3 Protocol Details
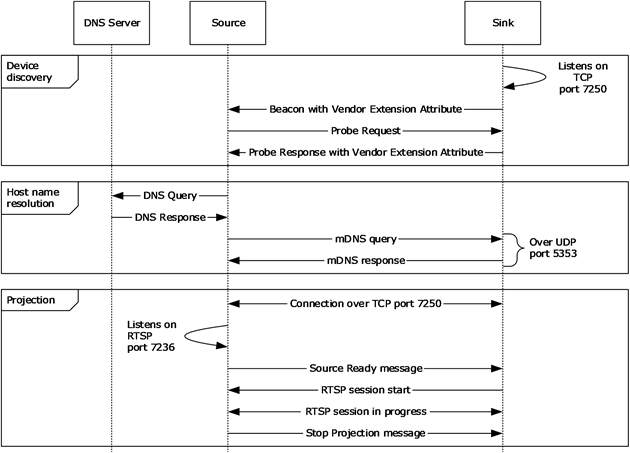
A Miracast over Infrastructure session consists of three phases: device discovery, host name resolution, and projection, as shown in the following diagram.
 Figure
2: A Miracast over Infrastructure session
Figure
2: A Miracast over Infrastructure session
Device discovery
The Miracast over Infrastructure session starts with peer to peer (P2P) device discovery ([WF-P2P1.2] section 3.1.2), which a Miracast Source uses to find a device capable of performing the functions of a Miracast Sink. This includes the Source sending Probe Request frames ([WF-P2P1.2] section 4.2.2) and listening for Probe Response frames ([WF-P2P1.2] section 4.2.3) and Beacon frames ([WF-P2P1.2] section 4.2.1).
Beacon frames are unsolicited broadcasts that advertise P2P devices. Probe Response frames are sent by a Sink in response to Probe Request frames sent by the Source. If the Source receives a Beacon or Probe Response that contains a WSC IE [WF-WSC2.0.2] Vendor Extension attribute (section 2.2.8), the Source checks the Capability attribute (section 2.2.8.1) for Miracast over Infrastructure support.
If the Capability attribute specifies that Miracast over Infrastructure is not supported, the Source falls back to standard Miracast [WF-WSC2.0.2].
If one or more IP Address attributes (section 2.2.8.5) are included, the Source can skip host name resolution.
Host name resolution
The host name received by the Source during device discovery specifies the unqualified host name of the target Sink. The Source tries to resolve this host name by using DNS [IANA-DNS] [RFC1034] [RFC2181] and/or mDNS [RFC6762].
When host name resolution is complete, the session proceeds to the Projection phase.
The Source uses a Discovery timer (section 3.2.2) to limit the time it spends on host name resolution. If this timer reaches its timeout, the host name resolution fails, and the Source falls back to standard Miracast.
Projection
When the Source finds a device that can perform as the Sink, the Source attempts a connection to it over TCP port 7250, which it will use for sending Miracast over Infrastructure messages (section 2.2) to the Sink. These messages include starting and stopping the projection, as well as negotiating options for the stream, such as encryption and PIN entry at connection time.
This phase is further subdivided into optional sections depending on the protocol version and options chosen by the Source and Sink device. The following diagram shows all the required and optional steps of the projection setup phase.
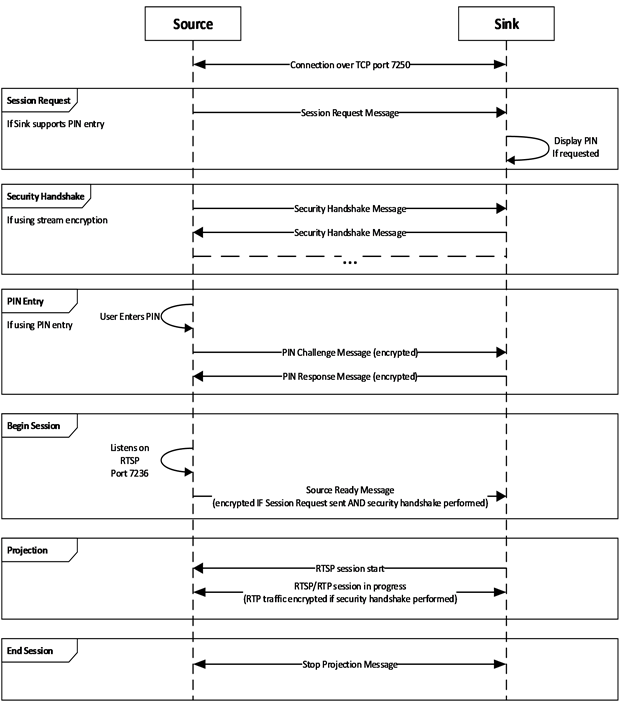
Figure 3: Projection setup phase
The Sink is expected to be listening for messages on TCP port 7250. The Sink listens for Source Ready messages (section 2.2.1). If the Sink supports stream encryption, it also listens for Security Handshake messages (section 2.2.3). If the sink supports PIN entry, it also listens for Session Request messages (section 2.2.4).
The Source will either begin at the Session Request step, Security Handshake step, or Begin Session step, depending on what it supports and what support was indicated by the sink in the Vendor Specific attribute.
In the case of beginning at the Begin Session step, when the Source is ready to project, it listens on Real-Time Streaming Protocol (RTSP) control port 7236 for a connection request, then it sends the Source Ready message. In turn, the Sink connects to the specified RTSP Source port to establish the link.
In the case of beginning at the Security Handshake step, the Source sends a Security Handshake message (section 2.2.3) and waits for a response, listening for Security Handshake messages from the Sink. The Source and Sink continue to exchange messages until the DTLS handshake is complete. After this, the Source proceeds to Begin Session as defined above by listening on Real-Time Streaming Protocol (RTSP) control port 7236 for a connection request, and sending the Source Ready message. In turn, the Sink connects to the specified RTSP Source port to establish the link. In this case, the RTP (video and audio) and UIBC traffic shall be encrypted using the DTLS key exchanged.
In the case beginning at the Session Request step, the Source sends a Session Request message (section 2.2.4) and then proceeds to the Security Handshake phase. When the Sink which supports PIN entry receives the Session Request message with the PIN entry bit in the Security Options set (section 2.2.7.5), it displays a random PIN for the user of the Source to provide. After the Security Handshake, if PIN entry was selected, the Source waits for user input of the displayed PIN then proceeds to the PIN entry phase to validate the PIN with the sink. The TLVArray of the PIN Challenge (section 2.2.5) and PIN Response (section 2.2.6) messages are encrypted using the key exchanged during the DTLS handshake. Following the PIN exchange, if performed, the Source listens on Real-Time Streaming Protocol (RTSP) control port 7236 for a connection request, then it sends the Source Ready message with the TLVArray encrypted using the key exchanged during the DTLS handshake. In turn, the Sink connects to the specified RTSP Source port to establish the link. In this case, the RTP (video and audio) and UIBC traffic shall be encrypted using the DTLS key exchanged.
To stop the projection, the Source sends a Stop Projection message (section 2.2.2) to notify the Sink. Upon receipt of that message, the Sink stops displaying the stream, and a disconnection follows from the Source on the socket that is connected on port 7250. The Sink may send a Stop Projection message to notify the Source of a graceful teardown of the session. Upon receipt of that message, the Source stops sending RTP/RTSP frames, and a disconnection follows on the socket that is connected on port 7250.