2.6 PAC Credentials
When the Kerberos authentication is performed through means other than a password, the PAC includes an element that is used to send credentials for alternate security protocols to the client during initial logon. Typically, this PAC credentials element is used when a public key form of authentication, such as that specified in [RFC4556], is used to establish the Kerberos authentication. This PAC credentials element MUST NOT be present when the PAC structure is used for other protocols. Credentials for other security protocols can be sent to the client for a single logon experience.
Because the information in the PAC credentials element is sensitive (PAC credentials essentially contains password equivalents), the information MUST be protected. This element is encrypted, as specified in PAC_CREDENTIAL_INFO (section 2.6.1).
The PAC credentials structure is a complex, nested structure that supports extensibility of security protocols that receive their credentials in the same way.
The following figure illustrates how PAC credentials data is nested.
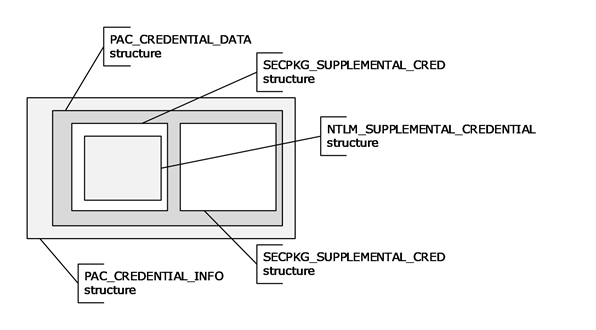
Figure 2: PAC credentials
The outermost PAC_CREDENTIAL_INFO structure contains an encrypted PAC_CREDENTIAL_DATA (section 2.6.2) structure, along with the encryption type, as an indicator of how to decrypt it. The PAC_CREDENTIAL_DATA structure, in turn, contains an array of SECPKG_SUPPLEMENTAL_CRED (section 2.6.3) structures, one per security protocol receiving credentials. Each of these structures contains the name of the security protocol receiving the credentials and credential information specific to the implementation of the protocol. NTLM [MS-NLMP] credentials are supplied in the NTLM_SUPPLEMENTAL_CREDENTIAL structure.