Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
[This article is prerelease documentation and is subject to change.]
Copilot Studio now supports multitenant mode. This new support allows an agent to be used in a different Microsoft Entra tenant than the tenant that hosts it. Multitenant mode changes the behavior of a Copilot Studio agent when using specific authentication options. This article describes authentication in Copilot Studio and the role authentication plays in multitenant mode.
Important
This feature in Copilot Studio is in public preview. The preview is clearly marked in Copilot Studio for makers. The multitenant feature in Public Preview has terms that are referenced in the product. Public preview features aren't supported for use in a generally available capacity. No support is provided or should be expected by using standard support processes. Agents using public preview features shouldn't be used in production. The Teams Store lets partners submit their agent for a single geography. Partners should highlight to their end users that their agents use preview functionality with a Preview banner in the icon.
Copilot Studio Makers can select from three authentication options for agents:
| Authentication method | Description |
|---|---|
| No Authentication | Copilot Studio allows for external users to use agents built and hosted in the platform when selecting the No Authenticaton configuration setting in the Authentication and Settings area of the agent. When this setting is turned on, no access token is passed to the agent from the client where the user accesses the agent. This type of scenario is commonly found in websites in self-service FAQ style use cases. This setting allows any user to access to the agent. |
| Authenticate with Microsoft | This option uses an integrated authentication option. The agent expects a Microsoft Entra ID identity from the client. Teams and other Microsoft clients send this identity when they authenticate users with work or school Microsoft Entra accounts. The agent uses this identity to let the user access its functionality. This option in Copilot Studio performs a single-sign-on (SSO) experience between the client, the agent, and the user. The user doesn't have to first sign in to access the client, and then a second time to access the agent. |
| Authenticate Manually | When selected, this option explicitly signals to Copilot Studio to not handle or expect the identity. The maker configures authentication for the selected authentication option. Manual authentication is typically used when not using a Microsoft-based identity or client. For example, you're embedding the agent in a website or native application and want to authenticate external users. When using manual authentication, you can select the type of authentication:
|
Important
To use Microsoft Teams as a channel in Copilot Studio, you must select Authenticate with Microsoft or Authenticate Manually. This requirement is by design and aligns identity models. Teams requires a user to always be signed in, so as a result, Teams agents can't be anonymous. The same is true for all Microsoft channels (for example SharePoint).
Multitenant mode
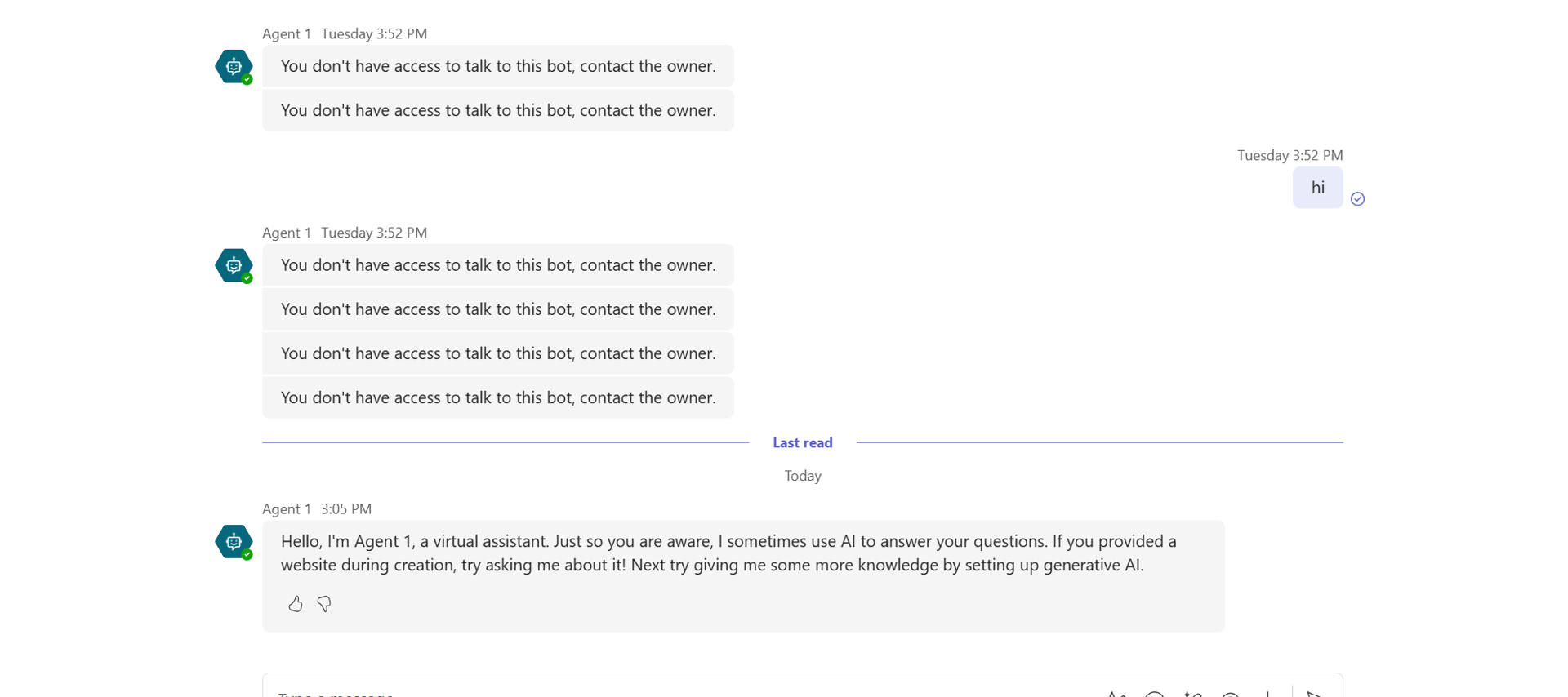
In single-tenant mode, Microsoft Teams users have to be signed in and accessing the Copilot Studio agent using the same tenant as where the agent is hosted in Copilot Studio. If a user from another tenant (for example, example@zavainsurance.com tries to access an agent hosted in example@contoso.com), the user receives a message from the agent: "You don't have access to talk to this bot. Contact the owner."
When multitenant mode in Copilot Studio is enabled for an agent, the agent hosted in one tenant can be accessed from a different Microsoft Entra ID tenant.
This feature is in public preview. Multitenant mode is supported for Copilot Studio agents in Microsoft Teams and Microsoft 365 Copilot. Multitenant mode allows for agents to be discovered on the global Microsoft Teams Store, where agents can be used from clients when they are in two different tenants.
Terminology
When working with agents and understanding authentication, it's important to separate the following behaviors:
- User to client authentication: For example, when a user logs into a Teams Client, or signs into a website with their Microsoft account. This isn't strictly related to the Copilot Studio agent and happens outside of the agent
- Client to agent authentication: The client can send information to the agent, and the agent can expect information from the client. The authentication is invisible for the end user of the client if the agent is configured for single sign-on (SSO). If not, the user is prompted to sign in to the agent separately.
- Agent authentication to other authenticated services: The agent needs to communicate with other services, and in some cases needs to pass along identity. That identity can be the agent's identity (service principal) if the agent has an identity. Otherwise, the agent can use the user's identity if the agent has permissions to do so, accessing resources and performing actions (using delegated permissions from the signed in client user)
There's also a blended authentication option experience where an agent authentication flow can be gated via topics in Copilot Studio using the Authenticate node, which prompts the user to sign in. Blended authentication is only available when Authenticate Manually is selected in Copilot Studio and when Require Users to Sign in is turned off.
When you're using multitenant mode, there's some common terminology used in this article:
The host is the environment where Copilot Studio is hosted, runs from, and is billed from. The host is where the Copilot Studio agent is built. The host is also where the agent moves through the standard software development lifecycle as the agent is developed, tested, and moved to a production environment for live usage. This is no different from the case for agents in single-tenant mode.
The client is where the agent is accessed from. This is a client application like Microsoft Teams or Microsoft 365 Copilot. From these clients, the agent is accessed and used by a user, who is signed in using Microsoft Entra ID. There's no Power Platform infrastructure, including Copilot Studio, required or used on the client.
The following documentation covers what functionality is currently supported in public preview when multitenant mode is turned on in Copilot Studio.
Supported functionality
Public preview for multitenant is launching within a specific scope.
When the agent is in multitenant mode, you should expect the agent to behave differently. Not all features of Copilot Studio are supported. The differences can be either due to the nature of the functionality (for example, SharePoint knowledge doesn't work across tenants), or due to the public preview scope. The sections that follow contain more details.
Important highlights:
- End-user authentication isn't yet supported in multitenant mode. This means you can't delegate access to use the user's identity in downstream behaviors. We know the value of this feature is to pass authenticated information to the agent from delegated authentication with other services. This functionality isn't yet available.
- Conversation transcripts are turned off when multitenant mode is turned on. This is to protect the privacy of the downstream tenants using the agent.
- Host tenants are responsible for the billing of the Copilot Studio agent in the same way as for single-tenant mode. Microsoft partners deploying to the global Teams and agent store looking for different patterns of working with their end customers, for example, charging for agents on the global Teams Store, should consult with Partner Center for what programs are available.
We summarized in the following section the functionality known to work or not work when using the agent in multitenant mode. If something isn't listed here as working, it should be expected to not work for multitenant mode. Functionality in Copilot Studio isn't modified to work differently when multitenant mode is on. For example, data policies still run on the host tenant, and features/functionality, if supported, have the same feature set as they do in single-tenant mode.
Knowledge
- Dataverse Upload: Supported in public preview across tenants.
- Public Websites: Supported in public preview across tenants.
Tools
- Prompts: Supported in public preview across tenants.
- Limited standard connectors: For more information, see Authentication.
- REST API connectors: Supported in public preview across tenants.
Note
Custom connectors, computer use, agent flows, and MCP tools aren't supported in multitenant mode.
Topics
- User variables: Not available or supported in public preview.
- Authentication node: Available for manual authentication only.
- HTTP node: Works for public endpoints in public preview for multitenant mode.
Channels
Supported channels for public preview include:
- Microsoft Teams
- Microsoft 365 Copilot
Authentication
- End-user authentication: Not supported. The client prompts users to open the connection manager, but isn't able to complete the request as it sends the user to their own Copilot Studio connection manager in a location different from where the agent is located.
- OAuth: Not supported for authenticate manually.
- Graph/Microsoft 365 standard connectors: Not supported.
- Custom connectors: Not supported.
- Maker authentication (service principal) on standard tools: Supported in public preview.
- Manual authentication with Microsoft Entra user ID and service principal: Not supported in public preview.
- Guest users: Not supported.
Other details
- Only 1-1 conversations are supported. Group conversations aren't supported.
- Multi-geo isn't supported. The feature doesn't support hosting an agent in one geography and accessing it from another geography.
- Government Community Cloud (GCC) and GCC High are not supported
- Manual Authentication is not yet supported (coming soon)
Note
Use caution when using maker authentication on connectors. Maker authentication on connectors can expose details of your tenant to third parties through URLs and so on.
Analytics
- Aggregated analytics: Not available in public preview.
- Transcript data: Not available in public preview.
- Download session data: Not available in public preview.
- Satisfaction, effectiveness, overview, and reactions: Not available in public preview.
Note
Channel metrics are based on what is offered via the channel capabilities and availability (that is, via Teams).
Admin controls
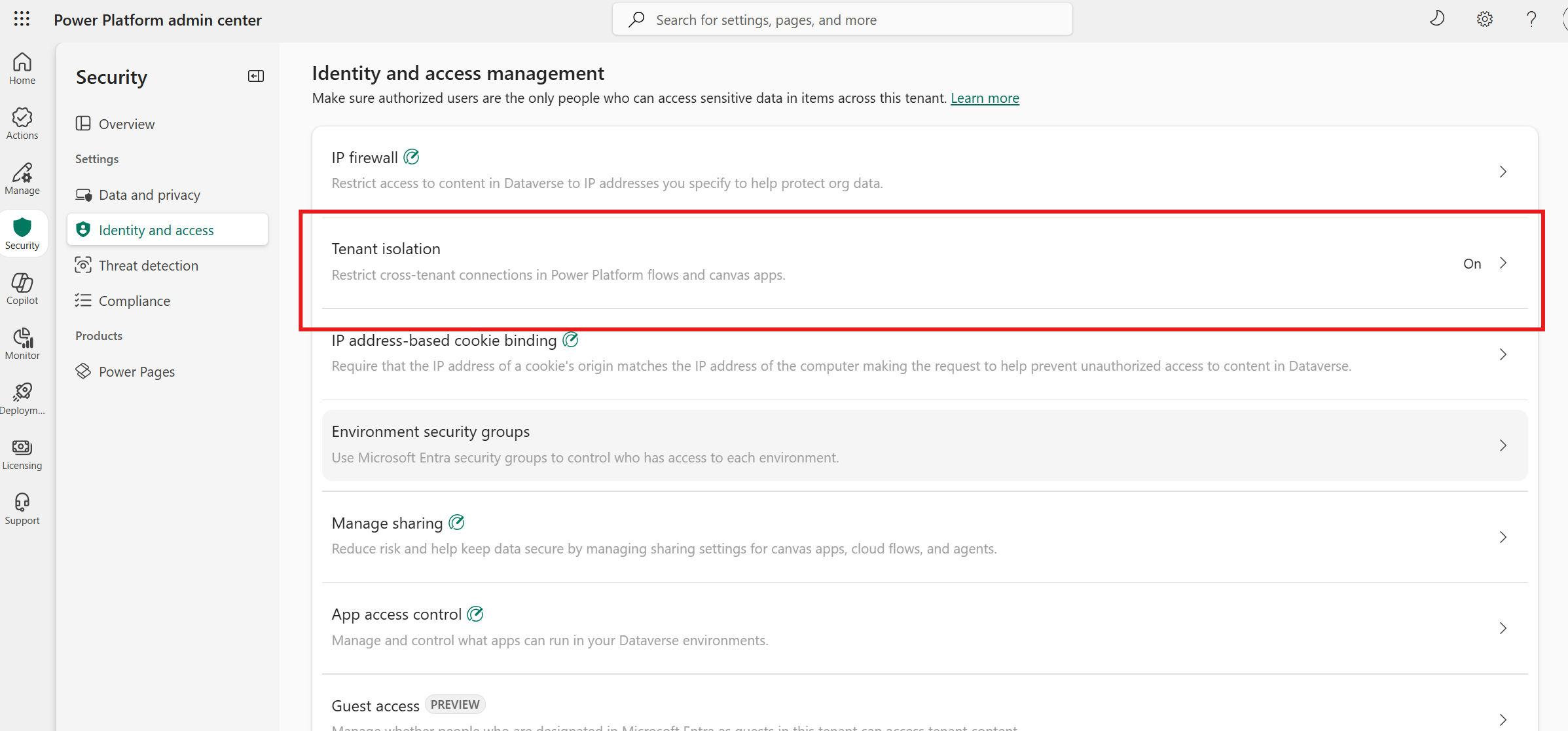
Admin controls for the agent host tenant
Multitenant mode is governed in the Power Platform Admin Center (PPAC). Host tenant admins have the ability to prevent makers from enabling multitenant mode for agents. Admins for the host tenant can navigate to the tenant isolation area in PPAC, which is off by default. When you turn on tenant isolation, the tenant is isolated and you can't use multitenant mode. If admins want to allow only a select set of tenants to establish connections to or from their tenant, they can turn on tenant isolation, and use the allow list feature to specify those tenants for inbound and outbound. For more information, see Cross-tenant inbound and outbound restrictions
If tenant isolation is on, multitenant mode isn't available in Copilot Studio.
Other Scenarios:
- If tenant isolation is turned on after an agent is enabled and published, Copilot Studio displays a notification explaining that the agent no longer works as multitenant. The agent then behaves the same as a single-tenant agent when another tenant tries to access it.
- If the admin control is turned on (to block multitenant) but there's an allow list entry, only tenants in the allow list can access the agent. All other tenants are blocked, the same as in the single-tenant mode.
- Data loss prevention controls expect the host agent's data policies.
- Copilot Studio permits disabling of the Teams channel for an agent. This stops the agent responding on the Teams client.
- If the Teams and Microsoft 365 Copilot channel is turned off, this disrupts service for your agent. You can turn on your agent again, since your agent ID isn't changed. You might be required to complete the publish process again.
- Updating an agent is the same as for Copilot Studio. Makers should use Publish' to push changes to the live agent in use. New updates don't need to be published via the teams store. The Teams Store policies have their own expectations on updating an agent if any metadata related to the agent, for example, purpose, terms links, and so on, are changed.
Admin controls for Copilot Studio in the client
In the client tenant where the agent is being used, there are no changes for Microsoft Admin Center (MAC) administrators. MAC admins are in control of a CEA using Copilot Studio the same as pro-code custom engine agents.
Billing and licensing
Billing is the responsibility of the host tenant. This arrangement is the same as for pro-code agents on the store and for customers deploying agents to their own users. For more information around billing, see Manage sessions and capacity
Host tenants must manage their billing as part of the product and ensure it has the adequate credits and/or billing configuration to support the audience they're allowing access to.
Multitenant mode is only supported in public preview with host tenants with a full Copilot Studio license.
If the partner doesn't have sufficient billing, and runs out of credits, the end user is affected and receives an error with the agent. Before this happens, the admins are notified and asked to address the issue via an automatic notification. The maximum number of Copilot Studio credits/sessions that can be allocated to an environment is the highest that can be assigned.
Partners or customers publishing their agent to the Teams Store could also cause unexpected billing if agent adoption proceeds at a fast rate (for example, via the Teams store or other discovery methods). The host tenant is responsible for this process and for the agent in the same way as publishing anonymous agents today on unauthenticated channels (for example, on the web).
Software development practices
As part of your agent's application lifecycle management (ALM) process, you need to subject multitenant agents to higher levels of testing. Multitenant agents have more areas of functionality to test since some areas behave differently than in single-tenant mode.
Here are some areas to consider when working with multitenant agents in Copilot Studio:
- Have your development environments configured and set up for the recommended ALM including a development environment, a test environment, a test environment in a second tenant, and a production environment.
- Have your capacity planned and configured for the environments and also plan a proactive way to review and monitor those agents.
- If you plan to create a multitenant agent, ensure you have a separate tenant for testing, so that you can test the specific configuration in multitenant mode by accessing the agent from a different tenant than the tenant the agent is hosted in.
- You can sideload your agent in your test client tenant and configure the tenant isolation policy in your host Power Platform Admin to work specifically with your test environment configuration.
- A customer/partner can sideload the .ZIP package that references an agent running in Copilot Studio. The .ZIP package can be uploaded via the Teams or Microsoft Admin Center and managed the same as for single-tenant agents in Copilot Studio.
Update your agent
Agents published to the Teams Store only require a republish via the Teams Store validation process if there are metadata changes (for example, purpose, terms, links, and so on). This means when a non-Microsoft agent is published and made live, it's available to all current users. This is the same for Copilot Studio today as for other channels and authentication methods.
Export the manifest from Copilot Studio
Once you're ready to test the agent in the Microsoft Teams or Microsoft 365 Copilot client in another tenant, the agent needs to be available in the second tenant. For testing, the agent needs to be sideloaded into another tenant either by a MAC admin or a user who has the permissions to sideload the agent in their client (granted by a MAC admin in the second tenant).
Host tenant access can be restricted via the Power Platform Admin Center tenant isolation policy by adding your test client tenant information when you're testing across your own specific tenants and you move through the application lifecycle management process.
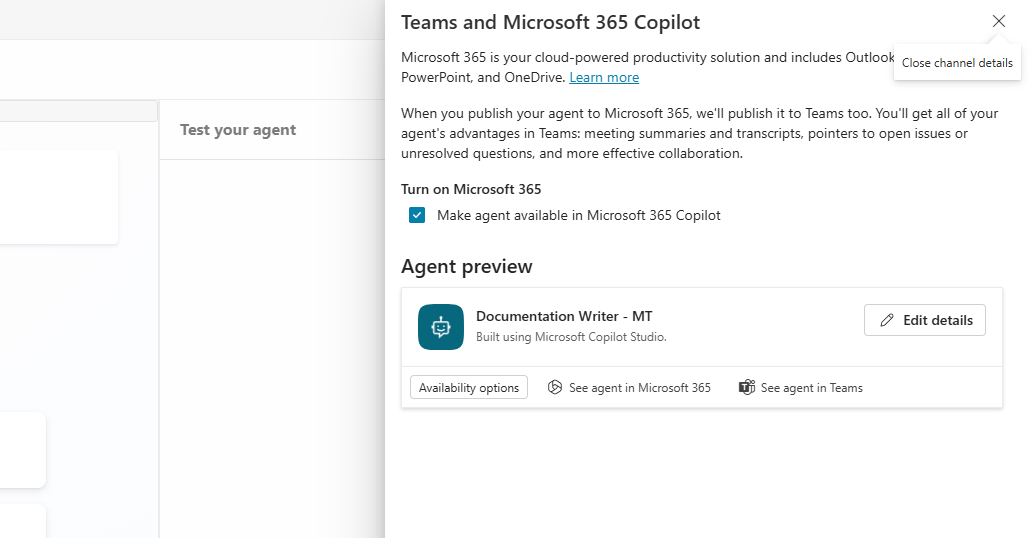
To export the manifest .ZIP file, go to Channels in Copilot Studio, select the Teams and Microsoft 365 Copilot channel, and then select Edit Details.
You can edit the name, description, and other details in the manifest file required by Microsoft Teams and Microsoft 365 Copilot. The manifest file contains important metadata about your agent, which the client tenant sees when reviewing your agent for use on their tenant.
Once you edit the details, you can export the .ZIP file by selecting Availability Options.
This downloads a local .ZIP file to your machine. The .ZIP file has the icon color and manifest files. You can also edit the manifest manually. While the feature is in public preview, makers need to edit the manifest, specifically in the Valid Domains node. For more information, see Make your agent available in Teams or Microsoft 365 Copilot
Related content
- Make your agent available in Teams or Microsoft 365 Copilot: This article includes documentation on sideloading and publishing to the global Teams Store.
- Best practices, troubleshooting, and additional information: This article includes guidance around the software development lifecycle when building agents, considerations, troubleshooting, and roadmap information.