Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
The following diagram shows the steps taken by a client that is negotiating SMB2 by using an SMB2 negotiate.
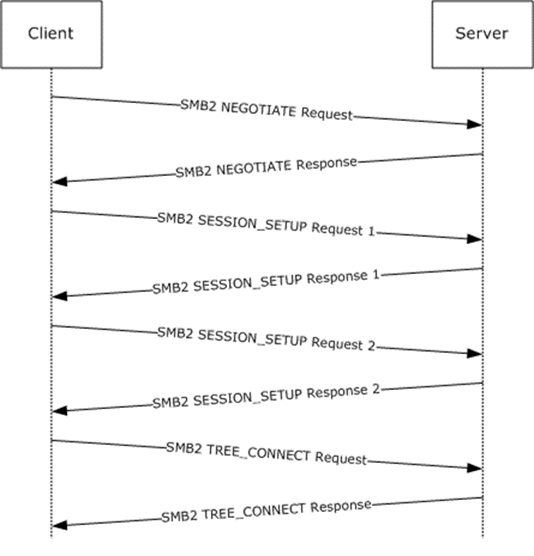
Figure 8: Client negotiating SMB2 with SMB2 negotiate
The client sends an SMB2 negotiate packet with the dialect 0x0202 in the Dialects array.
Smb2: C NEGOTIATE SMB2Header: Size: 64 (0x40) CreditCharge: 0 (0x0) Status: STATUS_SUCCESS Command: NEGOTIATE Credits: 126 (0x7E) Flags: 0 (0x0) ServerToRedir: ...............................0 Client to Server AsyncCommand: ..............................0. Command is not asynchronous Related: .............................0.. Packet is single message Signed: ............................0... Packet is not signed Reserved: 0 (0x0) DFS: 0............................... Command is not a DFS Operation NextCommand: 0 (0x0) MessageId: 0 (0x0) Reserved: 0 (0x0) TreeId: 0 (0x0) SessionId: 0 (0x0) CNegotiate: Size: 36 (0x24) DialectCount: 1 (0x1) SecurityMode: Signing Enabled Reserved: 0 (0x0) Capabilities: 0 (0x0) Guid: {00000000-0000-0000-0000-000000000000} StartTime: 0 (0x0) Dialects: 514 (0x0202)The server receives the SMB2 NEGOTIATE Request and finds dialect 0x0202. The server responds with an SMB2 negotiate.
Smb2: R NEGOTIATE SMB2Header: Size: 64 (0x40) CreditCharge: 0 (0x0) Status: STATUS_SUCCESS Command: NEGOTIATE Credits: 1 (0x1) Flags: 1 (0x1) ServerToRedir: ...............................1 Server to Client AsyncCommand: ..............................0. Command is not asynchronous Related: .............................0.. Packet is single message Signed: ............................0... Packet is not signed Reserved: 0 (0x0) DFS: 0............................... Command is not a DFS Operation NextCommand: 0 (0x0) MessageId: 0 (0x0) Reserved: 0 (0x0) TreeId: 0 (0x0) SessionId: 0 (0x0) RNegotiate: Size: 65 (0x41) SecurityMode: Signing Enabled DialectRevision: 514 (0x0202) Reserved: 0 (0x0) Guid: {3F5CF209-A4E5-0049-A7D6-6A456D5CA5CF} Capabilities: 1 (0x1) DFS: ...............................1 DFS available MaxTransactSize: 65536 (0x10000) MaxReadSize: 65536 (0x10000) MaxWriteSize: 65536 (0x10000) SystemTime: 127972992061679232 (0x1C6A6C21CAE2680) ServerStartTime: 127972985895467232 (0x1C6A6C0AD2538E0) SecurityBufferOffset: 128 (0x80) SecurityBufferLength: 30 (0x1E) Reserved2: 0 (0x0) Buffer:The client queries GSS for the authentication token and sends an SMB2 SESSION_SETUP Request with the output token received from GSS.
Smb2: C SESSION SETUP SMB2Header: Size: 64 (0x40) CreditCharge: 0 (0x0) Status: STATUS_SUCCESS Command: SESSION SETUP Credits: 126 (0x7E) Flags: 0 (0x0) ServerToRedir: ...............................0 Client to Server AsyncCommand: ..............................0. Command is not asynchronous Related: .............................0.. Packet is single message Signed: ............................0... Packet is not signed Reserved: 0 (0x0) DFS: 0............................... Command is not a DFS Operation NextCommand: 0 (0x0) MessageId: 1 (0x1) Reserved: 0 (0x0) TreeId: 0 (0x0) SessionId: 0 (0x0) CSessionSetup: Size: 25 (0x19) VcNumber: 0 (0x0) SecurityMode: Signing Enabled Capabilities: 1 (0x1) DFS: ...............................1 DFS available Channel: 0 (0x0) SecurityBufferOffset: 88 (0x58) SecurityBufferLength: 74 (0x4A) Buffer: (74 bytes)
The server processes the token received with GSS and gets a return code indicating a subsequent round trip is required. The server responds to the client with an SMB2 SESSION_SETUP Response with Status equal to STATUS_MORE_PROCESSING_REQUIRED and the response containing the output token from GSS.
Smb2: R SESSION SETUP (Status=STATUS_MORE_PROCESSING_REQUIRED) SMB2Header: Size: 64 (0x40) CreditCharge: 0 (0x0) Status: STATUS_MORE_PROCESSING_REQUIRED Command: SESSION SETUP Credits: 2 (0x2) Flags: 1 (0x1) ServerToRedir: ...............................1 Server to Client AsyncCommand: ..............................0. Command is not asynchronous Related: .............................0.. Packet is single message Signed: ............................0... Packet is not signed Reserved: 0 (0x0) DFS: 0............................... Command is not a DFS Operation NextCommand: 0 (0x0) MessageId: 1 (0x1) Reserved: 0 (0x0) TreeId: 0 (0x0) SessionId: 4398046511113 (0x40000000009) RSessionSetup: Size: 9 (0x9) SessionFlags: Normal session SecurityBufferOffset: 72 (0x48) SecurityBufferLength: 219 (0xDB) Buffer: (219 bytes)
The client processes the received token with GSS and sends an SMB2 SESSION_SETUP Request with the output token received from GSS and the SessionId received on the previous response.
Smb2: C SESSION SETUP SMB2Header: Size: 64 (0x40) CreditCharge: 0 (0x0) Status: STATUS_SUCCESS Command: SESSION SETUP Credits: 125 (0x7D) Flags: 0 (0x0) ServerToRedir: ...............................0 Client to Server AsyncCommand: ..............................0. Command is not asynchronous Related: .............................0.. Packet is single message Signed: ............................0... Packet is not signed Reserved: 0 (0x0) DFS: 0............................... Command is not a DFS Operation NextCommand: 0 (0x0) MessageId: 2 (0x2) Reserved: 0 (0x0) TreeId: 0 (0x0) SessionId: 4398046511113 (0x40000000009) CSessionSetup: Size: 25 (0x19) VcNumber: 0 (0x0) SecurityMode: Signing Enabled Capabilities: 1 (0x1) DFS: ...............................1 DFS available Channel: 0 (0x0) SecurityBufferOffset: 88 (0x58) SecurityBufferLength: 245 (0xF5) Buffer: (245 bytes)
The server processes the token received with GSS and gets a successful return code. The server responds to the client with an SMB2 SESSION_SETUP Response with Status equal to STATUS_SUCCESS and the response containing the output token from GSS.
Smb2: R SESSION SETUP SMB2Header: Size: 64 (0x40) CreditCharge: 0 (0x0) Status: STATUS_SUCCESS Command: SESSION SETUP Credits: 3 (0x3) Flags: 9 (0x9) ServerToRedir: ...............................1 Server to Client AsyncCommand: ..............................0. Command is not asynchronous Related: .............................0.. Packet is single message Signed: ............................1... Packet is signed Reserved: 0 (0x0) DFS: 0............................... Command is not a DFS Operation NextCommand: 0 (0x0) MessageId: 2 (0x2) Reserved: 0 (0x0) TreeId: 0 (0x0) SessionId: 4398046511113 (0x40000000009) RSessionSetup: Size: 9 (0x9) SessionFlags: Normal session SecurityBufferOffset: 72 (0x48) SecurityBufferLength: 29 (0x1D) Buffer: (29 bytes)
The client completes the authentication and sends an SMB2 TREE_CONNECT Request with the SessionId for the session, and a tree connect request containing the Unicode share name "\\smb2server\IPC$".
Smb2: C TREE CONNECT \\smb2server\IPC$ SMB2Header: Size: 64 (0x40) CreditCharge: 0 (0x0) Status: STATUS_SUCCESS Command: TREE CONNECT Credits: 123 (0x7B) Flags: 0 (0x0) ServerToRedir: ...............................0 Client to Server AsyncCommand: ..............................0. Command is not asynchronous Related: .............................0.. Packet is single message Signed: ............................0... Packet is not signed Reserved: 0 (0x0) DFS: 0............................... Command is not a DFS Operation NextCommand: 0 (0x0) MessageId: 3 (0x3) Reserved: 0 (0x0) TreeId: 0 (0x0) SessionId: 4398046511113 (0x40000000009) CTreeConnect: Size: 9 (0x9) Reserved: 0 (0x0) PathOffset: 72 (0x48) PathLength: 34 (0x22) Share: \\smb2server\IPC$
The server responds with an SMB2 TREE_CONNECT Response with MessageId of 3, CreditResponse of 5, Status equal to STATUS_SUCCESS, SessionId of 0x40000000009, and TreeId set to the locally generated identifier 0x1.
Smb2: R TREE CONNECT TID=0x1 SMB2Header: Size: 64 (0x40) CreditCharge: 0 (0x0) Status: STATUS_SUCCESS Command: TREE CONNECT Credits: 5 (0x5) Flags: 1 (0x1) ServerToRedir: ...............................1 Server to Client AsyncCommand: ..............................0. Command is not asynchronous Related: .............................0.. Packet is single message Signed: ............................0... Packet is not signed Reserved: 0 (0x0) DFS: 0............................... Command is not a DFS Operation NextCommand: 0 (0x0) MessageId: 3 (0x3) Reserved: 0 (0x0) TreeId: 1 (0x1) SessionId: 4398046511113 (0x40000000009) RTreeConnect: Size: 16 (0x10) ShareType: Pipe Reserved: 0 (0x0) Flags: No Caching Capabilities: 0 (0x0) MaximalAccess: 2032127 (0x1F01FF)
Further operations can now continue, using the SessionId and TreeId generated in the connection to this share.