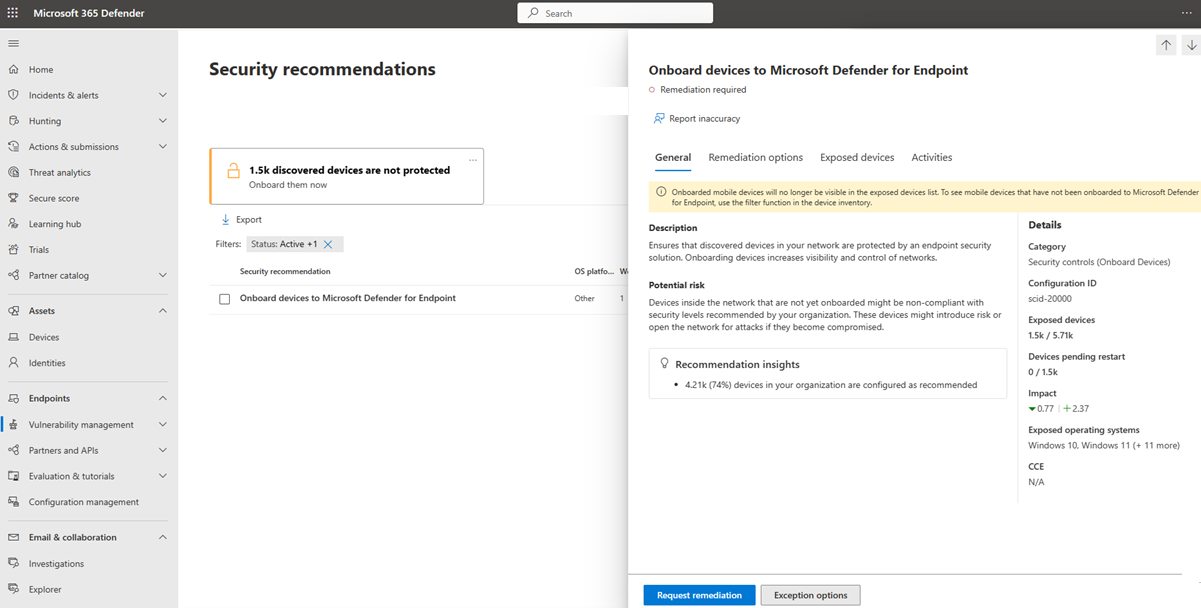
Once you're ready, you can start onboarding these devices by choosing the Onboard them now card. This card brings you directly to the Onboard devices to Microsoft Defender for Endpoint security recommendation.
To learn more about how to request remediation to onboard your devices using this security recommendation, see request remediation.
Next step
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for