2.1.1.2 Protocol Interactions
The following diagram illustrates the internal system architecture of the interactive domain logon authentication task. The authentication protocols that are involved in the interactive domain logon authentication process are:
Domain Logon (Username and Password):
Authentication Protocol Domain Support [MS-APDS] - NTLM pass-through
Smart card Domain Logon (X.509 Certificate):
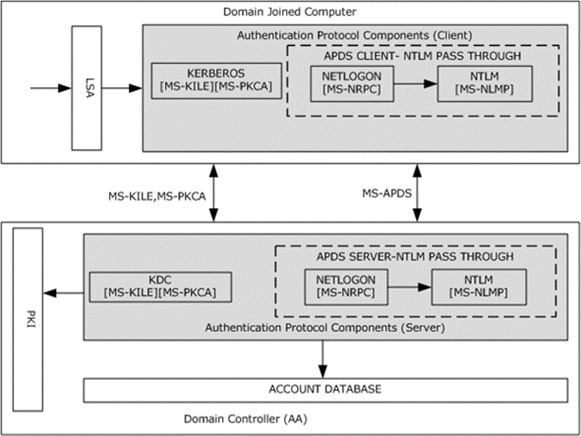
Figure 4: Protocol interactions for interactive domain logon authentication
If the user credentials consist of a user name and password pair, the domain logon authentication process first tries the Kerberos Authentication Protocol ([MS-KILE]). If Kerberos fails, the authentication process falls back to the NTLM pass-through mechanism ([MS-APDS]). For smart card logons in which the credentials contain X.509 certificates, the domain logon process uses the Public Key Cryptography for Initial Authentication (PKINIT) in the Kerberos Protocol ([MS-PKCA]).
A Kerberos client attempts to prove the user identity by sending Kerberos protocol messages to request a ticket-granting ticket (TGT) and a service ticket from the Key Distribution Center (KDC). The KDC verifies the user identity against the account database and returns the TGT to the Kerberos client. In subsequent messages, the Kerberos client requests the service ticket for a domain-joined computer from the KDC. The KDC attempts to validate the TGT. If the validation succeeds, the KDC returns the service ticket to the Kerberos client.
Next, the Kerberos client submits the service ticket to verify the user logon information. If the Kerberos authentication fails, the APDS client on the domain-joined computer calls the NTLM pass-through mechanism to prove the user identity and to get the user logon information. The APDS server validates the user credentials against the account database; if the validation succeeds, the APDS server returns the user logon information.
In the smart card logon scenario, the Kerberos client requests the TGT and service ticket from the KDC by proving the user's identity in the form of an X.509 certificate, as described in [MS-PKCA]. The KDC verifies the user identity against the account database by using PKI services and returns a TGT and a service ticket. The Kerberos client submits the service ticket to the Kerberos server to validate the service ticket and the user logon information. If the validation of user logon information succeeds, interactive domain logon is permitted; otherwise, logon attempts fail.