4.1 Telnet Client Successfully Authenticating to a Telnet Server
This section illustrates the Telnet: NTLM Authentication Protocol with an example scenario in which a Telnet client successfully authenticates to a Telnet server.
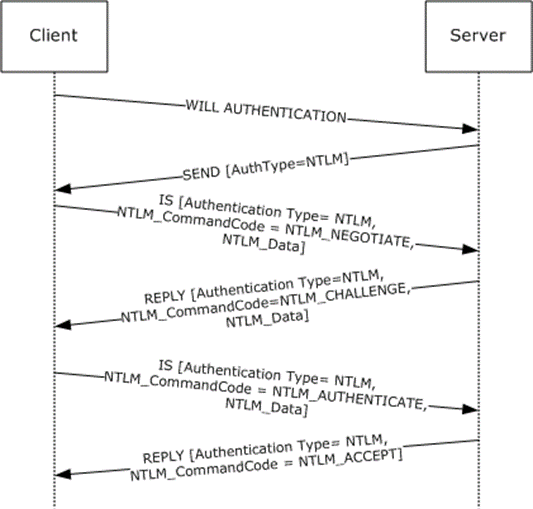
Figure 6: Telnet client authenticating Telnet server
The client sends an IAC WILL AUTHENTICATION command to the server. This command is defined in [RFC2941] and does not carry any Telnet: NTLM Authentication Protocol-specific data. It is included in this example to provide a better understanding.
The server sends the SEND command with AuthenticationType=0x0F. AuthenticationType 0x0F corresponds to NTLM.
Sample Frame:
-
+ Ethernet: Etype = Internet IP (IPv4) + Ipv4: Next Protocol = TCP, Packet ID = 52505, Total IP Length = 60 + Tcp: Flags=...PA..., SrcPort=Telnet(23), DstPort=1827, Len=8, Seq=4209081200 - 4209081208, Ack=3503001584, Win=65532 (scale factor 0) = 0 - Telnet: To Client, DstPort = 0x723 - Telcmd: IAC SB (START OF SUBNEGOTIATION PARAMETERS) Command: IAC SB (START OF SUBNEGOTIATION PARAMETERS) - AUTH: AUTHENTICATION OPTION SEND OptionCode: AUTHENTICATION OPTION SubCode: SEND AuthenticationType: NTLM - Modifier: 0x0,ENCRYPT_OFF AuthWhoMask: (0.......)AUTH_CLIENT_TO_SERVER AuthHowMask: (.0......)AUTH_HOW_ONE_WAY EncryptMask3: (..0.....) IniCredFwdMask: (...0....)INI_CRED_FWD_OFF EncryptMask5: (....0...) Unused: (.....000) EndCommand: IAC SE (END OF SUBNEGOTIATION PARAMETERS)
The client queries the local NTLM software for NTLM NEGOTIATE_MESSAGE, encapsulates it in an IS packet, sets various fields (see the following), and sends it to the server.
AuthenticationType = 0x0F
Modifier = 0x00
NTLM_CommandCode = NTLM_NEGOTIATE
NTLM_DataSize = size of NTLM NEGOTIATE_MESSAGE
NTLM_BufferType = 0x00000002
NTLM_Data = NTLM NEGOTIATE_MESSAGE
Sample Frame:
-
+ Ethernet: Etype = Internet IP (IPv4) + Ipv4: Next Protocol = TCP, Packet ID = 36869, Total IP Length = 130 + Tcp: Flags=...PA..., SrcPort=1827, DstPort=Telnet(23), Len=78, Seq=3503001590 - 3503001668, Ack=4209081208, Win=64232 (scale factor 0) = 0 - Telnet: To Server, SrcPort = 0x723 - Telcmd: IAC SB (START OF SUBNEGOTIATION PARAMETERS) Command: IAC SB (START OF SUBNEGOTIATION PARAMETERS) - AUTH: AUTHENTICATION OPTION IS OptionCode: AUTHENTICATION OPTION SubCode: IS AuthenticationType: NTLM - Modifier: 0x0,ENCRYPT_OFF AuthWhoMask: (0.......)AUTH_CLIENT_TO_SERVER AuthHowMask: (.0......)AUTH_HOW_ONE_WAY EncryptMask3: (..0.....) IniCredFwdMask: (...0....)INI_CRED_FWD_OFF EncryptMask5: (....0...) Unused: (.....000) - AuthData: NTLMCommandCode: NTLM_NEGOTIATE NTLMDataSize: 40 (0x28) NTLMBufferType: 2 (0x2) - NTLMData: + ntlmssp: NTLM NEGOTIATE MESSAGE EndCommand: IAC SE (END OF SUBNEGOTIATION PARAMETERS)
The server passes the NTLM NEGOTIATE_MESSAGE that it received from the client to the local NTLM software. The server then sends a REPLY command with the NTLM CHALLENGE_MESSAGE got from the local NTLM software encapsulated and various fields set as follows.
AuthenticationType = 0x0F
Modifier = 0x00
NTLM_CommandCode = NTLM_CHALLENGE
NTLM_DataSize = size of NTLM CHALLENGE_MESSAGE
NTLM_BufferType = 0x00000002
NTLM_Data = NTLM CHALLENGE_MESSAGE
The following is a Sample Frame.
-
+ Ethernet: Etype = Internet IP (IPv4) + Ipv4: Next Protocol = TCP, Packet ID = 52509, Total IP Length = 344 + Tcp: Flags=...PA..., SrcPort=Telnet(23), DstPort=1827, Len=292, Seq=4209081208 - 4209081500, Ack=3503001668, Win=65448 (scale factor 0) = 0 - Telnet: To Client, DstPort = 0x723 - Telcmd: IAC SB (START OF SUBNEGOTIATION PARAMETERS) Command: IAC SB (START OF SUBNEGOTIATION PARAMETERS) - AUTH: AUTHENTICATION OPTION REPLY OptionCode: AUTHENTICATION OPTION SubCode: REPLY AuthenticationType: NTLM - Modifier: 0x0,ENCRYPT_OFF AuthWhoMask: (0.......)AUTH_CLIENT_TO_SERVER AuthHowMask: (.0......)AUTH_HOW_ONE_WAY EncryptMask3: (..0.....) IniCredFwdMask: (...0....)INI_CRED_FWD_OFF EncryptMask5: (....0...) Unused: (.....000) - AuthData: NTLMCommandCode: NTLM_CHALLENGE NTLMDataSize: 240 (0xF0) NTLMBufferType: 2 (0x2) - NTLMData: + ntlmssp: NTLM CHALLENGE MESSAGE EndCommand: IAC SE (END OF SUBNEGOTIATION PARAMETERS)
The client passes the NTLM CHALLENGE_MESSAGE that it received from the server to the local NTLM software. The client then sends an IS command with NTLM AUTHENTICATE_MESSAGE got from the local NTLM software encapsulated and various fields set as follows.
AuthenticationType = 0x0F
Modifier = 0x00
NTLM_CommandCode = NTLM_AUTHENTICATE
NTLM_DataSize = size of NTLM AUTHENTICATE_MESSAGE
NTLM_BufferType = 0x00000002
NTLM_Data = NTLM AUTHENTICATE_MESSAGE
The following is a Sample Frame.
-
+ Ethernet: Etype = Internet IP (IPv4) + Ipv4: Next Protocol = TCP, Packet ID = 36871, Total IP Length = 294 + Tcp: Flags=...PA..., SrcPort=1827, DstPort=Telnet(23), Len=242, Seq=3503001712 - 3503001954, Ack=4209081500, Win=64159 (scale factor 0) = 0 - Telnet: To Server, SrcPort = 0x723 - Telcmd: IAC SB (START OF SUBNEGOTIATION PARAMETERS) Command: IAC SB (START OF SUBNEGOTIATION PARAMETERS) - AUTH: AUTHENTICATION OPTION IS OptionCode: AUTHENTICATION OPTION SubCode: IS AuthenticationType: NTLM - Modifier: 0x0,ENCRYPT_OFF AuthWhoMask: (0.......)AUTH_CLIENT_TO_SERVER AuthHowMask: (.0......)AUTH_HOW_ONE_WAY EncryptMask3: (..0.....) IniCredFwdMask: (...0....)INI_CRED_FWD_OFF EncryptMask5: (....0...) Unused: (.....000) - AuthData: NTLMCommandCode: NTLM_AUTHENTICATE NTLMDataSize: 186 (0xBA) NTLMBufferType: 2 (0x2) - NTLMData: + ntlmssp: NTLM AUTHENTICATE MESSAGE EndCommand: IAC SE (END OF SUBNEGOTIATION PARAMETERS)
The server passes the NTLM AUTHENTICATE_MESSAGE to the local NTLM software. The server then sends a REPLY command to the client with various fields set as follows.
AuthenticationType = 0x0F
Modifier = 0x00
NTLM_CommandCode = NTLM_ACCEPT
Sample Frame:
-
+ Ethernet: Etype = Internet IP (IPv4) + Ipv4: Next Protocol = TCP, Packet ID = 52520, Total IP Length = 64 + Tcp: Flags=...PA..., SrcPort=Telnet(23), DstPort=1827, Len=12, Seq=4209081500 - 4209081512, Ack=3503001954, Win=65162 (scale factor 0) = 0 - Telnet: To Client, DstPort = 0x723 - Telcmd: IAC SB (START OF SUBNEGOTIATION PARAMETERS) Command: IAC SB (START OF SUBNEGOTIATION PARAMETERS) - AUTH: AUTHENTICATION OPTION REPLY OptionCode: AUTHENTICATION OPTION SubCode: REPLY AuthenticationType: NTLM - Modifier: 0x0,ENCRYPT_OFF AuthWhoMask: (0.......)AUTH_CLIENT_TO_SERVER AuthHowMask: (.0......)AUTH_HOW_ONE_WAY EncryptMask3: (..0.....) IniCredFwdMask: (...0....)INI_CRED_FWD_OFF EncryptMask5: (....0...) Unused: (.....000) - AuthData: NTLMCommandCode: NTLM_ACCEPT EndCommand: IAC SE (END OF SUBNEGOTIATION PARAMETERS)
The actual value of NTLM_CommandCode depends on the return value given by the local NTLM software after it processes the NTLM AUTHENTICATE_MESSAGE. In this example, it is assumed that the NTLM software returns success.