1.3 Overview
The Online Certificate Status Protocol (OCSP), described in [RFC2560], provides a mechanism, as a supplement to checking against a periodic certificate revocation list (CRL), to obtain timely information regarding the revocation status of a certificate (see [RFC3280] section 3.3). OCSP enables applications to determine the revocation state of an identified X.509 certificate (see [X509] ). The Lightweight Online Certificate Status Protocol (OCSP) Profile for High-Volume Environments ([RFC5019]) provides a profile of OCSP that specifies a subset of the functionality of the complete OCSP defined in [RFC2560]. OCSP Extensions specifies the data that needs to be exchanged between an application that checks the status of a certificate and the responder that provides the status.
OCSP is a component of a public key infrastructure (PKI). A PKI consists of a system of digital certificates, certification authorities (CAs), and other registration authorities (RAs) that verify and authenticate the validity of each party involved in an electronic transaction through the use of public key cryptography.
The certificate status received as a result of using OCSP is known as a response from an OCSP responder. The OCSP request/response process involves a number of different machines (or functions that might be hosted on the same machine), as indicated in Figure 1.
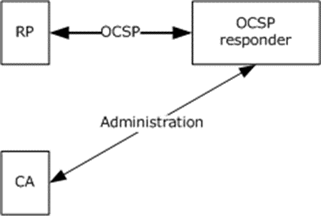
Figure 1: Response from an OCSP
In the preceding figure, the principal components are as follows:
CA: The certification authority that provides certificate status information to the OCSP responder through the use of CRLs.
Relying party (RP): The resource guard that validates a certificate chain and contacts an OCSP responder to request certificate status.
OCSP responder: An authoritative source for certificate revocation status (see [RFC3280] section 3.3). The protocols and data structures used for OCSP are defined in section 2.2. The connection over which OCSP is conducted is shown in the preceding figure as a solid bold horizontal line.