Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Note
The new and improved Power Platform admin center is now generally available. We're currently updating the documentation to reflect these changes, so check back to ensure that you're getting the latest updates.
You can use connector action control to allow or block individual actions or triggers within a given connector.
Important
In February 2025, support for triggers is added to the connector action control. This can be administered through PowerShell. Support for triggers is planned for the Power Platform admin center in the future, as well.
Making changes to policies through the Power Platform admin center doesn't remove triggers that were added via PowerShell.
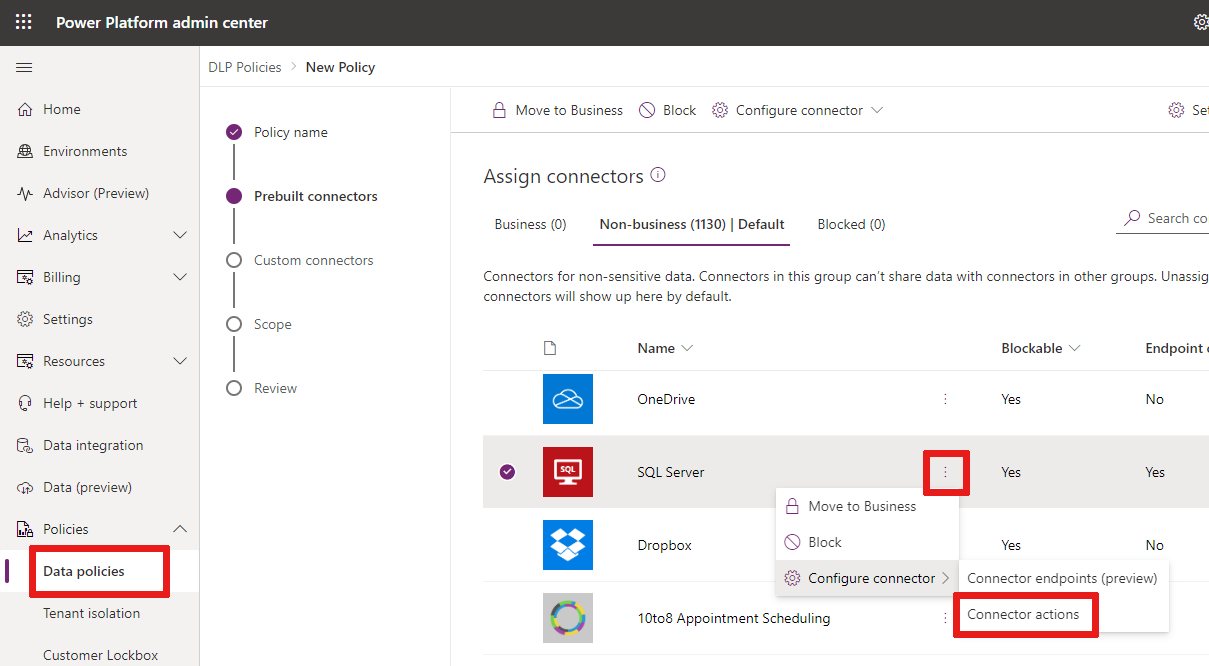
Sign in to the Power Platform admin center as a System Administrator.
On the left navigation pane, select Policies > Data policies.
Select a policy and on the command bar, select Edit Policy.
On the left, select Prebuilt connectors.
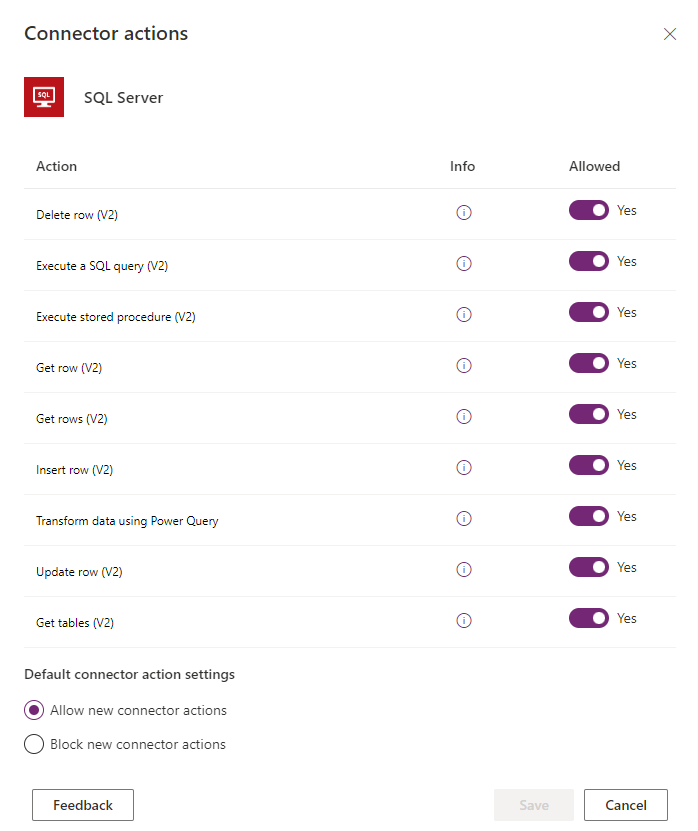
Select More actions next to your connector and then select Configure connector > Connector actions.
Note
You can configure connector actions for all blockable connectors, but not for unblockable connectors and custom connectors.
Use the side panel to allow or deny specific actions.
You can also set the Default connector action settings to allow or block for any new connector actions that will be added to the connector in the future.
Known limitations
Triggers are only supported in PowerShell
Support for allowing and blocking individual triggers is currently available only via PowerShell. Support is planned for the Power Platform admin center in the future. For an example of how to allow triggers that're already in use by Power Automate flows, see Identify blocked Power Automate flows.
Admins need to have maker access to Power Apps
The list of connector actions is retrieved using calls to Power Apps on behalf of the admin. The admin must sign in to Power Apps and have access to complete the user consent process. If the admin doesn't have access to Power Apps, then the list of connector actions won't be retrieved.
Republish Power Apps
Some Power Apps, published before October 1, 2020, need to be republished for connector action rules to enforce data loss prevention (DLP).
This script helps admins and makers identify the apps that must be republished.
Add-PowerAppsAccount
$GranularDLPDate = Get-Date -Date "2020-10-01 00:00:00Z"
ForEach ($app in Get-AdminPowerApp){
$versionAsDate = [datetime]::Parse($app.LastModifiedTime)
$olderApp = $versionAsDate -lt $GranularDLPDate
$wasBackfilled = $app.Internal.properties.executionRestrictions -ne $null -and $app.Internal.properties.executionRestrictions.dataLossPreventionEvaluationResult -ne $null -and ![string]::IsNullOrEmpty($app.Internal.properties.executionRestrictions.dataLossPreventionEvaluationResult.lastAdvancedBackfillDate)
If($($olderApp -and !$wasBackfilled)){
Write-Host "App must be republished to be Granular DLP compliant: " $app.AppName " " $app.Internal.properties.displayName " " $app.Internal.properties.owner.email
}
Else{
Write-Host "App is already Granular DLP compliant: " $app.AppName
}
}
PowerShell support for connector action control
Retrieve a list of available actions for a connector, using Get-AdminPowerAppConnectorAction.
Get-AdminPowerAppConnectorAction
For example:
Get-AdminPowerAppConnectorAction -ConnectorName shared_msnweather
| ID | Type | Properties |
|---|---|---|
| TodaysForecast | Microsoft.ProcessSimple/apis/apiOperations | Get the forecast for the current day in a specified location. |
| OnCurrentWeatherChange | Microsoft.ProcessSimple/apis/apiOperations | Triggers a new flow when the specified weather measure changes. |
| CurrentWeather | Microsoft.ProcessSimple/apis/apiOperations | Get the current weather for a location. Visibility=advanced |
| TomorrowsForecast | Microsoft.ProcessSimple/apis/apiOperations | Get the forecast for tomorrow in the specified location. |
| OnCurrentConditionsChange | Microsoft.ProcessSimple/apis/apiOperations | Triggers a new flow when the conditions change for a location. |
Configure connector action rules for a policy
The object that contains connector action rules for a policy is referred to below as the connector configurations.
The connector configurations object has the following structure:
$ConnectorConfigurations = @{
connectorActionConfigurations = @( # array – one entry per connector
@{
connectorId # string
actionRules = @( # array – one entry per rule
@{
actionId # string
behavior # supported values: Allow/Block
}
)
defaultConnectorActionRuleBehavior # supported values: Allow/Block
}
)
}
Retrieve existing connector configurations for a DLP policy
Get-PowerAppDlpPolicyConnectorConfigurations
Create connector configurations for a DLP policy
New-PowerAppDlpPolicyConnectorConfigurations
Update connector configurations for a DLP policy
Set-PowerAppDlpPolicyConnectorConfigurations
Example
Goal:
- Block actions TodaysForecast and CurrentWeather of connector MSN Weather; allow all other actions.
- Allow action GetRepositoryById of connector GitHub; block all other actions.
Note
In the following cmdlet, PolicyName refers to the unique GUID. You can retrieve the DLP GUID by running the Get-DlpPolicy cmdlet.
$ConnectorConfigurations = @{
connectorActionConfigurations = @(
@{
connectorId = "/providers/Microsoft.PowerApps/apis/shared_msnweather"
actionRules = @(
@{
actionId = "TodaysForecast"
behavior = "Block"
},
@{
actionId = "CurrentWeather"
behavior = "Block"
}
)
defaultConnectorActionRuleBehavior = "Allow"
},
@{
connectorId = "/providers/Microsoft.PowerApps/apis/shared_github"
actionRules = @(
@{
actionId = "GetRepositoryById"
behavior = "Allow"
}
)
defaultConnectorActionRuleBehavior = "Block"
}
)
}
New-PowerAppDlpPolicyConnectorConfigurations -TenantId $TenantId -PolicyName $PolicyName -NewDlpPolicyConnectorConfigurations $ConnectorConfigurations