Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
When a secure channel is required, a number of additional steps are taken in the process of executing the method. For example, if a client calls the NetrLogonSamLogon method (section 3.5.4.5.3) to execute an interactive account logon, the execution of the method involves several steps.
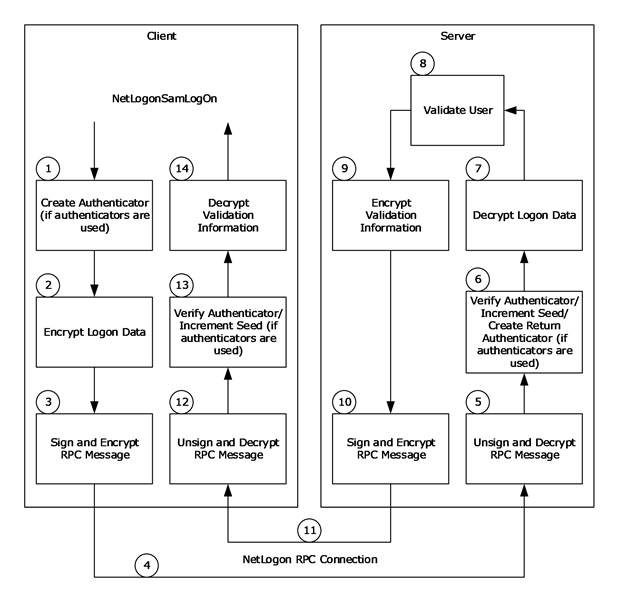
Figure 10: Secure channel execution of NetrLogonSamLogon
NetrLogonSamLogon involves the following steps:
If the Netlogon RPC call is using authenticators, the following steps are also performed.
The client creates an authenticator. An authenticator is represented by a NETLOGON_AUTHENTICATOR structure (section 2.2.1.1.5).
The client fills in the Timestamp field of the structure with the number of seconds since 00:00:00 on January 1, 1970 (UTC). The client then adds this value to the current authentication seed to produce a new seed value.
The client computes the credential based on the new authentication seed, the session key, and the client challenge, per the calculation specified in the previous Netlogon Credentials section.
If the LogonLevel parameter of the NetrLogonSamLogon method contained one of a set of specific values, the client encrypts the logon data using the session key with the negotiated encryption algorithm. The following table defines the LogonLevel parameter value and the data that is encrypted.
LogonLevel value
Data encrypted
NetlogonInteractiveInformation (1)
The LmOwfPassword and NtOwfPassword fields of the NETLOGON_INTERACTIVE_INFO structure (section 2.2.1.4.3) that was passed in the LogonInformation parameter.
NetlogonInteractiveTransitiveInformation (5)
The LmOwfPassword and NtOwfPassword fields of the NETLOGON_INTERACTIVE_INFO structure (section 2.2.1.4.3) that was passed in the LogonInformation parameter.
NetlogonServiceInformation (3)
The LmOwfPassword and NtOwfPassword fields of the NETLOGON_SERVICE_INFO structure (section 2.2.1.4.4) that was passed in the LogonInformation parameter.
NetlogonServiceTransitiveInformation (7)
The LmOwfPassword and NtOwfPassword fields of the NETLOGON_SERVICE_INFO structure (section 2.2.1.4.4) that was passed in the LogonInformation parameter.
NetlogonGenericInformation (4)
The contents of the LogonData buffer of the NETLOGON_GENERIC_INFO structure (section 2.2.1.4.2) that was passed in the LogonInformation parameter.
This step is not performed for any other LogonLevel parameter values.
The client signs and encrypts the RPC message or each message fragment. If the RPC message is fragmented, operations are done on each message fragment. The data is first passed to RPC, where it is formatted according to the RPC standard ([C706] section 12.6.2). RPC then calls back to Netlogon to encrypt the RPC data buffer. The encryption of the RPC data buffer includes the following steps. (The checksum algorithm used is the negotiated checksum algorithm. The encryption algorithm used is the negotiated encryption algorithm.)
Create and initialize a signature. A signature is represented by an NL_AUTH_SIGNATURE structure (section 2.2.1.3.2).
Generate random data for the confounder in the signature.
Assign the sequence number in the signature based on the nonce and increment the nonce.
Note The nonce is initialized to zero and is used to maintain the sequence number for the calls over the secure channel.
Calculate the checksum of the first 8 bytes of the signature.
Calculate the checksum of the 8 bytes that make up the confounder in the signature.
Create an encryption key by XOR’ing every byte of the session key with 0xF0.
Encrypt the confounder using the encryption key.
If PFC_SUPPORT_HEADER_SIGN has been negotiated by the RPC layer [MS-RPCE] section 3.3.1.5.2.2), calculate the checksum of the PDU Header.
Calculate the checksum of the caller's message.
Encrypt the caller's message or message fragment using the encryption key.
If PFC_SUPPORT_HEADER_SIGN has been negotiated by the RPC layer, calculate the checksum of the sec_trailer.
Finalize the checksum and assign it to the checksum in the signature.
Encrypt the sequence number in the signature using the session key.
The client sends the data over the Netlogon RPC connection.
The server verifies the signature and decrypts the RPC message or each message fragment. If the RPC message is fragmented, operations are done on each message fragment. The decryption of the RPC message includes the following steps:
Decrypt the sequence number in the signature using the session key.
Compare the sequence number with the nonce and increment the nonce.
Calculate the checksum of the first 8 bytes of the signature.
Create an encryption key by XOR'ing every byte of the session key with 0xF0.
Decrypt the confounder using the encryption key.
Calculate the checksum of the 8 bytes that make up the confounder in the signature.
If PFC_SUPPORT_HEADER_SIGN has been negotiated by the RPC layer [MS-RPCE] section 3.3.1.5.2.2), calculate the checkum of the PDU Header.
Decrypt the caller's message or message fragment using the encryption key.
Calculate the checksum of the caller's message.
Finalize the checksum and compare it with the checksum in the signature.
If the Netlogon RPC call is using authenticators, the server verifies the received authenticator and creates a return authenticator. To verify the received authenticator, the server adds the time stamp value in the authenticator to the current authentication seed to produce a new seed value. The server then computes the client's credential based on the new authentication seed, the session key, and the client challenge, per the calculation specified in the previous Netlogon Credentials section. Finally, the server checks whether the resulting credential is equal to the credential in the received authenticator. If successful, the server adds 1 to the authentication seed. Then the server creates a return authenticator. The server computes the credential for the return authenticator based on the new authentication seed, the session key, and the server challenge (SC), per the calculation specified in the previous Netlogon Credentials section.
If the LogonLevel parameter of the NetrLogonSamLogon method contained one of a set of particular values, the server decrypts the logon data, using the session key with the negotiated decryption algorithm. The following table defines the LogonLevel parameter values and the data that is decrypted.
LogonLevel value
Data decrypted
1
The LmOwfPassword and NtOwfPassword fields of the NETLOGON_INTERACTIVE_INFO structure that was passed in the LogonInformation parameter.
5
The LmOwfPassword and NtOwfPassword fields of the NETLOGON_INTERACTIVE_INFO structure that was passed in the LogonInformation parameter.
3
The LmOwfPassword and NtOwfPassword fields of the NETLOGON_SERVICE_INFO structure that was passed in the LogonInformation parameter.
7
The LmOwfPassword and NtOwfPassword fields of the NETLOGON_SERVICE_INFO structure that was passed in the LogonInformation parameter.
4
The contents of the LogonData buffer of the NETLOGON_GENERIC_INFO structure that was passed in the LogonInformation parameter.
This step is not performed for any other LogonLevel parameter values.
The server executes its implementation of the NetrLogonSamLogon method to validate the user. The resulting validation information is returned in a NETLOGON_VALIDATION union.
If the LogonLevel parameter of the NetrLogonSamLogon method contained one of the following values, the server encrypts the validation information:
NetlogonNetworkInformation
NetlogonNetworkTransitiveInformation
NetlogonGenericInformation
The validation data is encrypted using the session key with the negotiated encryption algorithm. The data that is encrypted depends on the value that was passed in the ValidationLevel parameter of the NetrLogonSamLogon method. The following table defines the ValidationLevel parameter values and the data that is encrypted.
ValidationLevel value
Data encrypted
2
The UserSessionKey and ExpansionRoom fields of the NETLOGON_VALIDATION_SAM_INFO structure (section 2.2.1.4.11) that was passed in the ValidationInformation parameter.
3
The UserSessionKey and ExpansionRoom fields of the NETLOGON_VALIDATION_SAM_INFO2 structure (section 2.2.1.4.12) that was passed in the ValidationInformation parameter.
5
The contents of the ValidationData buffer of the NETLOGON_VALIDATION_GENERIC_INFO2 structure (section 2.2.1.4.8) that was passed in the ValidationInformation parameter.
This step is not performed for any other LogonLevel parameter values.
The server signs and encrypts the RPC response message. The server performs the same steps as the client performed in step 3.
The server sends the response back to client over the Netlogon RPC connection.
The client unsigns and decrypts the RPC message. The client performs the same steps as the server performed in step 5.
If the Netlogon RPC call is using authenticators, the client verifies the return authenticator. To verify the return authenticator, the client adds 1 to the authentication seed to produce a new seed value. The client then computes the server's credential based on the new authentication seed, the session key, and the server challenge, per the calculation specified in the previous Netlogon Credentials section. Finally, the client checks whether the resulting credential is equal to the credential in the return authenticator.
If the LogonLevel parameter of the NetrLogonSamLogon method contained one of the following values, the client decrypts the validation information:
NetlogonNetworkInformation
NetlogonNetworkTransitiveInformation
NetlogonGenericInformation
The validation data is decrypted using the session key with the negotiated decryption algorithm. The data that is decrypted depends on the value that was passed in the ValidationLevel parameter of the NetrLogonSamLogon method. The following table defines the ValidationLevel parameter value and the data that is decrypted.
ValidationLevel value
Data decrypted
2
The UserSessionKey and ExpansionRoom fields of the NETLOGON_VALIDATION_SAM_INFO structure (section 2.2.1.4.11) that was passed in the ValidationInformation parameter.
3
The UserSessionKey and ExpansionRoom fields of the NETLOGON_VALIDATION_SAM_INFO2 structure (section 2.2.1.4.12) that was passed in the ValidationInformation parameter.
5
The contents of the ValidationData buffer of the NETLOGON_VALIDATION_GENERIC_INFO2 structure (section 2.2.1.4.8) that was passed in the ValidationInformation parameter.
This step is not performed for all other LogonLevel parameter values.
The execution of all other Netlogon methods requiring a secure channel is like the previous example.