Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
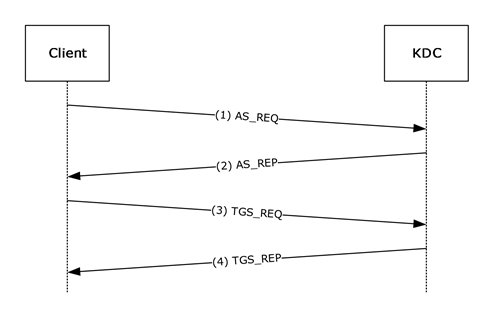
Figure 2: Interactive logon that uses passwords
Step 1: A user attempts to log on to a client and types a password at the logon screen, and an AS-REQ for a ticket-granting ticket (TGT) with pre-authentication data is generated. The AS-REQ, which uses the user name and password, is sent to the Key Distribution Center (KDC).
Step 2: In response to receiving the AS-REQ for a TGT, the KDC authenticates the user by checking that the credentials that are used in the AS-REQ are the same as that of the user's ([RFC4120] section 3.1). The KDC builds an AS-REP from the TGT and other requisite data and sends it back to the client.
The KDC builds a PAC (section 3.3.5.6). Data in the PAC includes account data for the user that is used for logging onto the client. The account data is expected to be supplied by the KDC that queries an account service for the account data. The KDC inserts the PAC that contains the account data that is received from the account service into the authorization_data field of the TGT.
Step 3: The client then sends a TGS-REQ based on the TGT that is obtained in step 2 to obtain a service ticket that is formatted according to the Kerberos protocol for completing a logon process at the local workstation. The client runtime issues a request to host/hostname.domain, where hostname is the actual name of the client machine, and domain is the domain or realm of the client machine.
Step 4: The KDC responds to the TGS-REQ with a TGS-REP that contains the service ticket for the local workstation. The authorization data from step 2 is carried forward to the service ticket, with additional group processing (section 3.3.5.7). The service ticket is then interpreted by the Kerberos runtime within the local workstation.
The following fields from the PAC are required by interactive logon to authorize the user for local logon and to establish the necessary management profile for the user. [MS-PAC] is the authoritative reference for formatting and encoding these fields.
LogonTime
LogoffTime
KickOffTime
PasswordLastSet
PasswordCanChange
EffectiveName
FullName
LogonScript
ProfilePath
HomeDirectory
HomeDirectoryDrive
LogonCount
BadPasswordCount
LogonServer
LogonDomainName
UserAccountControl