2.2.9.2 CertificateStore Configuration Service Provider
The CertificateStore configuration service provider is used to add Secure Sockets Layer (SSL), intermediate, and self-signed certificates.
Note: The CertificateStore configuration service provider does not support installing client certificates.
Note: For the CertificateStore CSP, the Replace command cannot be used unless the node already exists.
The following diagram shows the CertificateStore configuration service provider management object in tree format.
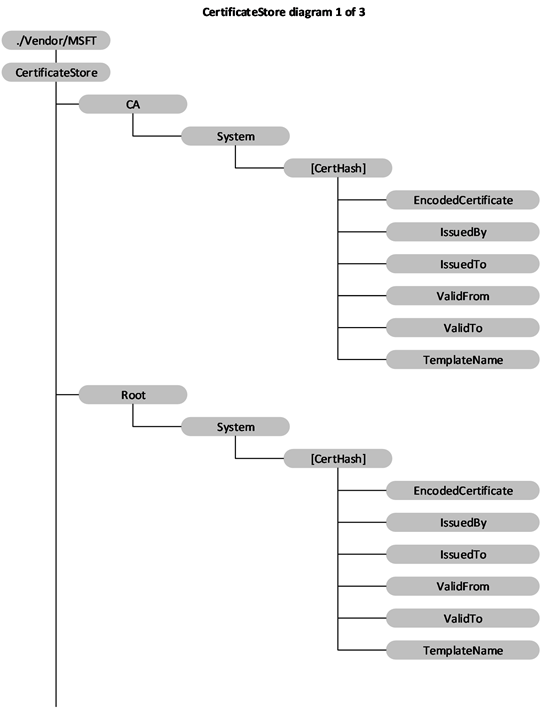
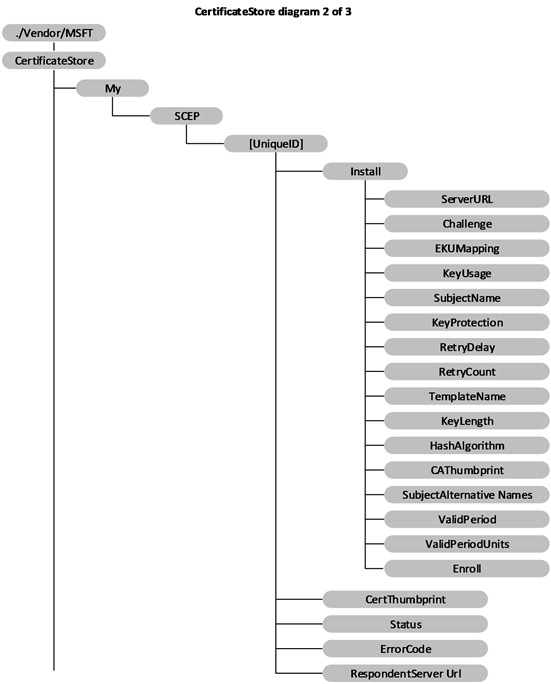
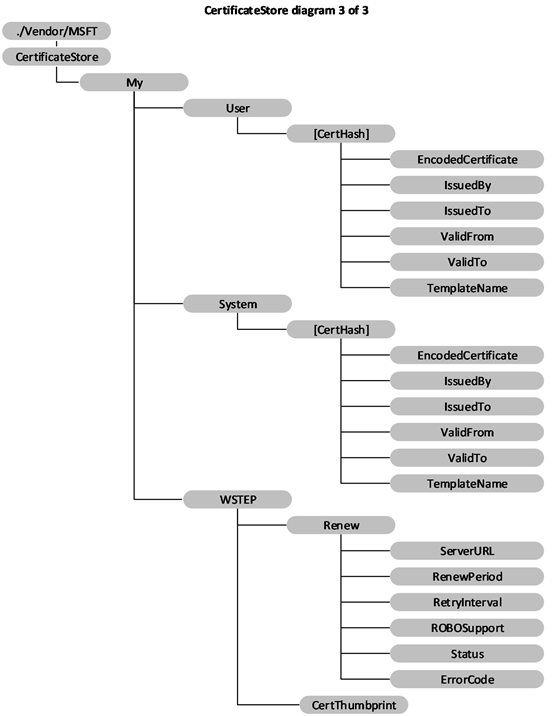
Figure 4: The CertificateStore configuration service provider management object in tree format
Root/System: Defines the certificate store that contains root, or self-signed, certificates. Supported operation is Get. Note that Root/System is case sensitive.
CA/System: Defines the certificate store that contains cryptographic information, including intermediary certification authorities. Supported operation is Get. Note that CA/System is case sensitive.
My/User: Defines the certificate store that contains public keys for client certificates. This is only used by enterprise servers to push down the public key of a client certificate. The client certificate is used by the device client to authenticate itself to the enterprise server for device management and downloading enterprise applications. Supported operation is Get. Note that My/User is case sensitive.
My/System: Defines the certificate store that contains the public key for the client certificate. This is only used by enterprise server to push down the public key of the client certificate. The client certificate is used by the device to authenticate itself to the enterprise server for device management and enterprise app downloading. Supported operation is Get. Note that My/System is case sensitive.
[CertHash]: Defines the SHA-1 hash for the certificate. The 20-byte value of the SHA-1 certificate hash is specified as a hexadecimal string value. Supported operations are Get, Delete, and Replace.
[CertHash]/EncodedCertificate: Required. Specifies the X.509 certificate as a base64-encoded string. The Base-64 string value cannot include extra formatting characters such as embedded linefeeds, etc. Supported operations are Add, Delete, Get, and Replace.
[CertHash]/IssuedBy: Returns the name of the certificate issuer. This is equivalent to the Issuer member in the CERT_INFO data structure (see [MSDOCS-CERT_INFO]). Supported operation is Get.
[CertHash]/IssuedTo: Returns the name of the certificate subject. This is equivalent to the Subject member in the CERT_INFO data structure. Supported operation is Get.
[CertHash]/ValidFrom: Returns the starting date of the certificate 's validity. This is equivalent to the NotBefore member in the CERT_INFO structure. Supported operation is Get.
[CertHash]/ValidTo: Returns the expiration date of the certificate. This is equivalent to the NotAfter member in the CERT_INFO structure. Supported operation is Get.
[CertHash]/TemplateName: Returns the certificate template name. Supported operation is Get.
My/SCEP: Required for Simple Certificate Enrollment Protocol (SCEP) certificate enrollment. The parent node grouping the SCEP certificate related settings. Supported operation is Get.
My/SCEP/[UniqueID]: Required for SCEP certificate enrollment. A unique ID to differentiate certificate enrollment requests. Format is node. Supported operations are Add, Get, Delete, and Replace.
My/SCEP/[UniqueID]/Install: Required for SCEP certificate enrollment. Parent node to group SCEP certificate install related request. Format is node. Supported operations are Add, Replace, and Delete.
-
Note: Though the children nodes under Install support Replace commands, after the Exec command is sent to the device, the device takes the values that are set when the Exec command is accepted. The node value change that occurs after the Exec command is accepted might not impact the current node undergoing enrollment. Implementers can check the Status node value to determine whether the device is not at an unknown stage previous to changing the children node values.
My/SCEP/[UniqueID]/Install/ServerURL: Required for SCEP certificate enrollment. Specifies the certificate enrollment server. The server could specify multiple server URLs separated by a semicolon. Value type is string. Supported operations are Add, Get, Delete, and Replace.
My/SCEP/[UniqueID]/Install/Challenge: Required for SCEP certificate enrollment. Base64 encoded SCEP enrollment challenge. Value type is chr. Supported operations are Add, Get, Delete, and Replace. Challenge will be deleted shortly after the Exec command is accepted.
My/SCEP/[UniqueID]/Install/EKUMapping: Required. Specifies the extended key usages and is subject to SCEP server configuration. The list of object identifiers (OIDs) are separated by plus sign (+), such as OID1+OID2+OID3. Value type is chr. Supported operations are Add, Delete, Get, and Replace.
My/SCEP/[UniqueID]/Install/KeyUsage: Required for enrollment. Specifies the key usage bits (0x80, 0x20, 0xA0, etc.) for the certificate in decimal format. The value MUST have at least the second (0x20) or fourth (0x80) or both bits set. If the value does not have those bits set, configuration will fail. Value type is int. Supported operations are Add, Delete, Get, and Replace.
My/SCEP/[UniqueID]/Install/SubjectName: Required. Specifies the subject name. Value type is chr. Supported operations are Add, Delete, Get, and Replace.
My/SCEP/[UniqueID]/Install/KeyProtection: Optional. Specifies the location of the private key. Although the private key is protected by trusted platform module (TPM), it is not protected with TPM PIN. SCEP enrolled certificate does not support TPM PIN protection.
-
Valid values:
-
1 – the private key is protected by device TPM.
-
2 – the private key is protected by device TPM if the device supports TPM.
-
3 (default) – the private key is only saved in the software Key Storage Provider (KSP).
-
4 – the private key is protected by Microsoft .NET Passport. If this option is specified, the container name MUST be specified, otherwise the enrollment will fail.
-
-
Value type is int. Supported operations are Add, Delete, Get, and Replace.
My/SCEP/[UniqueID]/Install/RetryDelay: Optional. Specifies the device retry waiting time in minutes when the SCEP server sends the pending status. Default value is 5 and the minimum value is 1. Value type is int. Supported operations are Add, Get, and Delete.
My/SCEP/[UniqueID]/Install/RetryCount: Optional. Special to SCEP. Specifies the device retry times when the SCEP server sends pending status. Value type is int. Default value is 3. Max value cannot be larger than 30. If it is larger than 30, the device will use 30.The min value is 0 which means no retry. Supported operations are Add, Delete, Get, and Replace.
My/SCEP/[UniqueID]/Install/TemplateName: Optional. OID of certificate template name. Note that this name is typically ignored by the SCEP server; therefore, the MDM server typically does not need to provide it. Value type is chr. Supported operations are Add, Get, and Delete.
My/SCEP/[UniqueID]/Install/KeyLength: Required for enrollment. Specifies private key length (RSA). Value type is int. Valid values are 1024, 2048, 4096<2>. Supported operations are Add, Delete, Get, and Replace.
My/SCEP/[UniqueID]/Install/HashAlgorithm: Required for enrollment. Hash algorithm family (SHA-1, SHA-2, SHA-3) specified by the MDM server. If multiple hash algorithm families are specified, they MUST be separated with a +. Value type is chr. Supported operations are Add, Delete, Get, and Replace.
My/SCEP/[UniqueID]/Install/CAThumbprint: Required. Specifies the root CA thumbprint. It is a 20-byte value of the SHA-1 certificate hash specified as a hexadecimal string value. When a client authenticates a SCEP server, it checks the CA certificate from the SCEP server for a match with this certificate. If it does not match, the authentication fails. Value type is chr. Supported operations are Add, Delete, Get, and Replace.
My/SCEP/[UniqueID]/Install/SubjectAlternativeNames: Optional. Specifies the subject alternative name. Multiple alternative names can be specified. Each name is the combination of name format+actual name. For more information on the name type definition see [MSDOCS-ClientCertInstall-CSP]. Each pair is separated by semicolon. For example, multiple subject alternative names are presented in the format <nameformat1>+<actual name1>;<name format 2>+<actual name2>. Value type is chr. Supported operations are Add, Delete, Get, and Replace.
My/SCEP/[UniqueID]/Install/ValidPeriod: Optional. Specifies the units for valid period. Valid values are Days (Default), Months, Years. Value type is chr. Supported operations are Add, Delete, Get, and Replace.
-
Note: The device only sends the MDM server expected certificate validation period (ValidPeriodUnits + ValidPeriod) of the SCEP server as part of certificate enrollment request. How this valid period is used to create the certificate depends on the MDM server.
My/SCEP/[UniqueID]/Install/ValidPeriodUnits: Optional. Specifies desired number of units used in validity period and subject to SCEP server configuration. Default is 0. The units are defined in ValidPeriod node. The valid period specified by MDM overwrites the valid period specified in the certificate template. For example, if ValidPeriod is days and ValidPeriodUnits is 30, it means the total valid duration is 30 days. Value type is int. Supported operations are Add, Delete, Get, and Replace.
-
Note: The device only sends the MDM server expected certificate validation period (ValidPeriodUnits + ValidPeriod) of the SCEP server as part of certificate enrollment request. How this valid period is used to create the certificate depends on the MDM server.
My/SCEP/[UniqueID]/Install/Enroll: Required. Triggers the device to start the certificate enrollment. The MDM server can later query the device to find out whether the new certificate is added. Value type is null, which means that this node does not contain a value. Supported operation is Exec.
My/SCEP/[UniqueID]/CertThumbprint: Optional. Specifies the current certificate thumbprint if certificate enrollment succeeds. It is a 20-byte value of the SHA-1 certificate hash specified as a hexadecimal string value. Value type is chr. Supported operation is Get.
My/SCEP/[UniqueID]/Status: Required. Specifies the latest status for the certificate due to enrollment request. Value type is chr. Supported operation is Get.
-
Valid values:
-
1 – Finished successfully.
-
2 – Pending. The device has not finished the action, but has received the SCEP server pending response.
-
32 – Unknown.
-
16 - Action failed.
-
My/SCEP/[UniqueID]/ErrorCode: Optional. The integer value that indicates the HRESULT of the last enrollment error code. Supported operation is Get.
My/SCEP/[UniqueID]/RespondentServerUrl: Required. Returns the URL of the SCEP server that responded to the enrollment request. Value type is string. Supported operation is Get.
My/WSTEP: Required for MDM enrolled device. The parent node that hosts the MDM enrollment client certificate related settings that is enrolled via WSTEP. The nodes under WSTEP are mostly for MDM client certificate renew requests. Value type is node. Supported operation is Get.
My/WSTEP/Renew: Optional. The parent node to group renewal related settings. Supported operation is Get.
My/WSTEP/Renew/ServerURL: Optional. Specifies the URL of certificate renewal server. If this node does not exist, the client uses the initial discovery URL from enrollment. Supported operations are Add, Delete, Get, and Replace.
My/WSTEP/Renew/RenewalPeriod: Optional. The time (in days) to trigger the client to initiate the MDM client certificate renew process before the MDM certificate expires. The MDM server cannot set and update the certificate expiration date. It is recommended that the renew period is set a couple months before the certificate expires to ensure that the certificate gets renewed successfully with data connectivity.
-
The default value is 42 and the valid values are 1 – 1000. Value type is int. Supported operations are Add, Delete, Get, and Replace.
-
Note: When the renewal schedule is set over SyncML DM commands to ROBOSupport, RenewalPeriod, and RetryInterval, it MUST be wrapped in Atomic commands as specified in [MS-MDM].
My/WSTEP/Renew/RetryInterval: Optional. Specifies the retry interval (in days) when the previous renewal failed. The retry schedule stops at the certificate expiration date.
-
The default value is 7 and the valid values are 1 – 1000 AND =< RenewalPeriod, otherwise it will result in error.. Value type is int. Supported operations are Add, Delete, Get, and Replace.
-
Note: When the renewal schedule is set over SyncML DM commands to ROBOSupport, RenewalPeriod, and RetryInterval, it MUST be wrapped in Atomic commands as specified in [MS-MDM].
My/WSTEP/Renew/ROBOSupport: Optional. Notifies the client if the MDM enrollment server supports ROBO auto certificate renewal. Value type is bool.<3>
-
Note: When the renewal schedule is set over SyncML DM commands to ROBOSupport, RenewalPeriod, and RetryInterval, it MUST be wrapped in Atomic commands as specified in [MS-MDM].
My/WSTEP/Renew/Status: Required. Shows the latest action status for this certificate. Value type is int. Supported operation is Get.
-
Valid values:
-
0 – Not started.
-
1 – Renewal in progress.
-
2 – Renewal succeeded.
-
3 – Renewal failed.
-
My/WSTEP/Renew/ErrorCode: Optional. If certificate renewal fails, this integer value indicates the HRESULT of the last error code during the renewal process. Value type is int. Supported operation is Get.
My/WSTEP/CertThumbprint: Optional. Returns the current MDM client certificate thumbprint. If renewal succeeds, it shows the renewed certificate thumbprint. If renewal fails or is in progress, it shows the thumbprint of the certificate that needs to be renewed. Value type is chr. Supported operation is Get.