Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
The following call flow outlines how the NTLM Authentication Protocol authentication mechanism works.
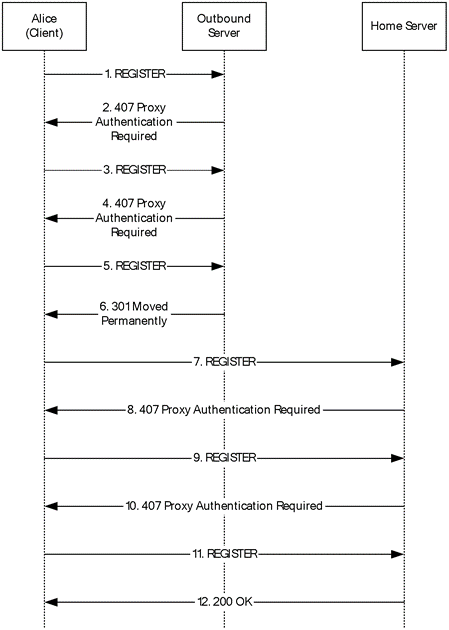
Figure 2: NTLM registration flow
Alice's client sends a REGISTER request with no credentials (no Proxy-Authorization: header) to the server.
REGISTER sip:registrar.contoso.com SIP/2.0 Via: SIP/2.0/TLS alice1.contoso.com;branch=z9hG4bK7 From: "Alice" <sip:alice@contoso.com>;tag=354354535;epid=6534555 To: "Alice" sip:alice@contoso.com Call-ID: 123213@alice1.contoso.com CSeq: 12345 REGISTER Max-Forwards: 70 User-Agent: Windows RTC/1.1.2600 Contact: "Alice" sip:alice@alice1.contoso.com Content-Length: 0
The epid parameter on the From: header uniquely identifies this particular endpoint for the user. The server will use this value in subsequent messages to determine the SA with which to sign the message.
Authentication is enabled at the outbound server, and it challenges Alice's client. The server indicates support for NTLM and Kerberos in the challenge.
SIP/2.0 407 Proxy Authentication Required Via: SIP/2.0/TLS alice1.contoso.com;branch=z9hG4bK7 From: "Alice" <sip:alice@contoso.com>;tag=354354535;epid=6534555 To: "Alice" <sip:alice@contoso.com>;tag=5564566 Call-ID: 123213@alice1.contoso.com CSeq: 12345 REGISTER Date: Sat, 13 Nov 2010 23:29:00 GMT Proxy-Authenticate: Kerberos realm="Contoso RTC Service Provider", targetname="sip/hs1.contoso.com", qop="auth" Proxy-Authenticate: NTLM realm="Contoso RTC Service Provider", targetname="hs1.contoso.com', qop="auth" Content-Length: 0
The targetname parameter carries the FQDN for this proxy for NTLM and the SPN of the proxy for Kerberos. The actual content of this parameter is meaningful for this proxy but is opaque to other proxies and the client. It is merely a unique string for correlation of the message header to an SA. Three Proxy-Authenticate: headers are present, indicating the server's capability to do one of Kerberos or NTLM.
The proxy inserts a Date: header in the 407 challenge to allow the client to detect clock skew between the client and server. Both NTLM 2.0 and Kerberos 5.0 require synchronization of the client and server clocks. Clock skew can cause authentication to fail even with valid credentials. The presence of the Date: header allows the client to log this condition and the administrator to correct the deviation.
The client reissues the REGISTER request, indicating support for NTLM authentication.
REGISTER sip:registrar.contoso.com SIP/2.0 Via: SIP/2.0/TLS alice1.contoso.com;branch=z9hG4bK8 From: "Alice" <sip:alice@contoso.com>;tag=354354535;epid=6534555 To: "Alice" sip:alice@contoso.com Call-ID: 123213@alice1.contoso.com CSeq: 12346 REGISTER Max-Forwards: 70 User-Agent: Windows RTC/1.1.2600 Proxy-Authorization: NTLM realm="Contoso RTC Service Provider", targetname="hs1.contoso.com",qop="auth",gssapi-data="" Contact: "Alice" sip:alice@alice1.contoso.com Content-Length: 0
The Cseq number has been incremented. The Call-ID and epid remain the same.
The targetname parameter echoes the value of the targetname parameter in the previous Proxy-Authenticate: header. The empty gssapi-data parameter indicates that no credentials (password) are being sent in this header. The choice of NTLM authentication is indicated by the scheme (NTLM) as the first token in the header.
The outbound server responds with a 407 containing a Proxy-Authenticate: header, which includes the NTLM challenge.
SIP/2.0 407 Proxy Authentication Required Via: SIP/2.0/TLS alice1.contoso.com;branch=z9hG4bK8 From: "Alice" <sip:alice@contoso.com>;tag=354354535;epid=6534555 To: "Alice" <sip:alice@contoso.com>;tag=5564566 Call-ID: 123213@alice1.contoso.com CSeq: 12346 REGISTER Date: Sat, 13 Nov 2010 23:29:00 GMT Proxy-Authenticate: NTLM realm="Contoso RTC Service Provider", targetname="hs1.contoso.com", qop="auth", gssapi-data ="345435acdecbba",opaque="ACDC123" Content-Length: 0
The gssapi-data parameter carries the challenge. The opaque parameter serves as an index to the (incomplete) SA state on the proxy.
Alice's client reissues the REGISTER request with a response to the outbound server's challenge.
REGISTER sip:registrar.contoso.com SIP/2.0 Via: SIP/2.0/TLS alice1.contoso.com;branch=z9hG4bK9 From: "Alice" <sip:alice@contoso.com>;tag=354354535;epid=6534555 To: "Alice" sip:alice@contoso.com Call-ID: 123213@alice1.contoso.com CSeq: 12347 REGISTER Max-Forwards: 70 User-Agent: Windows RTC/1.1.2600 Proxy-Authorization: NTLM realm="Contoso RTC Service Provider", targetname="hs1.contoso.com",qop="auth", gssapi-data="34fcdf9345345",opaque="ACDC123" Contact: "Alice" sip:alice@alice1.contoso.com Content-Length: 0
The Cseq number has been incremented. The Call-ID and epid remain the same. The gssapi-data parameter carries the client's response to the challenge. The opaque parameter is echoed from the previous challenge.
On reception of the REGISTER request, the outbound server authenticates the user with the information in the Proxy-Authorization: header. Authentication succeeds, and a SA is created in the outbound server for Alice's client.
The outbound server then redirects the REGISTER request to point the client at the appropriate home server for this user. The redirect response is signed, using the newly established SA between the client and this proxy.
SIP/2.0 301 Moved Permanently Via: SIP/2.0/TLS alice1.contoso.com;branch=z9hG4bK9 From: "Alice" <sip:alice@contoso.com>;tag=354354535;epid=6534555 To: "Alice" sip:alice@contoso.com Call-ID: 123213@alice1.contoso.com CSeq: 12347 REGISTER Proxy-Authentication-Info: NTLM realm="Contoso RTC Service Provider", targetname="hs1.contoso.com", qop="auth", opaque="ACDC123", srand="3453453", snum=1, rspauth="23423acfdee2" Contact: sip:hs2.contoso.com Content-Length: 0
The Proxy-Authentication-Info: header carries the signature for this SIP message. The snum is set to 1 because this is the first message signed with the newly established SA. The srand parameter contains the (random) salt value used by the server to generate the signature.
The client receives the redirect response, verifies the signature using the now complete SA for the outbound proxy, and reissues the REGISTER request to its proper home server.
REGISTER sip:hs2.contoso.com SIP/2.0 Via: SIP/2.0/TLS alice1.contoso.com;branch=z9hG4bKa From: "Alice" <sip:alice@contoso.com>;tag=354354535;epid=6534555 To: "Alice" sip:alice@contoso.com Call-ID: 123213@alice1.contoso.com CSeq: 12348 REGISTER Max-Forwards: 70 User-Agent: Windows RTC/1.1.2600 Contact: "Alice" sip:alice@alice1.contoso.com Content-Length: 0
The client will replace its current outbound proxy with the proxy indicated in the Contact: header of the 301 response. The REGISTER request is sent to this new outbound proxy (the user's true home server). Since no SA exists yet with this new outbound proxy, no Proxy-Authenticate: header is present in the request.
Alice's home server receives the REGISTER request and issues a challenge, indicating support for NTLM and Kerberos authentication.
SIP/2.0 407 Proxy Authentication Required Via: SIP/2.0/TLS alice1.contoso.com;branch=z9hG4bKa From: "Alice" <sip:alice@contoso.com>;tag=354354535;epid=6534555 To: "Alice" <sip:alice@contoso.com>;tag=8823488 Call-ID: 123213@alice1.contoso.com CSeq: 12348 REGISTER Date: Sat, 13 Nov 2010 23:29:00 GMT Proxy-Authenticate: Kerberos realm="Contoso RTC Service Provider", targetname="hs2.contoso.com", qop="auth" Proxy-Authenticate: NTLM realm="Contoso RTC Service Provider", targetname="hs2.contoso.com", qop="auth" Content-Length: 0
The targetname parameter contains the FQDN for Alice's home server. The two Proxy-Authenticate: headers indicate support for Kerberos and NTLM, respectively. The realm is the same as for HS1 because they fall under the same protection space. This means the client will use the same credentials in responding to HS2's challenge.
Alice's client receives the challenge, selects NTLM authentication, and reissues the REGISTER request to her home server.
REGISTER sip:hs2.contoso.com SIP/2.0 Via: SIP/2.0/TLS alice1.contoso.com;branch=z9hG4bKb From: "Alice" <sip:alice@contoso.com>;tag=354354535;epid=6534555 To: "Alice" sip:alice@contoso.com Call-ID: 123213@alice1.contoso.com CSeq: 12349 REGISTER Max-Forwards: 70 User-Agent: Windows RTC/1.1.2600 Proxy-Authorization: NTLM realm="Contoso RTC Service Provider", targetname="hs2.contoso.com",qop="auth",gssapi-data="" Contact: "Alice" sip:alice@alice1.contoso.com Content-Length: 0
The Cseq: number is incremented. The Call-ID and epid remain the same. The Proxy-Authorization: header indicates support for NTLM authentication.
Alice's home server receives the REGISTER request and issues an appropriate NTLM challenge.
SIP/2.0 407 Proxy Authentication Required Via: SIP/2.0/TLS alice1.contoso.com;branch=z9hG4bKb From: "Alice" <sip:alice@contoso.com>;tag=354354535;epid=6534555 To: "Alice" <sip:alice@contoso.com>;tag=8823488 Call-ID: 123213@alice1.contoso.com CSeq: 12349 REGISTER Date: Sat, 13 Nov 2010 23:29:00 GMT Proxy-Authenticate: NTLM realm="Contoso RTC Service Provider", targetname="hs2.contoso.com", qop="auth", opaque="CDEF1245", gssapi-data="dfd345435d" Content-Length: 0
The gssapi-data parameter contains the NTLM challenge. The opaque parameter identifies the (incomplete) SA on Alice's home server.
Alice's client responds to the challenge from Alice's home server by reissuing the REGISTER request.
REGISTER sip:hs2.contoso.com SIP/2.0 Via: SIP/2.0/TLS alice1.contoso.com;branch=z9hG4bKc From: "Alice" <sip:alice@contoso.com>;tag=354354535;epid=6534555 To: "Alice" sip:alice@contoso.com Call-ID: 123213@alice1.contoso.com CSeq: 12350 REGISTER Max-Forwards: 70 User-Agent: Windows RTC/1.1.2600 Proxy-Authorization: NTLM realm="Contoso RTC Service Provider", targetname="hs2.contoso.com",qop="auth", gssapi-data="8234934234", opaque="CDEF1245" Contact: "Alice" sip:alice@alice1.contoso.com Content-Length: 0
The CSeq number is incremented. The Call-ID remains the same. The opaque parameter is echoed from the server's challenge. The gssapi-data parameter carries the response to the server's challenge.
Alice's home server receives the REGISTER request, verifies the response to its challenge, and processes the REGISTER request. The SA between Alice's home server and Alice's client is now complete. The server responds to the REGISTER request and signs the response using the newly completed SA. The epid parameter from the From: header is saved as part of the registration information for Alice. This value will be inserted in the To: header of subsequent requests that are forwarded to Alice via her home server (registrar).
SIP/2.0 200 OK Via: SIP/2.0/TLS alice1.contoso.com;branch=z9hG4bKc From: "Alice" <sip:alice@contoso.com>;tag=354354535;epid=6534555 To: "Alice" <sip:alice@contoso.com>;tag=8823488 Call-ID: 123213@alice1.contoso.com CSeq: 12350 REGISTER Expires: 3600 Proxy-Authentication-Info: NTLM realm="Contoso RTC Service Provider", targetname="hs2.contoso.com", qop="auth", opaque="CDEF1245", rspauth="fefeacdd", srand=98984345, snum=1 Contact: "Alice" sip:alice@alice1.contoso.com Content-Length: 0
The epid parameter on the From: header is used by the server to determine how to sign this response (find the SA). The signature for this response is carried in the rspauth parameter of the Proxy-Authentication-Info: header.