2.5.3.1.1 Interactive Domain Logon: Service Ticket for Client Computer
The LSA initiates this use case with the goal of proving the identity of a user to the Authentication Authority (AA) and of getting a service ticket that contains user logon information from the AA for the client computer. The user provides the credential material information, which includes the identification and proof of that identification.
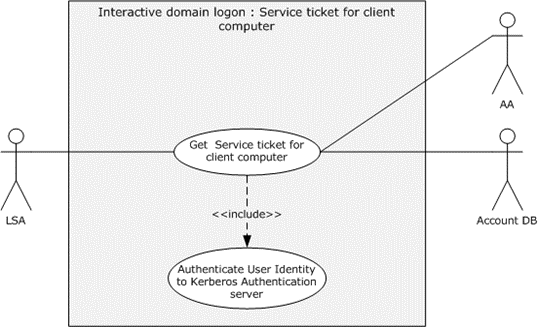
Figure 16: Interactive domain logon - service ticket for client computer use case
Goal: To get the service ticket for a client computer.
Context of Use: Applies when the user interactively logs on to the domain.
Direct Actor: The LSA.
Primary Actor: The user.
Supporting Actors: The AA and the account database (DB).
Preconditions:
The client computer is joined to a domain.
The identity of the user is configured in the account database.
The client computer and the AA can communicate with each other.
Minimal Guarantee: The LSA sends an error message to the user when the submitted credentials do not match the ones that are stored in the account database or when the interactive domain logon process fails.
Success Guarantee: The LSA receives a service ticket for the client computer.
Trigger: The user attempts to log on interactively to the client computer.
Main Success Scenario:
The identity of the user is proven to the AA as described in section 2.5.5.1.
The LSA requests a service ticket for the client computer by including a Kerberos authenticator and the TGT that was received in the preceding step in a Kerberos request and sending the request to the AA.
The AA validates the request and returns a service ticket for the client computer.
Alternative Scenario: This scenario occurs when Flexible Authentication Secure Tunneling (FAST) mode is supported and configured on both the Authentication Client and the AA and when the preceding preconditions are met.
The identity of the client computer is proven to the AA as described in the Main Scenario in sections 2.5.5.1.1 or 2.5.5.1.2, and a TGT for the computer is obtained.
The identity of the user is proven to the AA as described in the Alternative Scenario in section 2.5.5.1.1.
The LSA requests the AA to issue a service ticket for the client computer by sending a FAST TGS-REQ message that includes the Kerberos authenticator and the TGT that was received in the preceding step.
Same as step 3 of the Main Success Scenario.
Postconditions: The LSA has received a service ticket for the client computer, which contains user logon information.
Extensions: None.
Alternative Scenario: The following scenario occurs when Kerberos authentication fails.
The LSA submits a Netlogon message to prove the identity of the user to the AA. The message includes the identity of the user and a one-way hash of the password ([MS-NRPC] section 2.2.1.4.3).
The AA verifies the user identity and password hash against the account DB and returns the user logon information.