Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
The following figure shows the components that use the Group Policy: IPsec Protocol.
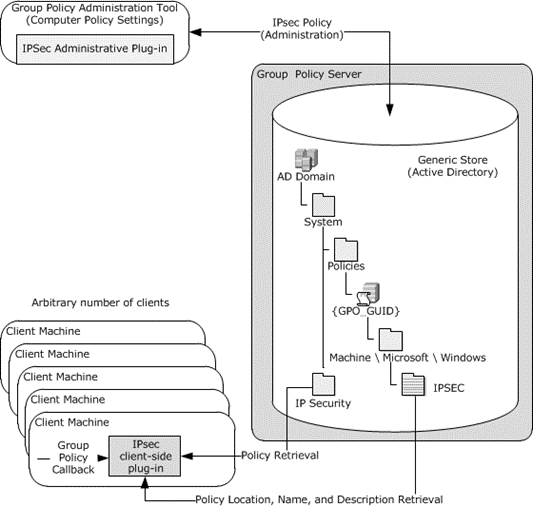
Figure 1: Components that use the Group Policy: IPsec Protocol Extension
The components in the protocol are as follows:
An IPsec administrative plug-in (computer policy settings) that is used to author and upload policy settings.
A generic binary large object (BLOB) store with no protocol-specific knowledge (in this case, Active Directory).
A client machine with an IPsec client-side plug-in.
The IPsec client-side plug-in locates the policy stores in the Active Directory store to retrieve policy information (see details in sections 3.2.5.1 and 3.2.5.3). Then, the IPsec client-side plug-in reads and applies policies, as specified in sections 3.2.5.1 and 3.2.5.4.
Policy information is authored in the IPsec administrative plug-in and is sent to a generic store (in this case, the Active Directory store). The policy data is generated by an IPsec policy administrator through an IPsec authoring user interface. The administrator creates one or more IPsec policies and assigns a single policy to a group of managed machines using a GPO.
The IPsec policy creation uses the LDAP "add" mechanism, as specified in [RFC2251] section 4.7. For details, see Message Syntax (section 2.2).

Figure 2: IPsec policy creation
The IPsec policy modification (for example, when changing an IPsec policy object name or reference GUID) uses the LDAP "modify" mechanism, as specified in [RFC2251] section 4.6. For details, see Message Syntax (section 2.2).

Figure 3: IPsec policy modification
A client obtains the IPsec policy in three steps:
A client-side Group Policy protocol client polls the store to discover the existence of a new policy. When a new or changed IPsec policy is detected, it signals the IPsec client-side plug-in that an IPsec policy change has occurred and provides an LDAP path to the assigned policy, as specified in [MS-GPOL] section 1.3.3.
The IPsec client-side plug-in reads the LDAP path that specifies the assigned policy location as an LDAP path reference that specifies the assigned IPsec policy details.
The IPsec policy detail LDAP path is then used by the IPsec client-side plug-in to read and interpret the assigned IPsec policy settings so that the IPsec policy settings can be enacted on the local system.
The details of the actual individual settings that are transferred by this protocol are specified in IPsec Policy Creation/Modification (section 2.2.1), because the relevant behavior is not part of the Group Policy: Core Protocol or its extensions, but rather of the Group Policy: IPsec Protocol. These details are included to enable a client to successfully read and interpret the IPsec policy data and understand the protocol.
IPsec policy retrieval uses the LDAP search functionality, as specified in [RFC2251] section 4.5, and in sections 3.2.5.3 and 3.2.5.4.

Figure 4: IPsec policy retrieval
Note Processing instructions for the first LDAP Search/Response pair is specified in section 3.2.5.3. Processing instructions for the second LDAP Search/Response pair is specified in section 3.2.5.4.