Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
In a scenario where a user does an interactive logon to a client machine and connects to a server, the connection is authenticated. The client and the server engage in an authentication protocol, such as NTLM (as specified in [MS-NLMP]), which validates the user credentials and logs the user on to the server upon successful validation. This type of logon is known as network logon because it happens over a network connection from the client to the server.
To authenticate the user, the server passes the user credentials securely to a Domain Controller (DC) in the domain of the user account. (The DC is the only entity, other than the client machine, that knows the user secret key; that is, the user password.) After the logon request is delivered to the DC and the DC successfully validates the credentials, the DC refers back to the server those attributes of the user account that the server can use in authorization decisions (such as granting the user access to a particular file). Unless otherwise specified, MS-NRPC uses little endian for byte ordering before encryption.
It is the responsibility of the Netlogon Remote Protocol to deliver the logon request to the DC over a secure channel that is established from the server (acting as the secure channel client) to the DC (acting as the secure channel server). The secure channel is achieved by encrypting the communication traffic with a session key computed using a secret key (called a server's machine account password) shared by the server and the DC.
Upon successful validation of the user credentials on the DC, the Netlogon Remote Protocol delivers the user authorization attributes (referred to as user validation information) back to the server over the secure channel.
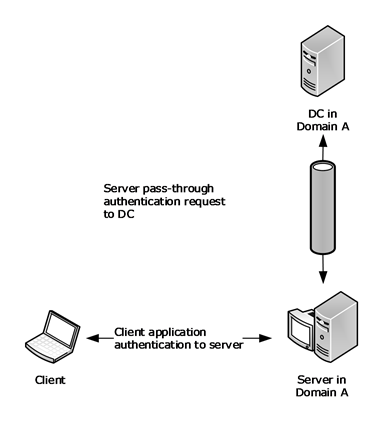
This mechanism of delegating the authentication request to a DC is called pass-through authentication, a process in which the server passes the logon request through to the DC. The following figure is an illustration that depicts a process of pass-through authentication in which the authentication request is passed over a secure channel from a server in Domain A to a DC in the domain containing the user account, in this case the DC is also in Domain A.
Figure 1: Pass-through authentication